Betterment breach exposes sensitive data of 1.4 million customers, raising serious security concerns
Published on: 2026-02-18
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Betterment data breach might be worse than we thought
1. BLUF (Bottom Line Up Front)
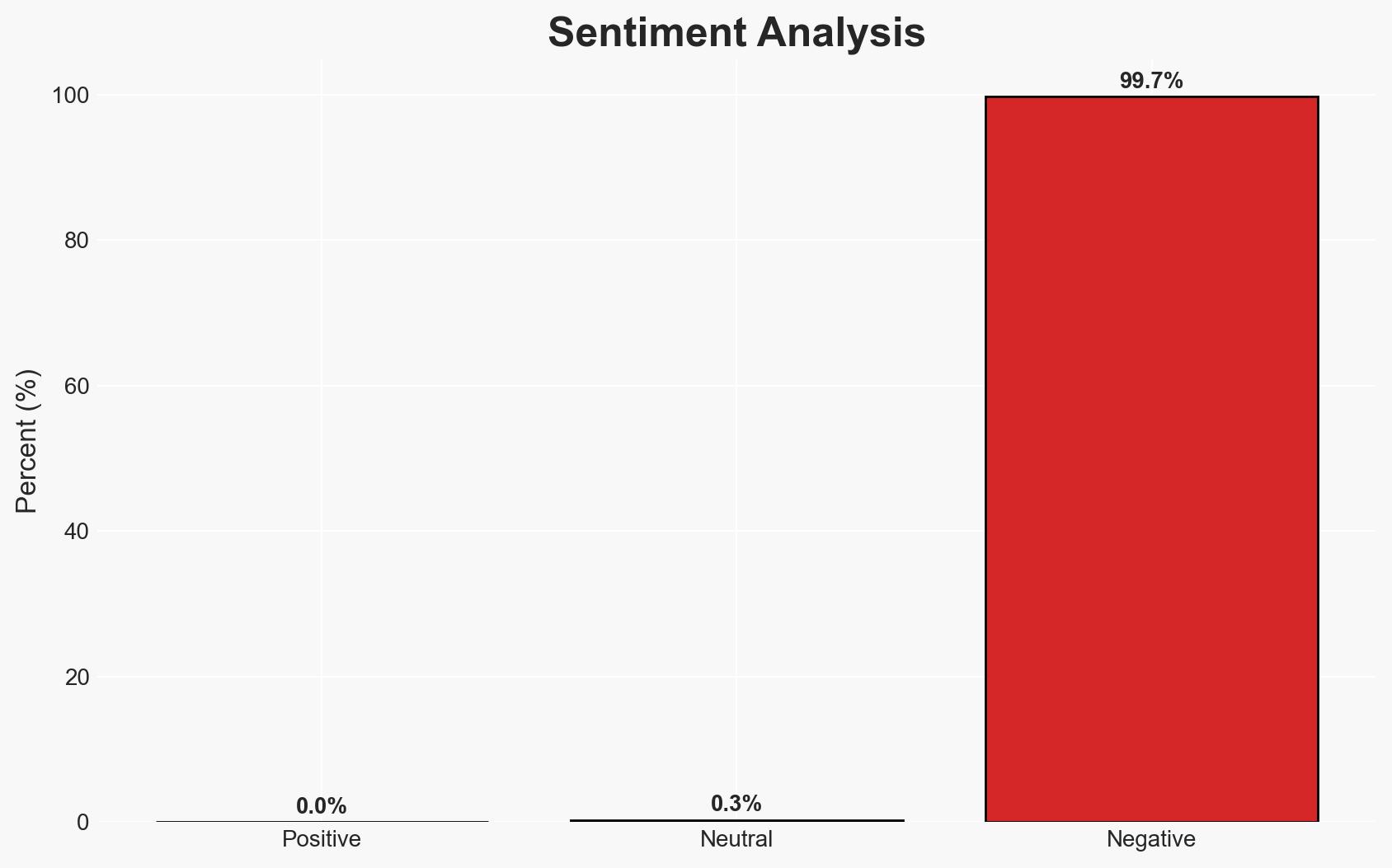
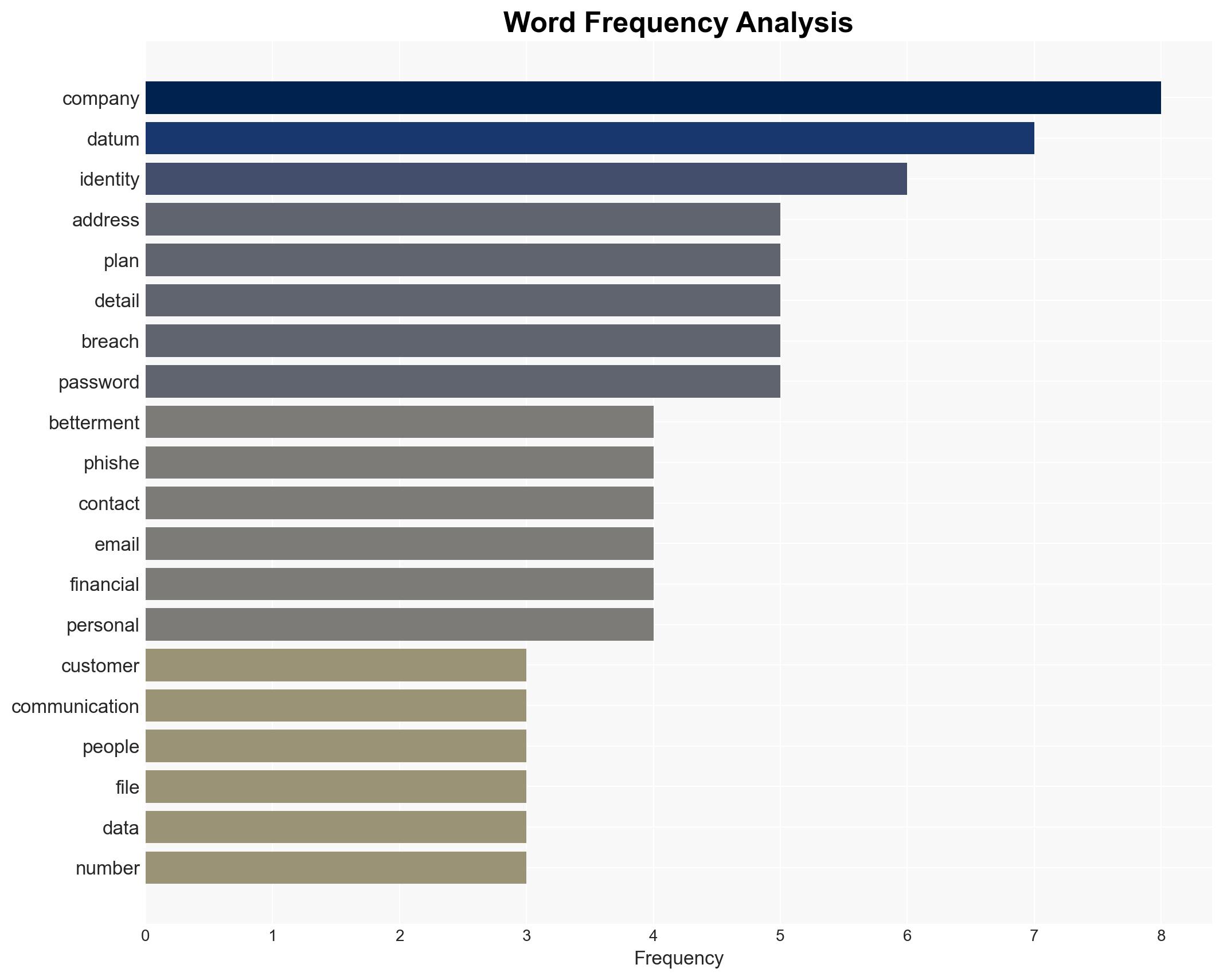
The Betterment data breach has exposed sensitive financial and personal information of approximately 1.4 million customers, potentially enabling targeted phishing attacks and identity theft. The breach’s severity is compounded by the public release of data by the ransomware group Shiny Hunters. This situation poses significant risks to individuals and organizations involved, with moderate confidence in the assessment due to incomplete data on the breach’s full impact.
2. Competing Hypotheses
- Hypothesis A: The breach was primarily a result of inadequate security measures on the third-party platform used by Betterment. Supporting evidence includes the use of social engineering to access the platform, indicating potential vulnerabilities. Contradicting evidence is the lack of detailed information on the security protocols in place at the time.
- Hypothesis B: The breach was orchestrated by a sophisticated cybercriminal group with advanced capabilities, possibly exploiting multiple vulnerabilities. Supporting evidence includes the involvement of the known ransomware group Shiny Hunters and the complexity of the data exfiltrated. Contradicting evidence is the absence of confirmed multi-vector attack details.
- Assessment: Hypothesis B is currently better supported due to the involvement of Shiny Hunters and the nature of the data released. Key indicators that could shift this judgment include new information on the security measures of the third-party platform and any evidence of insider involvement.
3. Key Assumptions and Red Flags
- Assumptions: The data breach was limited to the reported 1.4 million customers; Shiny Hunters’ claims are accurate; Betterment’s security measures were standard for the industry.
- Information Gaps: Detailed security audit reports from Betterment and the third-party platform; confirmation of the exact number of affected individuals; insights into the attackers’ methods and tools.
- Bias & Deception Risks: Potential bias in reporting from Betterment to minimize reputational damage; possible exaggeration by Shiny Hunters to increase perceived threat level; cognitive bias towards assuming sophisticated attack methods.
4. Implications and Strategic Risks
This breach could lead to increased phishing attacks and identity theft, affecting both individuals and organizations. The public release of data may also lead to regulatory scrutiny and legal challenges for Betterment.
- Political / Geopolitical: Potential for increased regulatory actions and international cooperation on cybersecurity standards.
