Clop Ransomware Hack Of WK Kellogg Shows Growing Threat To Your Data – Forbes
Published on: 2025-04-08
Intelligence Report: Clop Ransomware Hack Of WK Kellogg Shows Growing Threat To Your Data – Forbes
1. BLUF (Bottom Line Up Front)
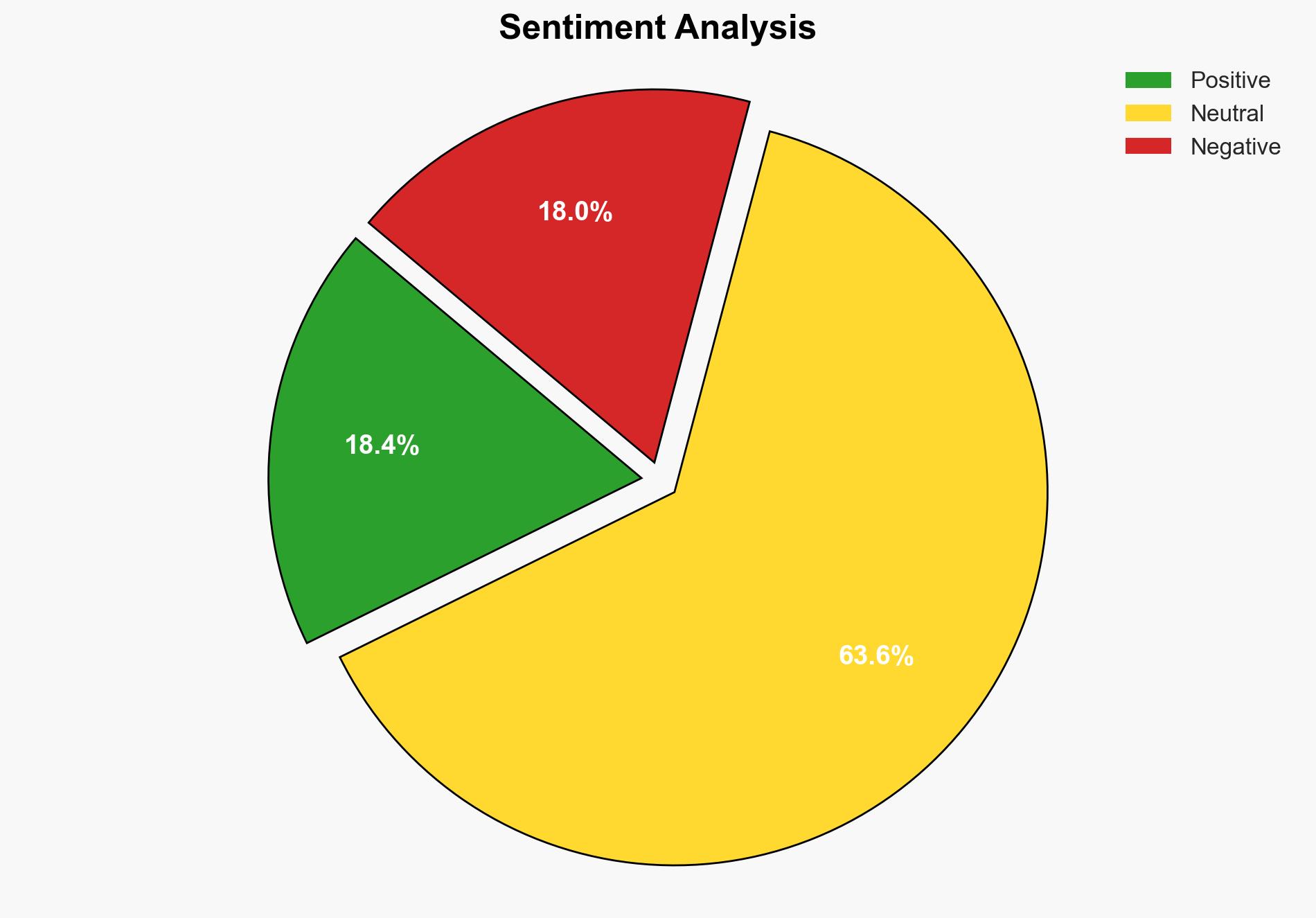
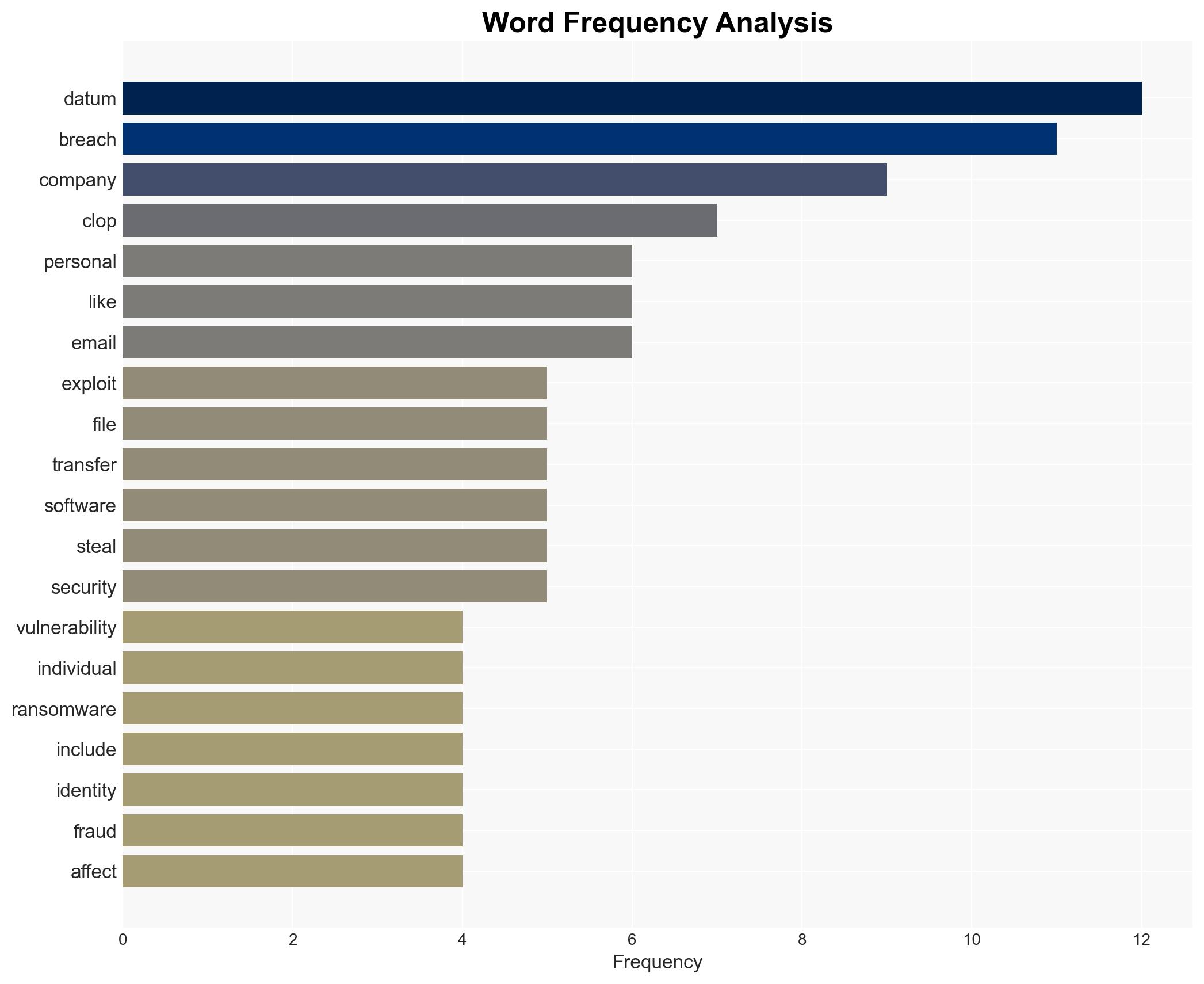
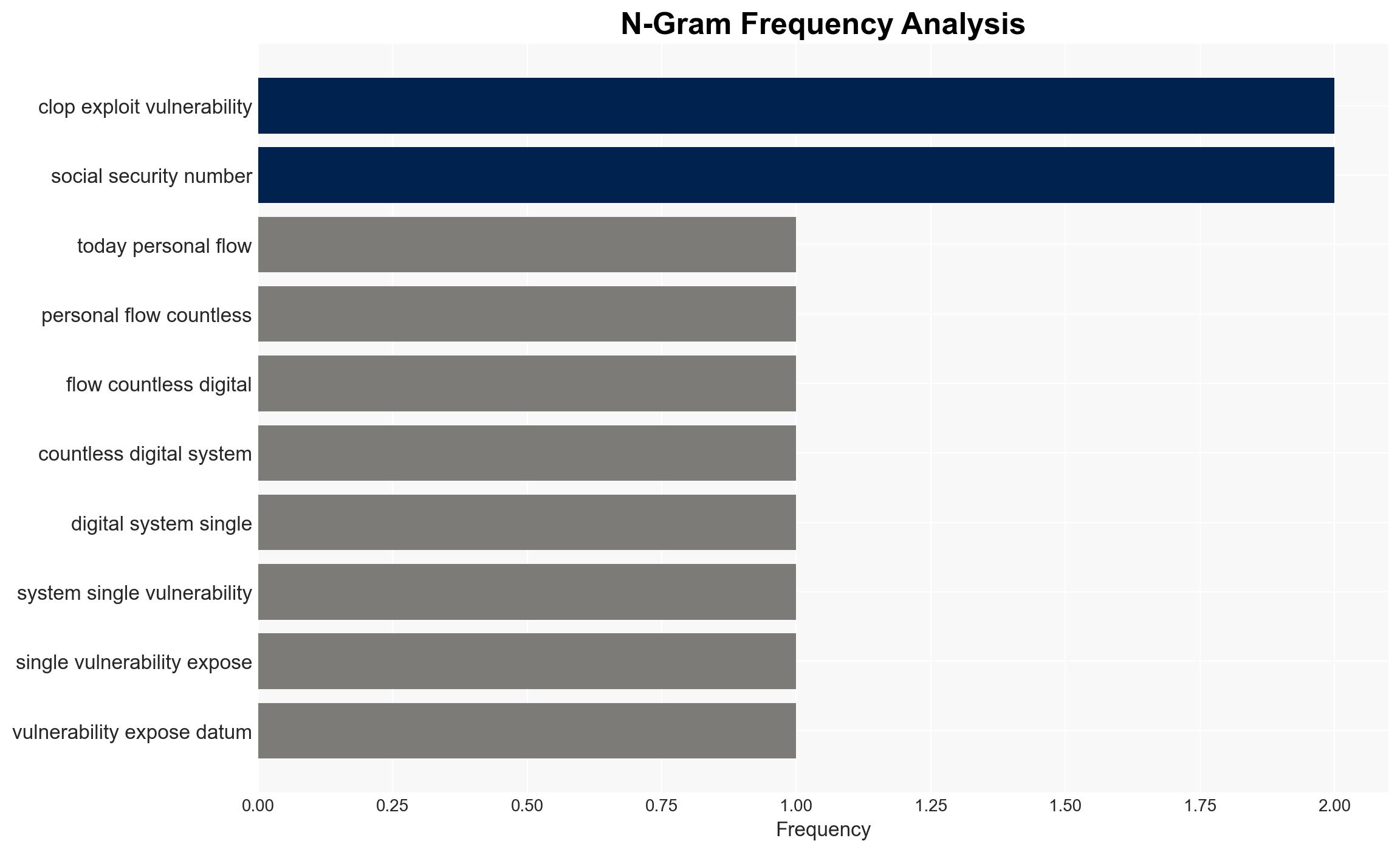
The Clop ransomware group has executed a significant cyberattack on WK Kellogg, exploiting vulnerabilities in Cleo file transfer software. This breach has compromised sensitive personal data, including names and social security numbers, of employees and customers. The incident underscores the growing threat of ransomware attacks targeting large corporations, with potential repercussions for individuals whose data is exposed. Immediate actions are recommended to mitigate risks and enhance cybersecurity measures.
2. Detailed Analysis
The following structured analytic techniques have been applied for this analysis:
General Analysis
