China-Linked Group UNC3886 Launches Cyber Espionage Attacks on Singapore’s Telecom Industry
Published on: 2026-02-09
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: China-Linked UNC3886 Targets Singapore Telecom Sector in Cyber Espionage Campaign
1. BLUF (Bottom Line Up Front)
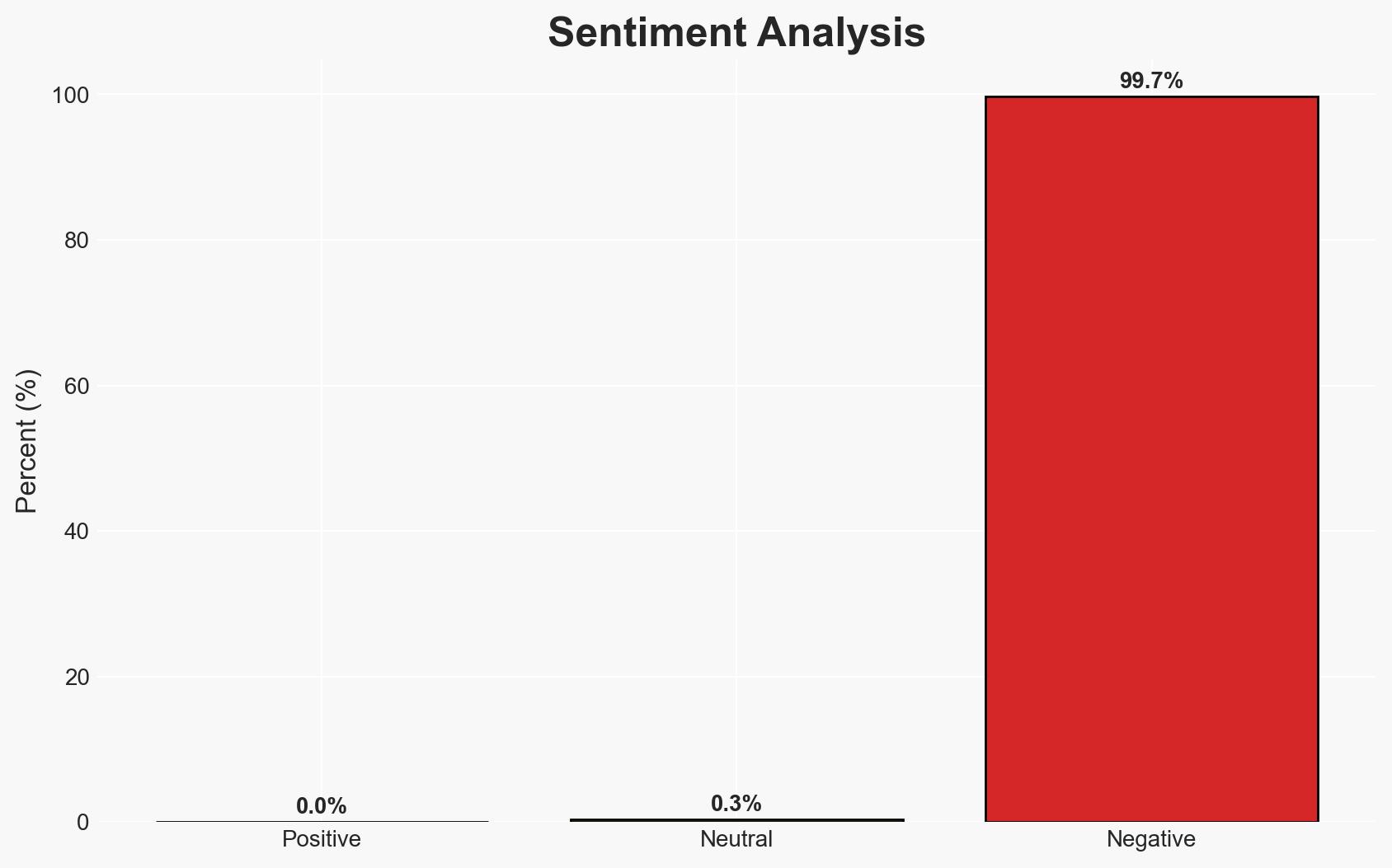
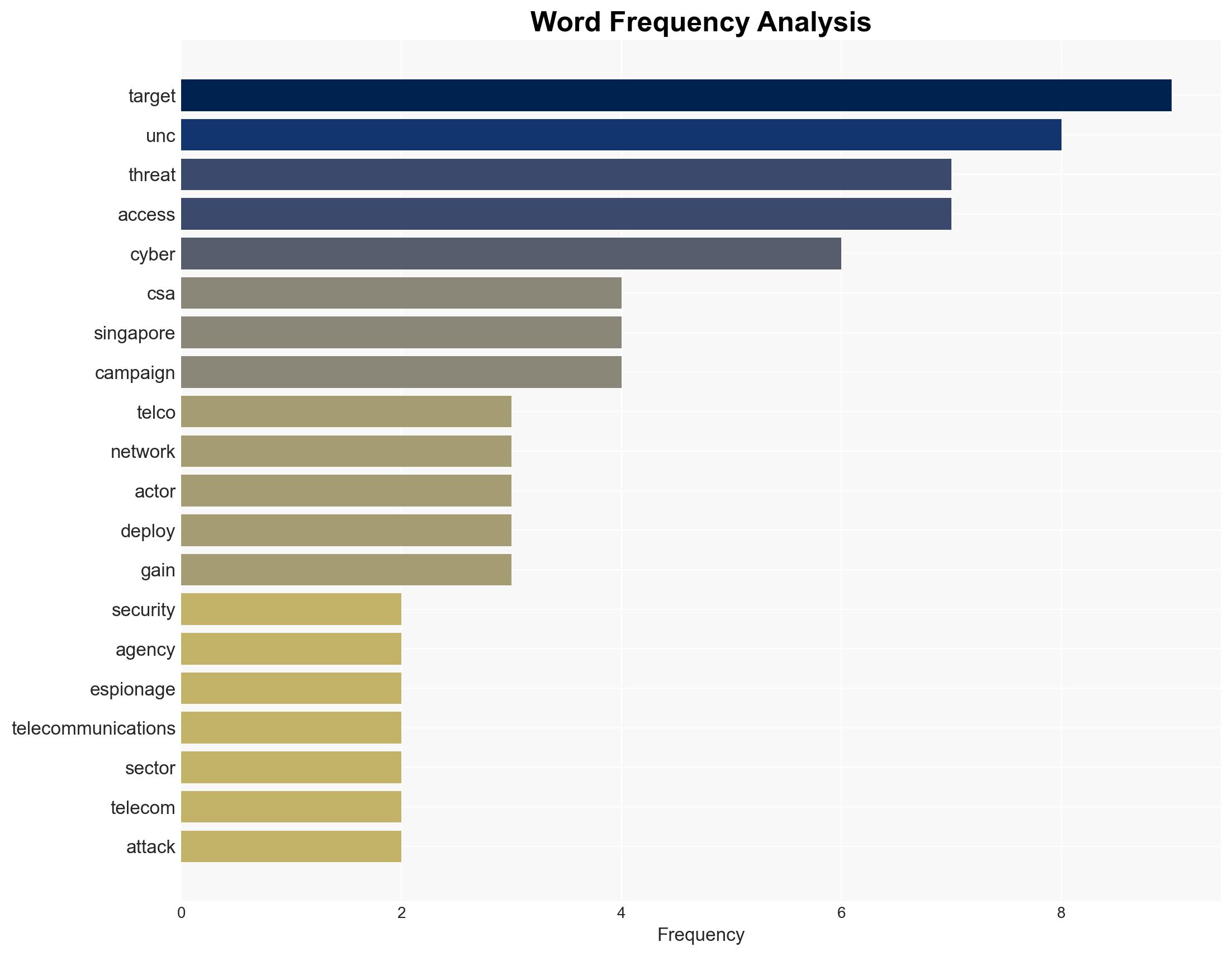
The cyber espionage group UNC3886, linked to China, has conducted a sophisticated campaign targeting Singapore’s telecommunications sector. This operation involved advanced techniques, including zero-day exploits and rootkits, but did not result in service disruption or personal data exfiltration. The most likely hypothesis is that this campaign aims to gather strategic intelligence on Singapore’s telecom infrastructure. Overall, the confidence level in this assessment is moderate due to existing information gaps and potential bias in source reporting.
2. Competing Hypotheses
- Hypothesis A: UNC3886’s campaign is primarily aimed at strategic intelligence gathering on Singapore’s telecommunications infrastructure to enhance China’s geopolitical and economic positioning. This is supported by the targeted nature of the attacks and the use of sophisticated tools. However, the lack of direct evidence of data exfiltration introduces uncertainty.
- Hypothesis B: The campaign is a preparatory phase for potential future disruptive cyber operations against Singapore’s critical infrastructure. The deployment of rootkits and zero-day exploits supports this, but the absence of service disruption or data exfiltration contradicts this hypothesis.
- Assessment: Hypothesis A is currently better supported due to the targeted intelligence-gathering nature of the campaign and the absence of immediate disruptive actions. Indicators that could shift this judgment include evidence of data exfiltration or changes in the operational tempo of UNC3886.
3. Key Assumptions and Red Flags
- Assumptions: UNC3886 is state-sponsored; the primary goal is intelligence gathering; Singapore’s telcos are critical targets due to their strategic importance.
