Senegal’s National ID Office Temporarily Closes Following Ransomware Attack and Data Breach
Published on: 2026-02-10
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Senegal shuts National ID office after ransomware attack
1. BLUF (Bottom Line Up Front)
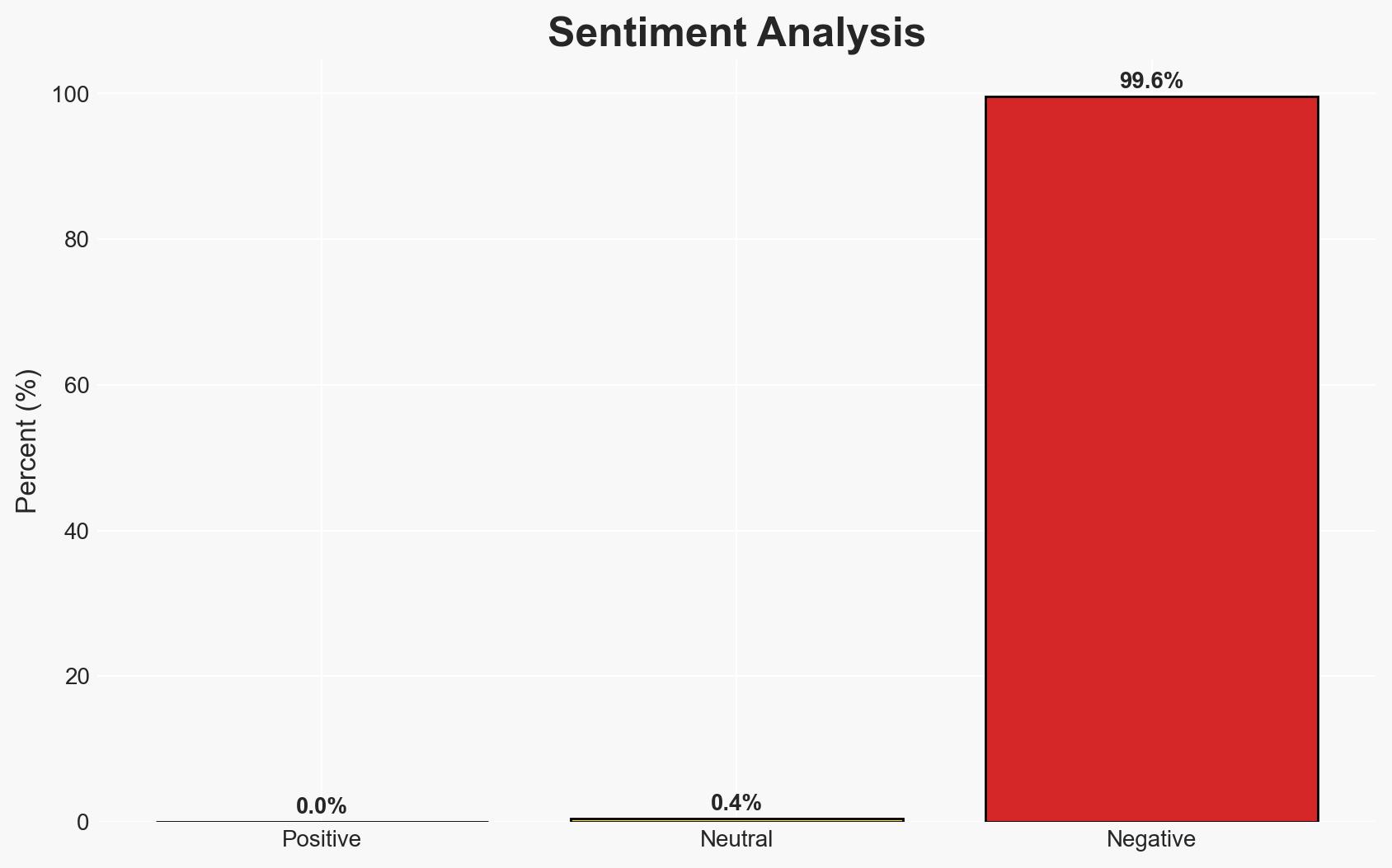
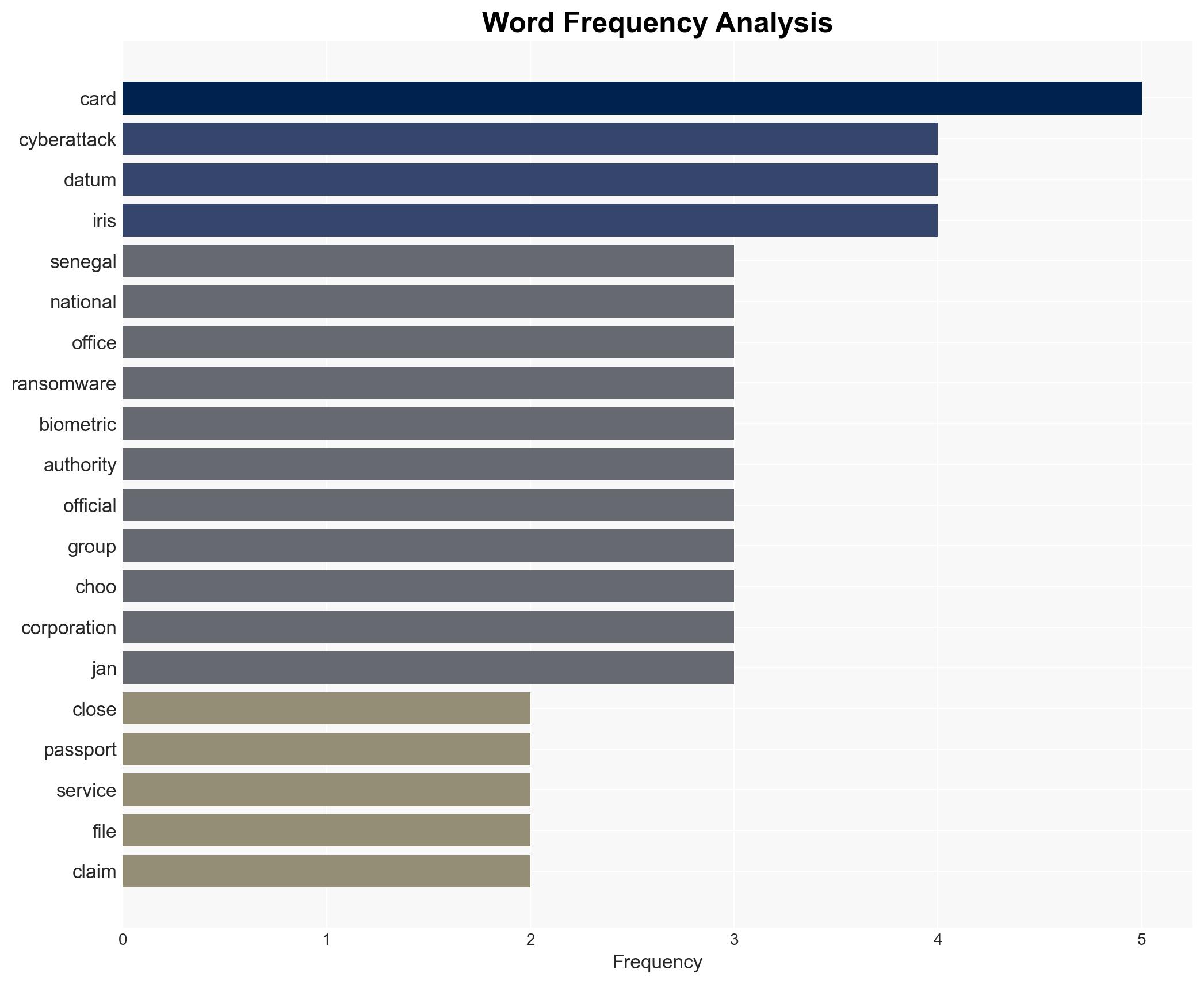
The ransomware attack on Senegal’s national ID office, attributed to the Green Blood Group, has disrupted critical identification services, impacting 19.5 million citizens. The breach coincides with a commercial dispute between Senegal and IRIS Corporation, raising suspicions of a possible link. The overall confidence in the assessment is moderate, given the current lack of definitive attribution and the potential for bias in reporting.
2. Competing Hypotheses
- Hypothesis A: The ransomware attack was orchestrated by the Green Blood Group independently of any external influence. Supporting evidence includes the group’s claim of responsibility and the publication of stolen data. Contradicting evidence is the timing of the attack amidst the commercial dispute with IRIS Corporation, which raises questions about potential motivations.
- Hypothesis B: The ransomware attack is linked to the ongoing commercial dispute between Senegal and IRIS Corporation. Supporting evidence includes the timing of the attack and IRIS Corporation’s immediate involvement in the response. However, there is no direct evidence linking the dispute to the cyberattack.
- Assessment: Hypothesis A is currently better supported due to the explicit claim by the Green Blood Group and the lack of direct evidence linking the attack to the commercial dispute. Future indicators that could shift this judgment include evidence of communication between the attackers and IRIS Corporation or further insights into the group’s motivations.
3. Key Assumptions and Red Flags
- Assumptions: The Green Blood Group is a genuine threat actor with the capability to execute sophisticated ransomware attacks. The data breach did not compromise the integrity of citizen data as claimed by authorities. IRIS Corporation’s involvement is limited to technical support and not operational influence.
- Information Gaps: The precise motivations and affiliations of the Green Blood Group. Detailed technical analysis of the breach to confirm the extent of data compromise. Any communications between IRIS Corporation and the attackers.
