CarGurus faces potential data leak as ShinyHunters claims theft of 1.7 million corporate records
Published on: 2026-02-20
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
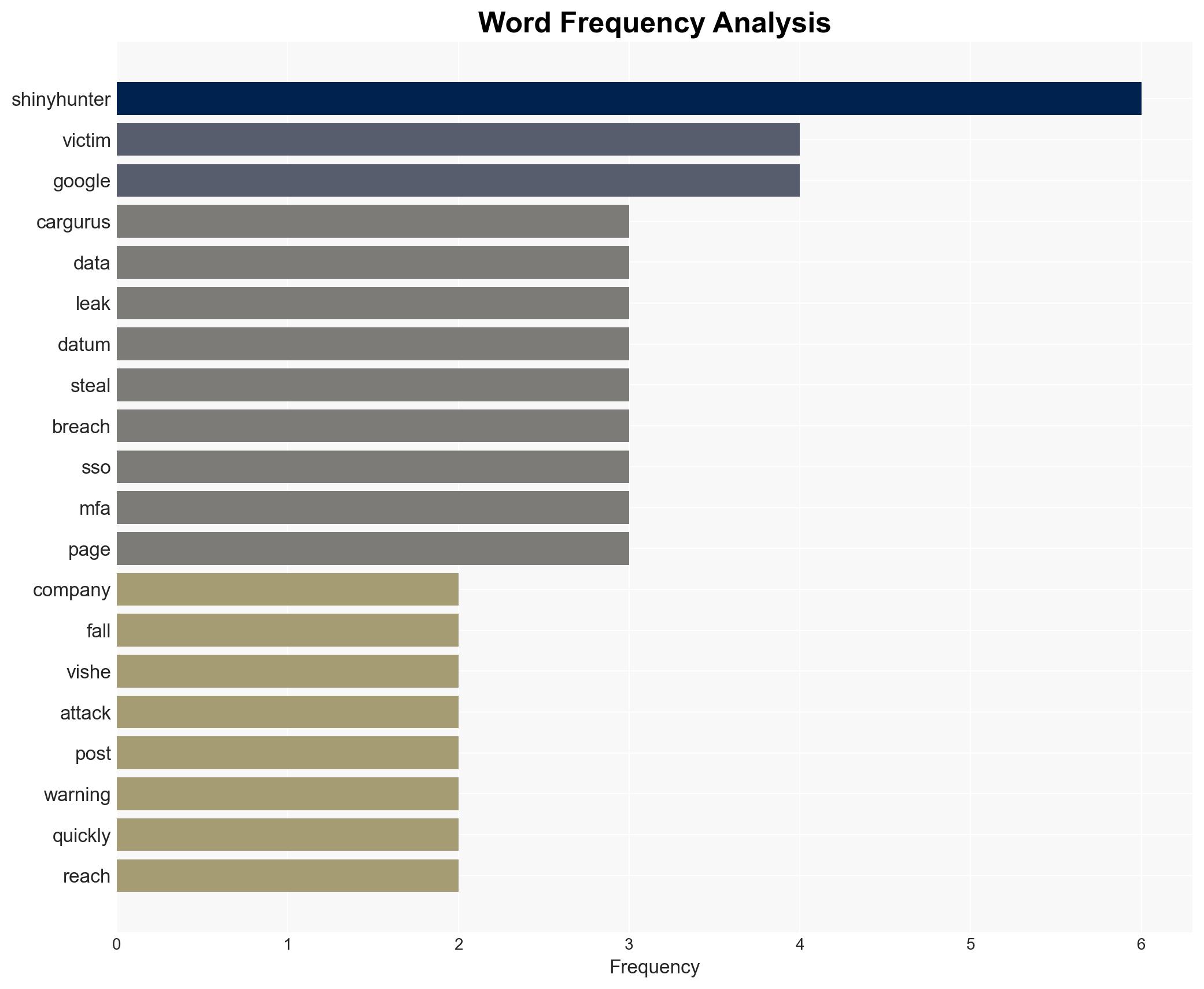
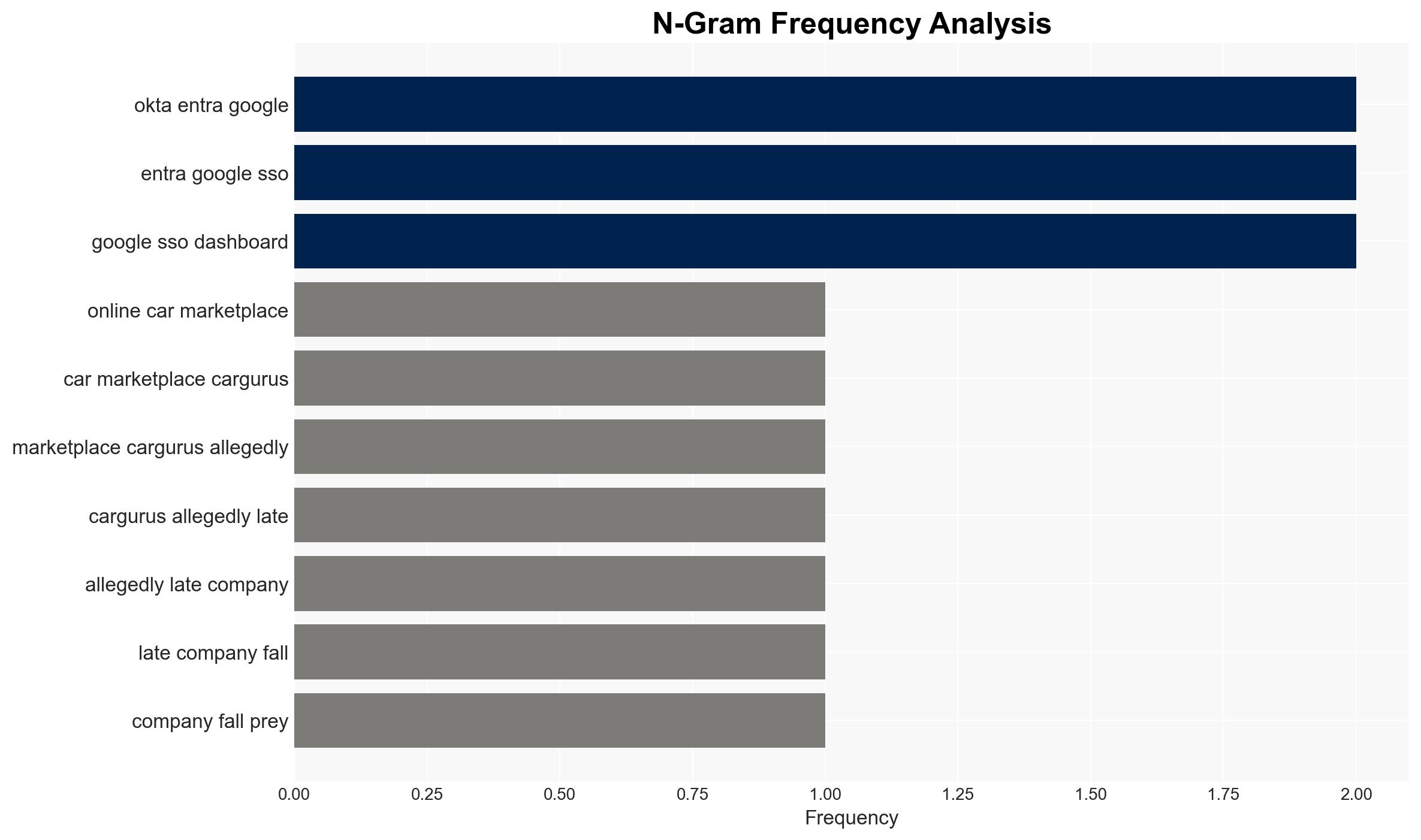
Intelligence Report: Major CarGurus data breach reportedly sees 17 million corporate records stolen
1. BLUF (Bottom Line Up Front)
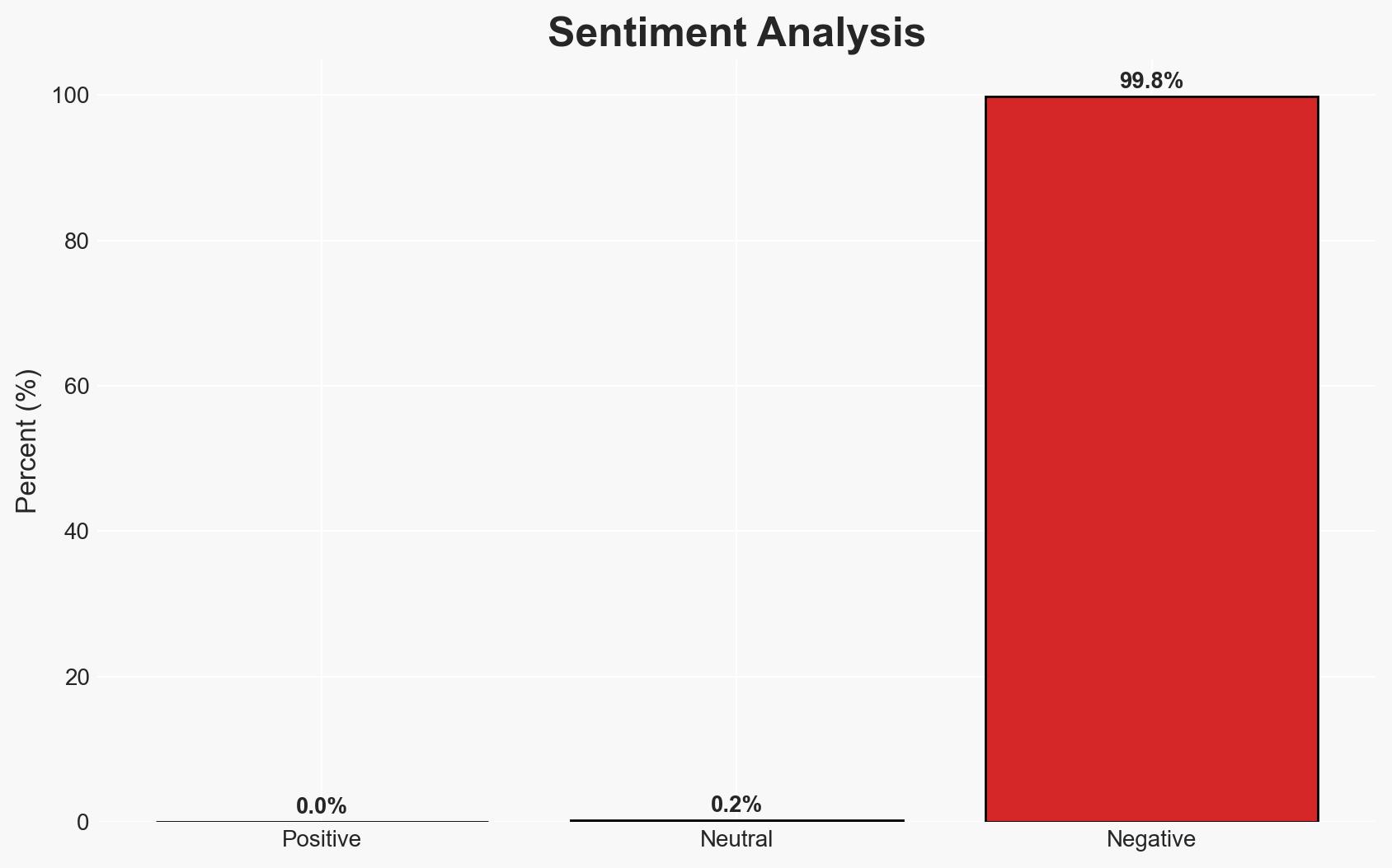
The CarGurus data breach, allegedly executed by the ShinyHunters group, highlights a significant cybersecurity threat involving the theft of 1.7 million records. This incident underscores vulnerabilities in corporate security systems, particularly related to vishing and phishing attacks targeting SSO dashboards. The breach could have extensive implications for CarGurus and its stakeholders. Overall confidence in this assessment is moderate, pending further verification of the breach details.
2. Competing Hypotheses
- Hypothesis A: ShinyHunters successfully breached CarGurus using vishing techniques to compromise SSO dashboards, resulting in the theft of 1.7 million records. This is supported by the group’s established pattern of similar attacks and the detailed methodology described. However, CarGurus has not confirmed the breach, leaving some uncertainty.
- Hypothesis B: The breach claim is a deception or exaggeration by ShinyHunters to extort CarGurus. The lack of confirmation from CarGurus and absence of independent verification of the breach data support this possibility.
