Reliance Global Group to Acquire Controlling Interest in Post-Quantum Cybersecurity Firm Enquantum
Published on: 2026-02-09
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Reliance Global Group Signs Definitive Agreement to Acquire Controlling Stake in Post-Quantum Cybersecurity Company Enquantum
1. BLUF (Bottom Line Up Front)
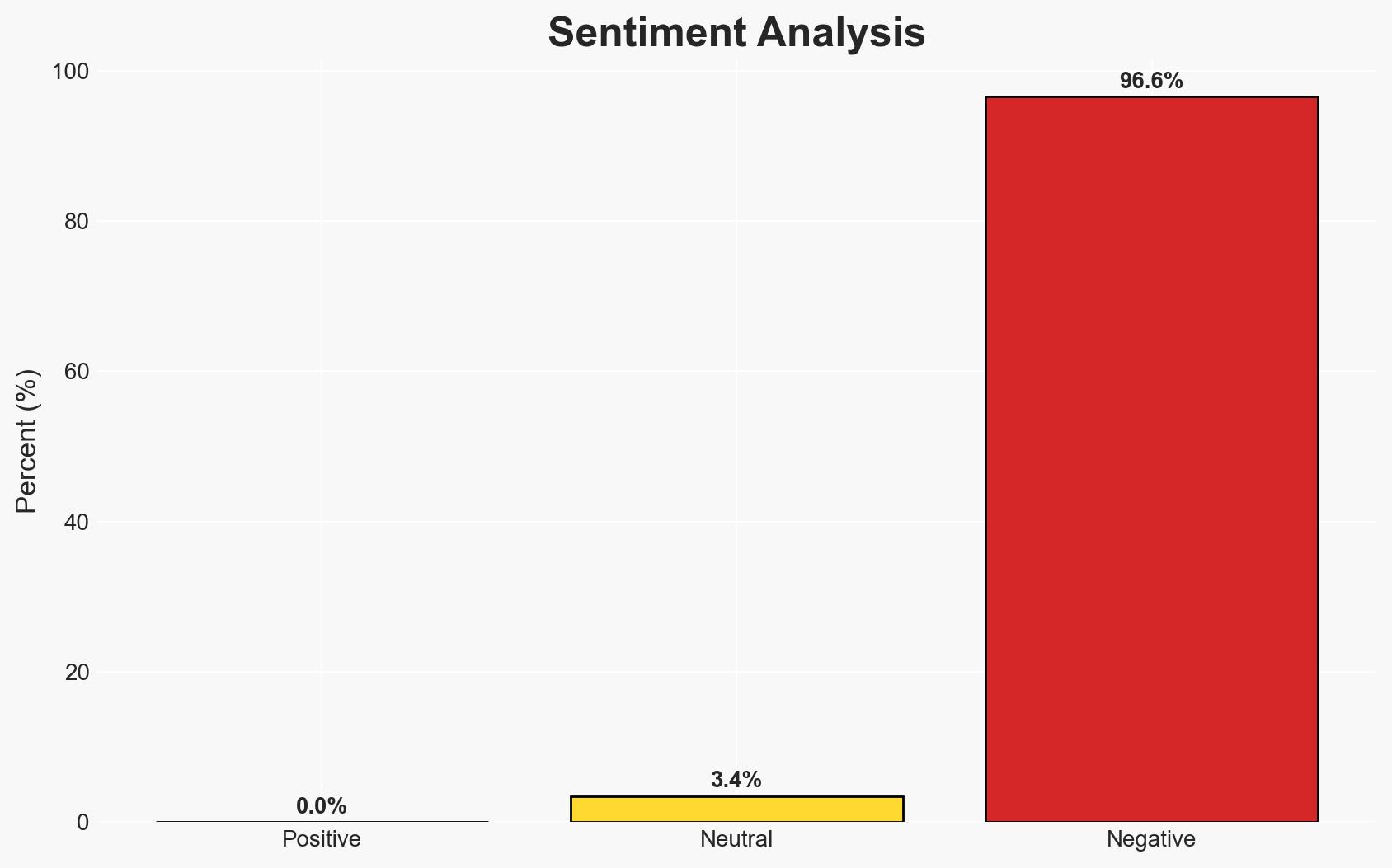
Reliance Global Group’s acquisition of a controlling stake in Enquantum positions it strategically in the emerging post-quantum cybersecurity market, potentially enhancing its influence across sectors reliant on cryptographic security. This move is likely driven by the anticipated shift in global cybersecurity standards due to advancements in quantum computing. The overall confidence level in this assessment is moderate, given the ongoing nature of the acquisition and incomplete information on Enquantum’s capabilities.
2. Competing Hypotheses
- Hypothesis A: Reliance’s acquisition of Enquantum is primarily motivated by the strategic need to secure a foothold in the post-quantum cybersecurity market, anticipating a significant shift in encryption standards. This is supported by the timing of the acquisition and the company’s Scale51 strategy. However, the full capabilities and market readiness of Enquantum remain uncertain.
