Whoops T-Mobile Reveals Names Real-Time Locations Of Customers Kids – Techdirt
Published on: 2025-04-08
Intelligence Report: Whoops T-Mobile Reveals Names Real-Time Locations Of Customers Kids – Techdirt
1. BLUF (Bottom Line Up Front)
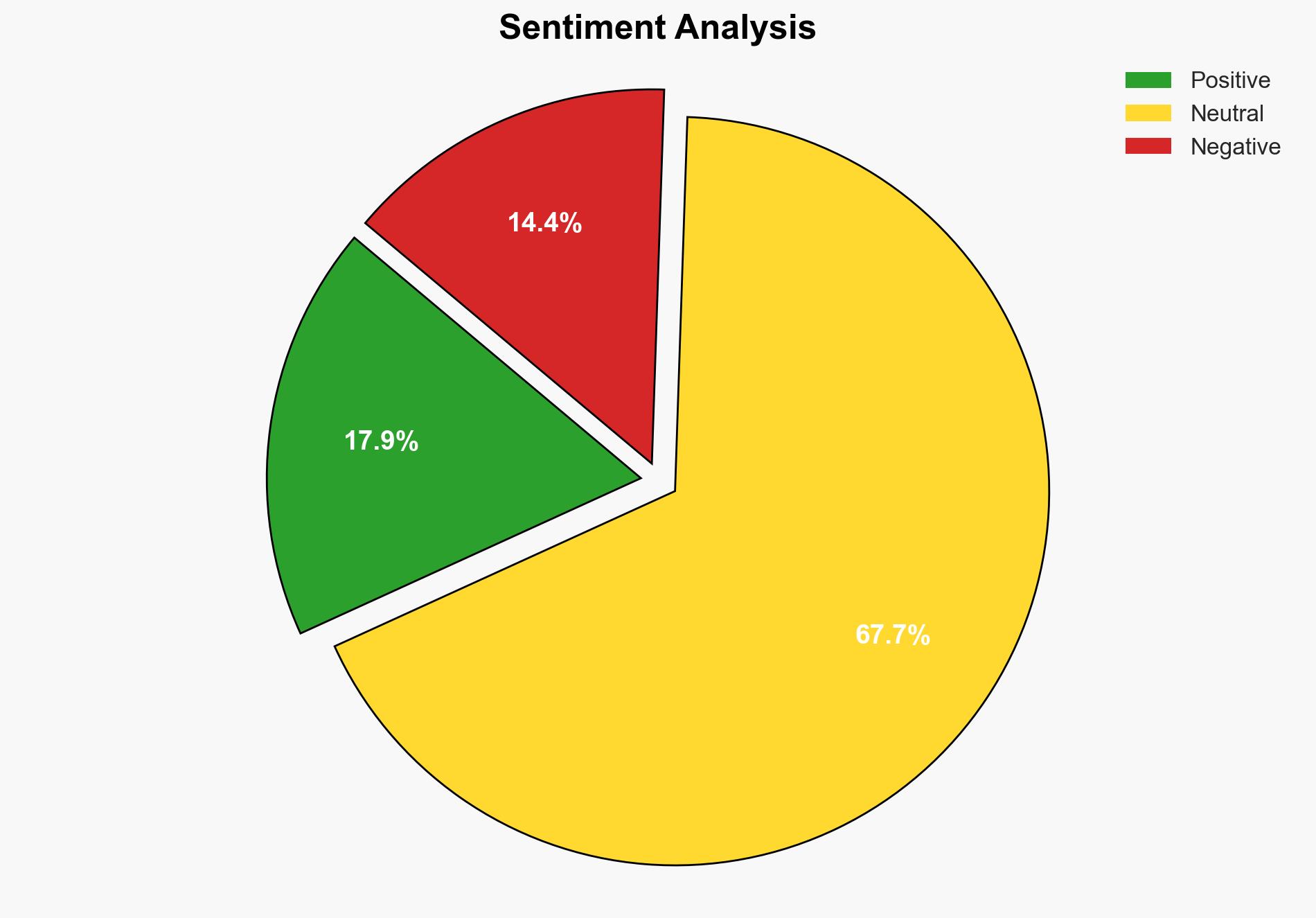
A recent security breach at T-Mobile has exposed the names and real-time locations of customers’ children, raising significant privacy and security concerns. The incident highlights vulnerabilities in T-Mobile’s data protection measures and underscores the need for stronger regulatory oversight. Immediate action is required to address these security lapses and prevent future occurrences.
2. Detailed Analysis
The following structured analytic techniques have been applied for this analysis:
General Analysis
The breach occurred due to an apparent bug in T-Mobile’s SyncUp service, which is designed to allow parents to monitor their children’s locations. This flaw resulted in unauthorized access to sensitive data, including names, photos, and real-time locations of children. The incident has been linked to a broader pattern of security issues at T-Mobile, exacerbated by the company’s merger with Sprint. The lack of robust data protection protocols and the company’s focus on monetizing user data have contributed to repeated privacy failures.
3. Implications and Strategic Risks
The exposure of children’s real-time locations poses significant risks to personal safety and privacy. It also raises concerns about the potential for misuse of data by malicious actors. The incident could lead to increased scrutiny from regulators and lawmakers, potentially resulting in stricter privacy laws and regulations. Additionally, the breach may damage T-Mobile’s reputation, affecting customer trust and market position.
4. Recommendations and Outlook
Recommendations:
- Enhance data protection measures by implementing advanced encryption and access controls.
- Conduct regular security audits and vulnerability assessments to identify and mitigate risks.
- Advocate for comprehensive privacy legislation to strengthen consumer data protection.
- Increase transparency with customers regarding data collection and usage practices.
Outlook:
In the best-case scenario, T-Mobile addresses the security flaws promptly, restoring customer trust and avoiding regulatory penalties. In the worst-case scenario, continued breaches could lead to significant financial losses and stricter regulatory actions. The most likely outcome is increased regulatory scrutiny and gradual improvements in data protection practices.
5. Key Individuals and Entities
The report mentions significant individuals and organizations but does not provide any roles or affiliations. Key individuals include Jenna, a parent affected by the breach. The primary organization involved is T-Mobile.