Security flaws in popular VS Code extensions with 125M installs risk user data and remote code execution
Published on: 2026-02-18
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: VS Code extensions with 125M installs expose users to cyberattacks
1. BLUF (Bottom Line Up Front)
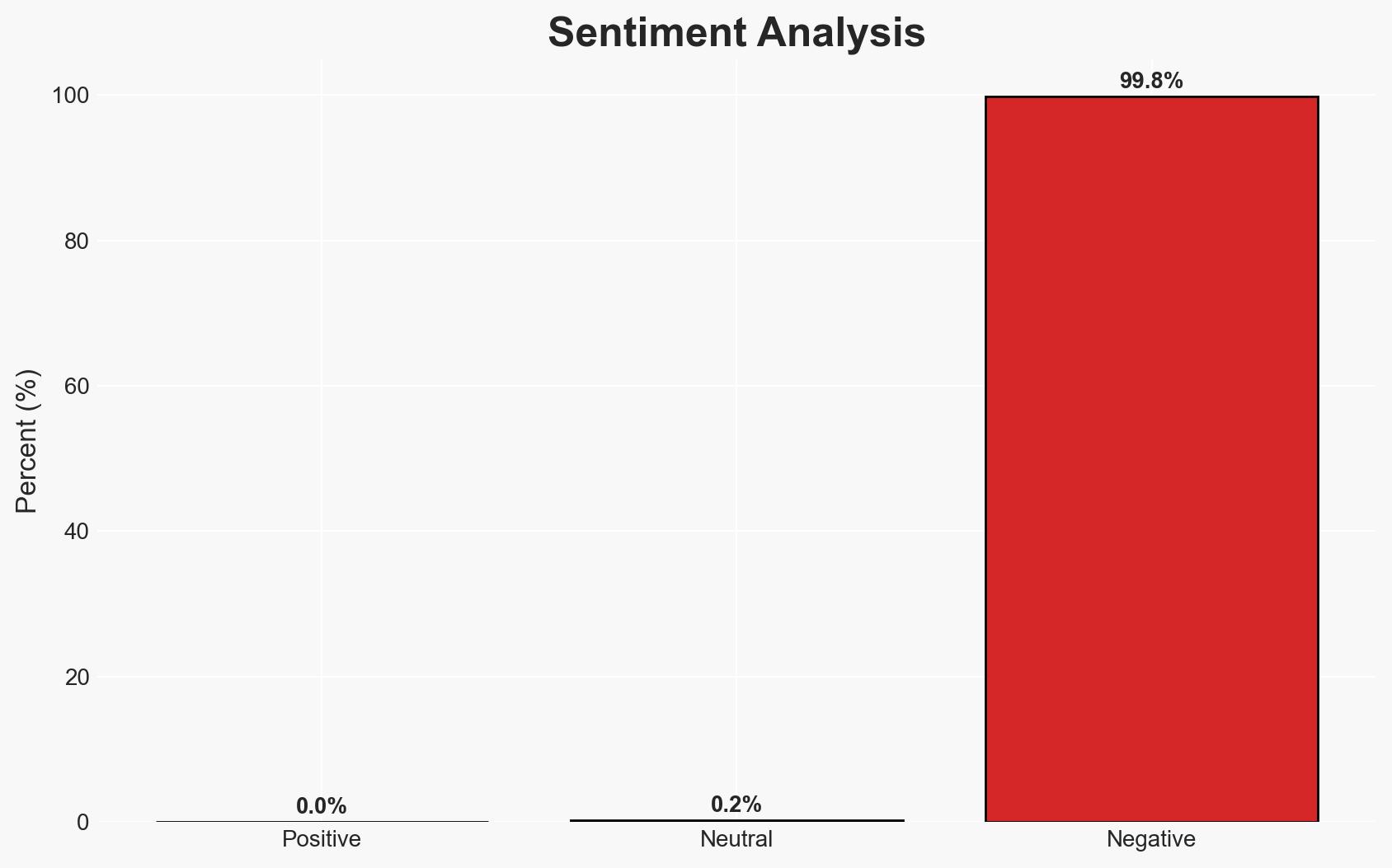
Four popular VS Code extensions with over 125 million installs contain vulnerabilities that could enable cyberattacks, affecting a significant number of developers globally. The lack of response from extension maintainers exacerbates the risk. The most likely hypothesis is that these vulnerabilities will remain unaddressed in the short term, posing ongoing threats. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The vulnerabilities in the VS Code extensions will be addressed promptly following increased awareness and pressure on maintainers. Supporting evidence includes the public disclosure of vulnerabilities and potential reputational damage to maintainers. However, the lack of initial response from maintainers contradicts this.
- Hypothesis B: The vulnerabilities will remain largely unaddressed due to systemic issues in extension security and lack of accountability. This is supported by the maintainers’ lack of response and the absence of mandatory security protocols. Contradicting evidence could emerge if maintainers begin to address the issues following public pressure.
- Assessment: Hypothesis B is currently better supported due to the systemic issues highlighted and the maintainers’ lack of response. Key indicators that could shift this judgment include any public commitments from maintainers to address the vulnerabilities or the implementation of mandatory security reviews.
3. Key Assumptions and Red Flags
- Assumptions: The vulnerabilities are not yet widely exploited; maintainers have the capability to address these issues; public disclosure will increase pressure on maintainers; users will not uninstall the extensions en masse.
- Information Gaps: Specific actions taken by maintainers post-disclosure; detailed exploitation data; user awareness and response to the vulnerabilities.
- Bias & Deception Risks: Potential bias in the reporting of vulnerabilities by security researchers; possible underreporting by maintainers to avoid reputational damage.
4. Implications and Strategic Risks
The vulnerabilities in these extensions could lead to widespread cyberattacks if not addressed, potentially compromising sensitive data across numerous organizations. This development could influence broader cybersecurity practices and policies.
- Political / Geopolitical: Increased scrutiny on software security practices could lead to regulatory changes.
- Security / Counter-Terrorism: Elevated risk of cyber intrusions and data breaches, possibly affecting critical infrastructure.
- Cyber / Information Space: Potential for increased cyber espionage activities leveraging these vulnerabilities.
- Economic / Social: Possible economic impact on companies relying on these extensions, leading to loss of trust in software ecosystems.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor for any updates from maintainers; advise users to limit use of affected extensions; enhance awareness campaigns on secure extension practices.
- Medium-Term Posture (1–12 months): Develop partnerships for shared security protocols in software development; invest in AI-powered vulnerability scanning tools.
- Scenario Outlook:
- Best: Vulnerabilities are patched, and security protocols are improved, reducing risk.
- Worst: Widespread exploitation of vulnerabilities leads to significant data breaches.
- Most-Likely: Slow progress on patching vulnerabilities, with sporadic exploitation incidents.
6. Key Individuals and Entities
- OX Security (Research team)
- VS Code Extension Maintainers (Live Server, Code Runner, Markdown Preview Enhanced, Microsoft Live Preview)
- Developers and Users of VS Code Extensions
7. Thematic Tags
cybersecurity, software vulnerabilities, open-source software, developer tools, cyber threats, information security, software maintenance
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us