Malicious Outlook Add-In Discovered, Compromising Over 4,000 Microsoft Account Credentials
Published on: 2026-02-11
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: First Malicious Outlook Add-In Found Stealing 4000 Microsoft Credentials
1. BLUF (Bottom Line Up Front)
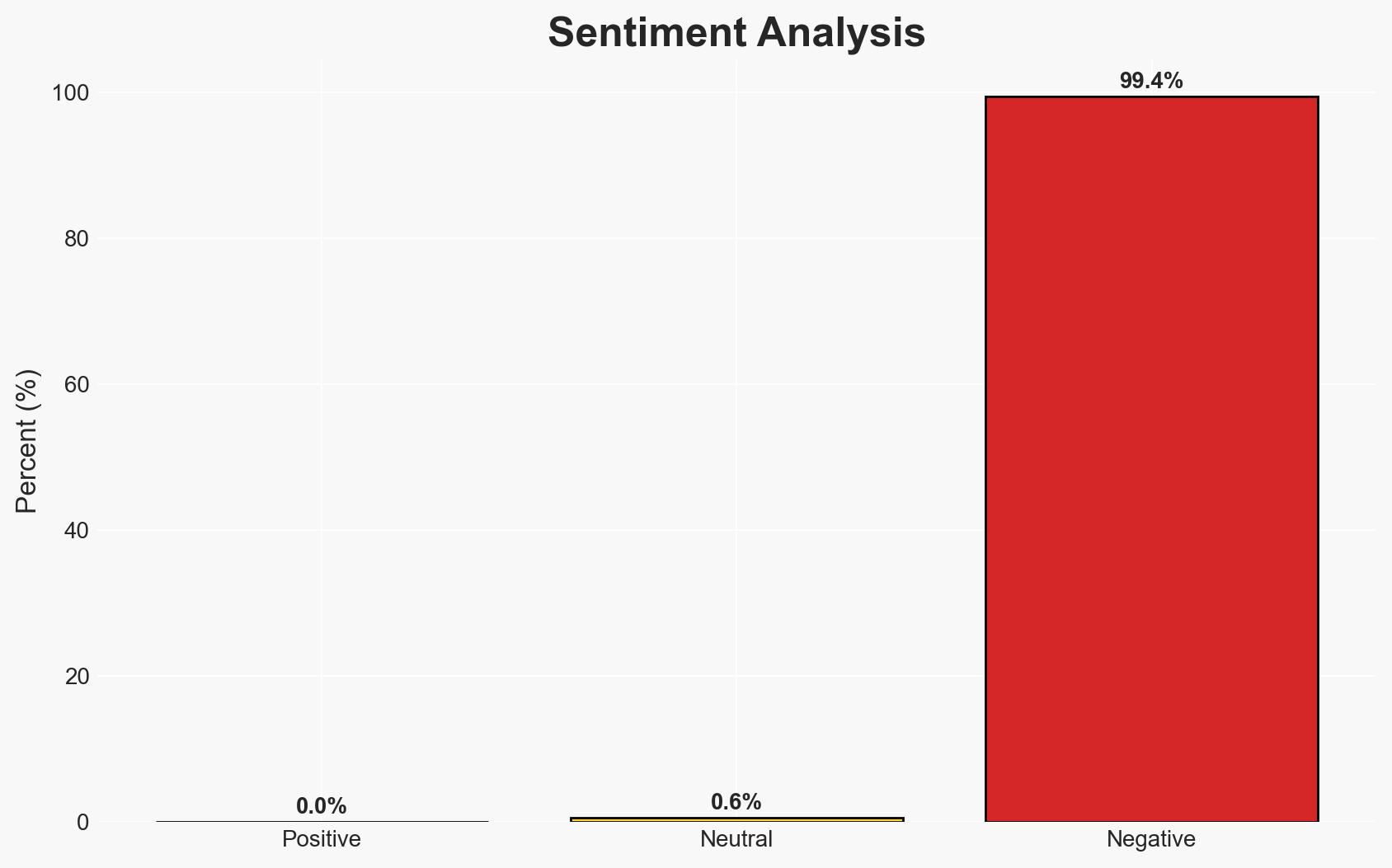
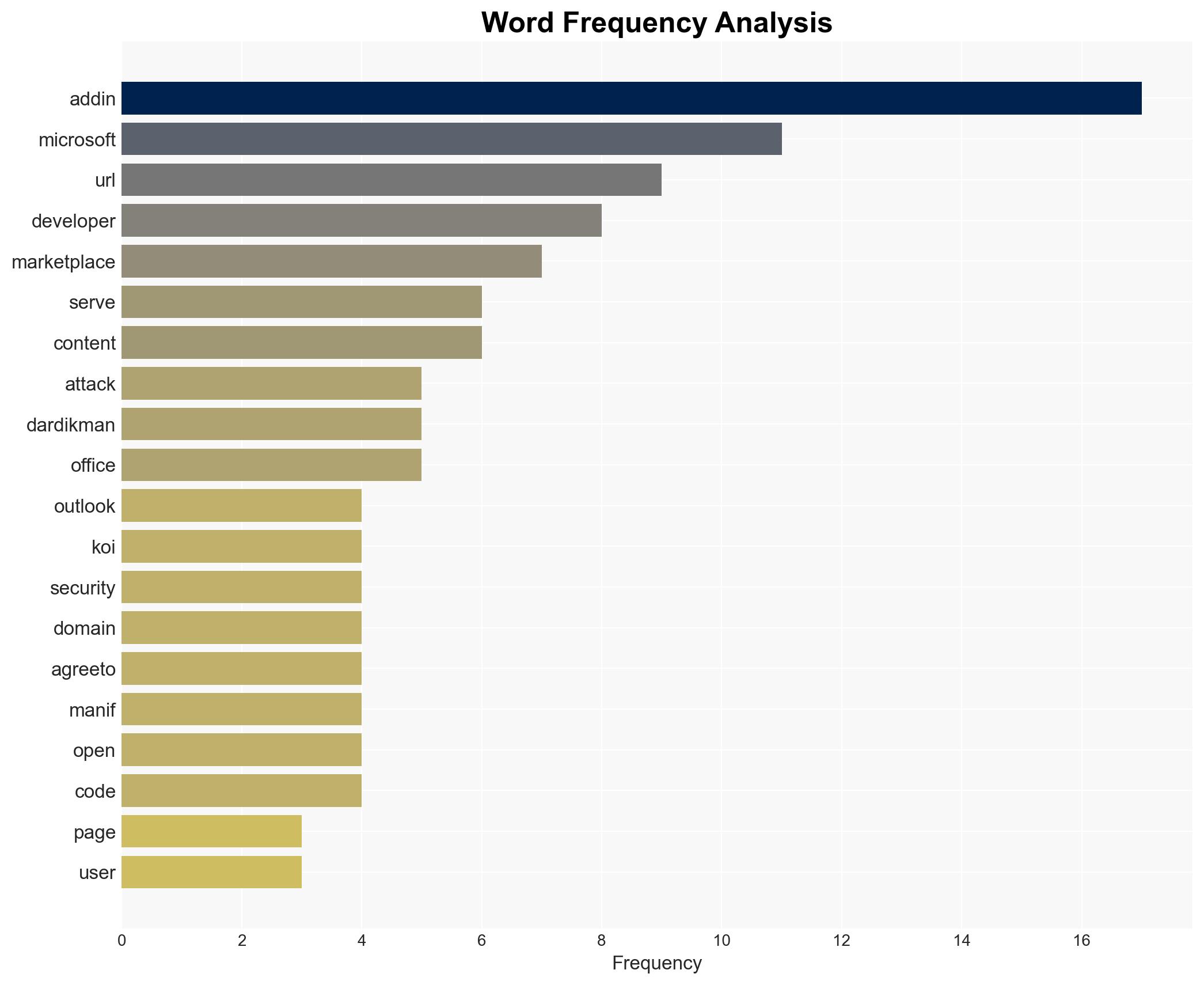
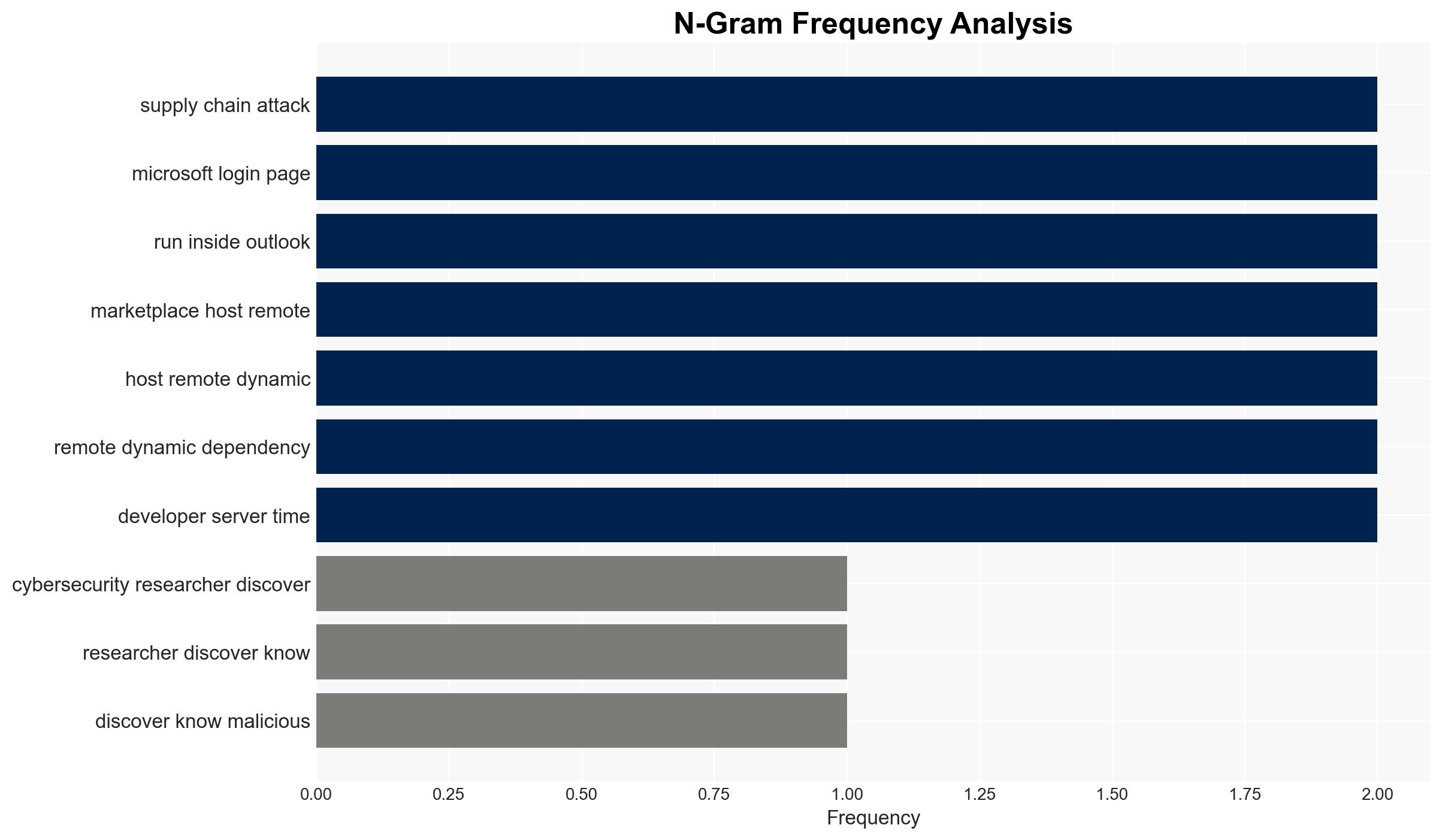
The discovery of a malicious Microsoft Outlook add-in, AgreeToSteal, marks a significant expansion in supply chain attack vectors, exploiting abandoned domains to steal over 4,000 credentials. This incident highlights vulnerabilities in trusted distribution channels, particularly within Microsoft’s ecosystem. The affected parties include users of the AgreeTo add-in and potentially broader Microsoft Outlook users. Overall confidence in this assessment is moderate due to the limited scope of the data provided.
2. Competing Hypotheses
- Hypothesis A: The attack was opportunistic, exploiting a known vulnerability in the management of abandoned domains within Microsoft’s add-in marketplace. This is supported by the fact that the domain was claimable after the developer’s inactivity, and the attack aligns with patterns seen in other software ecosystems. However, the identity and motivations of the attacker remain uncertain.
