Criminal IP Partners with IBM QRadar to Enhance Real-Time Threat Intelligence Integration for Security Operat…
Published on: 2026-02-09
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
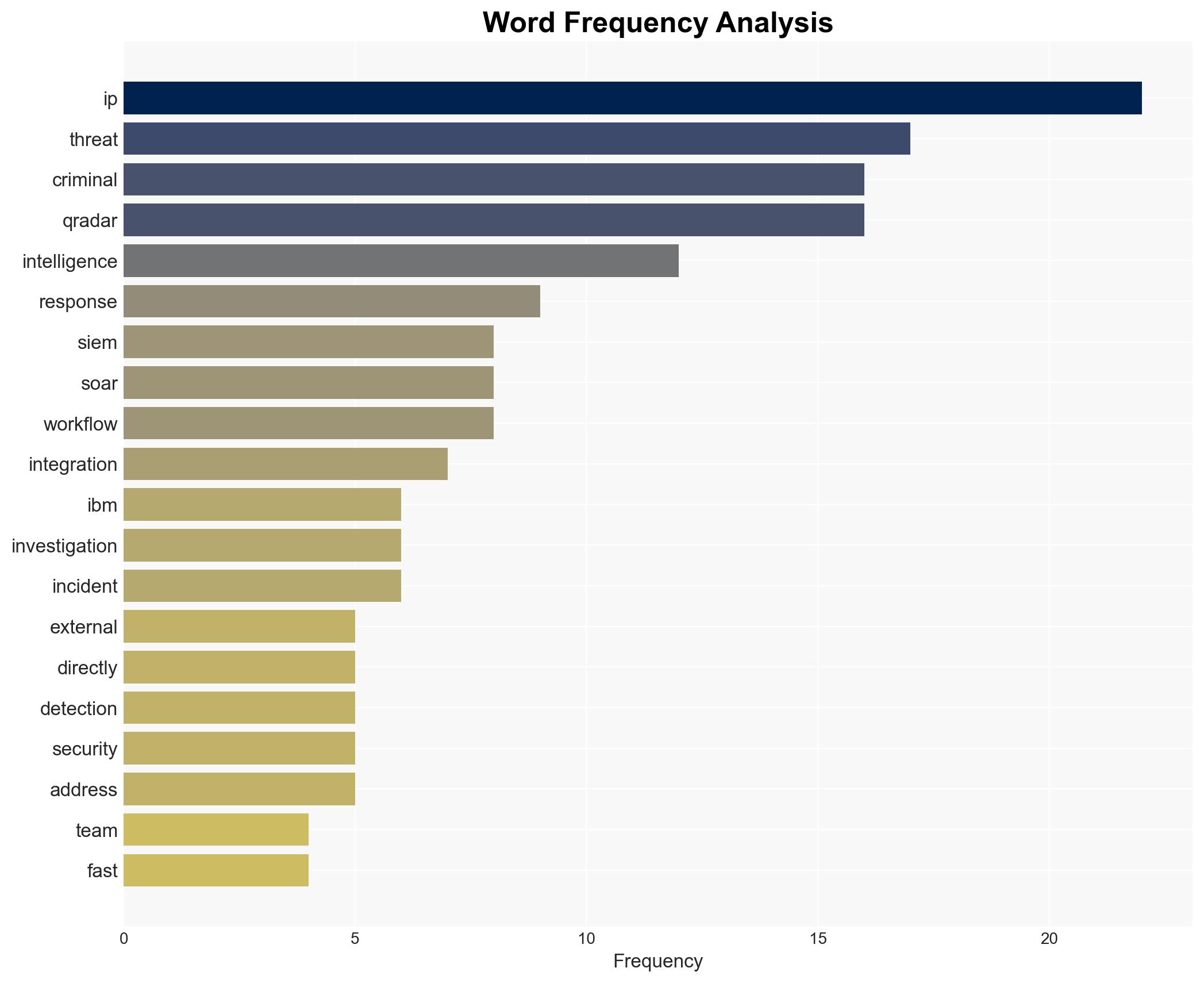
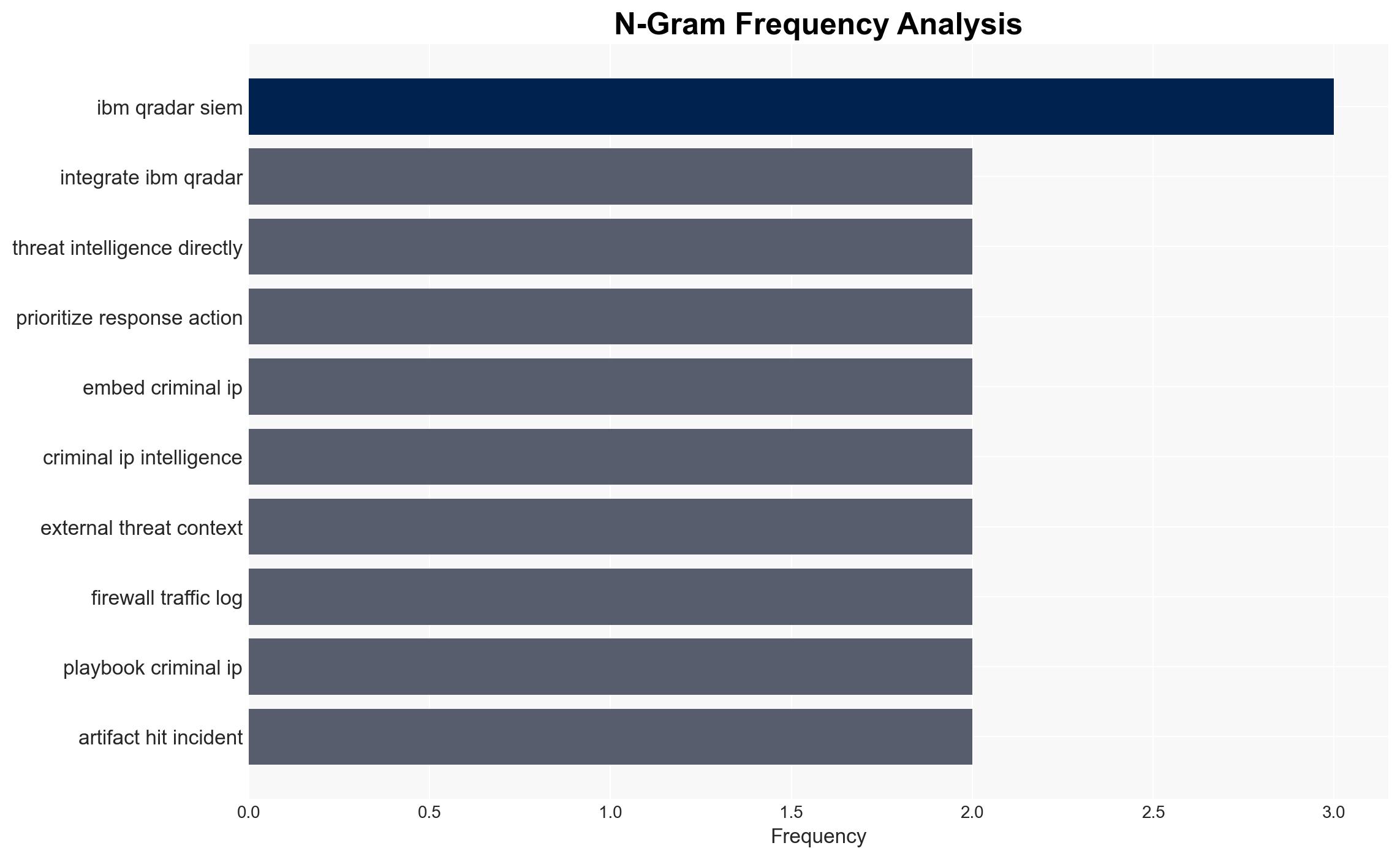
Intelligence Report: Criminal IP Integrates with IBM QRadar to Deliver Real-Time Threat Intelligence Across SIEM and SOAR
1. BLUF (Bottom Line Up Front)
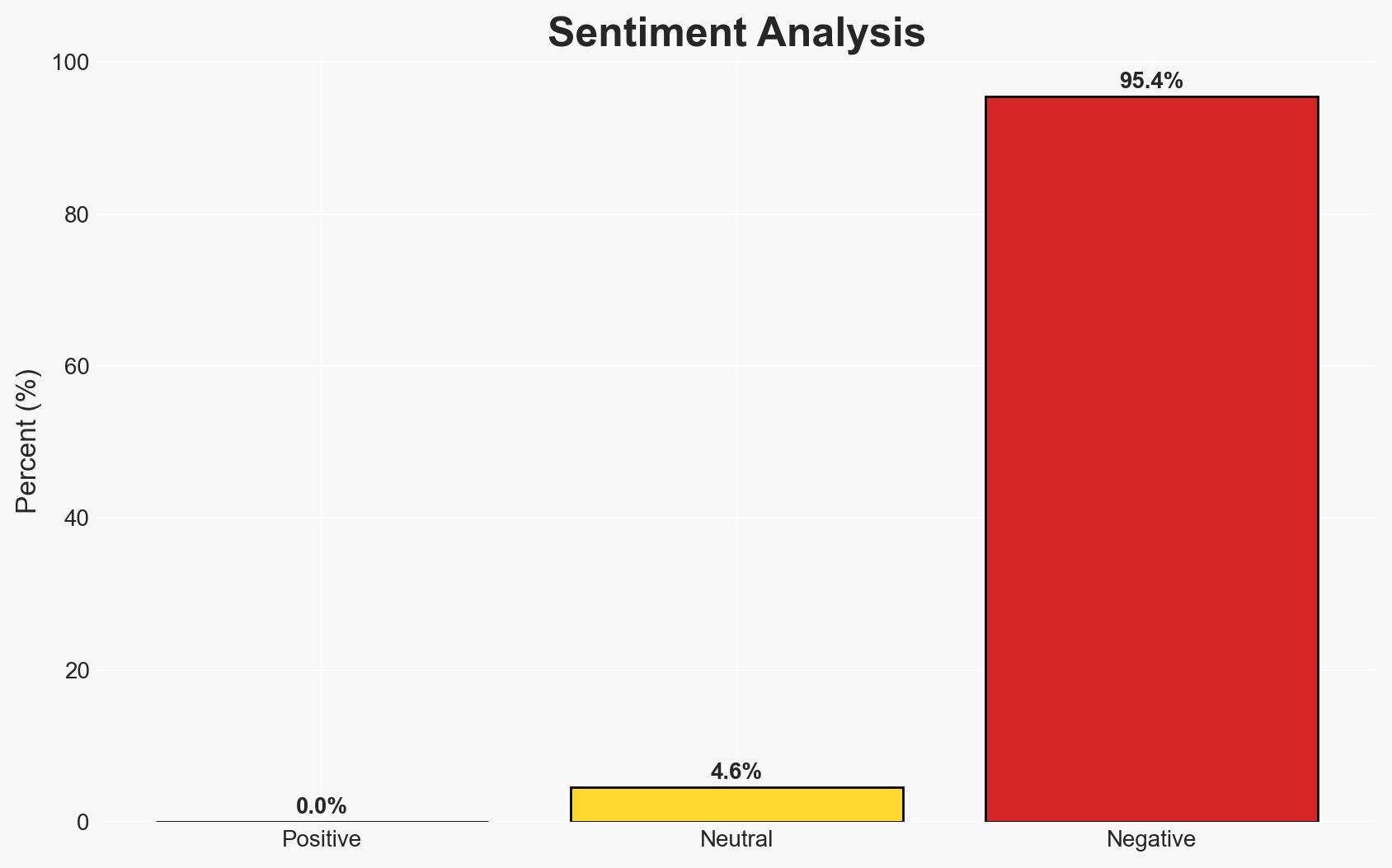
The integration of Criminal IP with IBM QRadar enhances real-time threat intelligence capabilities for security operations centers (SOCs), potentially improving incident response times and accuracy. This development primarily affects enterprises and public-sector organizations utilizing QRadar for security monitoring. The overall confidence level in this assessment is moderate, given the current information available.
2. Competing Hypotheses
- Hypothesis A: The integration will significantly improve SOC efficiency and threat response times by providing real-time threat intelligence and streamlined workflows. This is supported by the enhanced capabilities described, but lacks empirical performance data.
- Hypothesis B: The integration will have limited impact on SOC efficiency due to potential integration challenges or data overload. This hypothesis considers typical integration issues but lacks direct evidence from the current integration.
