Data Breach at Odido Affects Up to 6.2 Million Dutch Telecom Customers
Published on: 2026-02-16
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Odido Breach Impacts Millions of Dutch Telco Users
1. BLUF (Bottom Line Up Front)
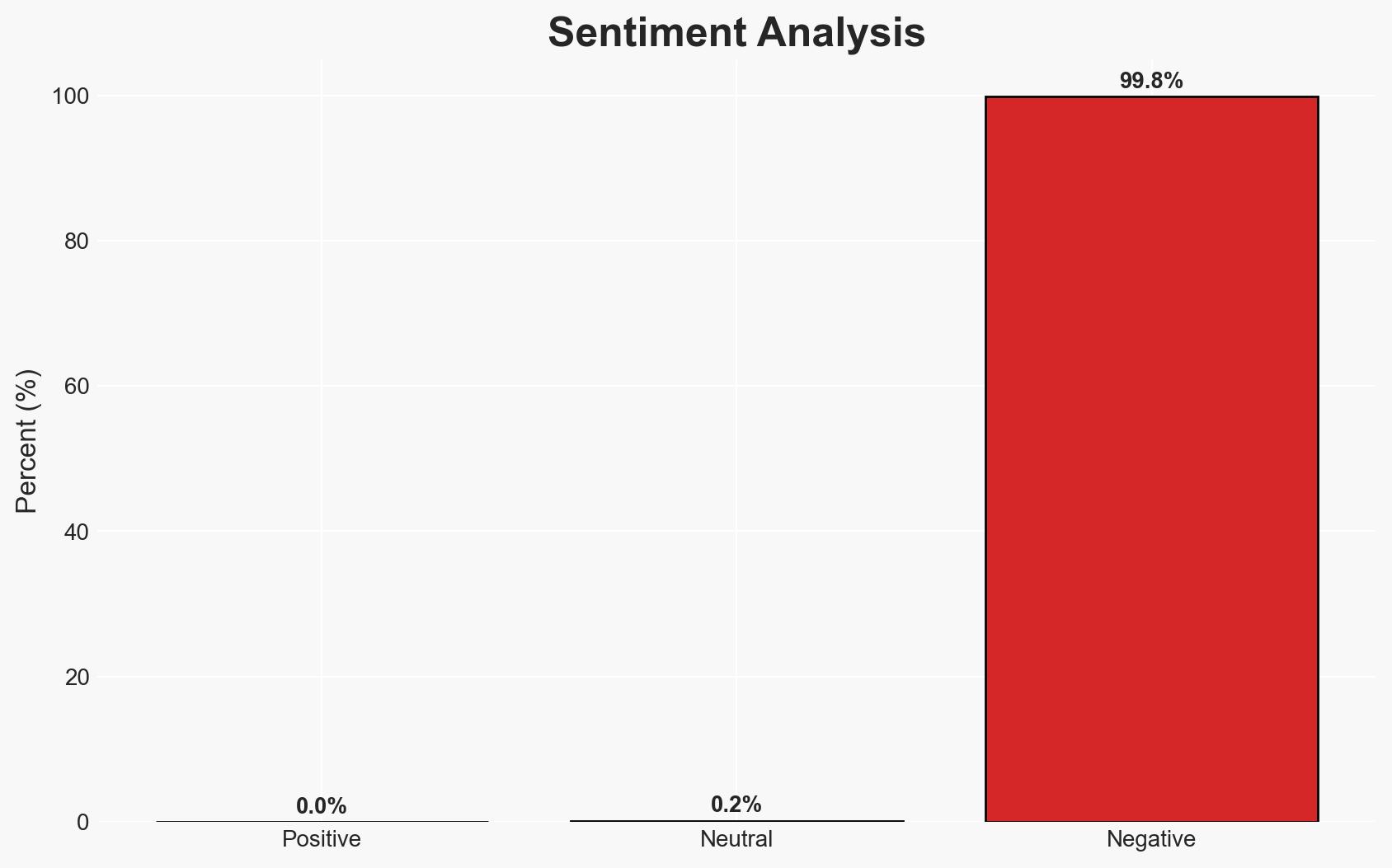
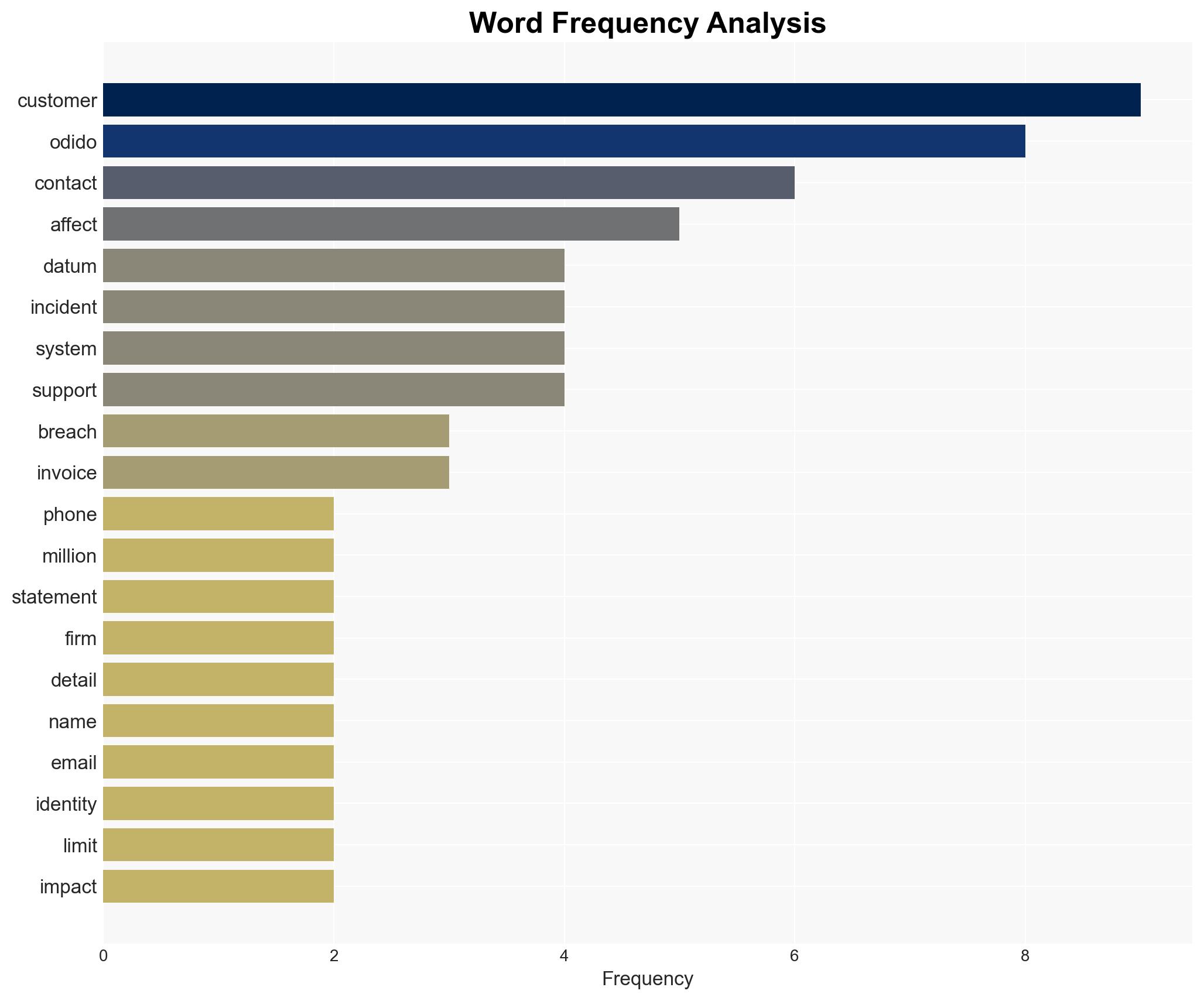
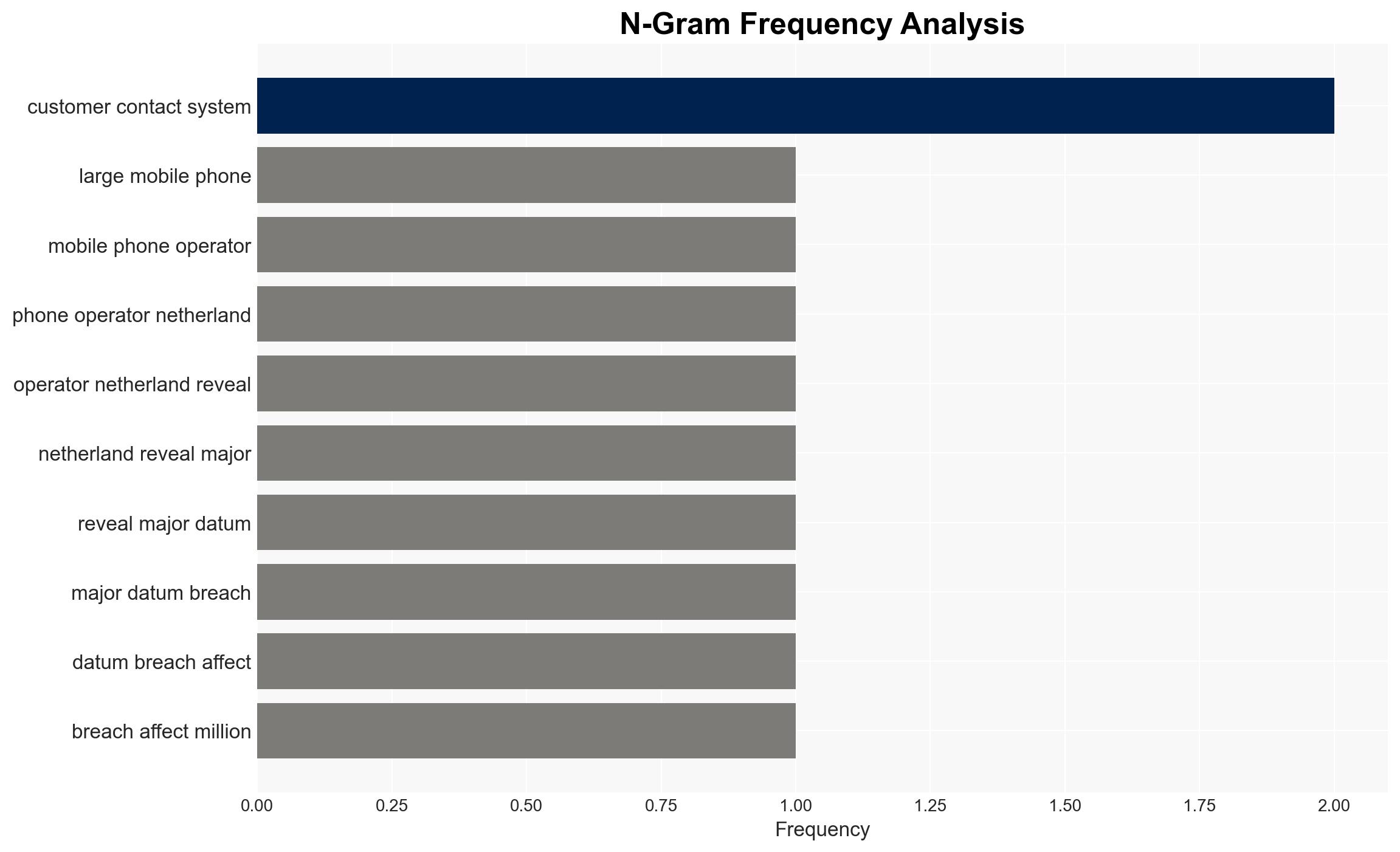
The Odido data breach has compromised sensitive personal information of potentially 6.2 million customers, posing significant risks for identity fraud and spear-phishing attacks. The breach highlights vulnerabilities in customer contact systems, which are often under-protected. The overall confidence level in this assessment is moderate, given the limited details on the breach’s origin and scope.
2. Competing Hypotheses
- Hypothesis A: The breach was conducted by financially motivated cybercriminals seeking to exploit personal data for identity theft and fraud. This is supported by the nature of the data accessed, which is valuable for such activities. However, the lack of immediate financial gain reported introduces uncertainty.
- Hypothesis B: The breach was a state-sponsored operation aimed at gathering intelligence on Dutch citizens. This hypothesis is less supported due to the absence of indicators typically associated with state-sponsored activities, such as targeting of strategic communications or infrastructure.