- Hypothesis B: The acquisition is driven more by financial incentives and speculative investment in emerging technology rather than immediate strategic needs. This hypothesis is less supported due to the explicit focus on post-quantum security needs articulated by Reliance, though it cannot be entirely dismissed without further financial analysis.
- Assessment: Hypothesis A is currently better supported, given the explicit statements regarding strategic alignment with post-quantum security needs and the structured acquisition strategy. Indicators such as successful milestone achievements by Enquantum could further validate this hypothesis.
3. Key Assumptions and Red Flags
- Assumptions: Reliance has accurately assessed the market potential and technological capabilities of Enquantum; quantum computing advancements will necessitate a shift in cybersecurity standards; Enquantum can meet the operational milestones set by Reliance.
- Information Gaps: Detailed information on Enquantum’s current technological capabilities and market position; specifics on the operational and commercialization milestones required for the acquisition.
- Bias & Deception Risks: Potential overestimation of quantum computing threats by Reliance; reliance on Enquantum’s self-reported capabilities and market potential; possible financial motivations overshadowing strategic ones.
4. Implications and Strategic Risks
This acquisition could significantly impact the cybersecurity landscape, particularly in sectors vulnerable to quantum computing threats. The strategic move may prompt similar acquisitions or investments by competitors.
- Political / Geopolitical: Potential influence on national cybersecurity policies and international standards for post-quantum encryption.
