Strengthening Cyber Defense Against Vulnerabilities in End-of-Support Edge Devices
Published on: 2026-02-05
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Reducing the Attack Surface for End-of-Support Edge Devices
1. BLUF (Bottom Line Up Front)
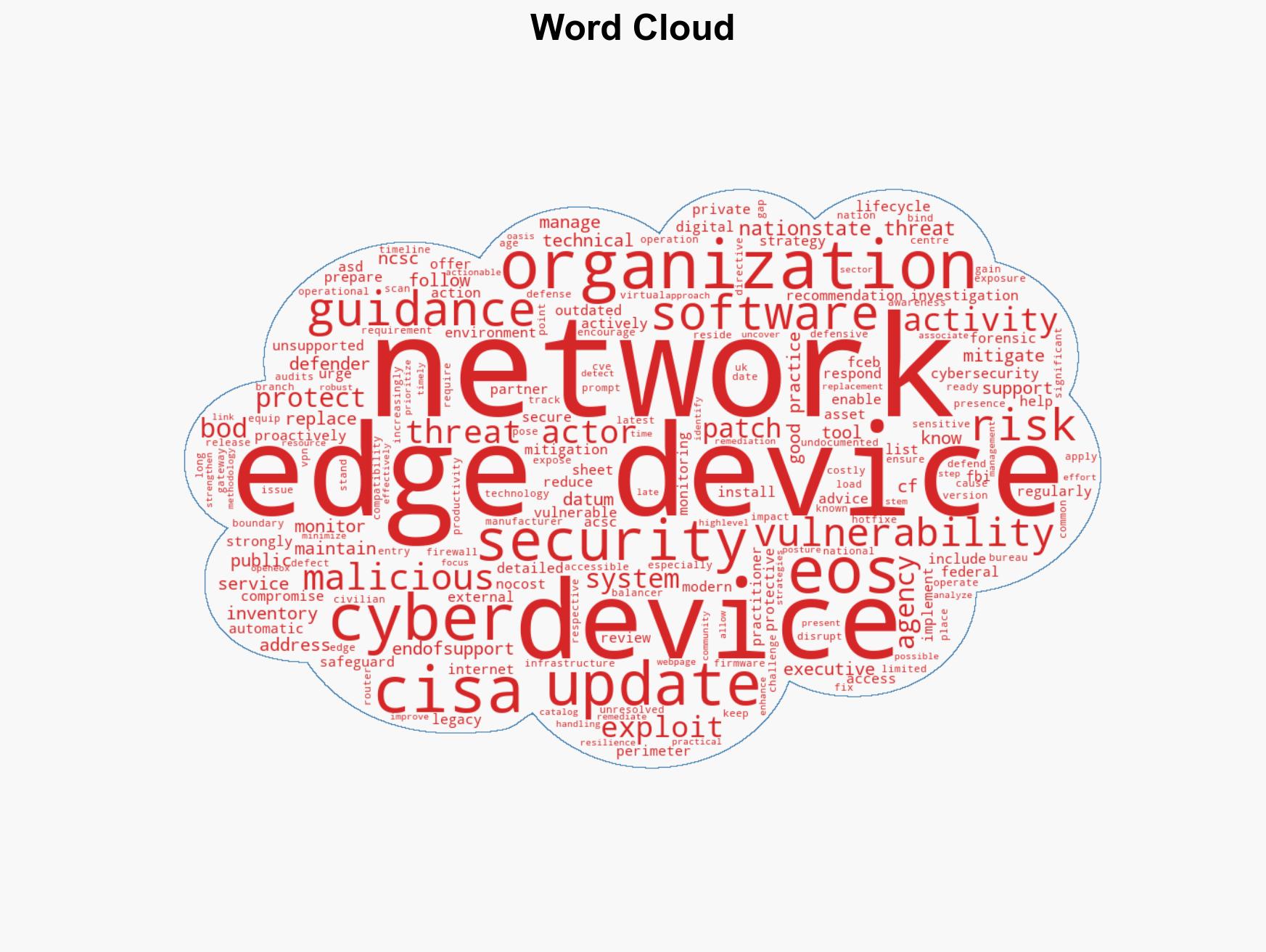
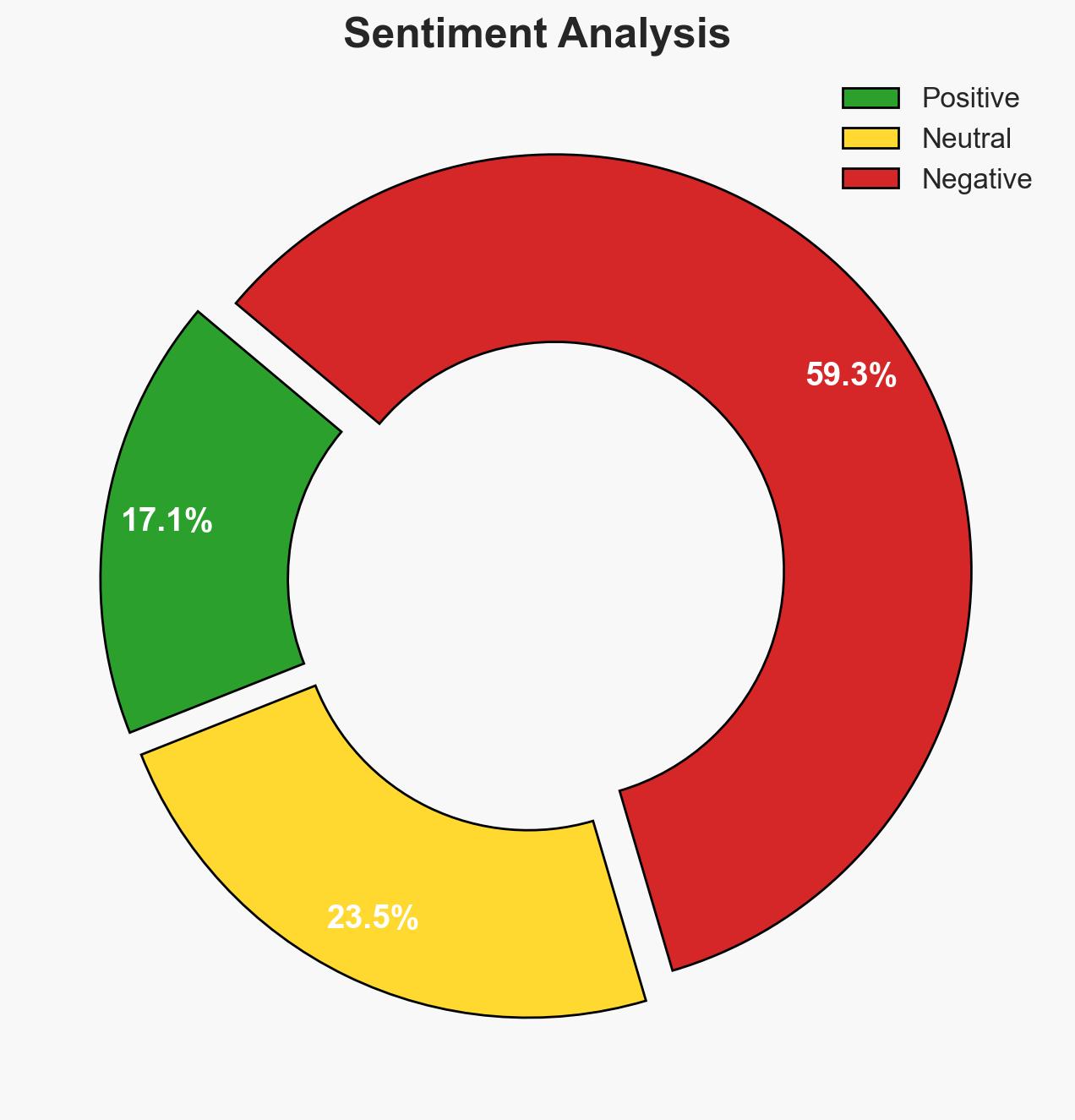
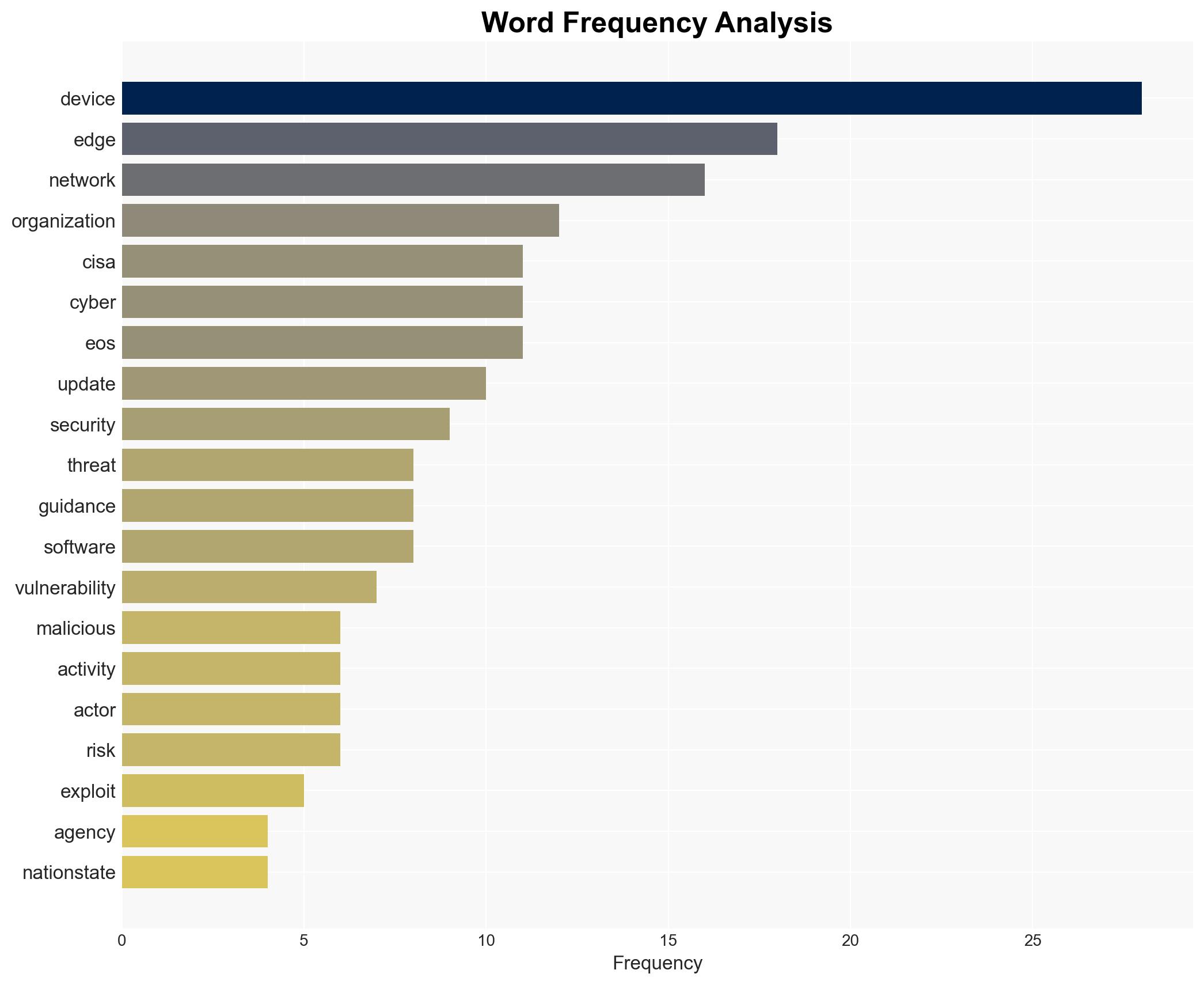
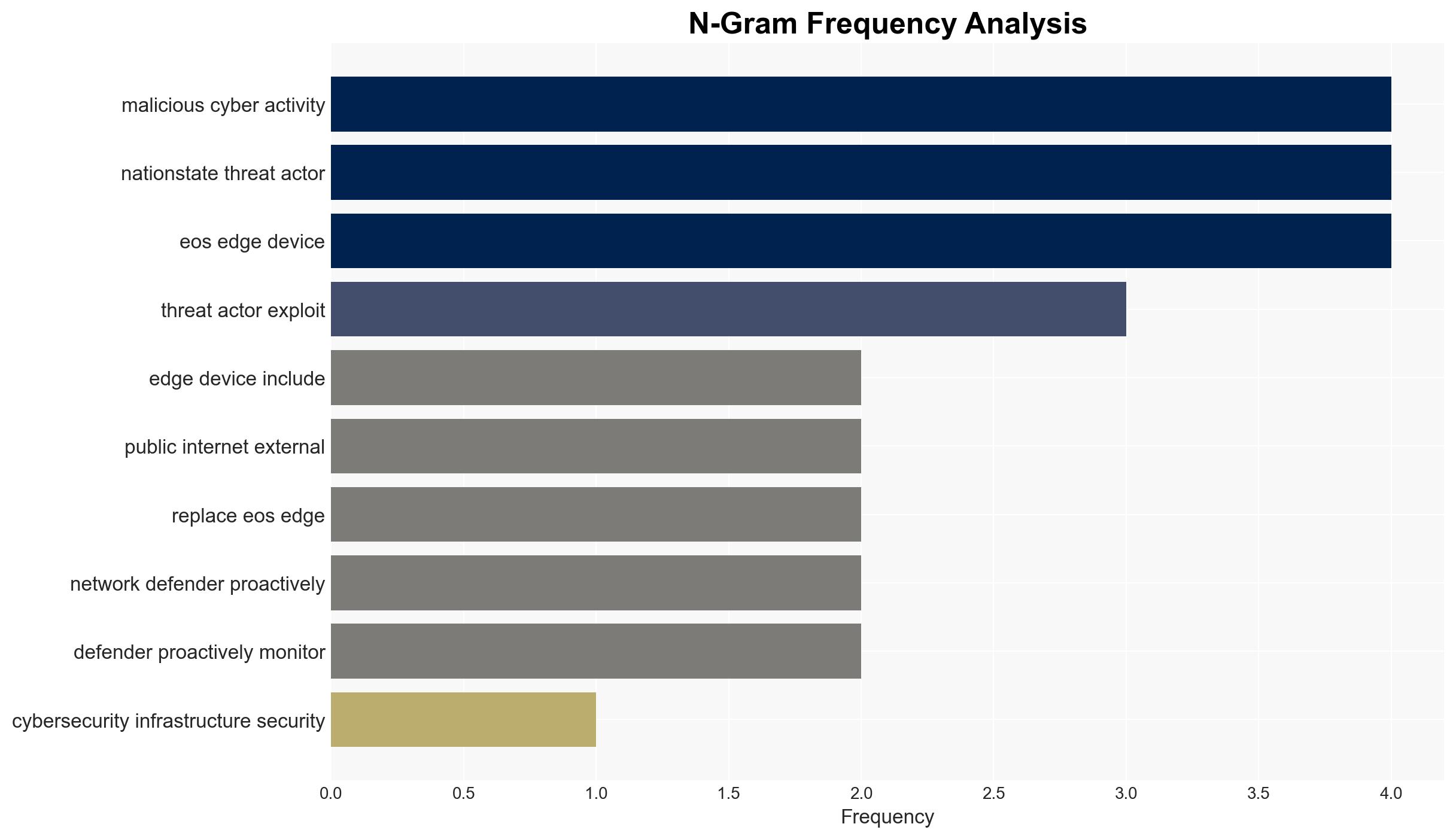
The exploitation of end-of-support (EOS) edge devices by nation-state threat actors poses a significant cybersecurity risk to organizations, particularly those with devices exposed to the public internet. The most likely hypothesis is that these actors will continue to exploit these vulnerabilities to gain unauthorized access to sensitive networks. This assessment is made with moderate confidence due to the ongoing nature of these threats and the explicit warnings from CISA, FBI, and NCSC.
