Sensitive Australian court files compromised by subcontractor based in India, violating federal regulations.
Published on: 2026-02-16
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Highly sensitive court data accessed by entity based in India
1. BLUF (Bottom Line Up Front)
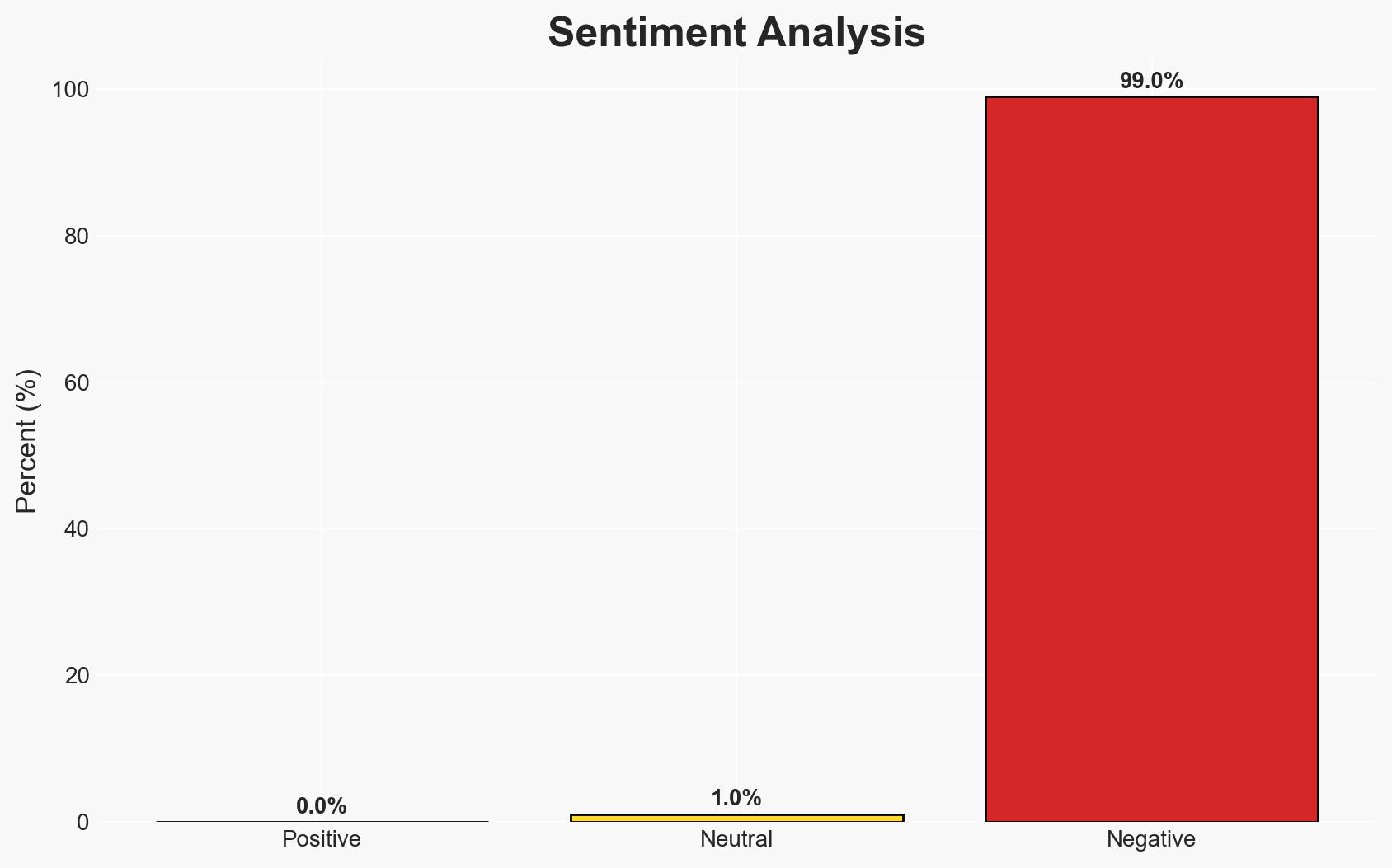
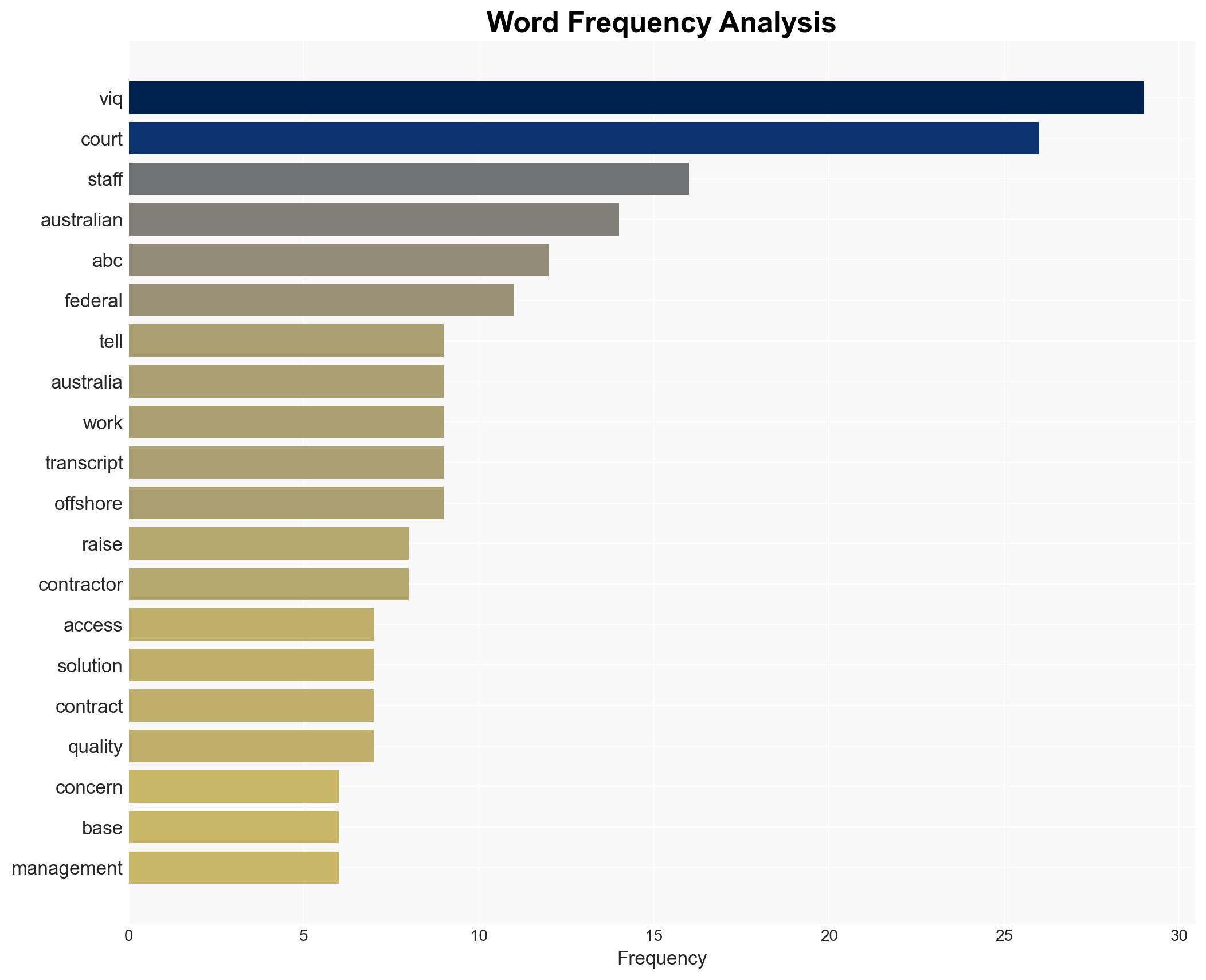
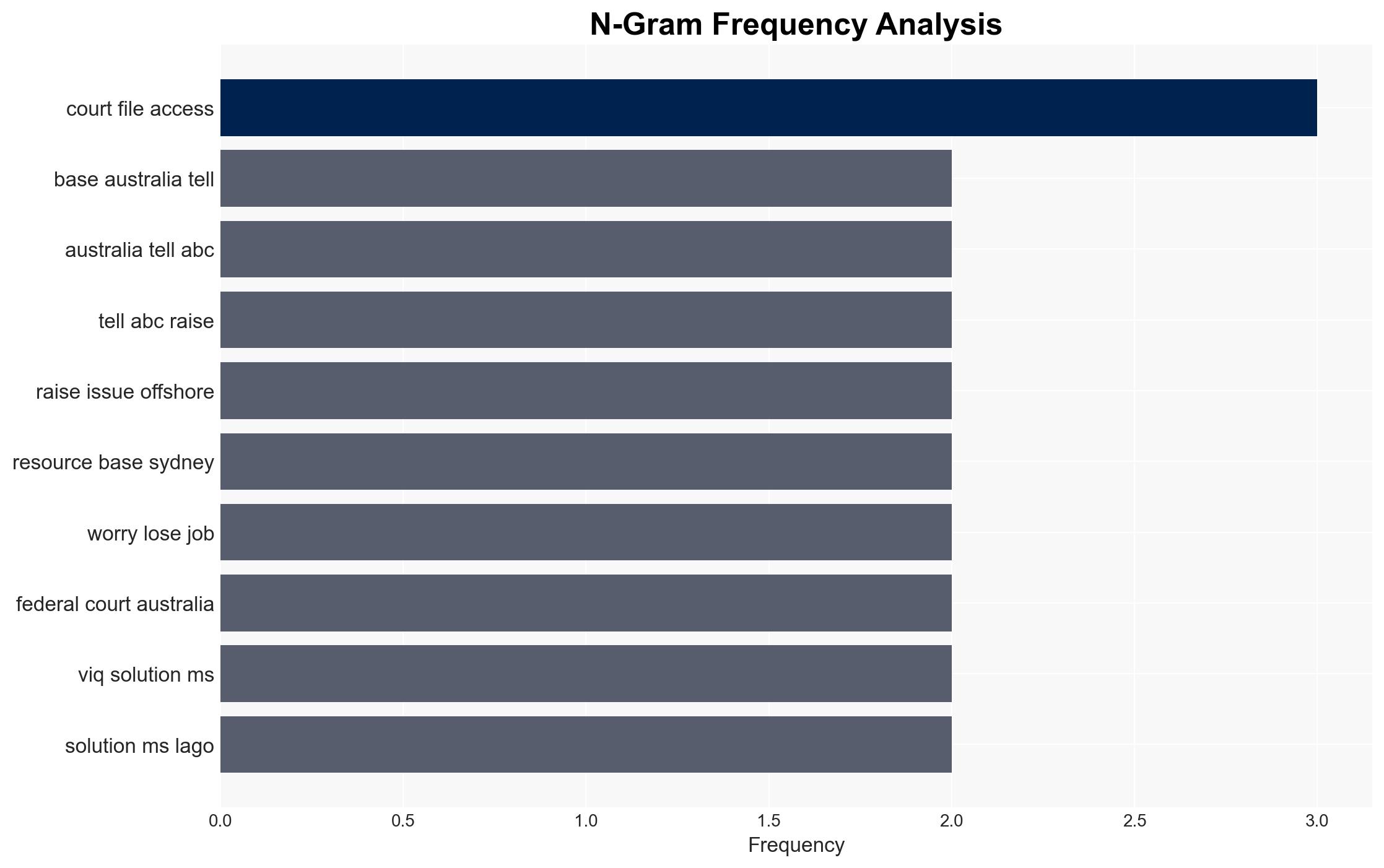
The unauthorized access of Australian court data by an Indian-based entity, e24 Technologies, represents a significant breach of national security protocols and contractual obligations. This incident poses potential risks to sensitive information, including intelligence and law enforcement operations. The most likely hypothesis is that VIQ Solutions subcontracted work to e24 Technologies without proper oversight, leading to this breach. Overall confidence in this assessment is moderate due to existing information gaps and potential biases.
2. Competing Hypotheses
- Hypothesis A: VIQ Solutions knowingly subcontracted work to e24 Technologies in India, breaching contractual obligations and exposing sensitive data. This is supported by internal documents and staff testimonies but contradicted by VIQ’s claims of compliance and location of resources in Sydney. Key uncertainties include the extent of VIQ management’s awareness and intent.
- Hypothesis B: The breach was unintentional, resulting from miscommunication or oversight within VIQ Solutions, with no deliberate intent to violate contracts. This is supported by VIQ’s review and corrective actions but lacks corroborative evidence of systemic oversight failures.