- Assessment: Hypothesis A is currently better supported due to the data’s suitability for financial exploitation. Indicators such as the emergence of fraud cases or further breaches could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The breach was limited to the customer contact system; Odido’s operational services remain unaffected; the data was accessed by external actors.
- Information Gaps: Details on the breach’s technical execution, the identity of the perpetrators, and the full scope of affected data.
- Bias & Deception Risks: Potential underreporting by Odido to minimize reputational damage; reliance on company statements without independent verification.
4. Implications and Strategic Risks
This breach could lead to increased regulatory scrutiny and pressure on telecommunications providers to enhance data protection measures. It may also embolden cybercriminals to target similar systems globally.
- Political / Geopolitical: Potential diplomatic tensions if a state-sponsored angle emerges, affecting international relations.
- Security / Counter-Terrorism: Increased risk of identity theft could facilitate terrorist financing and operations.
- Cyber / Information Space: Likely uptick in phishing and social engineering attacks exploiting the stolen data.
- Economic / Social: Potential loss of consumer trust in Odido, impacting its market position and customer retention.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring for fraud activities, engage with cybersecurity experts to audit and secure systems, and communicate transparently with affected customers.
- Medium-Term Posture (1–12 months): Develop resilience measures, including regular security audits and employee training on data protection; strengthen partnerships with law enforcement and cybersecurity firms.
- Scenario Outlook:
- Best: Rapid containment and no significant misuse of data.
- Worst: Widespread identity fraud and loss of customer trust.
- Most-Likely: Moderate increase in fraud attempts, leading to regulatory changes.
6. Key Individuals and Entities
- Odido (Dutch Telco)
- Aaron Colclough (VP of Operations, Suzu Labs)
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, data breach, telecommunications, identity theft, spear-phishing, regulatory compliance, cybercrime
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Forecast futures under uncertainty via probabilistic logic.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us