- Assessment: Hypothesis A is currently better supported due to the detailed description of the integration’s capabilities and benefits. Key indicators that could shift this judgment include empirical performance data post-integration and user feedback.
3. Key Assumptions and Red Flags
- Assumptions: The integration functions as described without significant technical issues. SOCs have the necessary infrastructure to support the integration. Users are adequately trained to utilize the new capabilities.
- Information Gaps: Lack of empirical data on the integration’s performance and user feedback post-implementation.
- Bias & Deception Risks: Potential bias from vendor-provided information emphasizing benefits without acknowledging possible limitations or challenges.
4. Implications and Strategic Risks
This integration could lead to improved threat detection and response capabilities, influencing broader cybersecurity strategies and investments.
- Political / Geopolitical: Enhanced cybersecurity capabilities could affect national security postures and international cyber cooperation.
- Security / Counter-Terrorism: Improved threat intelligence may enhance the ability to preempt and respond to cyber threats, including those from terrorist organizations.
- Cyber / Information Space: The integration may set a precedent for further collaborations between AI-driven threat intelligence platforms and SIEM/SOAR systems.
- Economic / Social: Increased cybersecurity efficiency could reduce economic losses from cyber incidents, but may also require additional investment in training and infrastructure.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor the integration’s rollout and gather initial user feedback. Evaluate the need for additional training or infrastructure upgrades.
- Medium-Term Posture (1–12 months): Develop partnerships with other threat intelligence platforms to enhance capabilities. Invest in ongoing training and capability development.
- Scenario Outlook:
- Best: Seamless integration leads to significant improvements in threat detection and response.
- Worst: Integration issues cause disruptions in SOC operations, leading to increased vulnerability.
- Most-Likely: Gradual improvement in SOC efficiency as integration challenges are resolved and users adapt.
6. Key Individuals and Entities
- Criminal IP (criminalip.io)
- IBM QRadar
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, threat intelligence, SIEM integration, SOC efficiency, AI-powered platforms, incident response, cyber defense
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us