TVT DVRs become prime target for Mirai botnet – TechRadar
Published on: 2025-04-09
Intelligence Report: TVT DVRs become prime target for Mirai botnet – TechRadar
1. BLUF (Bottom Line Up Front)
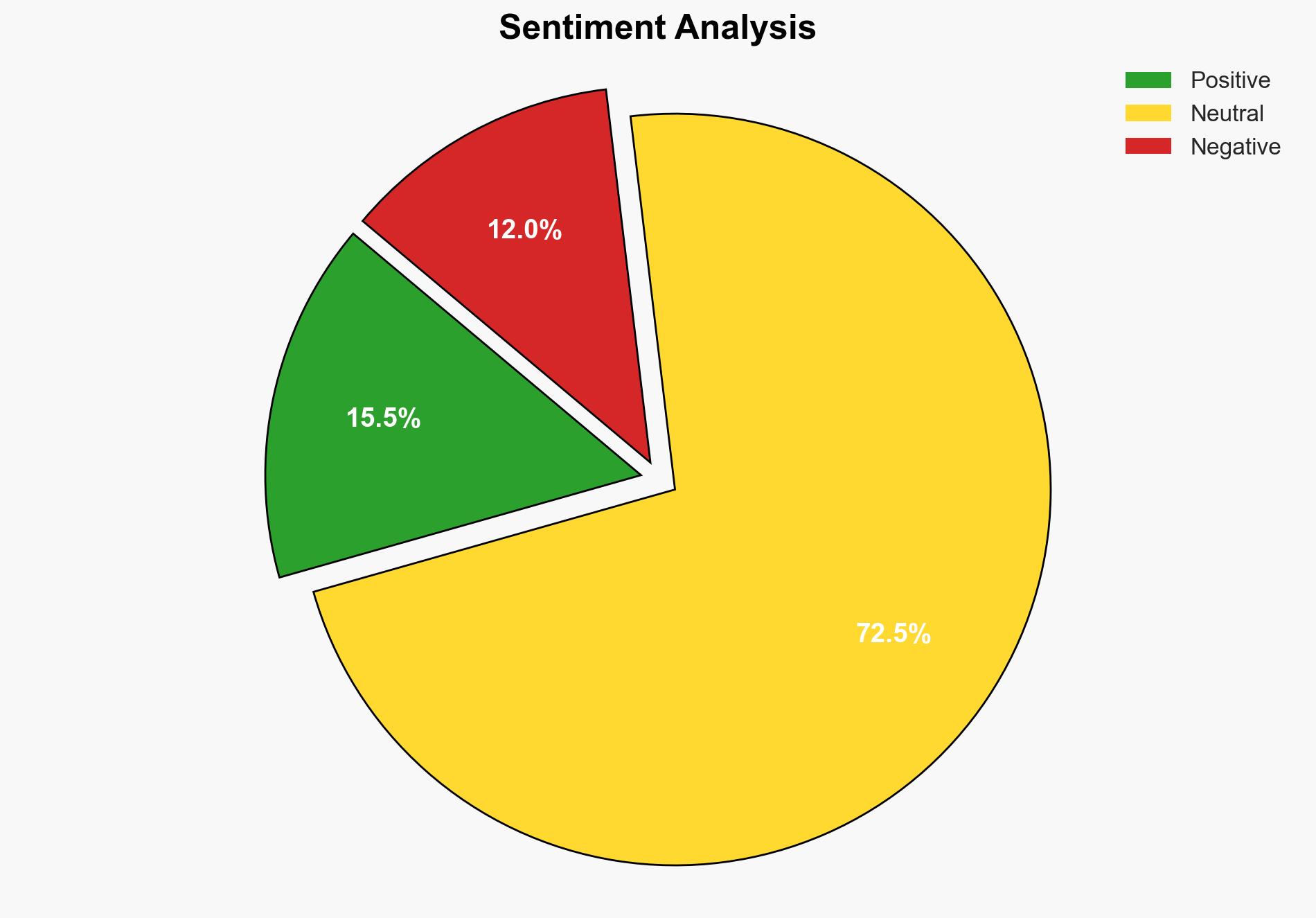
The Mirai botnet is actively targeting TVT DVRs due to a vulnerability that allows unauthorized access and control. This poses a significant threat to cybersecurity, as compromised devices can be used for disruptive activities such as Distributed Denial of Service (DDoS) attacks. Immediate action is recommended to patch affected systems and enhance monitoring to prevent exploitation.
