Criminals Exploit Employee Monitoring Tools for Ransomware Attacks, Blending into Corporate Networks
Published on: 2026-02-12
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Who’s the bossware Ransomware slingers like employee monitoring tools too
1. BLUF (Bottom Line Up Front)
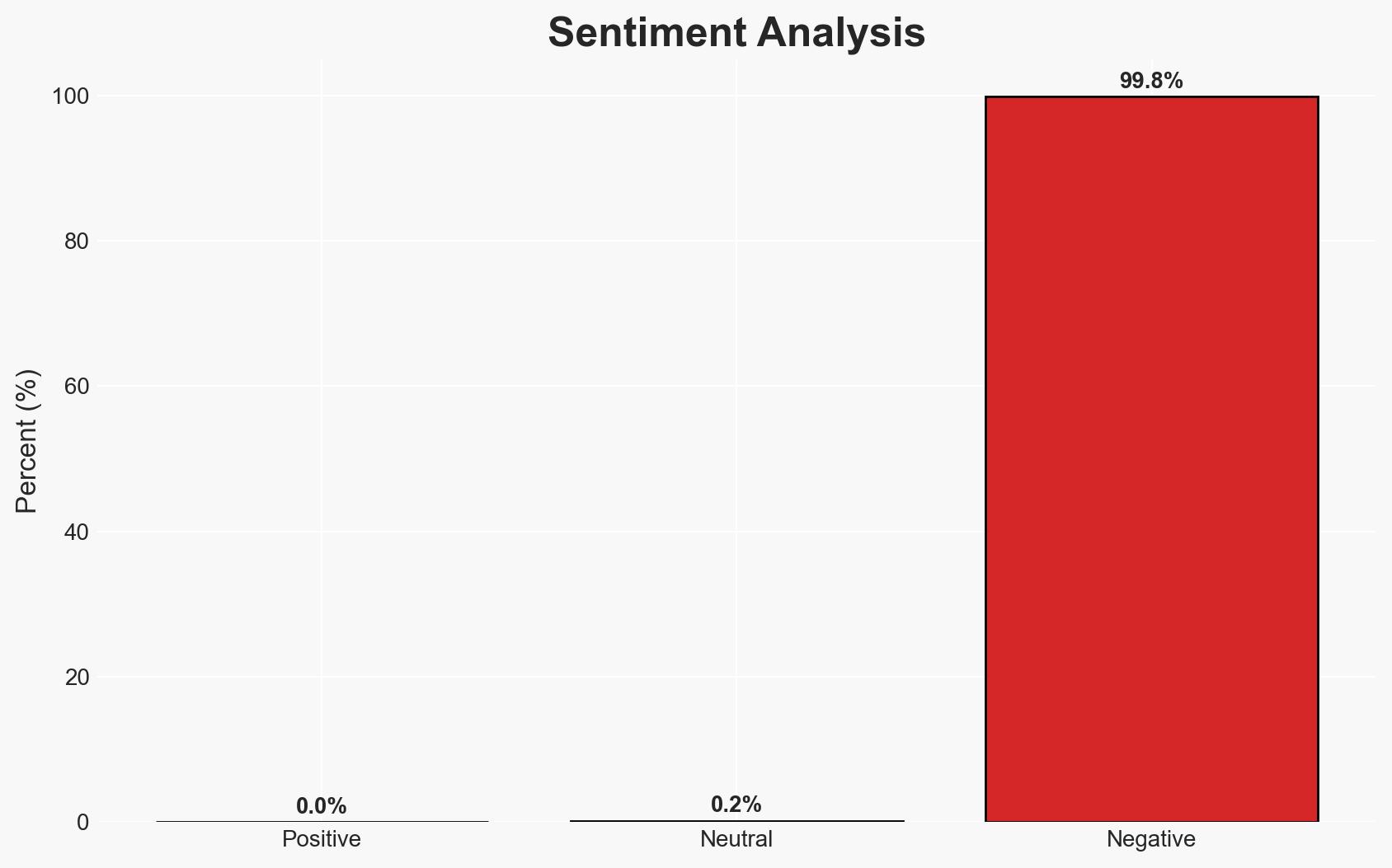
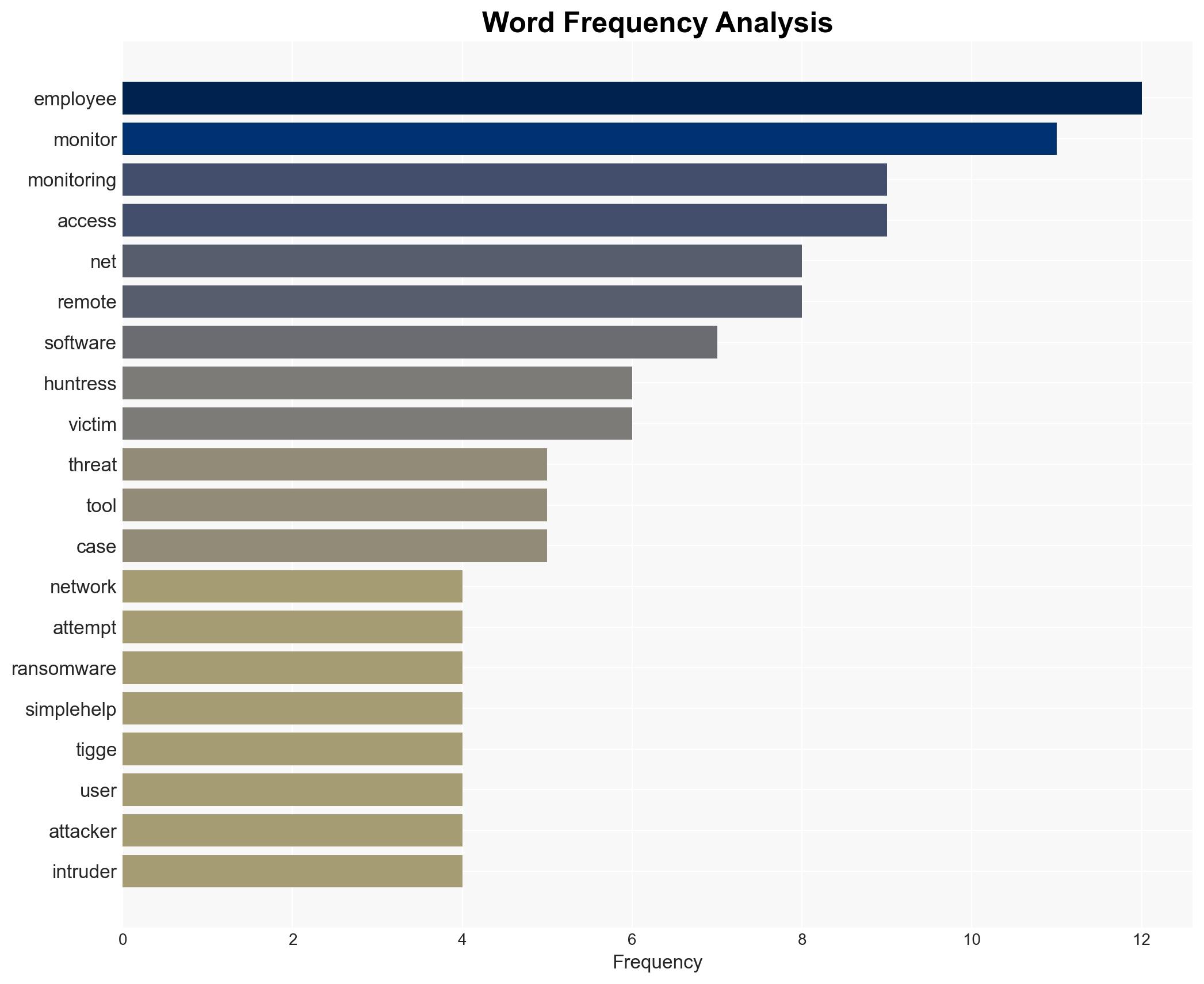
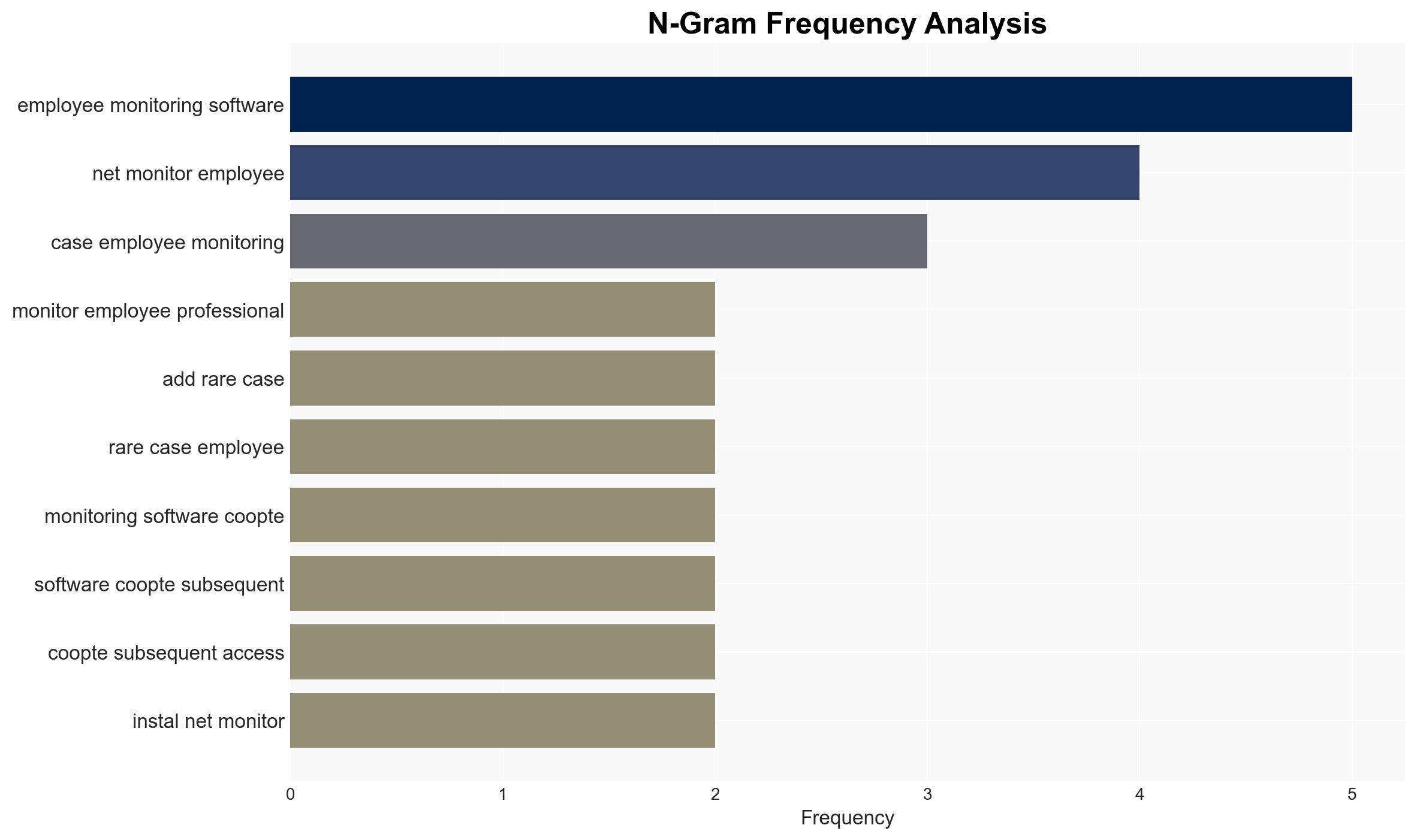
Threat actors are increasingly leveraging legitimate employee monitoring software to conduct ransomware attacks, posing a significant risk to corporate IT environments. The use of such software allows attackers to blend into networks, complicating detection efforts. This trend affects organizations across various sectors, with moderate confidence in the assessment due to limited information on initial access methods.
2. Competing Hypotheses
- Hypothesis A: Threat actors are opportunistically using employee monitoring software due to its legitimate appearance and capabilities, making it easier to infiltrate and persist in corporate networks. This is supported by the observed use of Net Monitor for Employees and SimpleHelp in recent attacks. However, the method of initial access remains unknown, introducing uncertainty.
- Hypothesis B: The use of employee monitoring software is part of a broader, targeted campaign against specific industries or organizations. This hypothesis is less supported as the victims appear to be opportunistic targets rather than part of a coordinated attack on specific sectors.