- Hypothesis B: The attack was part of a coordinated campaign targeting Microsoft users, potentially linked to a larger threat actor with specific objectives against Microsoft services. While the scale of credential theft suggests a targeted approach, there is no direct evidence linking this incident to broader campaigns.
- Assessment: Hypothesis A is currently better supported given the technical details and lack of broader context indicating a coordinated campaign. Key indicators that could shift this judgment include evidence of similar attacks on other platforms or identification of a threat actor with a history of targeting Microsoft services.
3. Key Assumptions and Red Flags
- Assumptions: The attack exploited a gap in Microsoft’s domain management; the attackers had no prior connection to the original developer; the attack was not detected by Microsoft until after significant credential theft.
- Information Gaps: The identity of the attacker, the full scope of affected users, and whether similar vulnerabilities exist in other Microsoft add-ins.
- Bias & Deception Risks: Potential bias in attributing the attack solely to opportunism without considering strategic motivations; risk of deception if the attack is a diversion from other malicious activities.
4. Implications and Strategic Risks
This development could lead to increased scrutiny of software supply chains and demand for improved monitoring of abandoned digital assets. It may also prompt other threat actors to exploit similar vulnerabilities.
- Political / Geopolitical: Potential for increased regulatory pressure on tech companies to secure their platforms and manage digital assets more effectively.
- Security / Counter-Terrorism: Heightened awareness of supply chain vulnerabilities may lead to enhanced security protocols, but also inspire similar attacks.
- Cyber / Information Space: Increased risk of phishing and credential theft campaigns exploiting similar vectors in other software ecosystems.
- Economic / Social: Potential loss of trust in digital marketplaces and services, impacting user engagement and economic activity within affected platforms.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a thorough audit of abandoned domains and add-ins within Microsoft and other platforms; enhance monitoring for suspicious activity.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms to improve threat detection; invest in user education on recognizing phishing attempts.
- Scenario Outlook: Best: Improved security measures prevent similar attacks; Worst: Widespread exploitation of similar vulnerabilities; Most-Likely: Incremental improvements in security with occasional breaches.
6. Key Individuals and Entities
- Idan Dardikman, Co-founder and CTO of Koi Security
- Microsoft Corporation
- Vercel (hosting platform)
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, supply chain attack, Microsoft Outlook, phishing, credential theft, software vulnerabilities, digital trust
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us