European Commission’s Mobile Systems Breached in Cyber Attack Linked to Ivanti Software Vulnerabilities
Published on: 2026-02-09
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Cyber Attack Hits European Commission Staff Mobile Systems
1. BLUF (Bottom Line Up Front)
The European Commission’s central mobile infrastructure was compromised due to critical vulnerabilities in Ivanti software, potentially exposing staff personal details. The breach was contained swiftly, but similar vulnerabilities have affected other European entities. The most likely hypothesis is that the attack was opportunistic, exploiting known software flaws. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
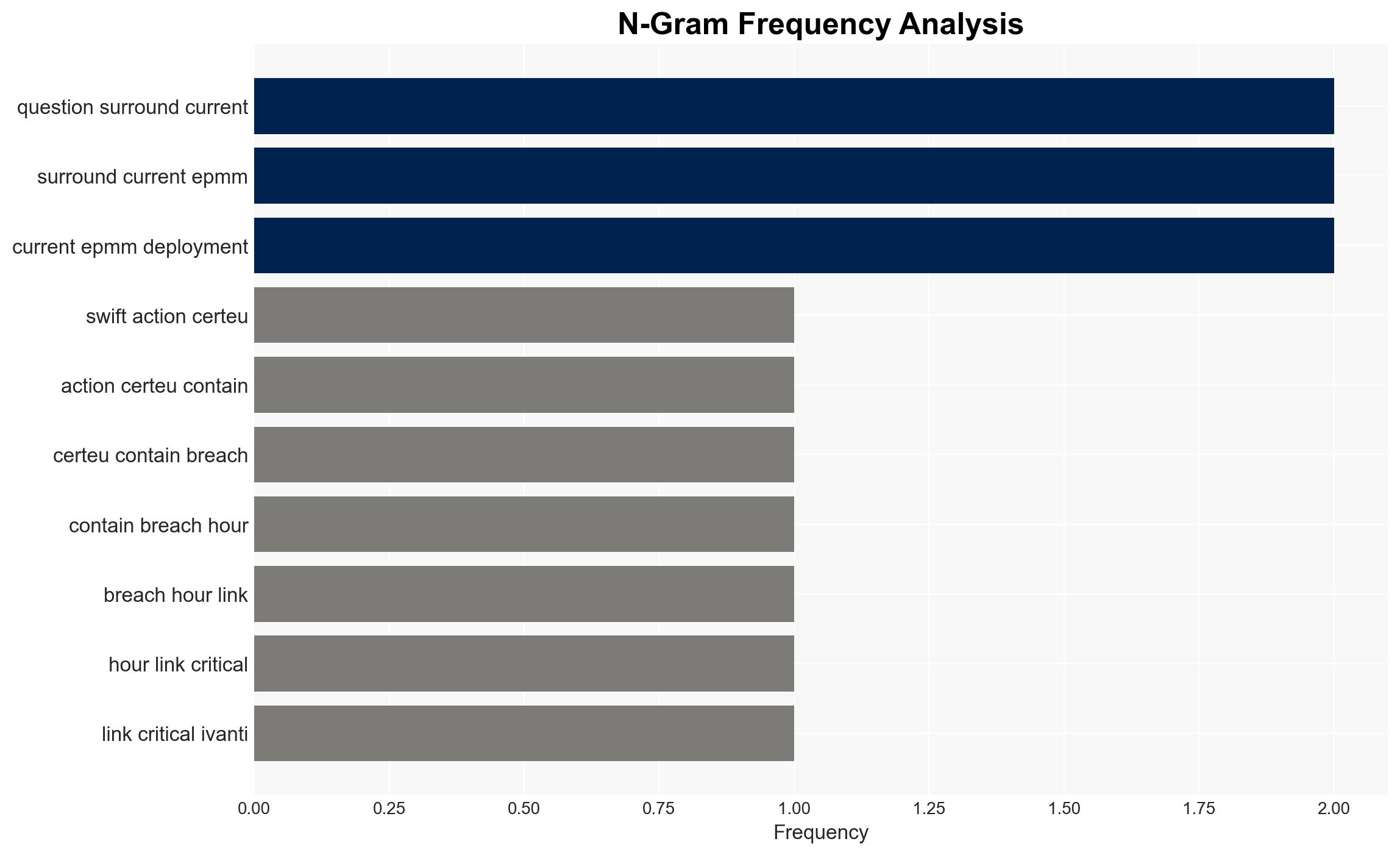
- Hypothesis A: The attack was opportunistic, exploiting known vulnerabilities in Ivanti software shortly after they were disclosed. This is supported by the timing of the attack and the nature of the vulnerabilities. However, the identity and motives of the attackers remain unclear.
- Hypothesis B: The attack was a targeted operation against the European Commission, possibly by a state-sponsored actor aiming to gather intelligence. This is less supported due to the lack of specific targeting indicators and the broader impact on other European entities.
