Intellexa’s Predator spyware implicated in hacking of Angolan journalist’s iPhone, reveals Amnesty Internatio…
Published on: 2026-02-18
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Intellexa’s Predator spyware used to hack iPhone of journalist in Angola research says TechCrunch
1. BLUF (Bottom Line Up Front)
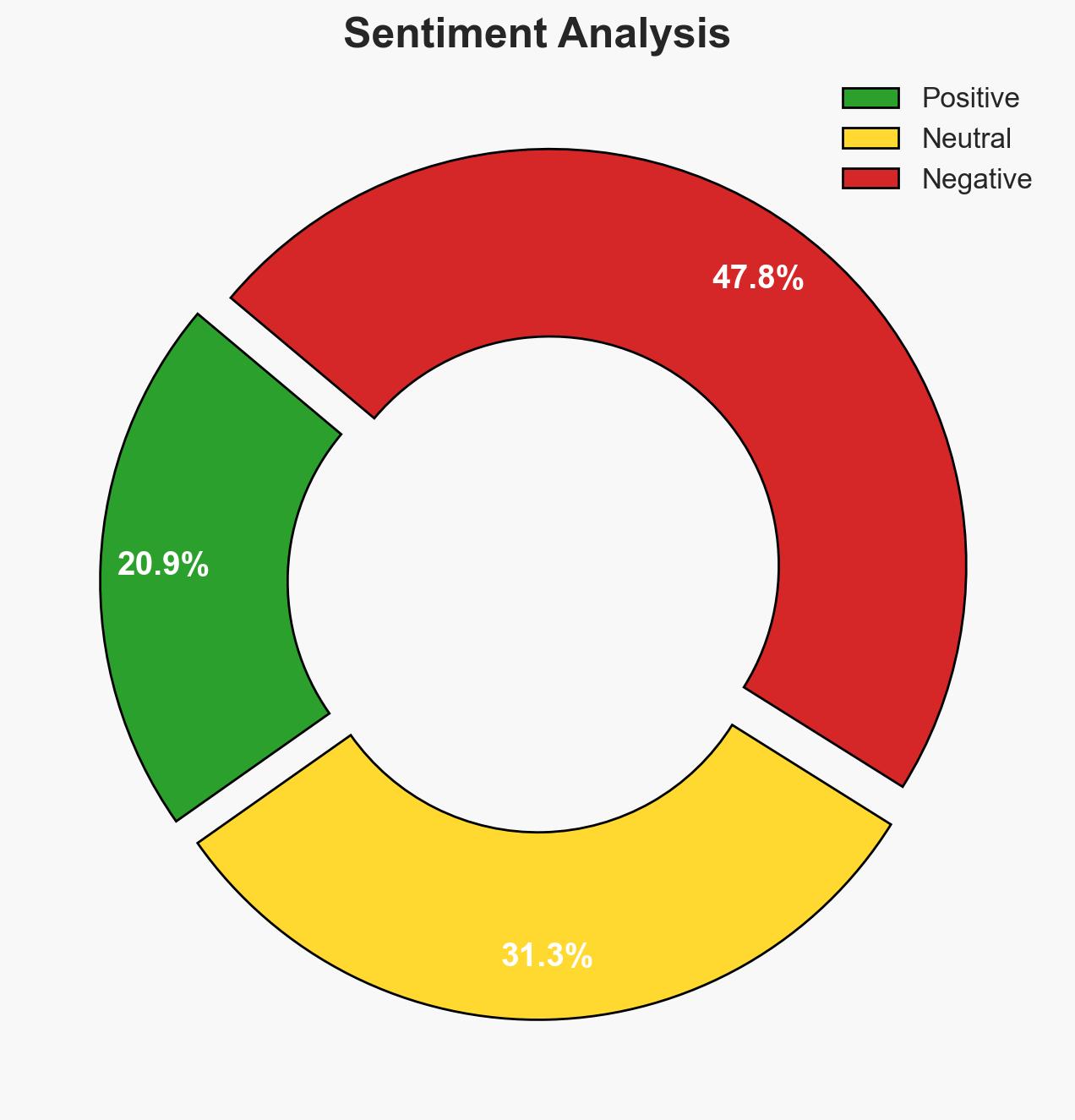
The hacking of Angolan journalist Teixeira Cândido’s iPhone using Intellexa’s Predator spyware highlights the ongoing use of commercial spyware by government entities to target civil society actors. This incident underscores the broader trend of surveillance abuses against journalists and activists. The current assessment, with moderate confidence, suggests that Intellexa’s operations continue to pose significant risks to privacy and press freedom globally.
2. Competing Hypotheses
- Hypothesis A: The Angolan government, or a faction within it, directly contracted Intellexa to target Cândido as part of a broader campaign against dissent. Supporting evidence includes the use of Predator spyware and the targeting of a known activist. However, the exact identity of the perpetrator remains unconfirmed.
- Hypothesis B: A non-state actor or foreign entity used Intellexa’s spyware to target Cândido, possibly to discredit the Angolan government or for other strategic purposes. This hypothesis is less supported due to the lack of direct evidence pointing to non-state involvement.
- Assessment: Hypothesis A is currently better supported due to the typical pattern of government use of such spyware and the targeting of a domestic journalist. Key indicators that could shift this judgment include evidence of foreign involvement or internal leaks from the Angolan government.
3. Key Assumptions and Red Flags
- Assumptions: Intellexa’s spyware is primarily used by state actors; the Angolan government has the capability and motive to target journalists; Amnesty International’s forensic analysis is accurate.