- Information Gaps: Specific details of the zero-day exploit; extent of data accessed by UNC3886; potential links between UNC3886 and other threat actors.
- Bias & Deception Risks: Potential bias in attributing the attack to China; reliance on open-source intelligence that may be incomplete or manipulated.
4. Implications and Strategic Risks
This development could exacerbate tensions between Singapore and China, impacting diplomatic relations and regional stability. The campaign underscores the vulnerability of critical infrastructure to sophisticated cyber threats.
- Political / Geopolitical: Potential diplomatic friction between Singapore and China, influencing regional security dynamics.
- Security / Counter-Terrorism: Increased vigilance and cybersecurity measures in Singapore, potential for retaliatory or preemptive cyber actions.
- Cyber / Information Space: Heightened awareness of cyber threats to critical infrastructure, potential for increased cyber defense collaboration.
- Economic / Social: Limited immediate economic impact, but potential long-term effects on investor confidence in Singapore’s cybersecurity resilience.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring and threat intelligence sharing among regional partners; conduct thorough forensic analysis of affected systems.
- Medium-Term Posture (1–12 months): Strengthen cybersecurity frameworks and incident response capabilities; engage in diplomatic dialogue with China to address cyber concerns.
- Scenario Outlook:
- Best: Improved cybersecurity collaboration and reduced tensions with China.
- Worst: Escalation of cyber operations leading to regional instability.
- Most-Likely: Continued low-level cyber espionage with periodic diplomatic engagements.
6. Key Individuals and Entities
- UNC3886
- Cyber Security Agency of Singapore (CSA)
- M1
- SIMBA Telecom
- Singtel
- StarHub
- K. Shanmugam (Coordinating Minister for National Security, Singapore)
- Sygnia
7. Thematic Tags
cybersecurity, cyber-espionage, telecommunications, China, Singapore, advanced persistent threat, regional security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us