- Assessment: Hypothesis A is currently better supported due to the timing and nature of the vulnerabilities. Key indicators that could shift this judgment include evidence of specific targeting or attribution to a known threat actor.
3. Key Assumptions and Red Flags
- Assumptions: The vulnerabilities were the primary vector for the breach; the attackers had no prior access to Commission systems; the breach was contained as reported.
- Information Gaps: Identity and motives of the attackers; full extent of data exposure; specific software used by the Commission.
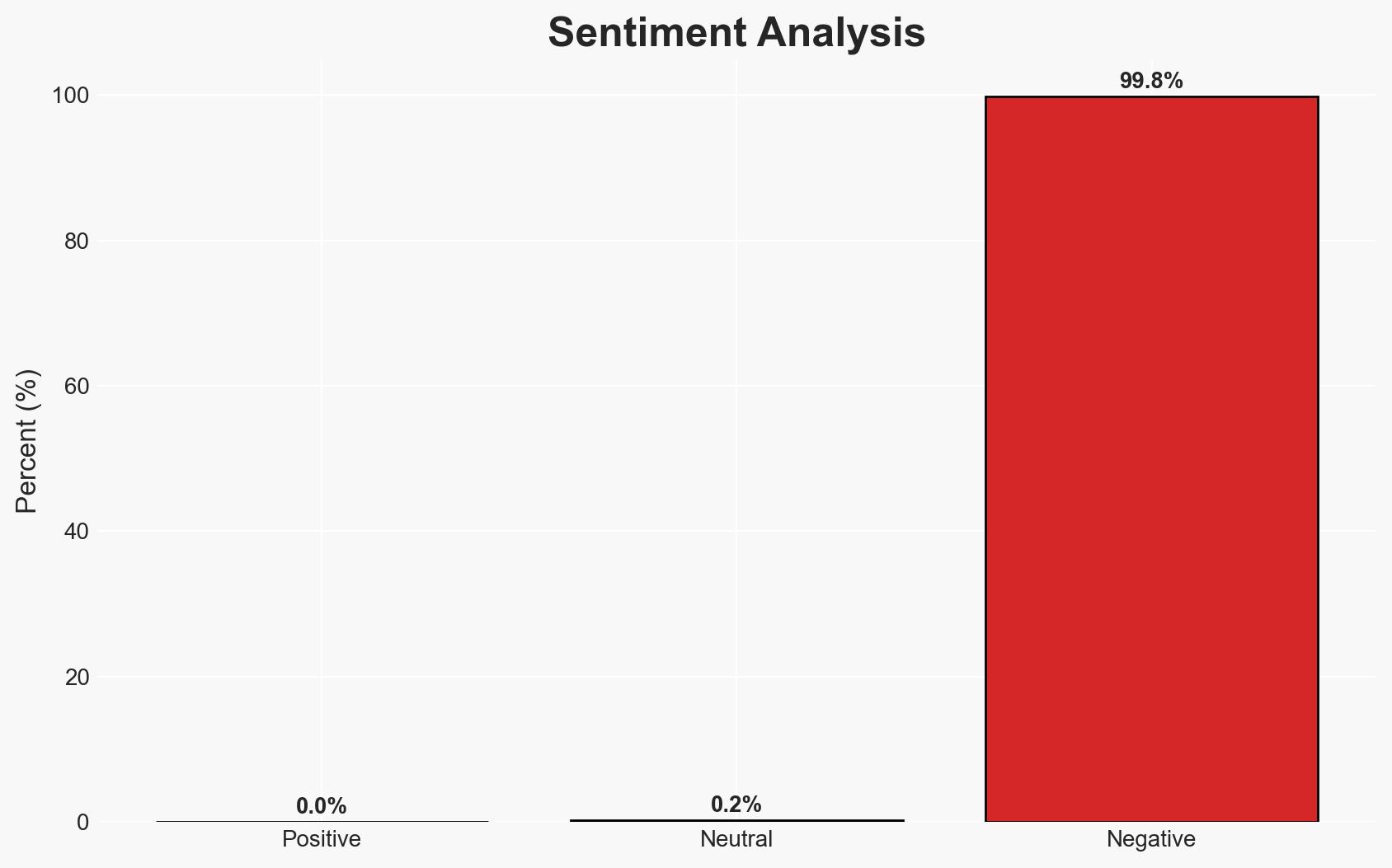
- Bias & Deception Risks: Potential underreporting of the breach’s impact; reliance on public statements from involved parties; possible misdirection by attackers regarding their true intent.
4. Implications and Strategic Risks
This incident highlights vulnerabilities in widely-used software and the rapid exploitation of disclosed flaws. It underscores the need for robust patch management and incident response capabilities.
- Political / Geopolitical: Increased scrutiny on EU cybersecurity policies; potential diplomatic tensions if state-sponsored involvement is suspected.
- Security / Counter-Terrorism: Heightened alert for similar attacks on other EU institutions; potential for increased cyber threat activity.
- Cyber / Information Space: Emphasizes the importance of timely vulnerability management and proactive threat intelligence sharing.
