Warlock ransomware gang exploits unpatched SmarterMail VM to breach SmarterTools network
Published on: 2026-02-09
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Hackers breach SmarterTools network using flaw in its own software
1. BLUF (Bottom Line Up Front)
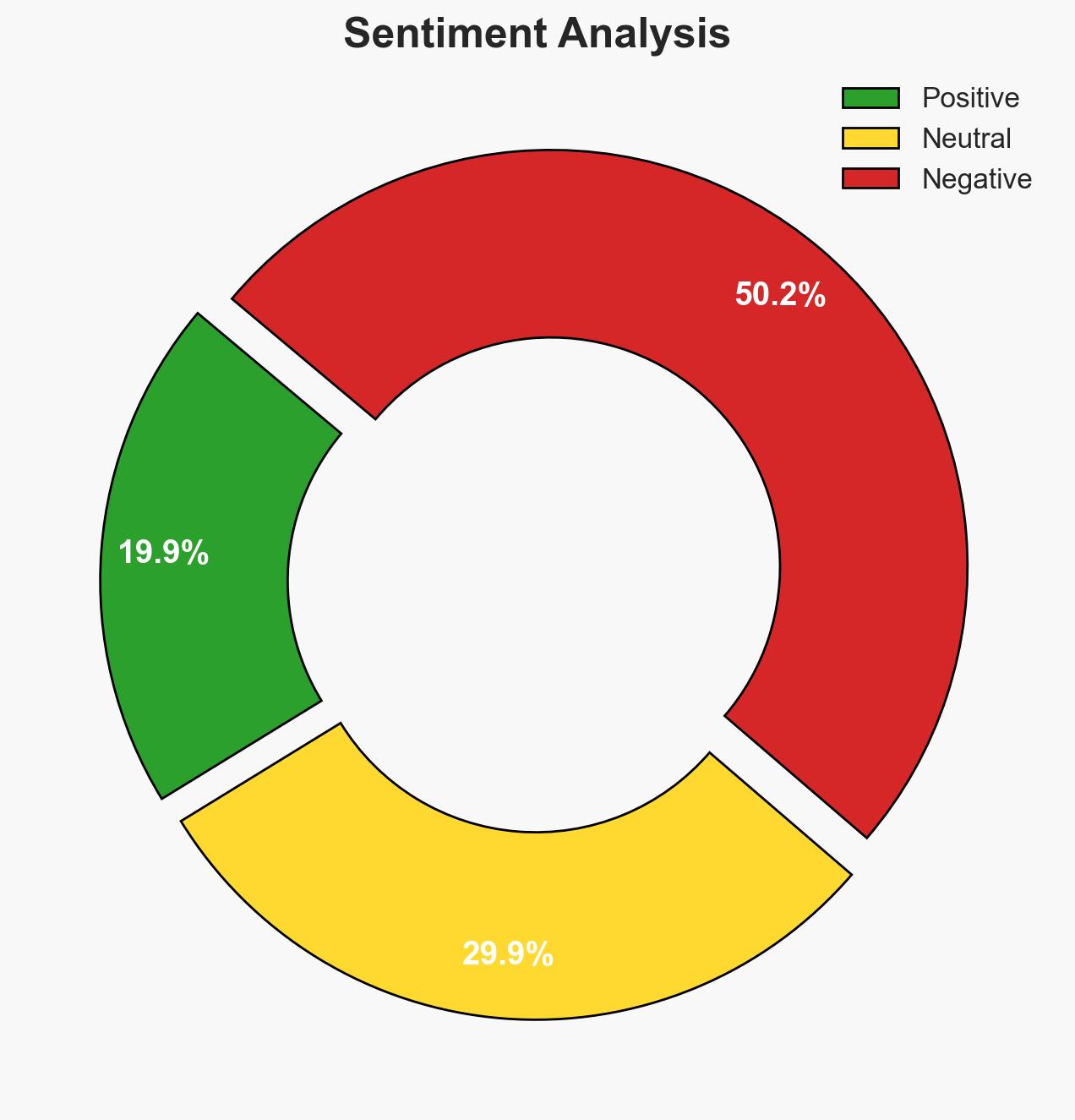
The Warlock ransomware gang exploited a vulnerability in SmarterMail software to breach SmarterTools’ network, compromising several Windows servers but not customer data. The attack is linked to a Chinese nation-state actor, Storm-2603. The breach highlights significant cybersecurity risks associated with software vulnerabilities and internal security lapses. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The breach was primarily opportunistic, leveraging a known vulnerability in SmarterMail due to a lack of patching on an isolated VM. This is supported by the fact that the breach exploited CVE-2026-23760, a known flaw, and the attackers used typical ransomware tactics.
- Hypothesis B: The breach was a targeted attack by a nation-state actor, Storm-2603, aiming to compromise SmarterTools for strategic gains. This is supported by the link to Storm-2603 and the sophisticated use of tools like Velociraptor for persistence.
- Assessment: Hypothesis B is currently better supported due to the involvement of Storm-2603, a known nation-state actor, and the use of advanced tools and techniques. Indicators that could shift this judgment include evidence of broader targeting patterns or geopolitical motivations.
3. Key Assumptions and Red Flags
- Assumptions: The breach was facilitated by a single unpatched VM; Storm-2603 is acting on behalf of a nation-state; Sentinel One effectively mitigated the ransomware’s final payload.
- Information Gaps: The full extent of the attackers’ objectives and whether other vulnerabilities were exploited remain unclear.
- Bias & Deception Risks: Potential bias in attributing the attack to Storm-2603 based on limited evidence; possible deception in attackers’ tactics to obscure true intent.
4. Implications and Strategic Risks
This breach underscores the persistent threat posed by nation-state actors exploiting software vulnerabilities. It may prompt increased scrutiny on software security practices and influence geopolitical tensions.
- Political / Geopolitical: Potential escalation in cyber tensions between China and affected nations.
- Security / Counter-Terrorism: Increased risk of similar attacks on other organizations using vulnerable software.
- Cyber / Information Space: Heightened awareness and potential regulatory actions on software security standards.
- Economic / Social: Potential economic impacts on SmarterTools and its clients due to reputational damage.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a thorough security audit of all systems, prioritize patching known vulnerabilities, and enhance monitoring for similar attack patterns.
- Medium-Term Posture (1–12 months): Develop partnerships for threat intelligence sharing, invest in advanced threat detection capabilities, and conduct regular security training for employees.
- Scenario Outlook: Best: Improved cybersecurity posture deters future attacks. Worst: Continued exploitation leads to significant data breaches. Most-Likely: Incremental improvements in security with occasional breaches.
6. Key Individuals and Entities
- Derek Curtis, Chief Commercial Officer, SmarterTools
- Warlock ransomware gang
- Storm-2603, Chinese nation-state actor
- ReliaQuest, cybersecurity company
- Sentinel One, security product provider
7. Thematic Tags
cybersecurity, ransomware, nation-state actors, software vulnerabilities, cyber defense, threat intelligence, information security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us