Dutch police apprehend suspect for hacking after mistakenly providing access to sensitive documents.
Published on: 2026-02-18
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
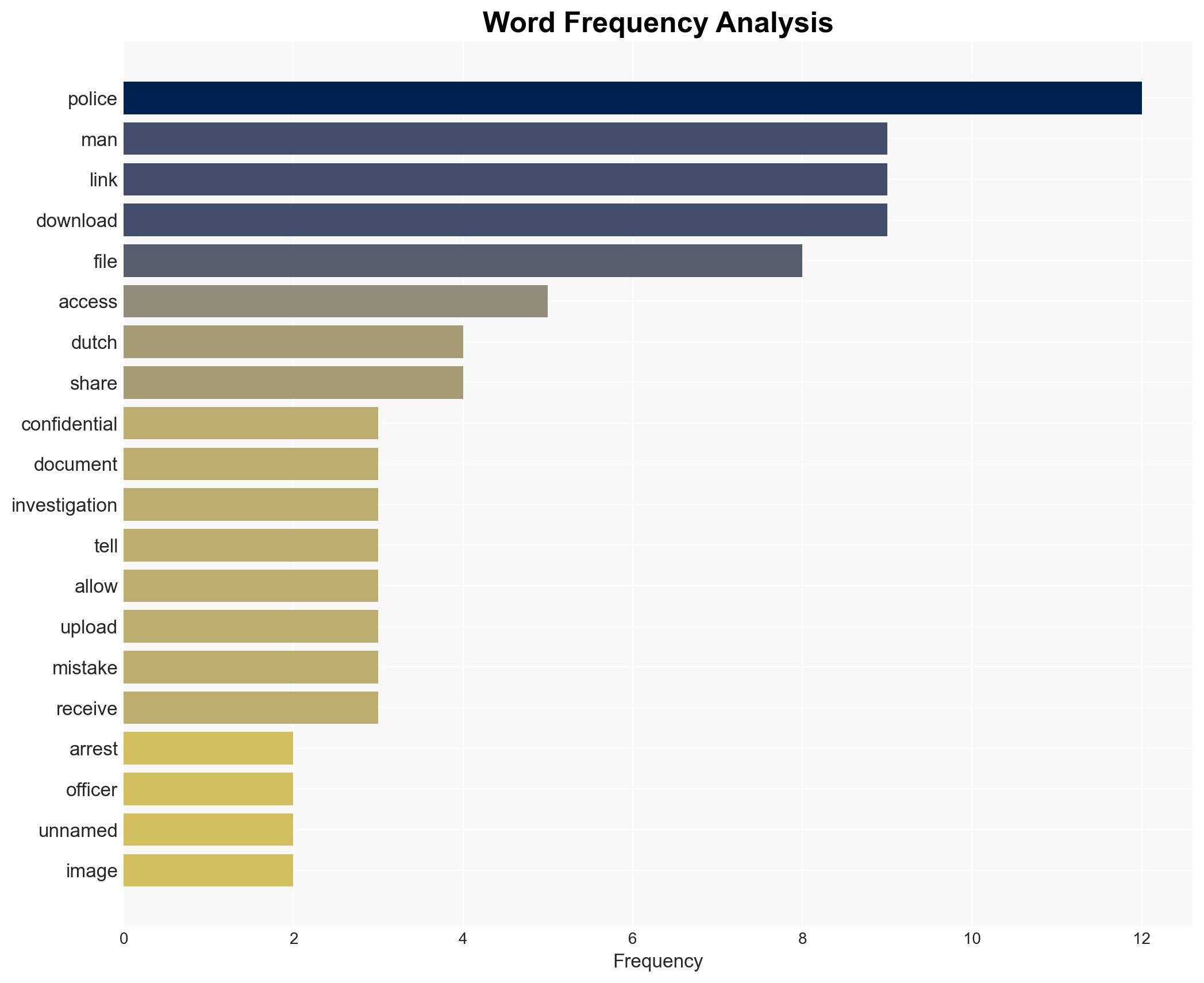
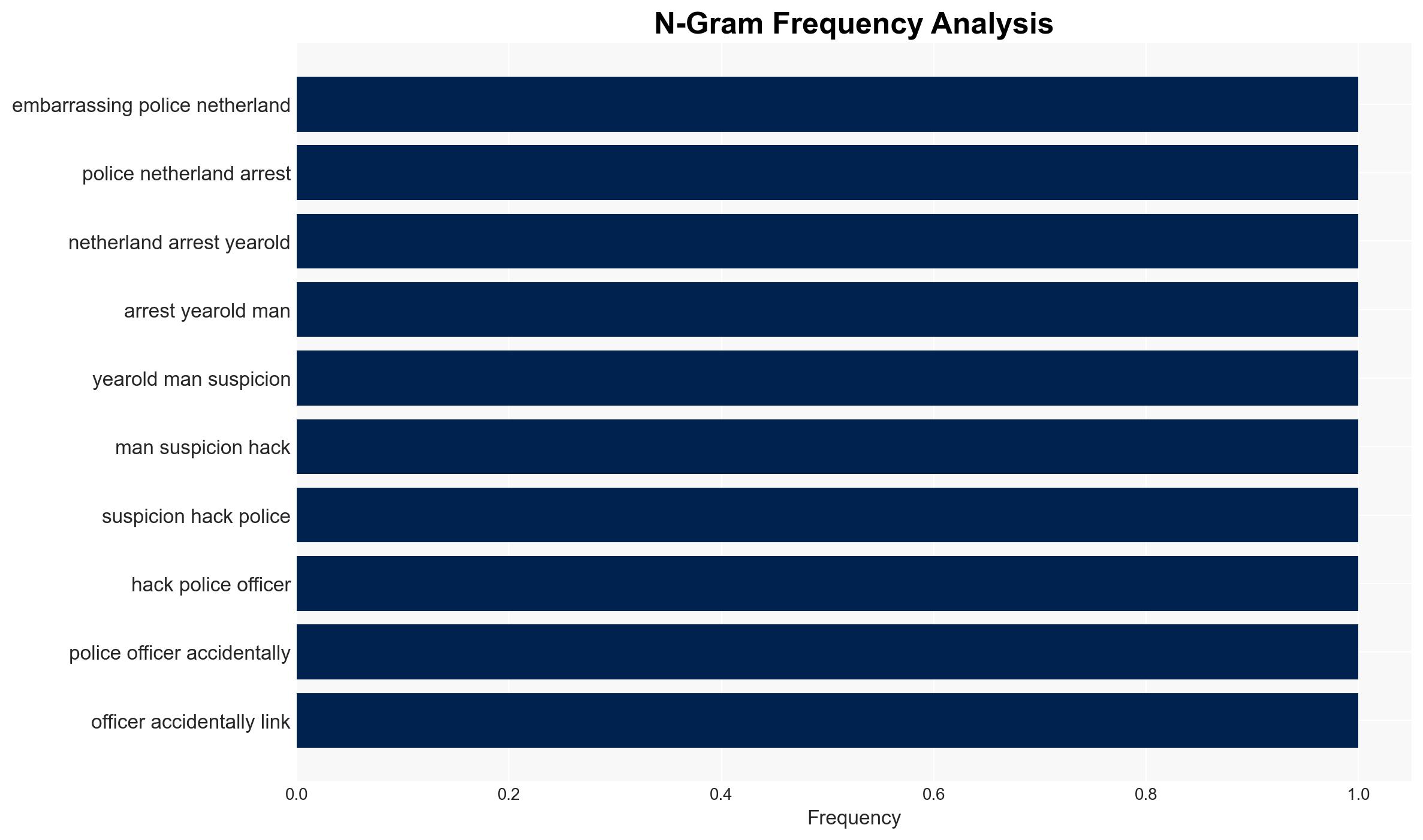
Intelligence Report: Dutch police arrest man for hacking after accidentally sending him confidential files
1. BLUF (Bottom Line Up Front)
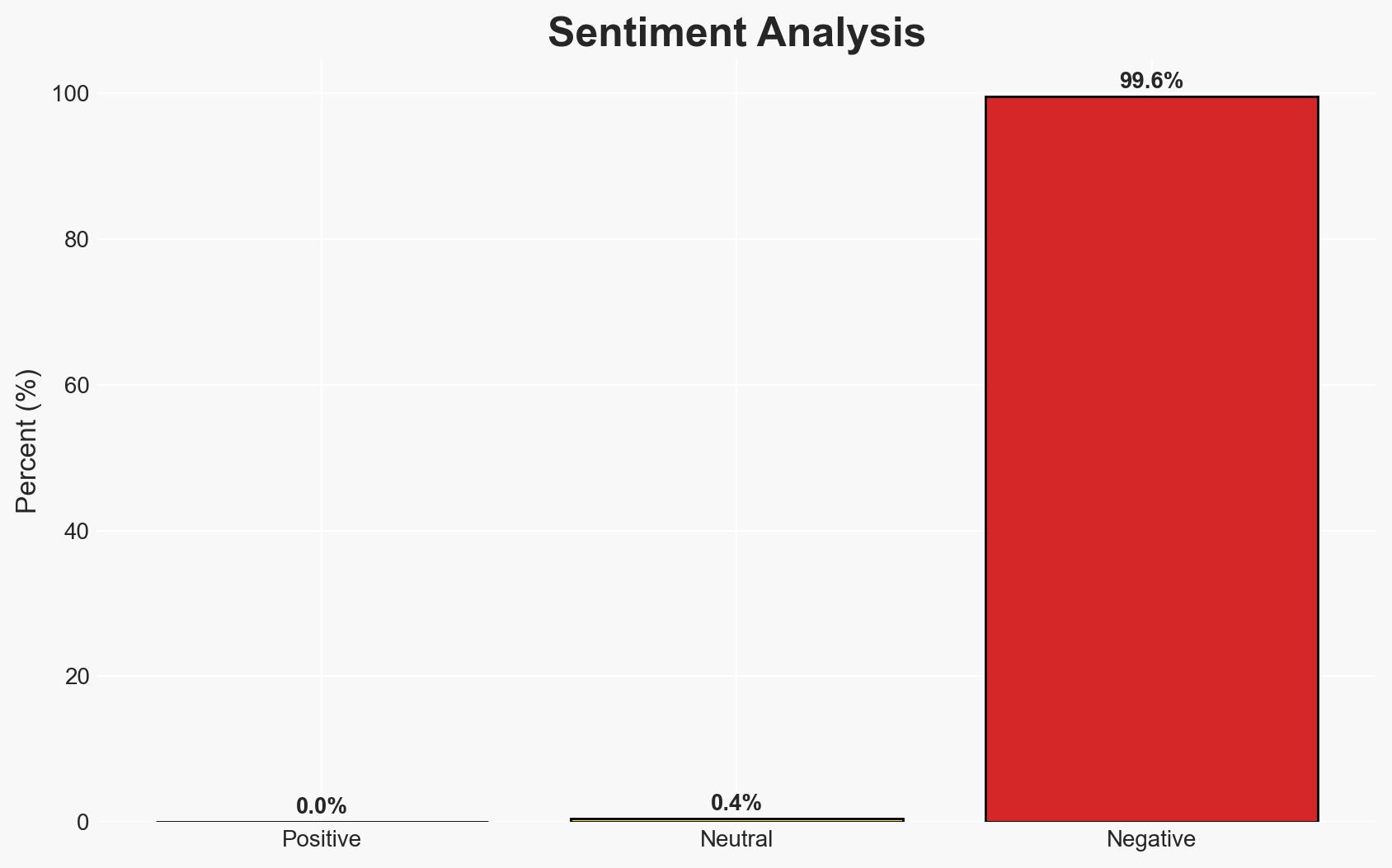
The Dutch police arrested a man for unauthorized access to confidential files after they mistakenly sent him a download link. The incident highlights potential vulnerabilities in police data handling procedures. The most likely hypothesis is that the man exploited the error for personal gain, though his exact intentions remain unclear. This assessment is made with moderate confidence due to limited information on the man’s motivations and the nature of the files accessed.
2. Competing Hypotheses
- Hypothesis A: The man intended to exploit the police’s error for financial gain. Supporting evidence includes his refusal to delete the files without compensation. Contradicting evidence is the lack of clarity on what he demanded in return.