- Assessment: Hypothesis A is currently better supported due to the documented evidence of subcontracting and staff reports, despite VIQ’s denial. Indicators such as further internal communications or external audits could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: VIQ Solutions had full knowledge of its contractual obligations; e24 Technologies had access to sensitive data; staff reports are accurate and unbiased.
- Information Gaps: Details on VIQ’s internal decision-making processes; extent of data accessed by e24 Technologies; verification of e24’s operational practices.
- Bias & Deception Risks: Potential bias in staff reports due to internal conflicts; VIQ’s public statements may be misleading to mitigate reputational damage.
4. Implications and Strategic Risks
This development could lead to increased scrutiny of foreign subcontractors in sensitive sectors and impact international trust in Australian data handling practices.
- Political / Geopolitical: Potential diplomatic tensions between Australia and India; increased regulatory oversight on foreign subcontracting.
- Security / Counter-Terrorism: Heightened risk of sensitive information exposure affecting intelligence and law enforcement operations.
- Cyber / Information Space: Increased vulnerability to cyber espionage and data breaches; potential exploitation of accessed data by malicious actors.
- Economic / Social: Possible economic repercussions for VIQ Solutions; erosion of public trust in data security practices.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a comprehensive audit of VIQ Solutions’ subcontracting practices; enhance monitoring of data access by foreign entities.
- Medium-Term Posture (1–12 months): Develop stricter compliance frameworks for subcontracting; foster partnerships for improved data security protocols.
- Scenario Outlook:
- Best: Rapid implementation of corrective measures restores confidence and prevents future breaches.
- Worst: Continued breaches lead to significant national security threats and diplomatic fallout.
- Most-Likely: Incremental improvements in oversight and compliance reduce immediate risks but require ongoing vigilance.
6. Key Individuals and Entities
- VIQ Solutions
- e24 Technologies
- David Shoebridge, Greens Senator
- Crystal Oliphant, VIQ Vice-President of Legal, Compliance and Human Relations
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
national security threats, national security, data breach, cyber-espionage, subcontracting compliance, information security, international relations, legal data handling
Structured Analytic Techniques Applied
- Cognitive Bias Stress Test: Expose and correct potential biases in assessments through red-teaming and structured challenge.
- Bayesian Scenario Modeling: Use probabilistic forecasting for conflict trajectories or escalation likelihood.
- Network Influence Mapping: Map relationships between state and non-state actors for impact estimation.
Explore more:
National Security Threats Briefs ·
Daily Summary ·
Support us