Five Ways the Signal Leak Could be Trouble for Trump – Antiwar.com
Published on: 2025-04-01
Intelligence Report: Five Ways the Signal Leak Could be Trouble for Trump – Antiwar.com
1. BLUF (Bottom Line Up Front)
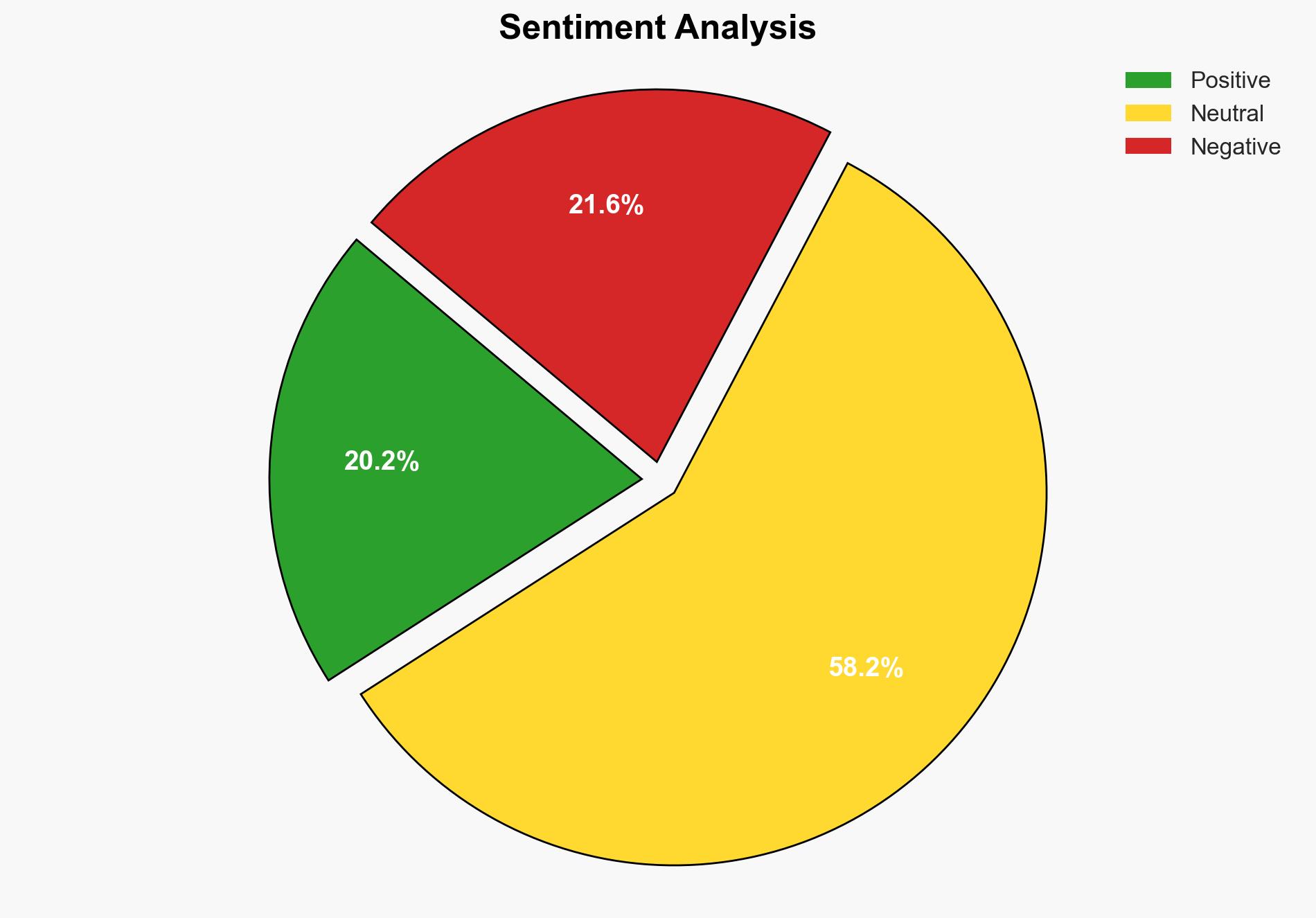
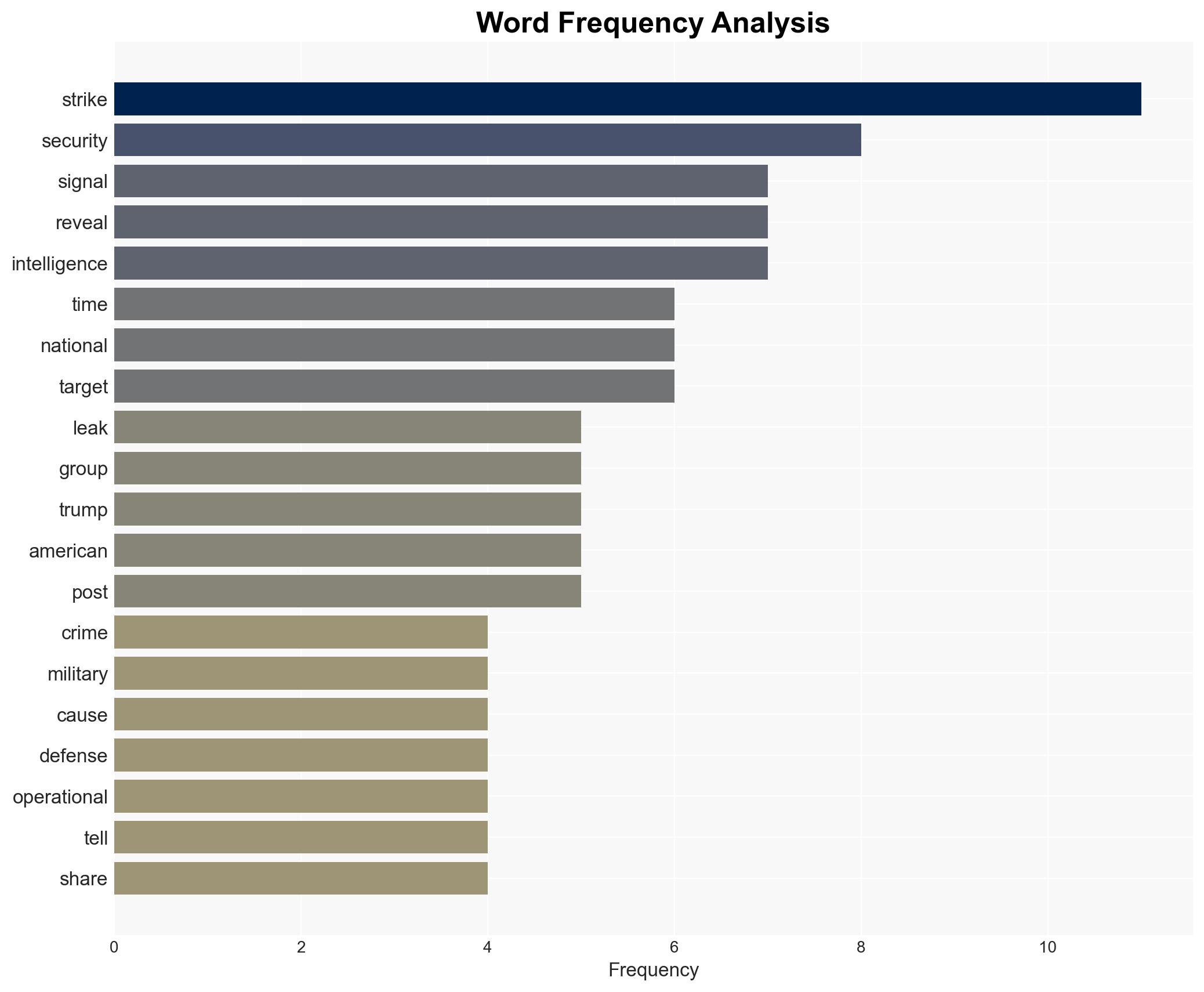
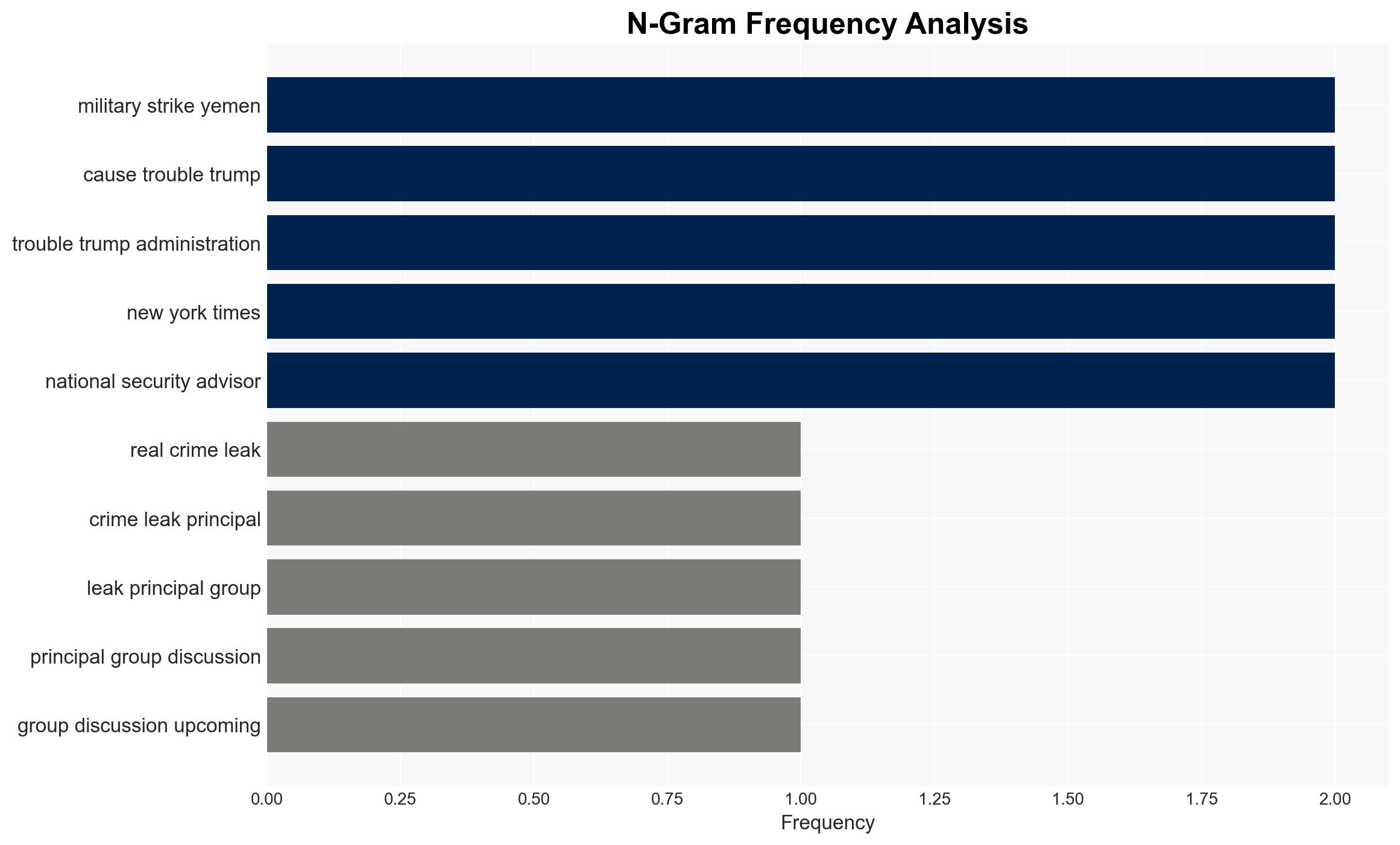
The recent leak of sensitive military discussions via the Signal app poses significant risks to national security and operational integrity. The leak, which involved discussions of military strikes in Yemen, has raised concerns about the potential violation of the Espionage Act and operational security protocols. Key findings indicate that the leak could undermine trust with international allies and expose vulnerabilities in communication channels. Immediate actions are recommended to address security breaches and reinforce communication protocols.
2. Detailed Analysis
The following structured analytic techniques have been applied for this analysis:
General Analysis