2. Competing Hypotheses
- Hypothesis A: Nation-state threat actors will increasingly target EOS edge devices to exploit unresolved security gaps, leading to significant data breaches and network compromises. This is supported by the explicit warnings from CISA, FBI, and NCSC, and the inherent vulnerabilities in unsupported devices. Key uncertainties include the specific capabilities and intentions of the threat actors.
- Hypothesis B: Organizations will effectively mitigate the risks associated with EOS edge devices by following the guidance in BOD 26-02, thus reducing the potential for successful cyber intrusions. This hypothesis relies on the assumption that organizations will prioritize and implement the recommended security measures, which may not be uniformly applied.
- Assessment: Hypothesis A is currently better supported due to the historical pattern of cyber exploitation by nation-state actors and the technical challenges in rapidly replacing or securing EOS devices. Indicators that could shift this judgment include widespread adoption of the recommended mitigations and a decrease in reported incidents involving EOS devices.
3. Key Assumptions and Red Flags
- Assumptions: Organizations will not uniformly replace or secure EOS devices; nation-state actors have the capability to exploit these vulnerabilities; the guidance from CISA, FBI, and NCSC is technically feasible for most organizations; EOS devices are prevalent in critical infrastructure.
- Information Gaps: Specific data on the number of EOS devices currently in use and the rate of their replacement or mitigation; detailed intelligence on the specific nation-state actors targeting these devices.
- Bias & Deception Risks: Potential for confirmation bias in assessing the threat level based on historical incidents; reliance on public statements from government agencies without independent verification; possible misinformation from threat actors to obscure their true capabilities or intentions.
4. Implications and Strategic Risks
The continued exploitation of EOS edge devices could lead to significant breaches of sensitive data and disruption of critical services, affecting national security and economic stability. Over time, this could erode trust in digital infrastructure and increase geopolitical tensions.
- Political / Geopolitical: Increased tensions between nation-states due to perceived or actual cyber intrusions; potential for retaliatory cyber operations.
- Security / Counter-Terrorism: Heightened threat environment as cyber vulnerabilities are exploited for espionage or sabotage; potential for cascading effects on critical infrastructure.
- Cyber / Information Space: Increased focus on cybersecurity measures and public-private partnerships; potential for misinformation campaigns exploiting fear of cyber threats.
- Economic / Social: Potential economic losses from data breaches and service disruptions; increased costs for organizations to replace or secure EOS devices.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct comprehensive audits of network devices to identify EOS devices; prioritize replacement or mitigation of high-risk devices; increase monitoring for signs of exploitation.
- Medium-Term Posture (1–12 months): Develop and implement a lifecycle management plan for all network devices; enhance collaboration with cybersecurity agencies for threat intelligence sharing; invest in training for cybersecurity personnel.
- Scenario Outlook:
- Best Case: Rapid adoption of mitigation measures leads to a significant decrease in successful cyber intrusions.
- Worst Case: Continued exploitation of EOS devices results in major breaches of critical infrastructure, leading to severe economic and security consequences.
- Most-Likely: Gradual improvement in security posture as organizations implement recommended measures, with periodic incidents highlighting ongoing vulnerabilities.
6. Key Individuals and Entities
- Cybersecurity and Infrastructure Security Agency (CISA)
- Federal Bureau of Investigation (FBI)
- U.K.’s National Cyber Security Centre (NCSC)
- U.S. Federal Civilian Executive Branch (FCEB) agencies
- Nation-state threat actors (not clearly identifiable from open sources in this snippet)
7. Thematic Tags
cybersecurity, nation-state actors, end-of-support devices, network security, critical infrastructure, cyber defense, vulnerability management
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us