- Information Gaps: The specific identity of the actor who commissioned the spyware attack; the full extent of Predator’s deployment in Angola.
- Bias & Deception Risks: Potential bias in Amnesty International’s reporting; possible deception by Intellexa or its customers to obscure true operators.
4. Implications and Strategic Risks
This development could exacerbate tensions between civil society and the Angolan government, potentially leading to increased international scrutiny and pressure. It may also embolden other governments to use similar technologies against dissenters.
- Political / Geopolitical: Increased diplomatic friction and potential sanctions against Angola or Intellexa.
- Security / Counter-Terrorism: Heightened risk of surveillance abuse leading to civil unrest or radicalization.
- Cyber / Information Space: Escalation in the use of sophisticated spyware against journalists and activists globally.
- Economic / Social: Potential impact on Angola’s international relations and economic partnerships due to reputational damage.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Increase monitoring of spyware use in Angola; engage with international partners to address spyware proliferation.
- Medium-Term Posture (1–12 months): Develop resilience measures for journalists and activists; strengthen international legal frameworks against spyware abuse.
- Scenario Outlook:
- Best: International pressure leads to reforms in spyware regulation.
- Worst: Widespread adoption of spyware by authoritarian regimes.
- Most-Likely: Continued sporadic use of spyware with limited international response.
6. Key Individuals and Entities
- Teixeira Cândido – Angolan journalist and activist
- Intellexa – Spyware maker
- Tal Dilian – Intellexa founder
- Sara Aleksandra Fayssal Hamou – Intellexa business partner
- Amnesty International – Human rights organization conducting research
7. Thematic Tags
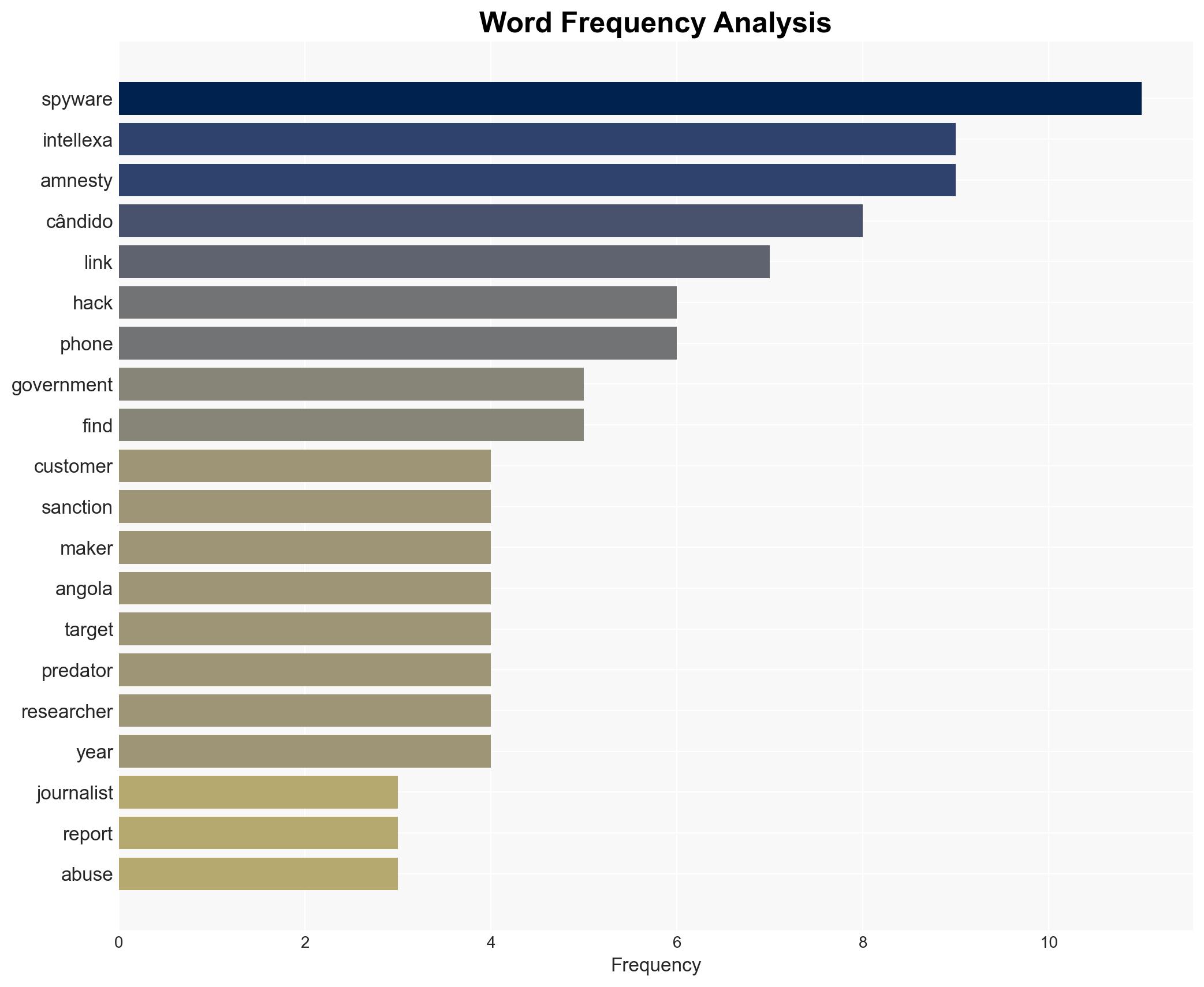
cybersecurity, cyber-espionage, press freedom, spyware, Angola, Intellexa, surveillance, human rights
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us