WhatsApp for Windows Vulnerability Found Hackers Can Run Malicious Code via Attachments – Smashingapps.com
Published on: 2025-04-10
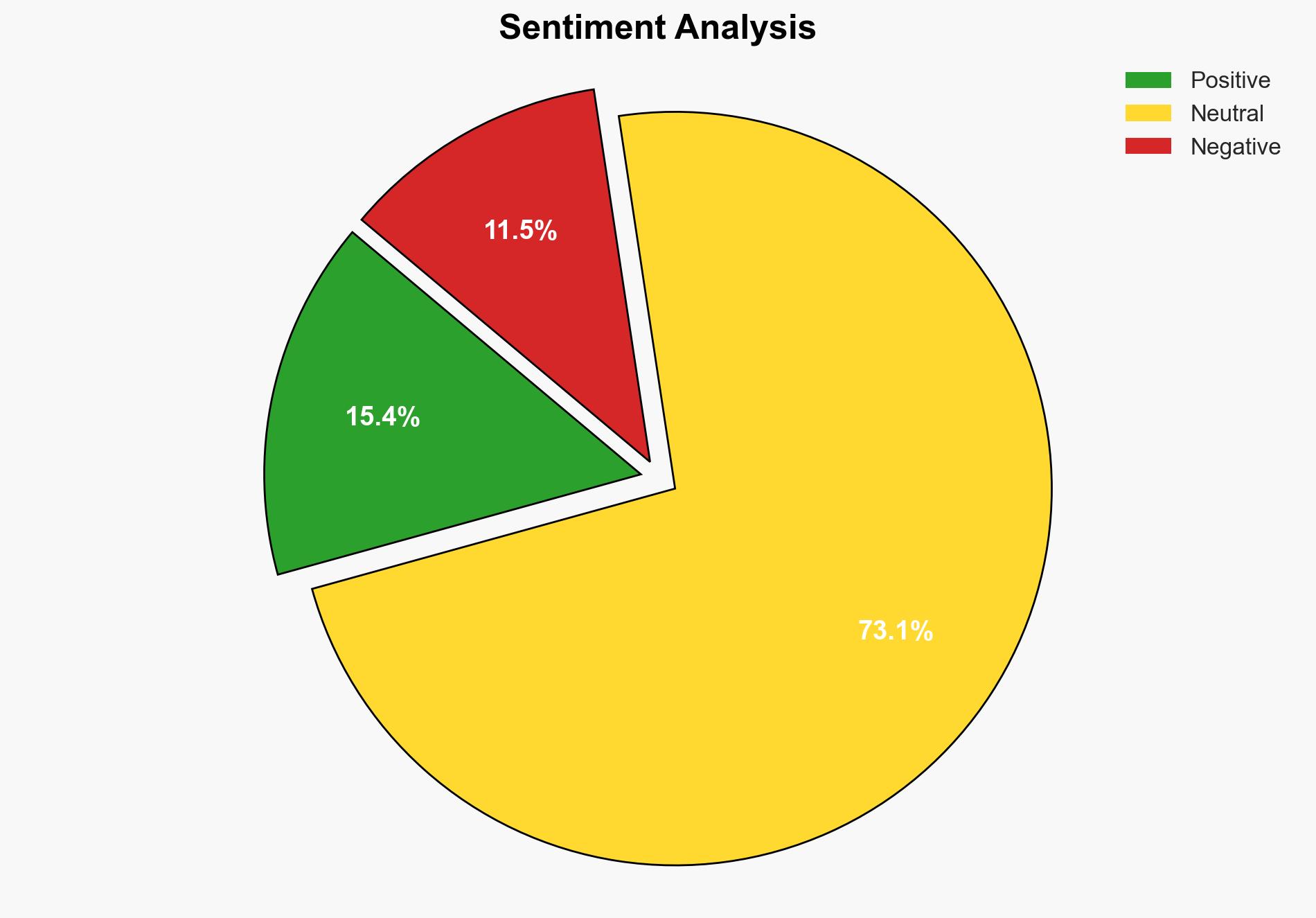
Intelligence Report: WhatsApp for Windows Vulnerability Found Hackers Can Run Malicious Code via Attachments – Smashingapps.com
1. BLUF (Bottom Line Up Front)
A critical vulnerability identified in WhatsApp for Windows, tracked as CVE-2025-30401, allows attackers to execute malicious code via specially crafted file attachments. This vulnerability poses a significant threat to millions of users, potentially enabling unauthorized access, data theft, and ransomware deployment. Immediate software updates are essential to mitigate risks.
2. Detailed Analysis
The following structured analytic techniques have been applied for this analysis:
General Analysis
The vulnerability in WhatsApp for Windows bypasses standard security protocols, allowing the execution of scripts embedded in files such as PDFs and images. This exploit can lead to silent malware installations and remote system takeovers without user interaction. The threat primarily affects unpatched versions of the desktop app, posing risks to both individual and business communications.
3. Implications and Strategic Risks
The exploitation of this vulnerability could have far-reaching implications, including:
- Compromised national security due to potential access to sensitive communications.
- Economic impacts from ransomware attacks on businesses and individuals.
- Increased cybersecurity threats leading to instability in digital communication platforms.
4. Recommendations and Outlook
Recommendations:
- Urgently update WhatsApp for Windows to version 2.2350.3 or later to close the security gap.
- Implement regular security audits and vulnerability assessments for communication platforms.
- Enhance user awareness and training on recognizing and handling suspicious file attachments.
Outlook:
In the best-case scenario, rapid updates and increased security measures will mitigate the vulnerability’s impact. In the worst-case scenario, widespread exploitation could lead to significant data breaches and financial losses. The most likely outcome involves a moderate level of disruption, with ongoing efforts to strengthen cybersecurity defenses.
5. Key Individuals and Entities
The report does not specify individuals by name but highlights the involvement of security researchers and the potential impact on WhatsApp users globally. The focus remains on the vulnerability and its implications rather than specific entities.