- Economic / Social: Potential erosion of trust in digital infrastructure; increased demand for cybersecurity solutions and services.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a thorough forensic analysis of the breach; enhance monitoring of related vulnerabilities; engage in information sharing with other affected entities.
- Medium-Term Posture (1–12 months): Strengthen patch management protocols; invest in cybersecurity training and awareness; develop partnerships for rapid threat intelligence exchange.
- Scenario Outlook:
- Best: No further incidents; vulnerabilities are patched, and systems are secured.
- Worst: Additional breaches occur, leading to significant data loss and operational disruption.
- Most-Likely: Continued attempts to exploit similar vulnerabilities, prompting ongoing cybersecurity enhancements.
6. Key Individuals and Entities
- European Commission
- Ivanti
- CERT-EU
- David Neeson, Deputy SOC Team Lead at Barrier Networks
- Valtori (Finnish government agency)
- Shadowserver
7. Thematic Tags
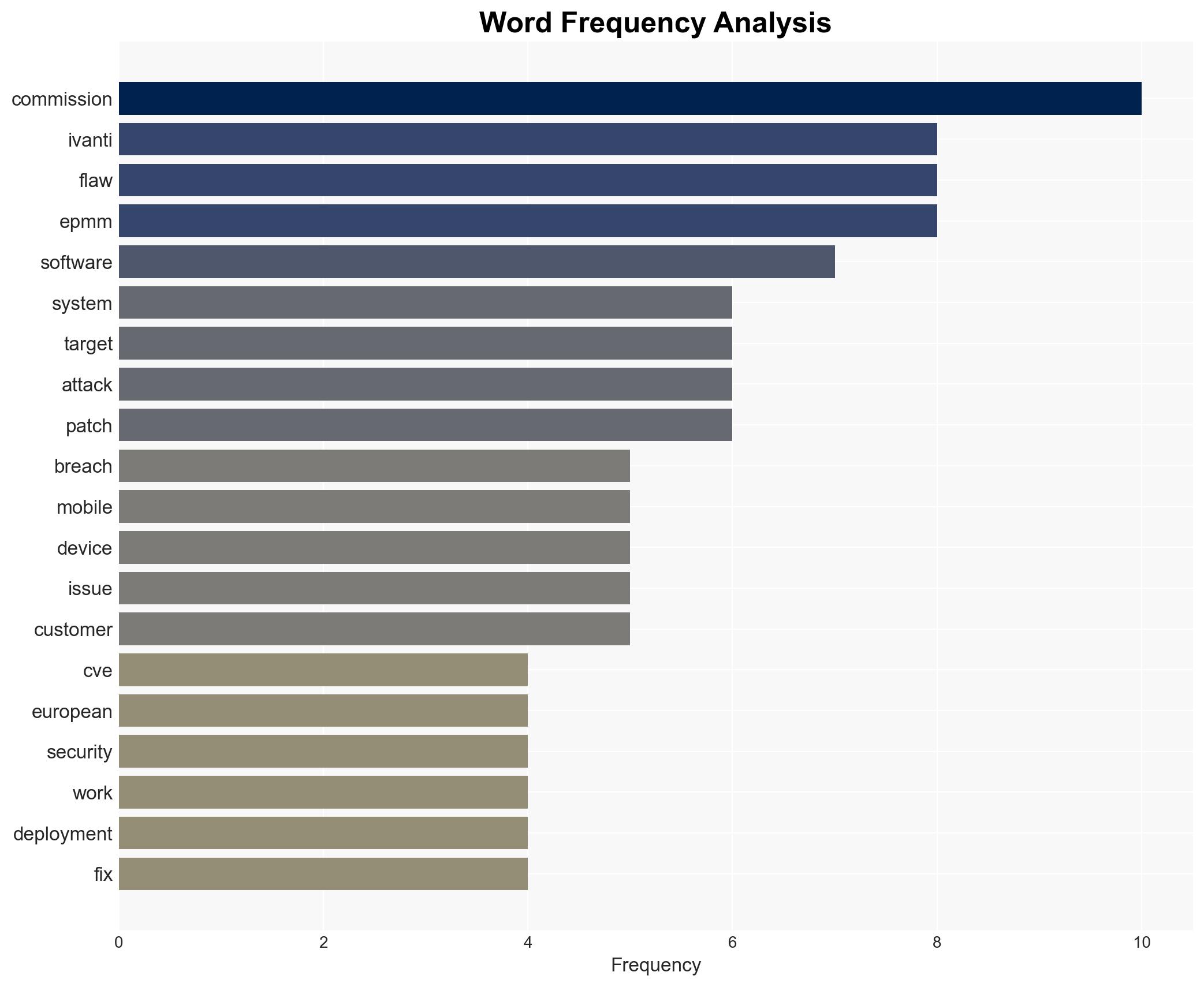
cybersecurity, vulnerability management, EU institutions, cyber-attack, information security, software flaws, incident response
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us