- Security / Counter-Terrorism: Enhanced capabilities in protecting critical infrastructure from emerging quantum threats.
- Cyber / Information Space: Increased focus on developing and deploying post-quantum cryptographic solutions.
- Economic / Social: Potential economic benefits from leading in a new technology sector, but also risks if the technology does not meet expectations.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor the completion of the acquisition and initial integration steps; assess Enquantum’s technological capabilities and market position.
- Medium-Term Posture (1–12 months): Develop partnerships with other technology firms and research institutions to enhance post-quantum capabilities; invest in workforce training for post-quantum security.
- Scenario Outlook:
- Best: Successful integration and market leadership in post-quantum security.
- Worst: Failure to meet operational milestones, leading to financial losses and strategic setbacks.
- Most-Likely: Gradual integration with moderate success in achieving strategic objectives, contingent on technological advancements.
6. Key Individuals and Entities
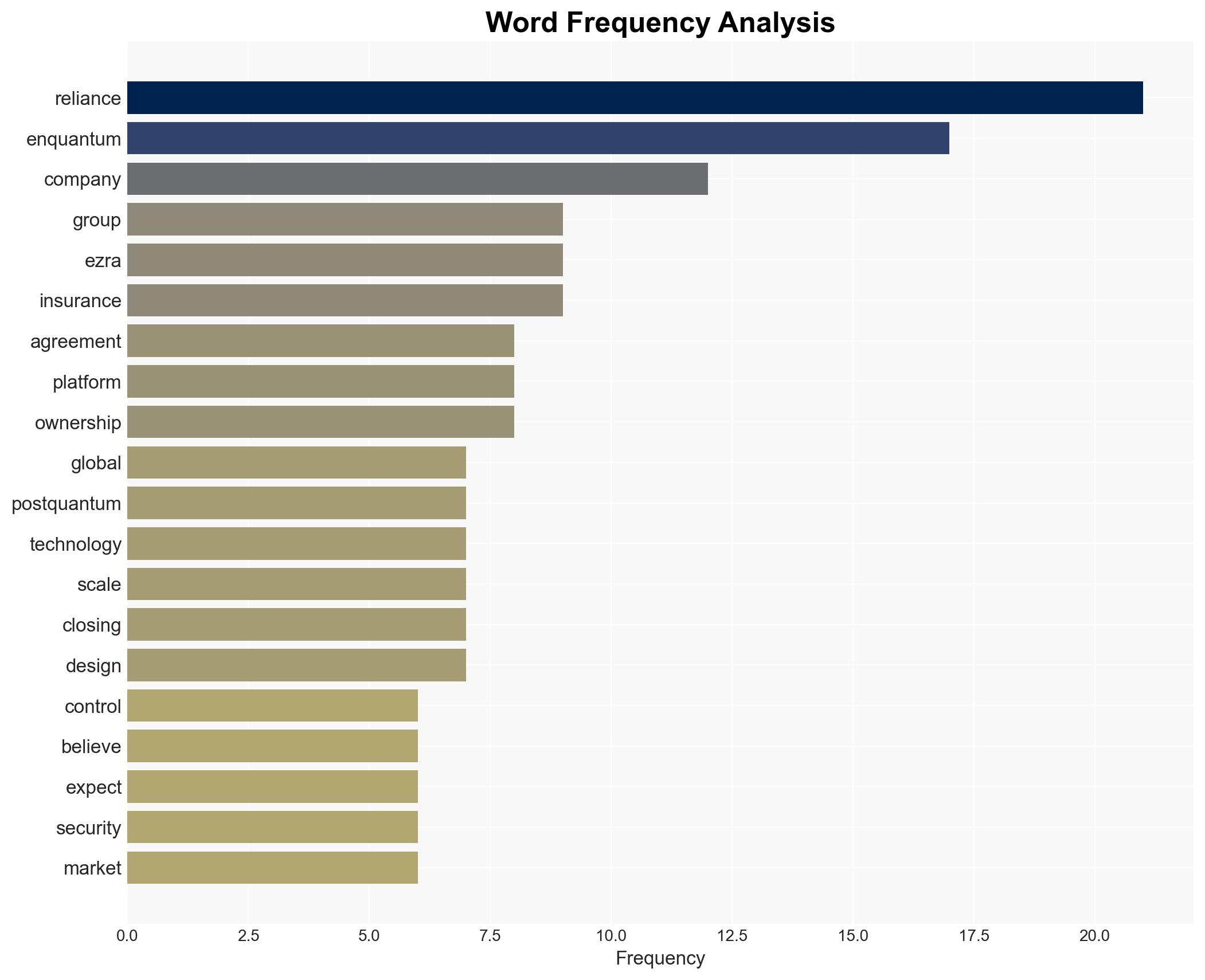
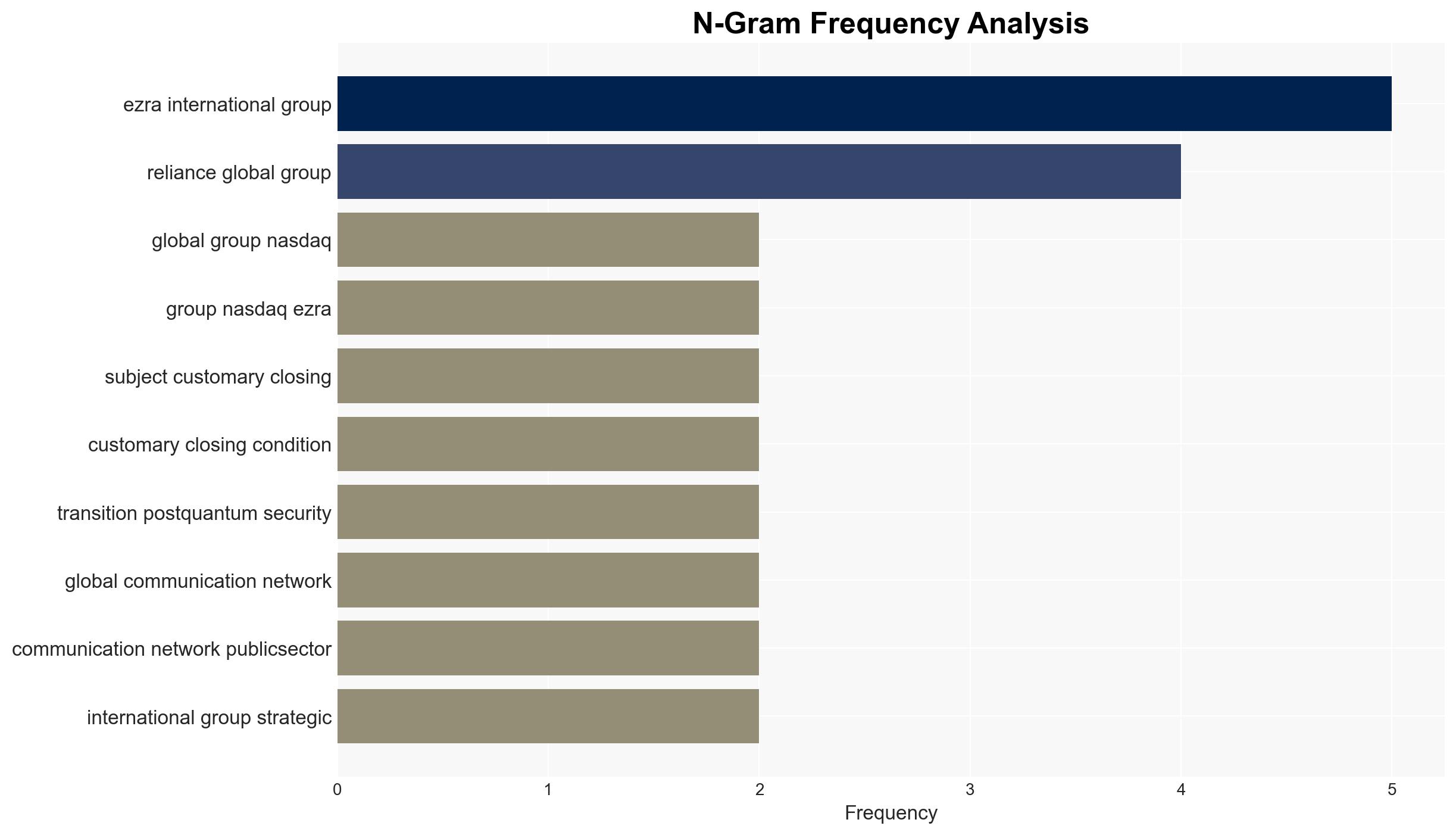
- Reliance Global Group
- Enquantum Ltd.
- EZRA International Group
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, post-quantum cryptography, strategic acquisition, quantum computing, technology investment, encryption standards
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
- Narrative Pattern Analysis: Deconstruct and track propaganda or influence narratives.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us