- Hypothesis B: The man acted out of curiosity or misunderstanding, not realizing the legal implications. This is supported by the accidental nature of the access. However, his refusal to comply with police requests suggests otherwise.
- Assessment: Hypothesis A is currently better supported due to the man’s demand for compensation, indicating potential exploitation. Key indicators that could shift this judgment include further details on his demands and any evidence of file distribution.
3. Key Assumptions and Red Flags
- Assumptions: The man understood the nature of the files; the files contained sensitive information; police procedures were not followed correctly.
- Information Gaps: The specific content of the files and the man’s exact demands are unknown.
- Bias & Deception Risks: Potential bias in police reporting to justify their actions; risk of the man’s statements being self-serving.
4. Implications and Strategic Risks
This incident could lead to increased scrutiny of police data handling practices and potential legal reforms. It may also affect public trust in law enforcement’s ability to protect sensitive information.
- Political / Geopolitical: Could prompt legislative reviews of data protection laws.
- Security / Counter-Terrorism: Highlights vulnerabilities in police data systems that could be exploited by malicious actors.
- Cyber / Information Space: Raises concerns about cybersecurity practices within law enforcement agencies.
- Economic / Social: Potential erosion of public trust in police, impacting social cohesion and cooperation with law enforcement.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a thorough review of data handling procedures; ensure secure communication channels; initiate staff training on data security.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity experts; enhance internal audit capabilities; implement robust data protection measures.
- Scenario Outlook:
- Best: Incident leads to improved data security practices without significant legal or public fallout.
- Worst: Files are leaked, leading to legal challenges and loss of public trust.
- Most-Likely: Incident prompts procedural changes and minor public relations issues.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, data breach, law enforcement, unauthorized access, public trust, legal implications, police procedures
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us