The leak involved discussions of a military strike in Yemen, revealing sensitive operational details such as launch times and target locations. This breach of operational security could enable adversaries to anticipate military actions, thereby endangering personnel and compromising mission success. The use of the Signal app for such discussions, as reported, raises questions about the legality and appropriateness of the communication method. The incident has sparked debate over the handling of classified information and the potential for legal repercussions under the Espionage Act.
3. Implications and Strategic Risks
The leak presents several strategic risks:
- **National Security**: Compromised military operations may lead to increased threats to personnel and assets.
- **Regional Stability**: Escalation of conflict in Yemen could destabilize the region further.
- **Economic Interests**: Disruptions in the region may impact global trade routes and energy supplies.
- **Allied Trust**: The breach may erode trust with international partners, affecting intelligence sharing and cooperation.
4. Recommendations and Outlook
Recommendations:
- Enhance security protocols for handling and discussing classified information.
- Implement stricter controls and oversight on communication platforms used for sensitive discussions.
- Conduct a thorough investigation to identify and address the source of the leak.
Outlook:
Best-case scenario: Immediate corrective actions restore trust and prevent further leaks, maintaining operational integrity and allied cooperation.
Worst-case scenario: Continued breaches lead to significant operational failures and strained international relations.
Most likely outcome: Incremental improvements in security measures reduce the risk of future leaks, though trust rebuilding with allies may take time.
5. Key Individuals and Entities
The report mentions several individuals involved in the discussions and subsequent fallout:
- Donald Trump
- Jeffrey Goldberg
- Pete Hegseth
- Tulsi Gabbard
- John Ratcliffe
- Mike Waltz
- Vance
- Ben Hodge
These individuals are central to the discussions and the subsequent analysis of the leak’s impact.