Security Flaws in Major Password Managers Enable Unauthorized Access and Modification of User Credentials
Published on: 2026-02-16
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Vulnerabilities in Password Managers Allow Hackers to View and Change Passwords
1. BLUF (Bottom Line Up Front)
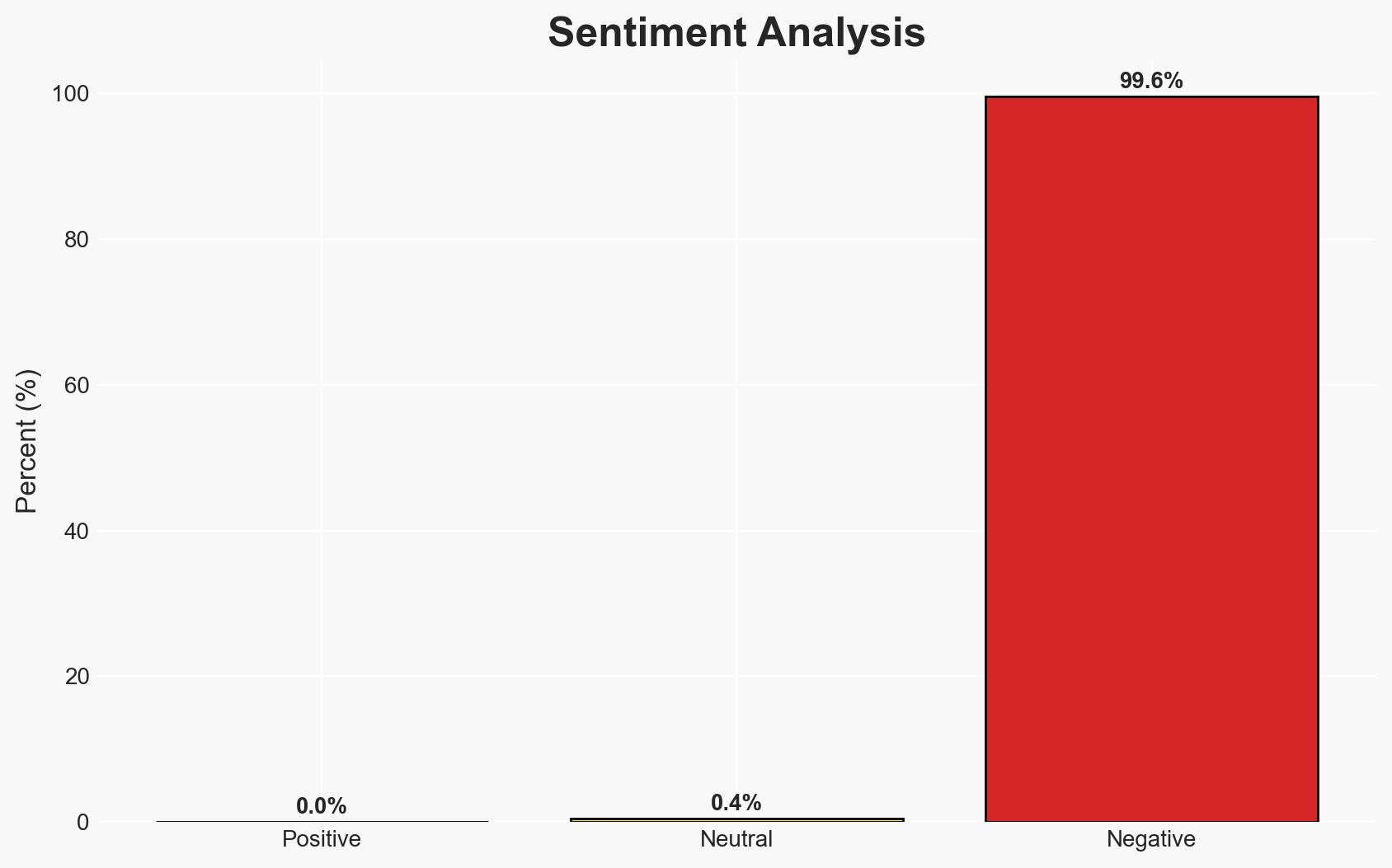
Recent research has identified critical vulnerabilities in several popular cloud-based password managers, potentially allowing attackers to access and alter stored passwords. This affects users of Bitwarden, LastPass, Dashlane, and 1Password, with varying degrees of risk. The findings challenge the security claims of these services, particularly regarding ‘zero-knowledge encryption.’ Overall, there is moderate confidence in the assessment due to the peer-reviewed nature of the research but limited insight into the real-world exploitability of these vulnerabilities.
2. Competing Hypotheses
- Hypothesis A: The vulnerabilities identified are primarily theoretical and difficult to exploit in real-world scenarios. Supporting evidence includes the lack of reported widespread breaches and the high level of technical expertise required to execute the attacks. Key uncertainties involve the potential for these vulnerabilities to be exploited by sophisticated threat actors.
- Hypothesis B: The vulnerabilities present a significant and immediate risk to users, with potential for exploitation by cybercriminals. This is supported by the detailed nature of the attack scenarios and the weaknesses in cryptographic implementations. Contradicting evidence includes the absence of immediate reports of exploitation and the security measures already in place by some providers, such as 1Password’s use of a high-entropy cryptographic key.
- Assessment: Hypothesis B is currently better supported due to the comprehensive nature of the research and the specific vulnerabilities identified. However, further monitoring of threat actor activity and potential exploitation reports could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The vulnerabilities are accurately described and applicable to current versions of the software; password managers will respond to these findings with updates; users are generally unaware of these vulnerabilities.
- Information Gaps: Lack of data on actual exploitation in the wild; details on the response and mitigation measures by the affected companies.
- Bias & Deception Risks: Potential bias from researchers seeking to highlight weaknesses for academic or reputational gain; possible underreporting by companies to maintain consumer trust.
4. Implications and Strategic Risks
The discovery of these vulnerabilities could lead to increased scrutiny of password management solutions and potentially drive innovation in security practices. However, it may also erode trust in these services, impacting user adoption and security posture.
- Political / Geopolitical: Limited direct implications, but potential for increased regulatory scrutiny on cybersecurity standards.
- Security / Counter-Terrorism: Potential for increased cybercrime activity targeting password managers, impacting operational security.
- Cyber / Information Space: Heightened risk of data breaches and information theft; potential for misinformation campaigns exploiting fear of compromised security.
- Economic / Social: Potential financial impact on affected companies; erosion of consumer trust in digital security solutions.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor for any reports of exploitation; engage with password manager providers for updates and mitigation strategies; inform users of potential risks and encourage best practices.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms to enhance threat intelligence; invest in research and development for improved encryption technologies.
- Scenario Outlook:
- Best: Vulnerabilities are patched without major incidents, leading to improved security standards.
- Worst: Widespread exploitation leads to significant data breaches and loss of consumer trust.
- Most-Likely: Gradual patching and increased awareness mitigate risks without major incidents.
6. Key Individuals and Entities
- ETH Zurich, Università della Svizzera italiana (USI), Bitwarden, LastPass, Dashlane, 1Password
7. Thematic Tags
cybersecurity, password management, encryption vulnerabilities, data protection, cybercrime, information security, digital trust
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Forecast futures under uncertainty via probabilistic logic.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us