- Assessment: Hypothesis A is currently better supported due to ShinyHunters’ history of successful breaches and the detailed attack methodology. Confirmation from CarGurus or independent cybersecurity firms would further solidify this assessment.
3. Key Assumptions and Red Flags
- Assumptions: ShinyHunters has the capability to execute sophisticated vishing attacks; CarGurus’ security infrastructure is vulnerable to such attacks; the data stolen includes sensitive PII.
- Information Gaps: Confirmation of the breach from CarGurus; independent verification of the data’s authenticity and scope; details on the specific data types stolen.
- Bias & Deception Risks: Potential bias in reporting from sources with vested interests; risk of deception by ShinyHunters to inflate their capabilities or extort victims.
4. Implications and Strategic Risks
The CarGurus breach, if confirmed, could lead to increased scrutiny on corporate cybersecurity practices and regulatory pressures. The incident may also embolden other cybercriminal groups to adopt similar tactics.
- Political / Geopolitical: Potential for increased international cooperation on cybersecurity standards and enforcement.
- Security / Counter-Terrorism: Heightened awareness and potential for increased security measures within targeted industries.
- Cyber / Information Space: Possible escalation in vishing and phishing attacks; increased demand for cybersecurity solutions.
- Economic / Social: Potential financial losses for CarGurus and affected individuals; erosion of consumer trust in online marketplaces.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Encourage CarGurus to conduct a thorough forensic investigation and communicate transparently with stakeholders; monitor for further ShinyHunters activities.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms to enhance threat detection and response capabilities; implement robust employee training programs on phishing and vishing threats.
- Scenario Outlook:
- Best Case: Breach is contained with minimal data exposure; CarGurus strengthens its cybersecurity posture.
- Worst Case: Extensive data leak leads to significant financial and reputational damage; similar attacks proliferate.
- Most-Likely: CarGurus confirms breach and takes corrective actions; industry-wide focus on improving security against vishing threats.
6. Key Individuals and Entities
- ShinyHunters (hacking collective)
- CarGurus (targeted company)
- Google and Mandiant (cybersecurity experts)
- Not clearly identifiable from open sources in this snippet for specific individuals.
7. Thematic Tags
cybersecurity, data breach, vishing, phishing, corporate security, ShinyHunters, SSO vulnerabilities
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us