Nation-state cyberattacks on critical infrastructure escalate, threatening global security and sensitive data.
Published on: 2026-02-20
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: News brief Nation-state hackers active on the global stage
1. BLUF (Bottom Line Up Front)
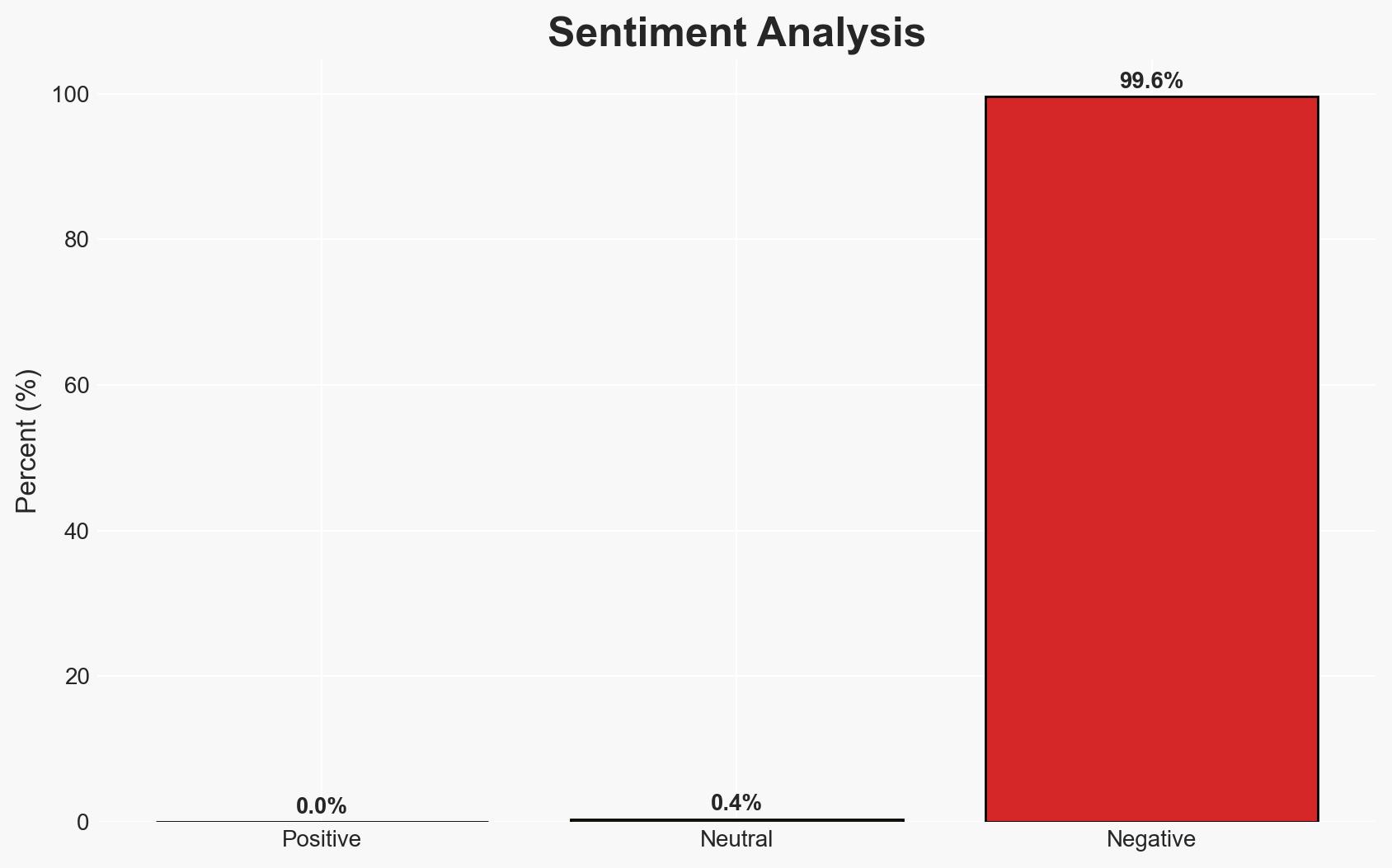
Nation-state hackers are increasingly targeting critical infrastructure globally, with significant implications for national security and economic stability. The most likely hypothesis is that these attacks are state-sponsored efforts to gain strategic advantages and disrupt adversaries’ capabilities. Affected sectors include defense, telecommunications, and biometric databases. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: Nation-state hackers are conducting coordinated cyber campaigns to disrupt critical infrastructure and steal sensitive data for strategic military and economic advantages. This is supported by evidence of attacks on defense firms and the use of sophisticated techniques. However, the specific motivations and long-term goals of these campaigns remain uncertain.
- Hypothesis B: The increase in cyberattacks is primarily driven by non-state actors and criminal groups exploiting geopolitical tensions for financial gain. While some attacks are attributed to nation-states, the involvement of criminal groups like the Green Blood Group suggests a mixed threat landscape. Contradicting evidence includes the lack of direct attribution to nation-states in some cases.
- Assessment: Hypothesis A is currently better supported due to the involvement of state-sponsored groups from China, Russia, and North Korea, as well as the strategic nature of the targeted sectors. Indicators that could shift this judgment include evidence of financial motivations or direct links to criminal enterprises.
3. Key Assumptions and Red Flags
- Assumptions: Nation-state actors have the capability and intent to conduct sophisticated cyber operations; critical infrastructure vulnerabilities are exploitable; geopolitical tensions drive cyber operations.
- Information Gaps: Detailed attribution of specific attacks to nation-states; comprehensive understanding of attackers’ long-term objectives; data on the effectiveness of defensive measures.
- Bias & Deception Risks: Potential bias in attributing attacks to nation-states without conclusive evidence; risk of deception by attackers to mislead attribution efforts.
4. Implications and Strategic Risks
The escalation of nation-state cyberattacks on critical infrastructure could lead to increased geopolitical tensions and destabilization of global security. Over time, these developments may prompt nations to enhance their cyber defenses and engage in retaliatory cyber operations.
- Political / Geopolitical: Heightened tensions between nation-states, potential for cyber warfare escalation.
- Security / Counter-Terrorism: Increased vulnerability of defense systems and critical infrastructure, necessitating enhanced security measures.
- Cyber / Information Space: Greater emphasis on cybersecurity resilience and incident response capabilities; potential for misinformation campaigns.
- Economic / Social: Disruption of essential services could impact economic stability and public trust in government institutions.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of critical infrastructure networks; conduct vulnerability assessments; improve information sharing between government and private sectors.
- Medium-Term Posture (1–12 months): Develop resilience measures, including advanced threat detection capabilities; strengthen international partnerships for cyber defense collaboration.
- Scenario Outlook:
- Best: Improved international cooperation leads to reduced cyber threats.
- Worst: Escalation into cyber warfare with significant infrastructure disruptions.
- Most-Likely: Continued cyberattacks with incremental improvements in defense capabilities.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, nation-state cyberattacks, critical infrastructure, espionage, defense sector, geopolitical tensions, cyber resilience
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us