Cyber Group Bloody Wolf Launches Spear-Phishing Attacks on Uzbekistan and Russia Using NetSupport RAT
Published on: 2026-02-09
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Bloody Wolf Targets Uzbekistan Russia Using NetSupport RAT in Spear-Phishing Campaign
1. BLUF (Bottom Line Up Front)
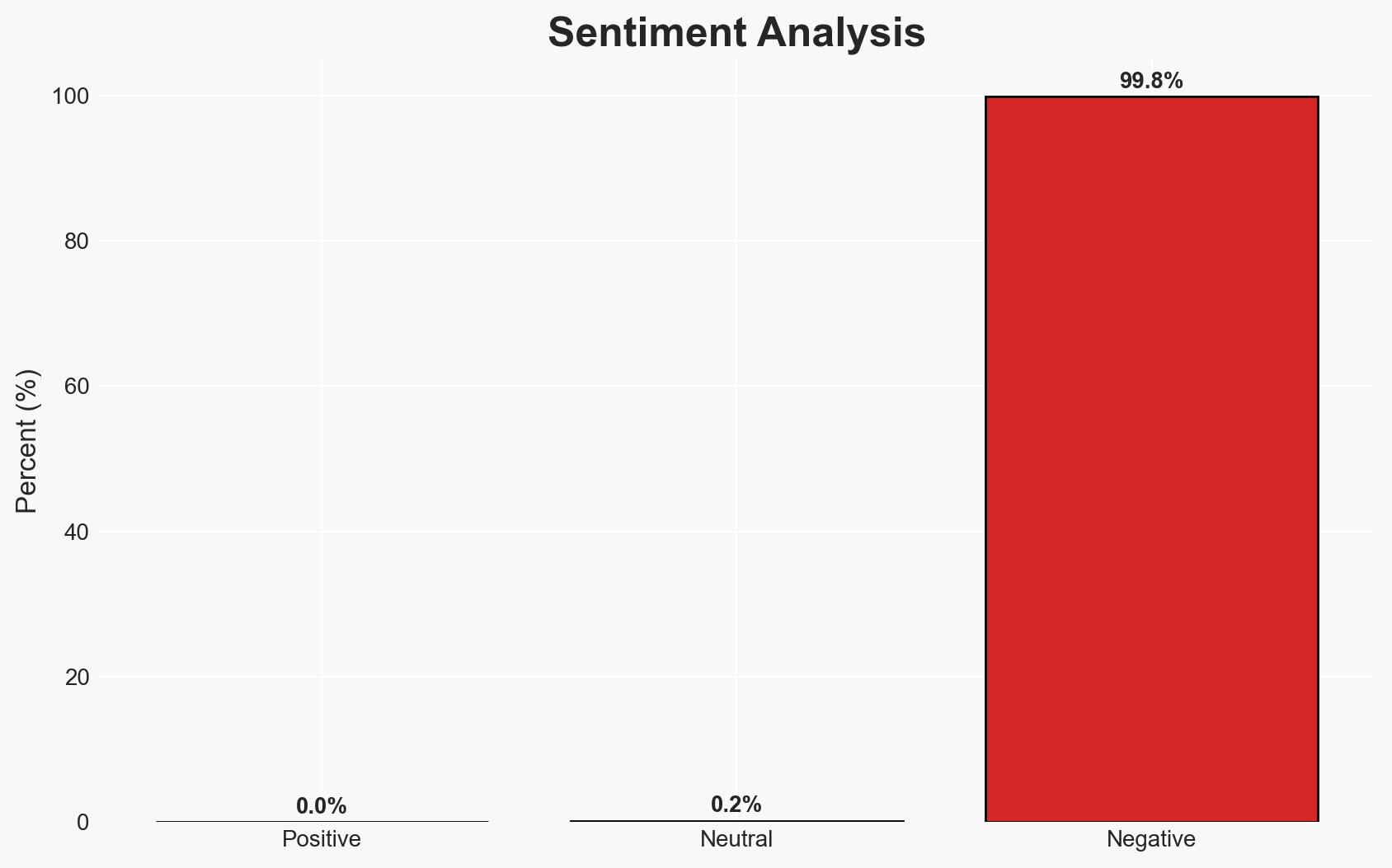
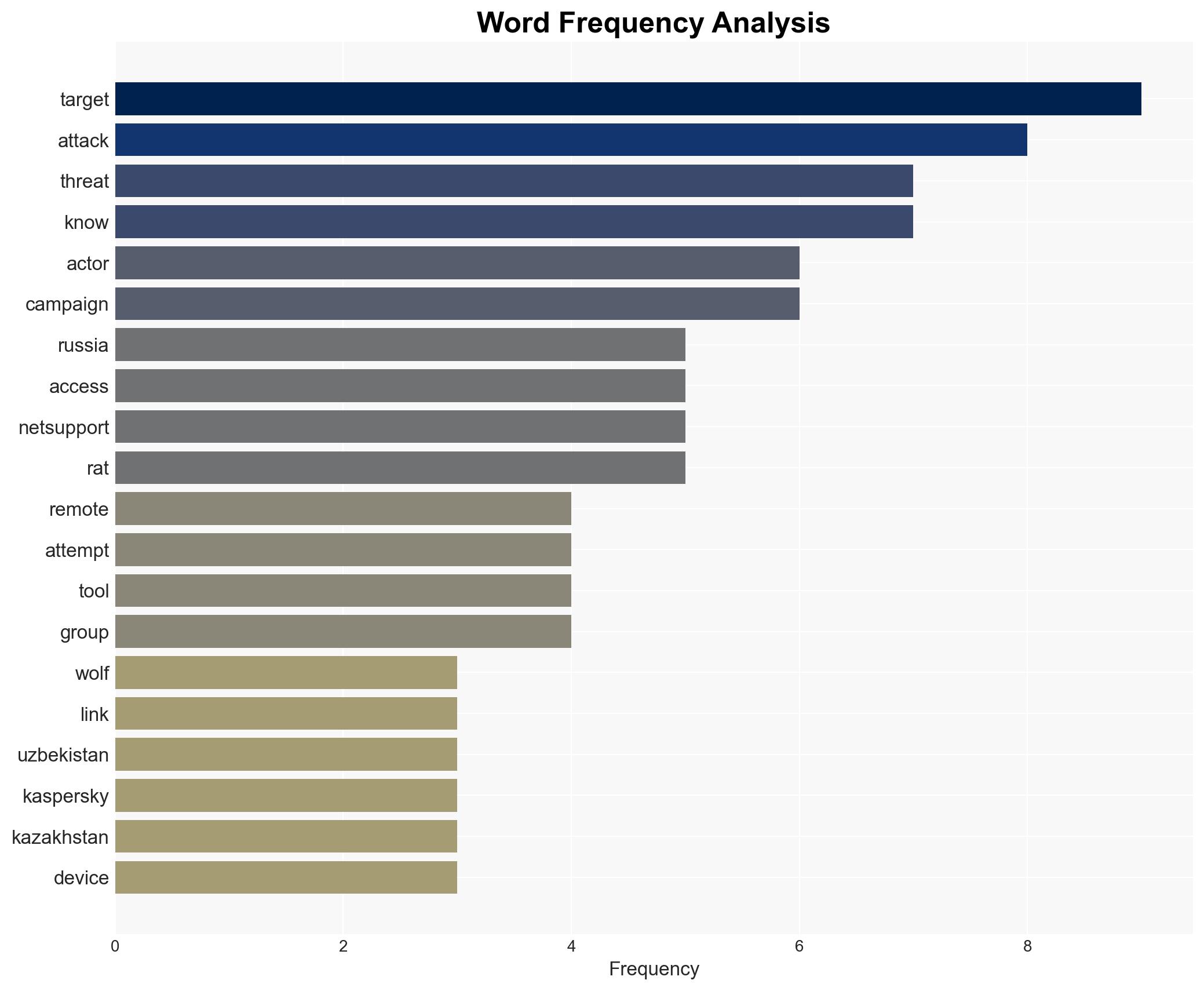
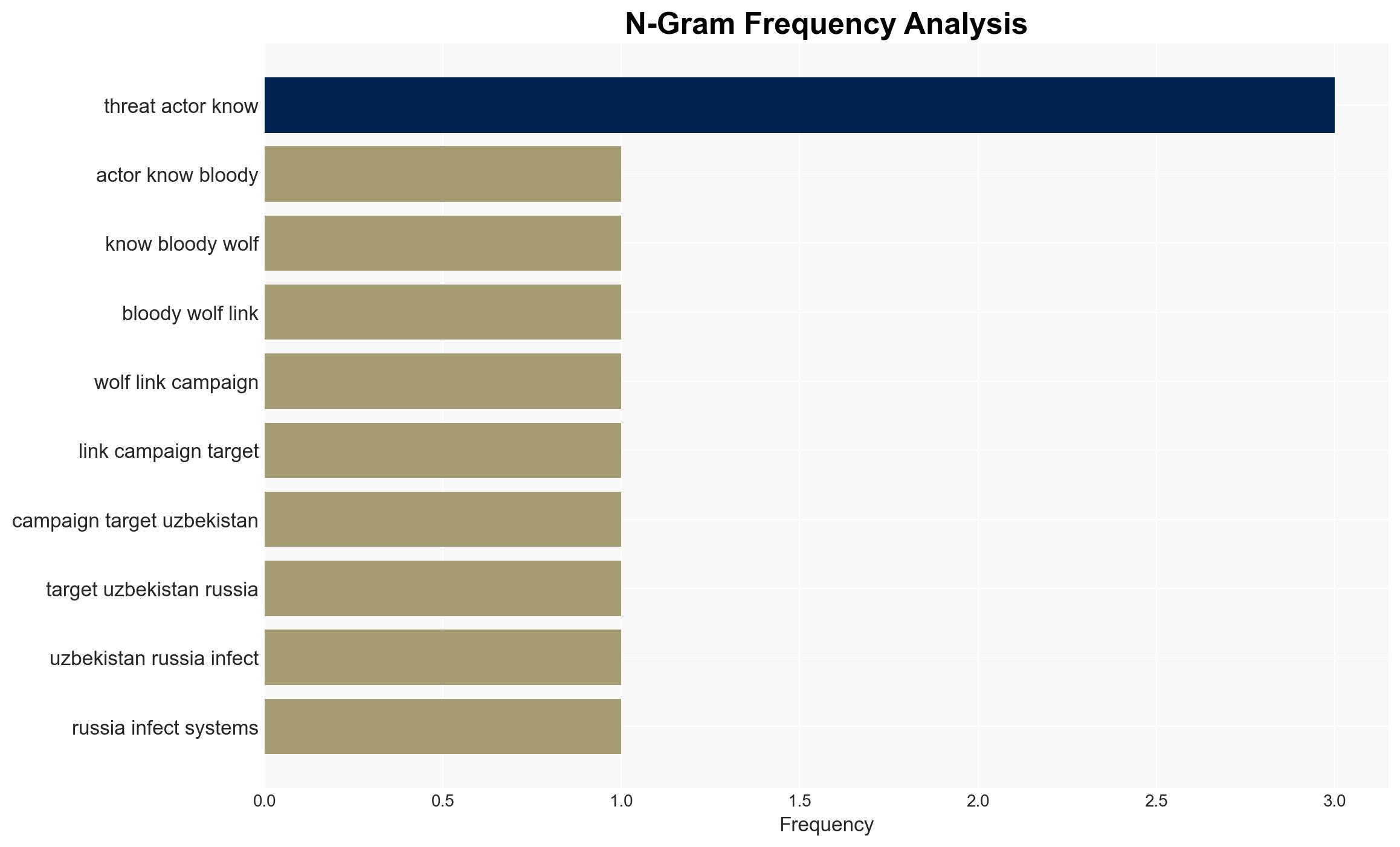
The cyber threat actor known as Bloody Wolf is conducting a spear-phishing campaign targeting Uzbekistan and Russia using the NetSupport RAT. The campaign primarily affects sectors such as manufacturing, finance, and IT, with potential motives of financial gain and cyber espionage. The operation’s sophistication and volume suggest a significant threat to regional cybersecurity. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: Bloody Wolf’s primary motive is financial gain, as indicated by targeting financial institutions and using RATs to potentially exfiltrate financial data. However, the use of RATs could also support espionage activities, creating uncertainty about the true intent.
- Hypothesis B: The campaign is primarily aimed at cyber espionage, leveraging NetSupport RAT to gain persistent access to sensitive systems. The financial targeting might be a cover or secondary objective. This hypothesis is supported by the strategic targeting of government and critical infrastructure sectors.
