Ex-Army Colonel Receives Two-Year Sentence for Sharing Classified Military Plans to Impress Online Acquaintan…
Published on: 2026-02-12
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
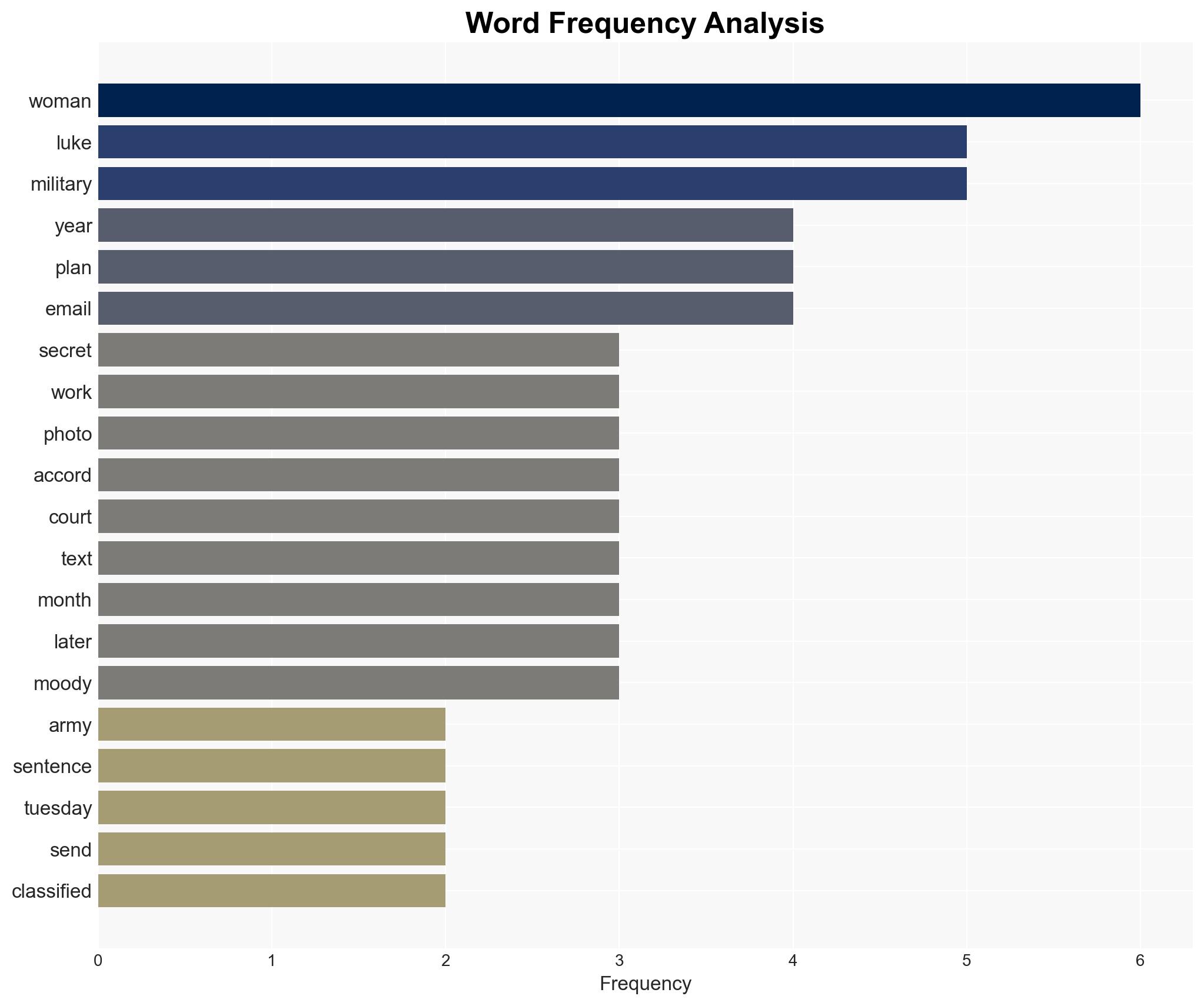
Intelligence Report: Former Army Colonel sentenced to 2 years for sending secret classified battle plans to woo woman
1. BLUF (Bottom Line Up Front)
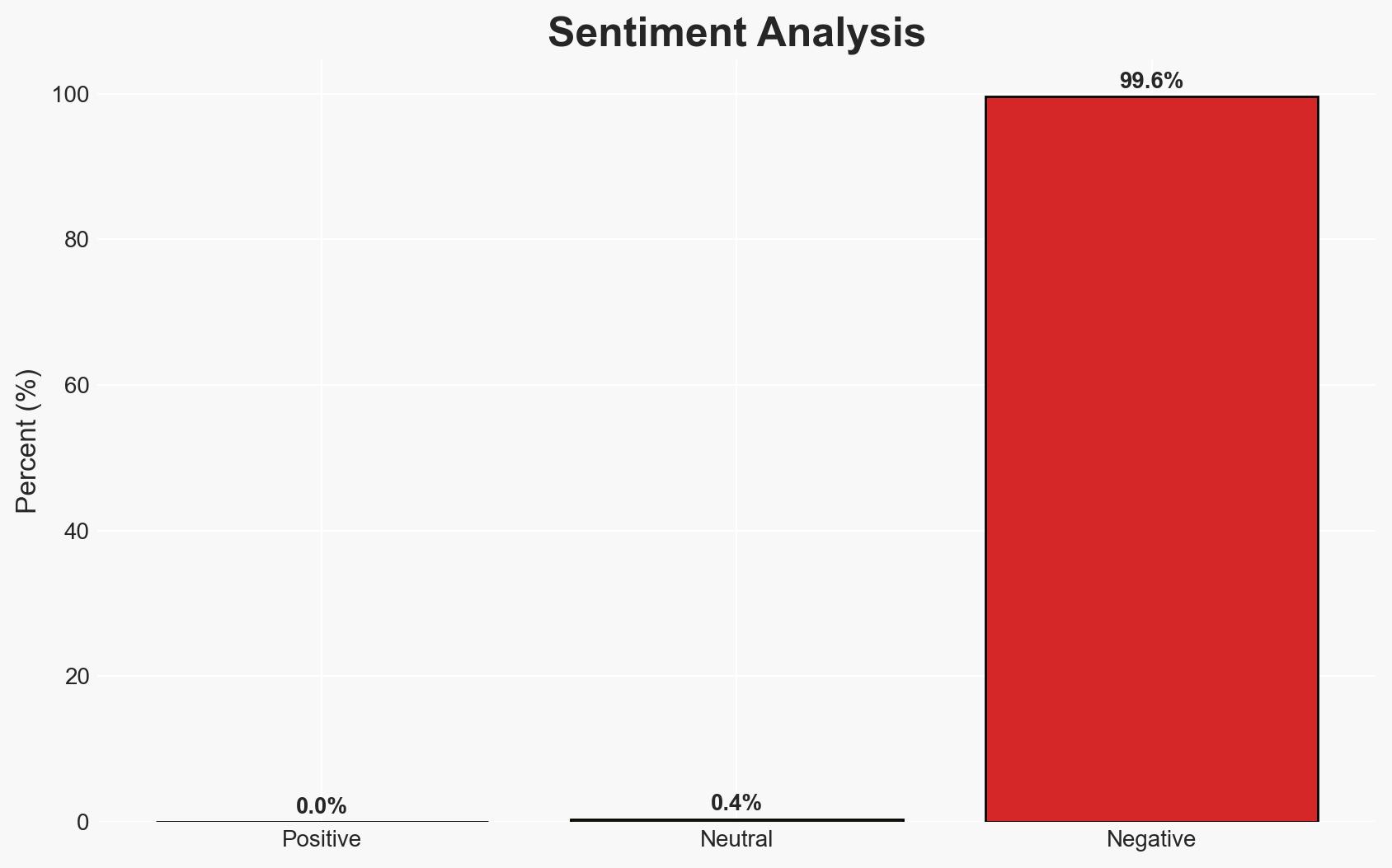
Retired Army Colonel Kevin Charles Luke was sentenced to two years for unauthorized communication of classified military plans, motivated by personal reasons rather than espionage. This incident highlights vulnerabilities in personnel security protocols. The most likely hypothesis is that this was an isolated incident driven by personal motives, with moderate confidence due to limited information on potential broader implications.
2. Competing Hypotheses
- Hypothesis A: Luke’s actions were an isolated incident driven by personal motives to impress a romantic interest, without intent to harm national security. Supporting evidence includes his guilty plea and lack of financial or espionage motives. Key uncertainties include the potential for undisclosed external influences.
- Hypothesis B: Luke’s actions were part of a broader pattern of security breaches, potentially indicating systemic issues within military contractor oversight. Contradicting evidence includes the absence of any identified network or repeated behavior.
- Assessment: Hypothesis A is currently better supported due to the lack of evidence suggesting broader espionage activities or systemic issues. Indicators that could shift this judgment include discovery of additional breaches or connections to foreign entities.
3. Key Assumptions and Red Flags
- Assumptions: Luke acted independently without external coercion; the breach was not part of a larger espionage operation; current security measures are generally effective but failed in this instance.
- Information Gaps: Details on the extent of classified information exposure and any potential foreign intelligence interest or contact.
- Bias & Deception Risks: Potential bias in assessing Luke’s motivations solely based on his statements; risk of underestimating systemic vulnerabilities in contractor oversight.
4. Implications and Strategic Risks
