Deadly motorcycle raids in northern Nigeria claim at least 46 lives and result in multiple abductions.
Published on: 2026-02-15
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Gunmen kill at least 32 people in northern Nigeria residents say
1. BLUF (Bottom Line Up Front)
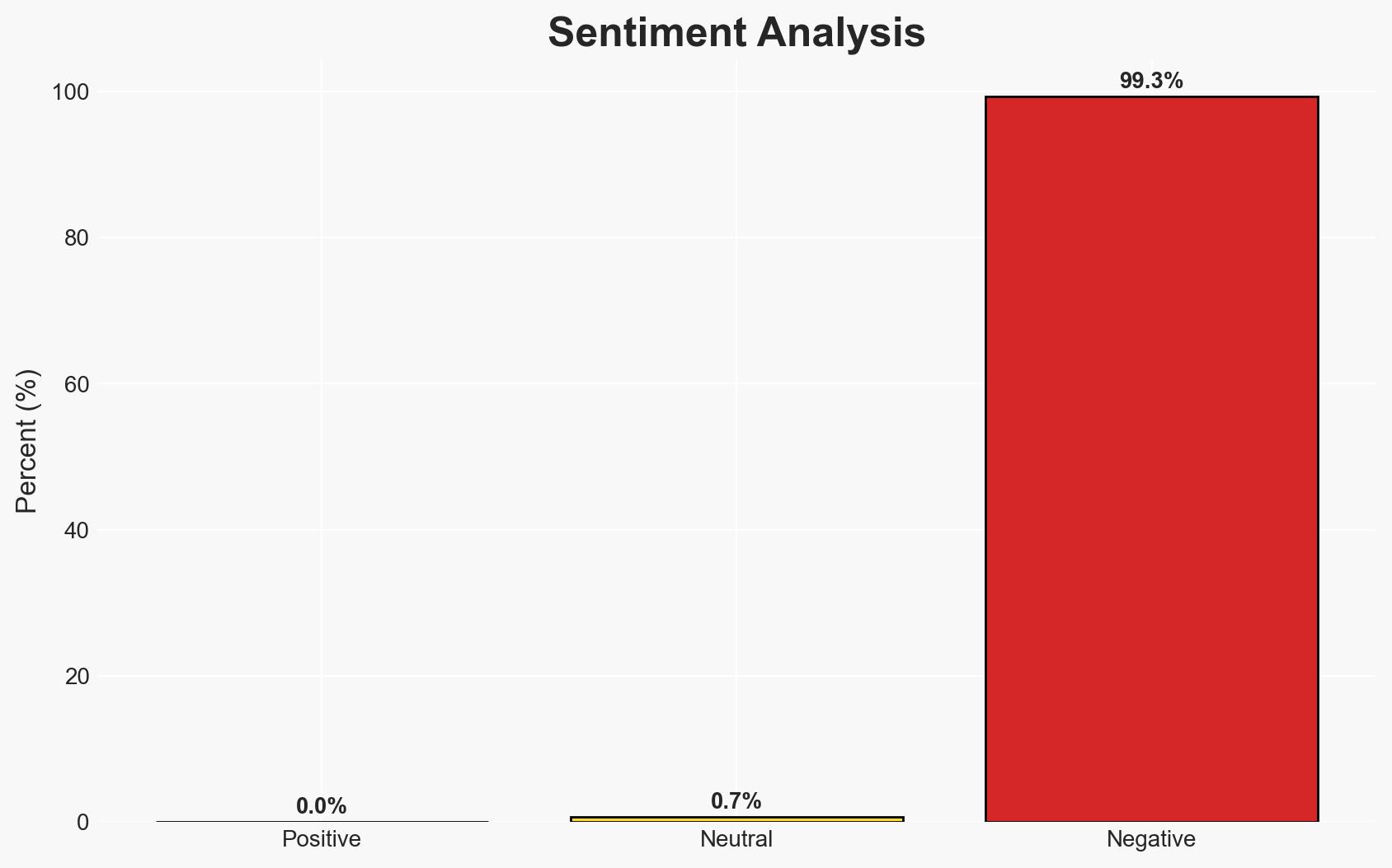
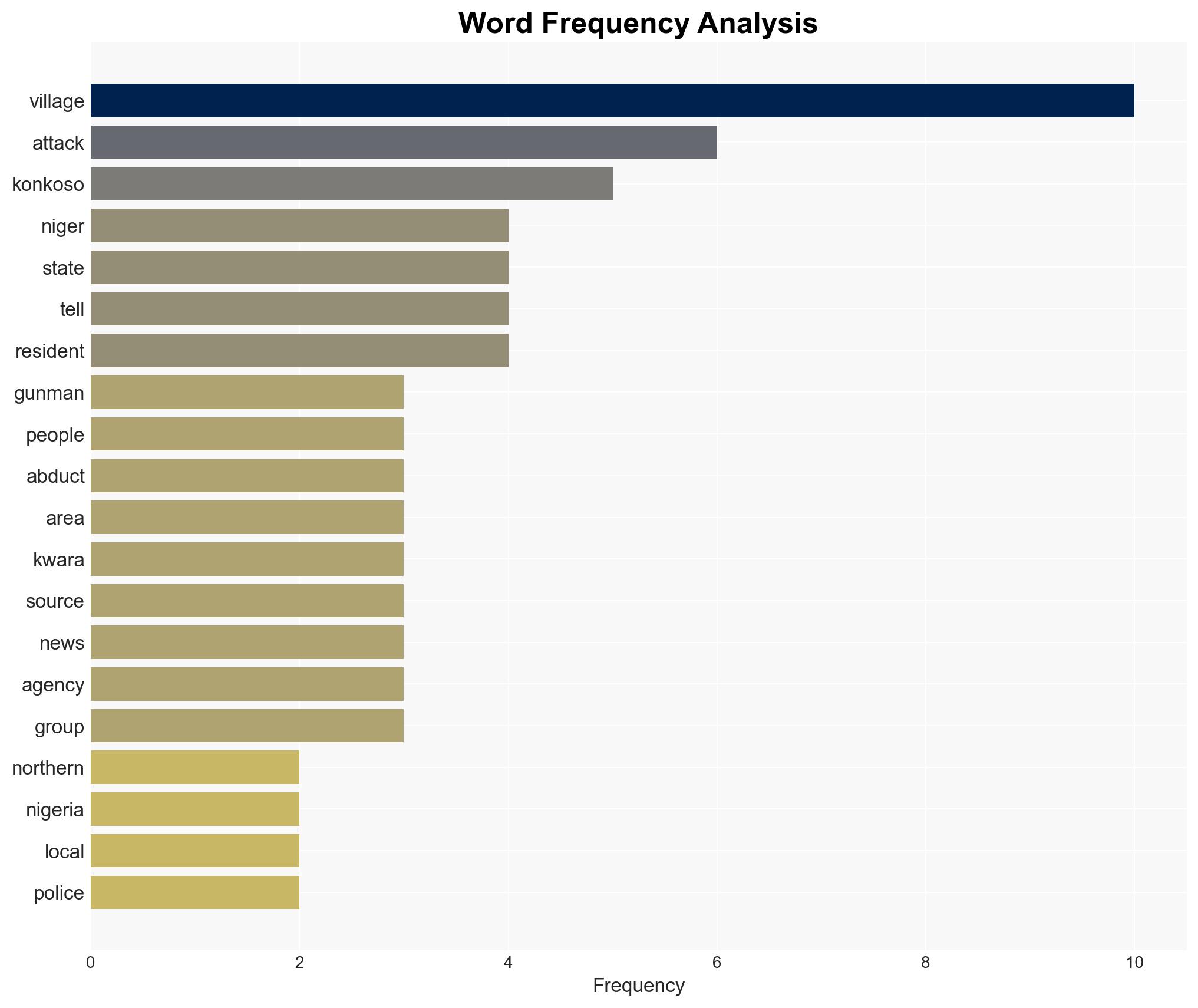
The recent attacks in northern Nigeria, resulting in at least 46 deaths and multiple abductions, highlight the persistent security challenges in the region. The involvement of armed groups and bandits suggests a complex threat landscape. The most likely hypothesis is that these attacks are primarily driven by local banditry rather than coordinated terrorist actions, with moderate confidence. This situation affects local populations and regional stability.
2. Competing Hypotheses
- Hypothesis A: The attacks are primarily driven by local banditry seeking ransom and resources. Supporting evidence includes the modus operandi of abductions for ransom and the lack of immediate claims by terrorist organizations. However, the presence of ISIL-affiliated groups in the area introduces uncertainty.
- Hypothesis B: The attacks are orchestrated by terrorist groups like ISIL or Boko Haram aiming to destabilize the region. This is supported by the historical presence of such groups and recent claims by JNIM. Contradicting evidence includes the absence of a direct claim of responsibility for these specific attacks.
- Assessment: Hypothesis A is currently better supported due to the absence of direct terrorist claims and the typical banditry patterns observed. Indicators such as a formal claim of responsibility by a known terrorist group could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The attacks are not state-sponsored; local security forces lack the capacity to effectively counter these threats; the primary motive is financial gain through ransom.
- Information Gaps: Detailed intelligence on the identity and affiliations of the attackers; confirmation of any terrorist group involvement; the exact number of abducted individuals.
- Bias & Deception Risks: Potential bias in local reporting due to fear of retribution; possible exaggeration or underreporting of events by local sources; manipulation by groups seeking to amplify their perceived threat.
4. Implications and Strategic Risks
The continuation of such attacks could exacerbate regional instability and undermine public confidence in government security measures. This may lead to increased calls for international intervention or support.
- Political / Geopolitical: Potential for increased political pressure on the Nigerian government to enhance security measures; risk of cross-border tensions if attacks spill over into neighboring states.
- Security / Counter-Terrorism: Heightened threat environment requiring enhanced intelligence and military operations; potential for increased recruitment by terrorist groups exploiting local grievances.
- Cyber / Information Space: Possible use of digital platforms by attackers to spread propaganda or misinformation; risk of cyber operations targeting local infrastructure.
