5 ways to avoid spyware disguised as legit apps – before it’s too late – ZDNet
Published on: 2025-04-09
Intelligence Report: 5 Ways to Avoid Spyware Disguised as Legit Apps – Before It’s Too Late – ZDNet
1. BLUF (Bottom Line Up Front)
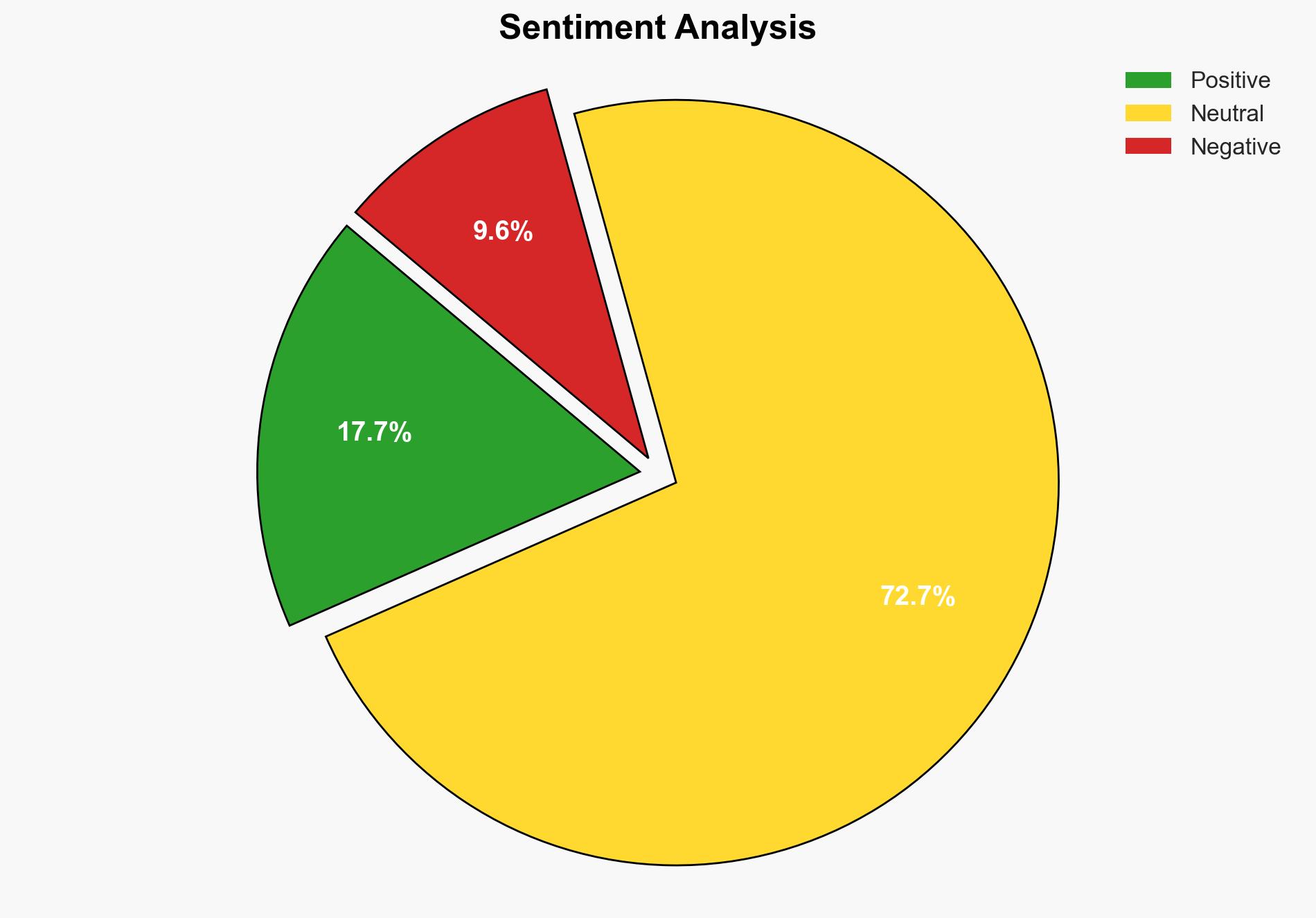
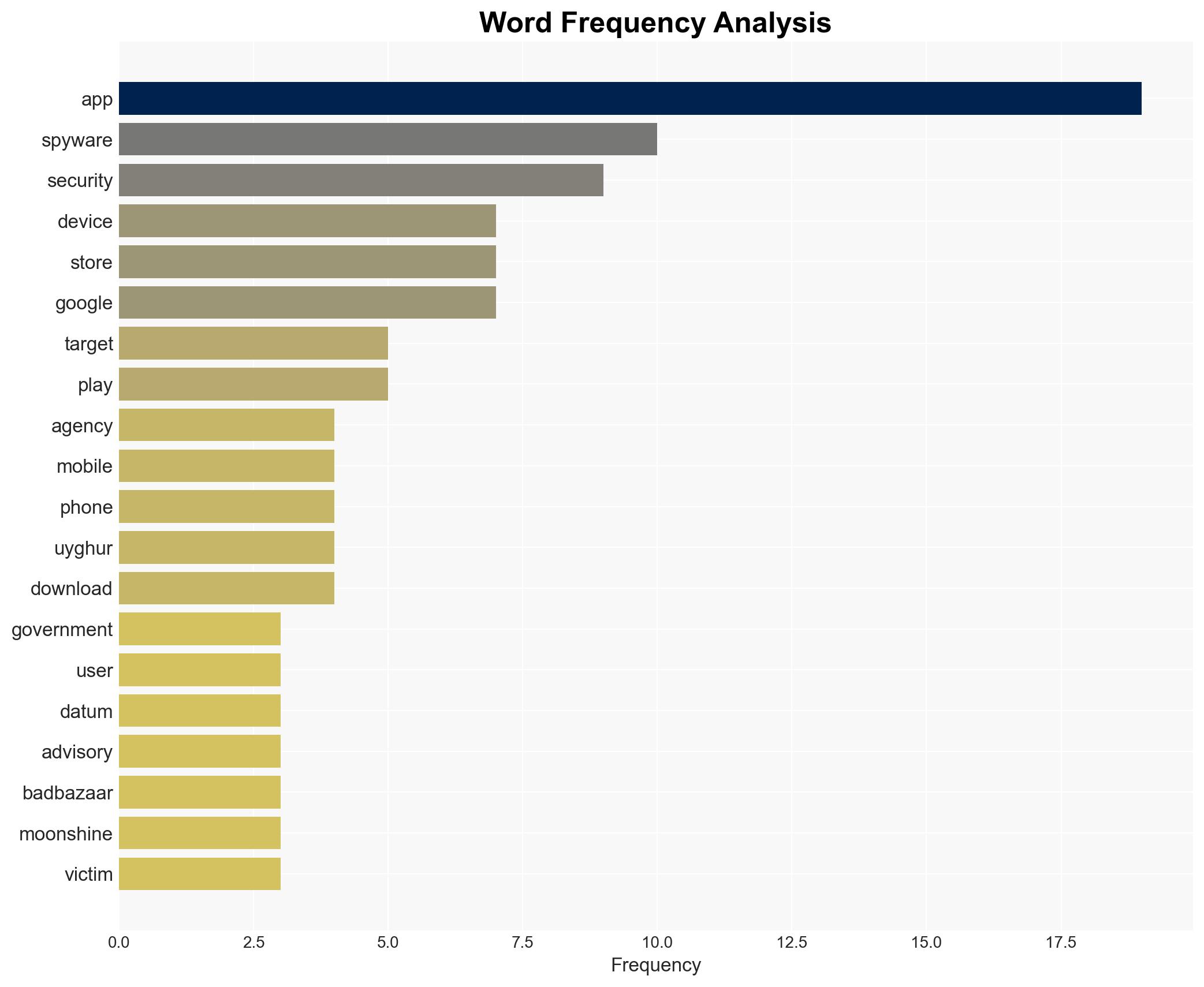
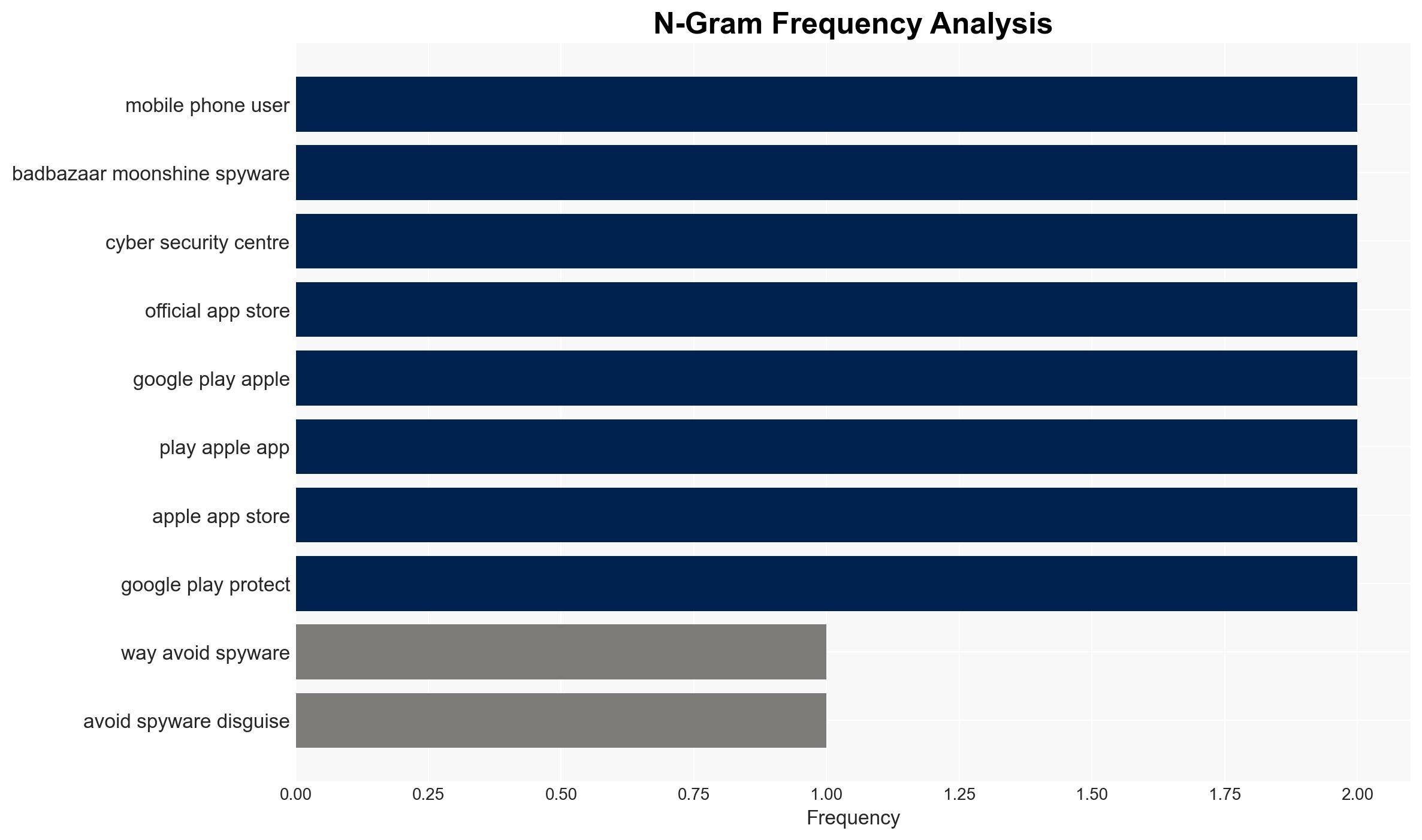
Recent advisories from global security agencies highlight the emergence of spyware variants such as BadBazaar and Moonshine. These spyware strains are designed to mimic legitimate applications, targeting individuals associated with movements considered sensitive by certain authorities. The spyware aims to compromise mobile devices, steal sensitive data, and track users. Immediate actions are required to enhance cybersecurity measures and protect vulnerable groups.
2. Detailed Analysis
The following structured analytic techniques have been applied for this analysis:
General Analysis