- Security / Counter-Terrorism: Heightened threat environment as cybercriminals exploit the leaked data for targeted attacks.
- Cyber / Information Space: Increased cyber threat activity and potential for further data breaches as attackers leverage the exposed information.
- Economic / Social: Financial instability for affected individuals and potential loss of trust in financial advisory services.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a comprehensive security audit of Betterment and the third-party platform; enhance monitoring for phishing attempts targeting affected individuals.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms to improve resilience; implement advanced threat detection and response capabilities.
- Scenario Outlook:
- Best: Rapid containment and mitigation of the breach’s impact, leading to restored customer trust.
- Worst: Proliferation of secondary breaches and identity theft cases, resulting in significant financial and reputational damage.
- Most-Likely: Ongoing targeted phishing attacks and regulatory scrutiny, with gradual recovery as security measures are enhanced.
6. Key Individuals and Entities
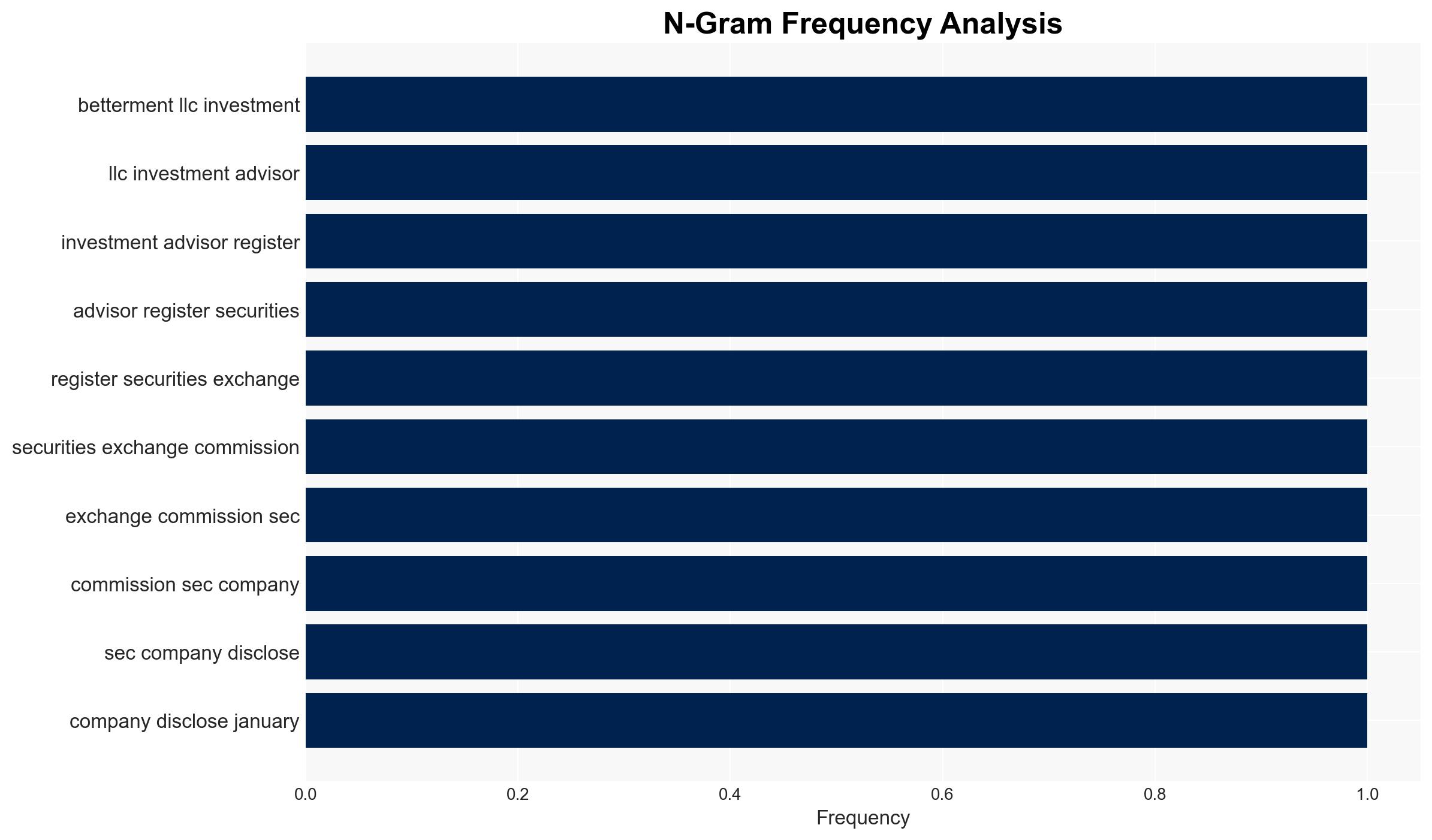
- Betterment LLC
- Shiny Hunters
- US Securities and Exchange Commission (SEC)
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, data breach, financial services, ransomware, identity theft, phishing, regulatory compliance
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us