- Economic / Social: Disruption of local economies due to instability; potential for increased displacement and humanitarian needs.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance intelligence collection and sharing among regional partners; deploy rapid response units to affected areas; increase community engagement to gather local insights.
- Medium-Term Posture (1–12 months): Strengthen border security and surveillance; develop resilience programs for affected communities; foster regional cooperation to address cross-border threats.
- Scenario Outlook:
- Best: Effective countermeasures reduce attacks, restoring stability.
- Worst: Escalation of violence leads to broader regional conflict.
- Most-Likely: Continued sporadic attacks with gradual improvements in security response.
6. Key Individuals and Entities
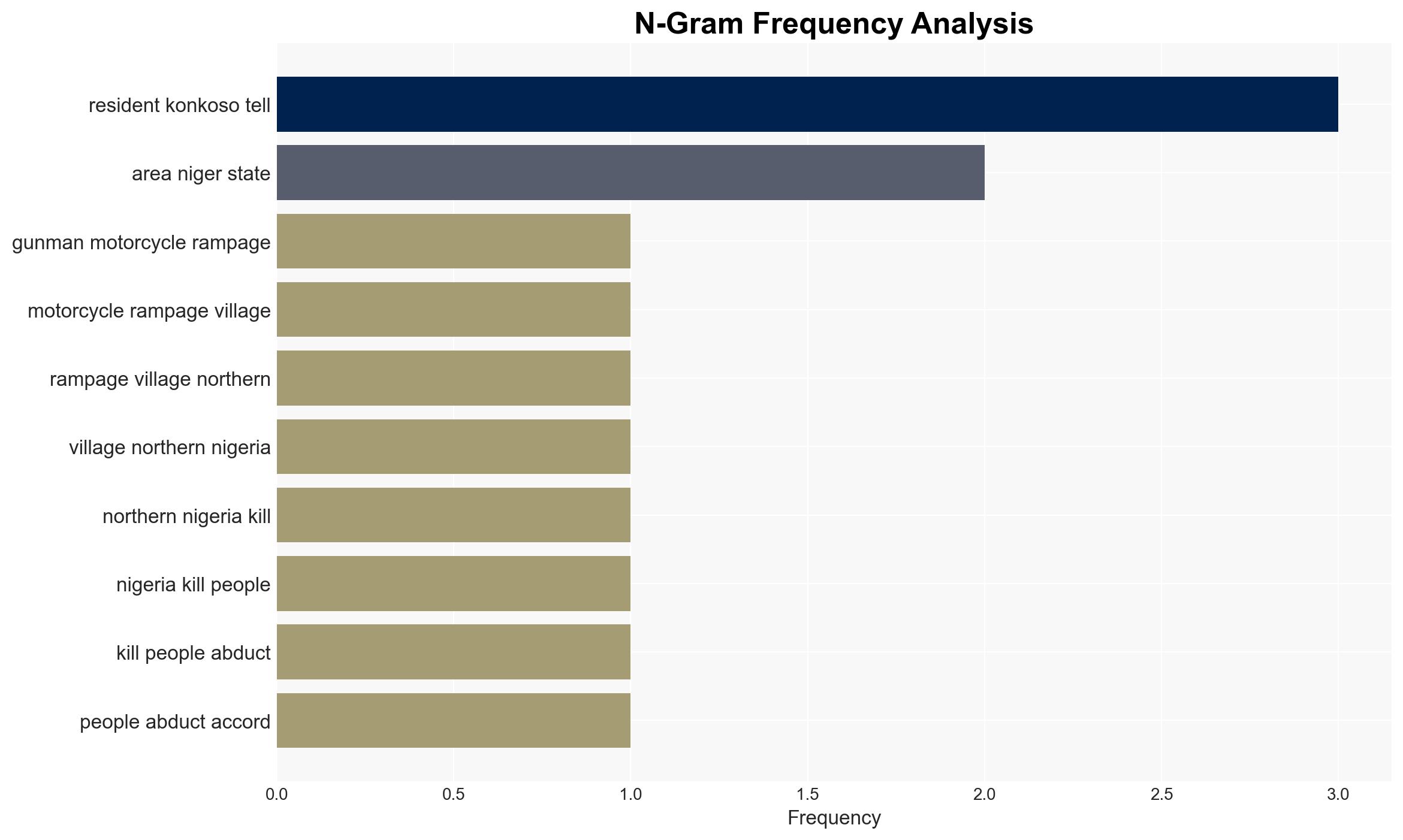
- Wasiu Abiodun – Niger State police spokesperson
- Jeremiah Timothy – Resident of Konkoso
- Abdullahi Adamu – Resident of Konkoso
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
Counter-Terrorism, banditry, regional stability, intelligence sharing, community engagement, security operations, humanitarian impact
Structured Analytic Techniques Applied
- ACH 2.0: Reconstruct likely threat actor intentions via hypothesis testing and structured refutation.
- Indicators Development: Track radicalization signals and propaganda patterns to anticipate operational planning.
- Narrative Pattern Analysis: Analyze spread/adaptation of ideological narratives for recruitment/incitement signals.
Explore more:
Counter-Terrorism Briefs ·
Daily Summary ·
Support us