The spyware variants BadBazaar and Moonshine are sophisticated threats that exploit legitimate app platforms to infiltrate devices. They specifically target individuals connected to movements like Taiwanese independence and other groups perceived as threats by certain governments. These spyware strains have been observed impersonating popular apps such as Adobe Acrobat, Signal, and WhatsApp, among others. The widespread nature of these threats poses a significant challenge to cybersecurity efforts globally.
3. Implications and Strategic Risks
The proliferation of spyware disguised as legitimate apps presents several strategic risks:
- Threats to national security as sensitive information is at risk of being compromised.
- Potential destabilization of regional political movements due to targeted surveillance.
- Economic impacts on businesses and individuals through data theft and privacy breaches.
4. Recommendations and Outlook
Recommendations:
- Encourage the use of official app stores such as Google Play and Apple App Store to minimize exposure to malicious apps.
- Implement regular security updates and enable automatic updates on devices to protect against vulnerabilities.
- Educate users on reviewing app permissions and avoiding unnecessary access to sensitive features like cameras and microphones.
- Strengthen regulatory frameworks to enforce stricter app vetting processes and enhance cybersecurity standards.
Outlook:
In a best-case scenario, increased awareness and improved cybersecurity measures will significantly reduce the impact of spyware. In a worst-case scenario, failure to address these threats could lead to widespread data breaches and compromised national security. The most likely outcome involves a continued arms race between cybersecurity advancements and evolving spyware tactics.
5. Key Individuals and Entities
The report references several significant entities, including:
- Australian Cyber Security Centre
- Canadian Centre for Cyber Security
- German Federal Intelligence Service
- New Zealand National Cyber Security Centre
- FBI
- NSA
These organizations are instrumental in issuing advisories and providing guidance to mitigate the risks associated with spyware threats.