- Bias & Deception Risks: Potential bias in reporting due to the commercial dispute context. Deception indicators include the possibility of false flag operations or misattribution by the attackers.
4. Implications and Strategic Risks
This cyberattack could exacerbate existing tensions between Senegal and IRIS Corporation, potentially affecting future digital infrastructure projects. The incident highlights vulnerabilities in Senegal’s cyber defenses and could embolden other threat actors.
- Political / Geopolitical: Strained relations with IRIS Corporation could impact Senegal’s international partnerships and digital transformation efforts.
- Security / Counter-Terrorism: Increased cyber threat environment, necessitating heightened vigilance and improved cybersecurity measures.
- Cyber / Information Space: Potential for further cyberattacks targeting critical infrastructure and data integrity concerns.
- Economic / Social: Disruption of ID services may affect economic activities and social stability, particularly if prolonged.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a thorough forensic investigation to ascertain the full scope of the breach. Enhance cybersecurity measures and public communication to reassure citizens.
- Medium-Term Posture (1–12 months): Develop partnerships with international cybersecurity experts to bolster defenses. Review and update contractual and operational protocols with IRIS Corporation.
- Scenario Outlook:
- Best: Quick resolution of the breach with minimal data compromise and strengthened cyber defenses.
- Worst: Prolonged disruption and further attacks leading to significant data loss and public distrust.
- Most-Likely: Gradual restoration of services with ongoing cybersecurity improvements and diplomatic negotiations with IRIS Corporation.
6. Key Individuals and Entities
- Green Blood Group (ransomware group)
- IRIS Corporation (Malaysian firm involved in digital ID cards)
- Quik Saw Choo (Senior GM at IRIS Corporation)
- Directorate of File Automation (Senegalese government office)
7. Thematic Tags
cybersecurity, ransomware, national security, digital identity, international relations, data breach, cyber defense
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us