Beware these dangerous fake Microsoft Office add-ons are spreading malware – TechRadar
Published on: 2025-04-09
Intelligence Report: Beware these dangerous fake Microsoft Office add-ons are spreading malware – TechRadar
1. BLUF (Bottom Line Up Front)
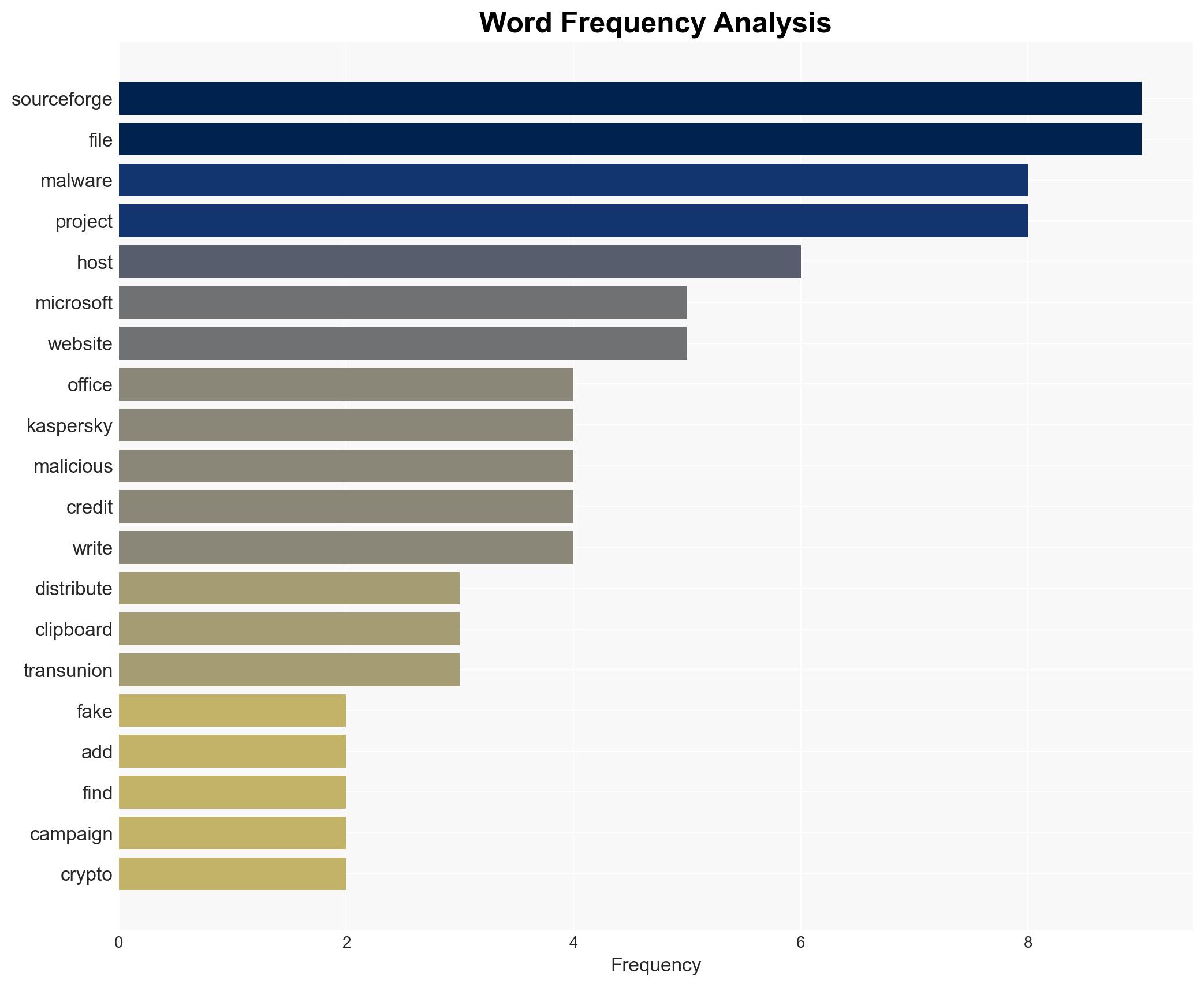
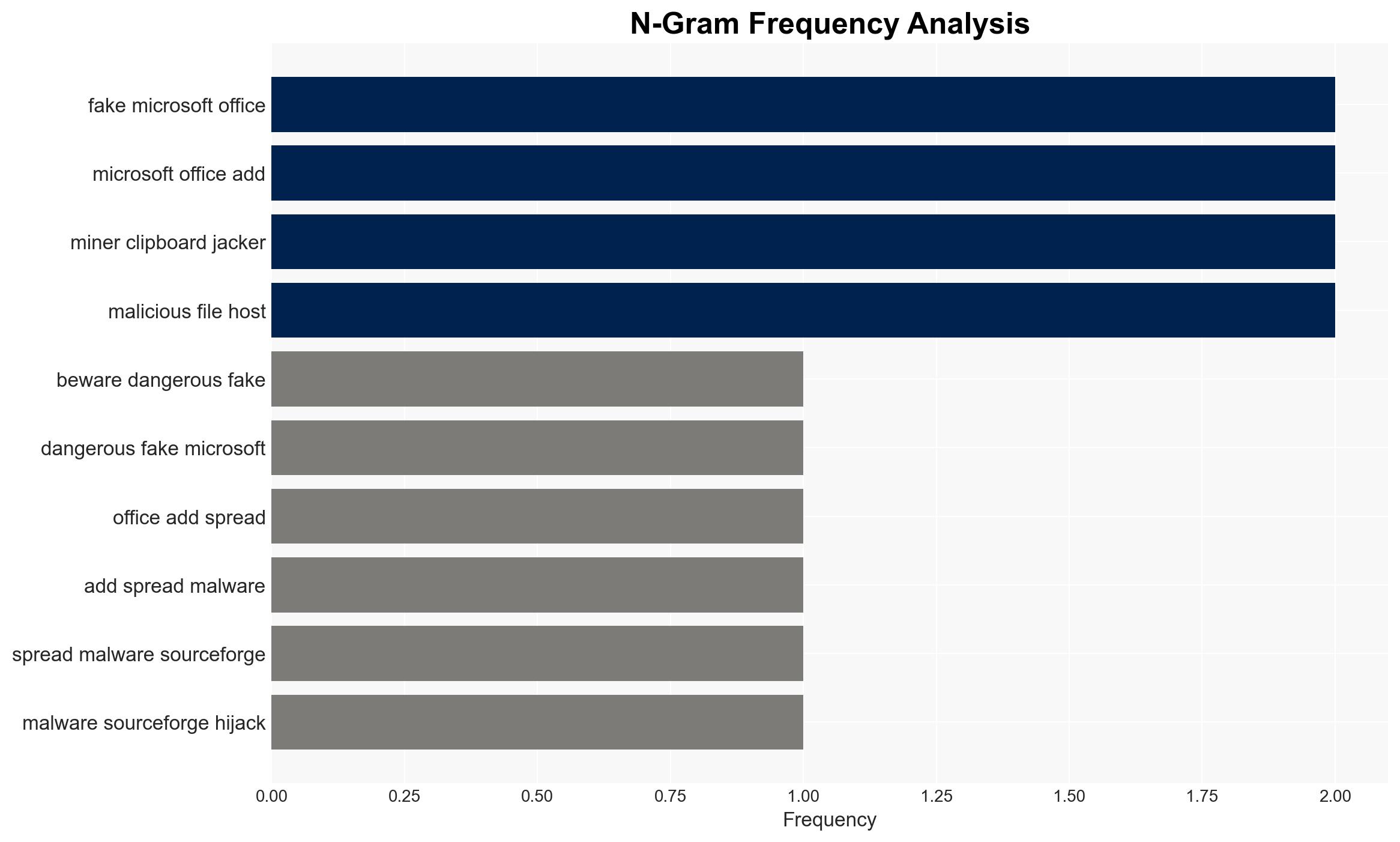
Recent intelligence indicates a malicious campaign leveraging fake Microsoft Office add-ons to distribute malware via SourceForge. The campaign involves a crypto miner and a clipboard jacker, posing significant cybersecurity threats. Swift action by SourceForge and security researchers has mitigated immediate risks, but vigilance is required to prevent future incidents.
2. Detailed Analysis
The following structured analytic techniques have been applied for this analysis:
General Analysis
The campaign identified by Kaspersky involves the distribution of malware disguised as legitimate Microsoft Office add-ons. The malicious files, hosted on SourceForge, are advertised as development tools but serve as malware droppers. The malware includes a cryptocurrency miner and a clipboard jacker, which can replace copied cryptocurrency addresses with those of the attacker. The rapid response by SourceForge prevented a major escalation, but the incident highlights vulnerabilities in open-source software hosting platforms.
3. Implications and Strategic Risks