- Assessment: Hypothesis A is currently better supported due to the evidence of opportunistic targeting and the inherent advantages of using legitimate software for concealment. Indicators such as a pattern of targeting specific industries could shift this judgment towards Hypothesis B.
3. Key Assumptions and Red Flags
- Assumptions: Threat actors prioritize tools that blend into legitimate network traffic; employee monitoring software will continue to be used for malicious purposes; organizations lack sufficient detection capabilities for such software misuse.
- Information Gaps: Initial access vectors used by attackers; specific industries or organizations targeted; potential collaboration between threat actors.
- Bias & Deception Risks: Confirmation bias towards seeing all employee monitoring software as a threat; potential misinformation from threat actors to mislead security efforts.
4. Implications and Strategic Risks
The misuse of employee monitoring software for ransomware attacks could lead to increased scrutiny and regulation of such tools, impacting their legitimate use. Organizations may face heightened security risks and operational disruptions.
- Political / Geopolitical: Increased regulatory pressure on software vendors and potential international cooperation on cybersecurity standards.
- Security / Counter-Terrorism: Enhanced threat landscape with more sophisticated attack vectors leveraging legitimate tools.
- Cyber / Information Space: Challenges in distinguishing between legitimate and malicious software use, complicating cybersecurity defenses.
- Economic / Social: Potential economic impact from successful ransomware attacks; decreased trust in digital workplace tools.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of employee software use; conduct security audits to identify potential misuse; increase user awareness training.
- Medium-Term Posture (1–12 months): Develop partnerships with software vendors for improved security features; invest in advanced threat detection capabilities; establish industry-wide best practices for software use.
- Scenario Outlook:
- Best: Improved detection and regulation reduce misuse of monitoring tools.
- Worst: Escalation in ransomware attacks using legitimate software leads to significant economic damage.
- Most-Likely: Continued opportunistic attacks with gradual improvements in detection and response capabilities.
6. Key Individuals and Entities
- Michael Tigges, Senior Security Operations Analyst at Huntress
- Anna Pham, Dray Agha, Anton Ovrutsky, Threat Hunters at Huntress
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, ransomware, employee monitoring, threat actors, IT security, software misuse, network infiltration
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us