- Assessment: Hypothesis A is currently better supported due to explicit targeting of financial sectors and the historical pattern of similar threat actors. However, indicators such as expanded malware arsenals and targeting of governmental entities could shift this judgment towards espionage motives.
3. Key Assumptions and Red Flags
- Assumptions: The campaign’s primary motive is financial gain; NetSupport RAT is the main tool used for data exfiltration; Bloody Wolf operates independently without state sponsorship.
- Information Gaps: Lack of detailed attribution to specific individuals or groups; limited understanding of the full scope of targeted entities; insufficient data on the operational infrastructure supporting the campaign.
- Bias & Deception Risks: Potential bias from cybersecurity vendors emphasizing financial motives; risk of deception by the threat actor to obscure true objectives; reliance on open-source data may limit comprehensive understanding.
4. Implications and Strategic Risks
The campaign could evolve into a broader regional threat, potentially escalating tensions between affected nations and impacting international relations. The persistent threat to critical sectors may necessitate increased cybersecurity measures and international cooperation.
- Political / Geopolitical: Potential strain on diplomatic relations between targeted countries and perceived state sponsors of cyber activities.
- Security / Counter-Terrorism: Increased cybersecurity threats to critical infrastructure, necessitating enhanced defensive measures.
- Cyber / Information Space: Potential for broader cyber operations targeting additional sectors or countries; increased need for information sharing and cyber defense collaboration.
- Economic / Social: Disruption to financial and manufacturing sectors could lead to economic instability and reduced investor confidence in affected regions.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of phishing campaigns; strengthen cybersecurity protocols in targeted sectors; initiate information sharing with international partners.
- Medium-Term Posture (1–12 months): Develop resilience measures, including employee training and incident response capabilities; foster partnerships for intelligence sharing and joint cyber defense initiatives.
- Scenario Outlook:
- Best: Successful mitigation and disruption of the campaign, leading to reduced threat levels.
- Worst: Escalation of attacks with significant data breaches and economic impact.
- Most-Likely: Continued targeting with moderate success, prompting ongoing defensive efforts.
6. Key Individuals and Entities
- Bloody Wolf (Threat Actor)
- Kaspersky (Cybersecurity Vendor)
- Group-IB (Cybersecurity Vendor)
- Stan Ghouls (Moniker for Campaign)
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, cyber-espionage, financial crime, spear-phishing, remote access trojan, regional security, threat actor
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us