2. Detailed Analysis
The following structured analytic techniques have been applied for this analysis:
General Analysis
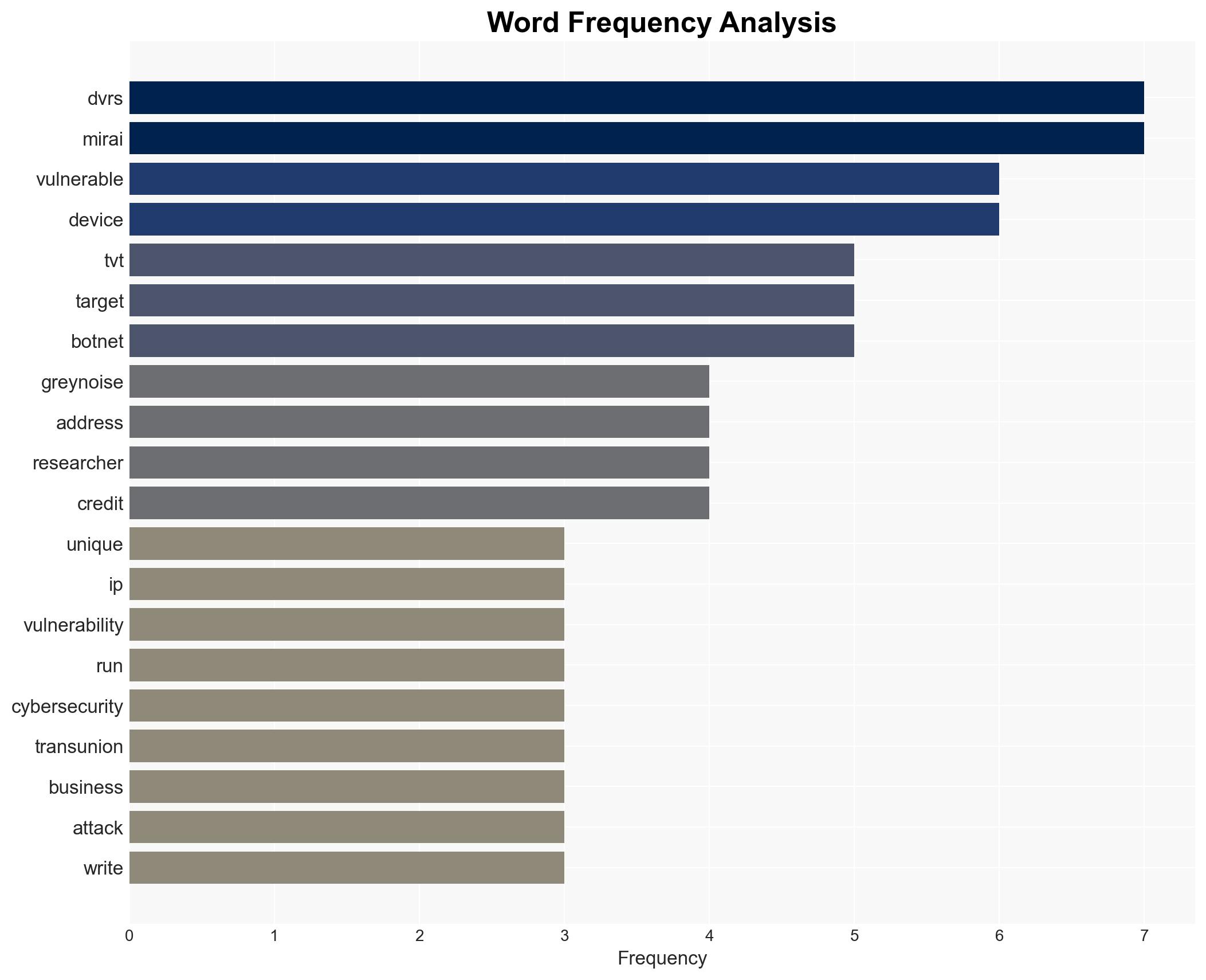
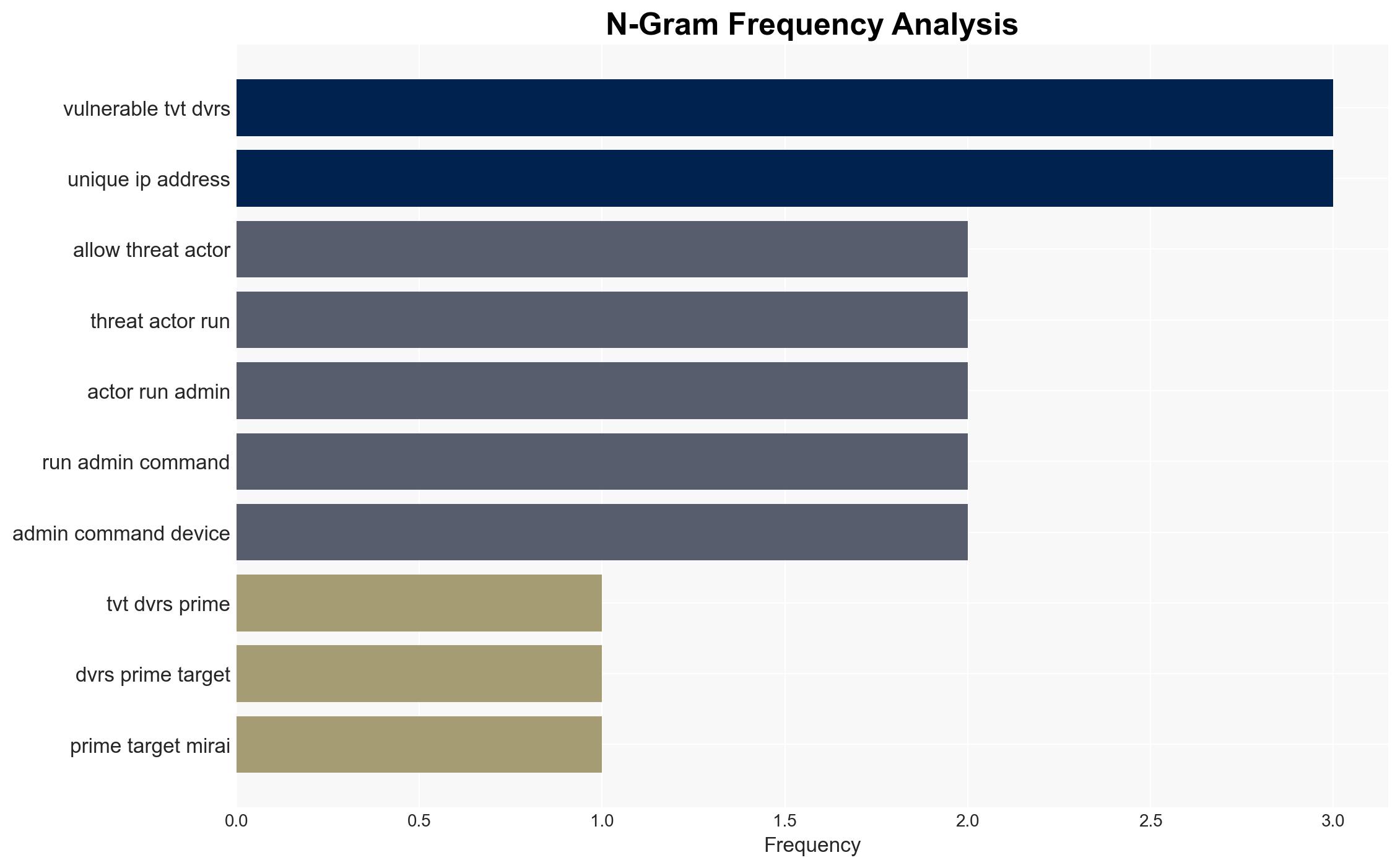
The vulnerability in TVT DVRs, manufactured by Shenzhen-based TVT Digital Technology, allows threat actors to bypass authentication and execute administrative commands. This has led to a surge in scanning activity by the Mirai botnet operators, as reported by cybersecurity researchers. The vulnerability affects NVMS DVRs with versions prior to the latest patch. The exploitation attempts have been notably high, with unique IP addresses from regions such as Taiwan, Japan, and South Korea being involved.
3. Implications and Strategic Risks
The exploitation of TVT DVRs by the Mirai botnet poses several strategic risks:
- Increased potential for large-scale DDoS attacks, disrupting critical infrastructure and services.
- Compromised devices could be leveraged for further cyber-attacks, affecting national security and economic stability.
- The vulnerability highlights the broader risk associated with IoT devices and their security weaknesses.
4. Recommendations and Outlook
Recommendations:
- Immediate patching of affected TVT DVRs to prevent unauthorized access.
- Enhanced network monitoring to detect and respond to unusual scanning activities.
- Development of regulatory frameworks to ensure IoT device security standards.
Outlook:
Best-case scenario: Rapid patch deployment and improved security measures reduce the risk of exploitation, minimizing the impact of the botnet.
Worst-case scenario: Failure to address vulnerabilities leads to widespread DDoS attacks, causing significant disruption to services and economic activities.
Most likely outcome: A mixed response with partial mitigation, leading to continued but reduced risk of exploitation.
5. Key Individuals and Entities
The report mentions significant individuals and organizations:
- Greynoise – Cybersecurity research entity reporting on scanning activities.
- SSD Secure Disclosure – Security researchers who reported the vulnerability.
- Akamai – Security researchers involved in identifying new botnet variants.
- Sead – A journalist providing insights into cybersecurity trends.