CISA Adds Google and Microsoft Vulnerabilities to Known Exploited Catalogue, Urging Immediate Action
Published on: 2026-02-18
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Flaws in Google Microsoft products added to Cisa catalogue
1. BLUF (Bottom Line Up Front)
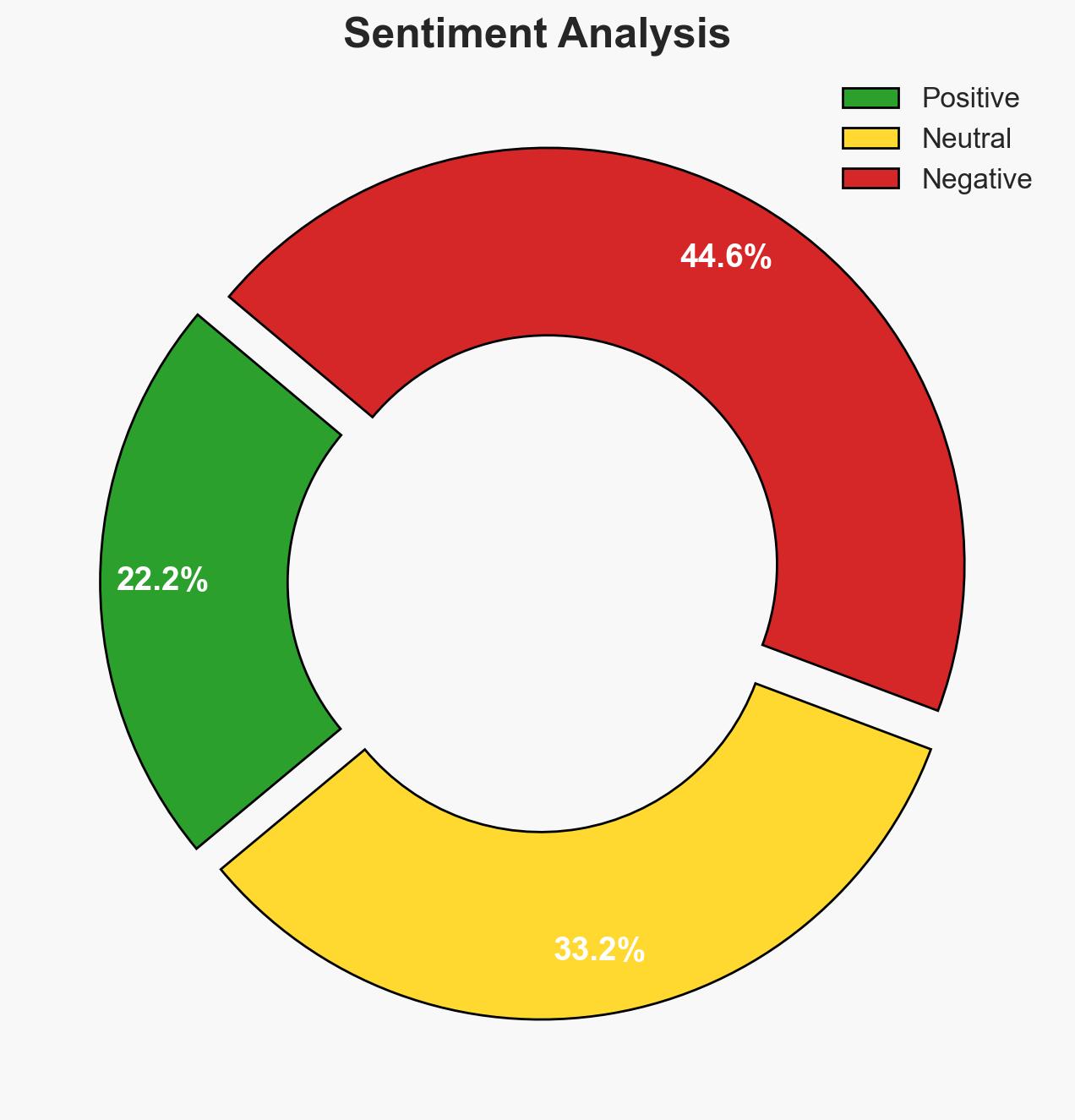
Recent additions to the CISA Known Exploited Vulnerabilities catalogue highlight critical flaws in widely-used software, notably Google Chromium and Microsoft Windows Video ActiveX Control. These vulnerabilities pose significant risks to both public and private sectors, necessitating immediate remediation efforts. The most likely hypothesis is that threat actors will continue exploiting these vulnerabilities due to their widespread presence and potential for high impact. Overall confidence in this assessment is moderate, given the known exploitation in the wild and historical neglect of legacy systems.
2. Competing Hypotheses
- Hypothesis A: Threat actors are exploiting these vulnerabilities primarily due to their high impact and the widespread use of the affected software. Supporting evidence includes the active exploitation of these vulnerabilities and their presence in critical systems. However, uncertainties remain regarding the full scope of exploitation and the specific threat actors involved.
- Hypothesis B: The vulnerabilities are being exploited opportunistically, with no coordinated effort, as attackers leverage any available exploit to gain access. This is supported by the diversity of the vulnerabilities and the pragmatic nature of attackers. Contradicting evidence includes the targeted nature of some attacks, suggesting possible coordination.
- Assessment: Hypothesis A is currently better supported due to the known active exploitation and the strategic value of the affected systems. Key indicators that could shift this judgment include new intelligence on coordinated campaigns or shifts in attacker tactics.
3. Key Assumptions and Red Flags
- Assumptions:
- Organizations have not fully patched legacy systems.
- Threat actors prioritize high-impact vulnerabilities.
- CISA’s catalogue reflects the most critical vulnerabilities.
- Public and private sectors will respond to CISA’s advisories.
- Information Gaps: Detailed intelligence on the specific threat actors exploiting these vulnerabilities and their methods of exploitation.
- Bias & Deception Risks: Potential bias in reporting due to reliance on vendor disclosures; risk of deception if threat actors intentionally mislead about the scope of exploitation.
4. Implications and Strategic Risks
The continued exploitation of these vulnerabilities could lead to significant disruptions in both government and private sector operations, potentially affecting national security and economic stability.
- Political / Geopolitical: Increased tensions with states suspected of harboring cyber actors exploiting these vulnerabilities.
- Security / Counter-Terrorism: Enhanced threat landscape as vulnerabilities provide entry points for espionage or disruptive attacks.
- Cyber / Information Space: Potential for increased cyber espionage and data breaches affecting sensitive information.
- Economic / Social: Economic impacts from data breaches and operational disruptions, potentially affecting public trust and social stability.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Urgent patching of affected systems, enhanced monitoring for signs of exploitation, and dissemination of threat intelligence to relevant stakeholders.
- Medium-Term Posture (1–12 months): Development of resilience measures, including regular security audits and strengthening public-private partnerships for information sharing.
- Scenario Outlook:
- Best: Rapid patching and mitigation efforts prevent significant exploitation.
- Worst: Widespread exploitation leads to major data breaches and operational disruptions.
- Most-Likely: Continued exploitation with gradual mitigation as organizations patch systems.
6. Key Individuals and Entities
- Gunter Ollman, CTO at Cobalt
- Microsoft
- CISA (Cybersecurity and Infrastructure Security Agency)
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, vulnerabilities, public sector, private sector, threat actors, patch management, information security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us