The use of popular platforms like SourceForge for malware distribution poses significant risks to cybersecurity. This method exploits the trust users place in well-known platforms, increasing the likelihood of successful attacks. The potential compromise of endpoint computing power for cryptocurrency mining can lead to financial losses and reduced operational efficiency. Additionally, the clipboard jacker represents a direct threat to cryptocurrency transactions, potentially impacting financial markets and individual investors.
4. Recommendations and Outlook
Recommendations:
- Enhance monitoring and vetting processes for software hosted on open-source platforms to detect and remove malicious files swiftly.
- Develop and implement advanced threat detection systems to identify unusual activities indicative of malware distribution.
- Encourage collaboration between cybersecurity firms and platform providers to share intelligence and improve response times.
Outlook:
In the best-case scenario, improved security measures and collaboration will prevent similar incidents, maintaining user trust in open-source platforms. In the worst-case scenario, continued exploitation of these platforms could lead to widespread malware distribution, significant financial losses, and erosion of trust. The most likely outcome involves ongoing attempts by threat actors to exploit platform vulnerabilities, necessitating continuous vigilance and adaptation of security strategies.
5. Key Individuals and Entities
The report mentions Logan Abbott, who provided a statement regarding the incident. Additionally, Sead is noted as a contributor to the source article. The involvement of Kaspersky as a key cybersecurity entity in identifying the threat is also highlighted.