This incident underscores the need for robust personnel security measures and highlights potential vulnerabilities in contractor oversight. Over time, similar breaches could erode trust within intelligence-sharing alliances and impact operational security.
- Political / Geopolitical: Potential strain on Five Eyes intelligence-sharing if systemic issues are perceived.
- Security / Counter-Terrorism: Increased scrutiny on contractor vetting and monitoring processes to prevent future breaches.
- Cyber / Information Space: Potential exploitation of similar vulnerabilities by adversarial entities through cyber means.
- Economic / Social: Limited direct economic impact, but potential reputational damage to military contracting entities.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a thorough review of contractor security protocols and implement immediate corrective measures; enhance monitoring of personnel with access to sensitive information.
- Medium-Term Posture (1–12 months): Develop resilience measures through improved training and awareness programs; strengthen partnerships with allied intelligence agencies to ensure continued trust and collaboration.
- Scenario Outlook: Best: Isolated incident with no further breaches; Worst: Discovery of systemic issues leading to multiple breaches; Most-Likely: Minor adjustments in security protocols prevent similar incidents.
6. Key Individuals and Entities
- Kevin Charles Luke – Former Army Colonel and civilian contractor
- US Central Command – Military headquarters involved
- Five Eyes Alliance – Intelligence alliance affected
- US District Judge James Moody – Presiding judge
- Mark O’Brien – Defense attorney
7. Thematic Tags
regional conflicts, national security, personnel security, intelligence-sharing, military contracting, classified information breach, counter-espionage, operational security
Structured Analytic Techniques Applied
- Causal Layered Analysis (CLA): Analyze events across surface happenings, systems, worldviews, and myths.
- Cross-Impact Simulation: Model ripple effects across neighboring states, conflicts, or economic dependencies.
- Scenario Generation: Explore divergent futures under varying assumptions to identify plausible paths.
Explore more:
Regional Conflicts Briefs ·
Daily Summary ·
Support us