The Clop ransomware group has a history of exploiting vulnerabilities in file transfer tools, previously targeting MOVEit and Accellion software. The attack on WK Kellogg is part of a broader trend of ransomware groups focusing on high-profile targets to maximize impact and ransom demands. The breach has resulted in the unauthorized access and theft of sensitive data, posing risks of identity theft and financial fraud for affected individuals. The attack highlights the critical need for organizations to secure their digital infrastructures and for individuals to remain vigilant about their personal data security.
3. Implications and Strategic Risks
The breach poses significant risks to national security, economic interests, and individual privacy. The exposure of personal data can lead to identity theft, financial fraud, and phishing scams, affecting both individuals and businesses. The attack also underscores vulnerabilities in widely used enterprise software, raising concerns about the security of digital infrastructures across various sectors. The incident could lead to increased regulatory scrutiny and demand for improved cybersecurity measures.
4. Recommendations and Outlook
Recommendations:
- Enhance cybersecurity protocols by regularly updating and patching software vulnerabilities.
- Implement robust data encryption and access controls to protect sensitive information.
- Conduct regular cybersecurity training for employees to recognize and respond to phishing attempts.
- Encourage organizations to collaborate with cybersecurity experts to assess and improve their security posture.
Outlook:
In the best-case scenario, organizations will strengthen their cybersecurity measures, reducing the likelihood of future breaches. In the worst-case scenario, continued vulnerabilities could lead to more frequent and severe attacks, with widespread implications for individuals and businesses. The most likely outcome is an increased focus on cybersecurity, driven by regulatory requirements and the need to protect sensitive data.
5. Key Individuals and Entities
The report mentions significant individuals and organizations, including Clop and WK Kellogg. These entities are central to the analysis, with Clop being the perpetrator of the attack and WK Kellogg the primary victim. The involvement of Cleo software highlights the importance of securing third-party tools used in data transfer processes.