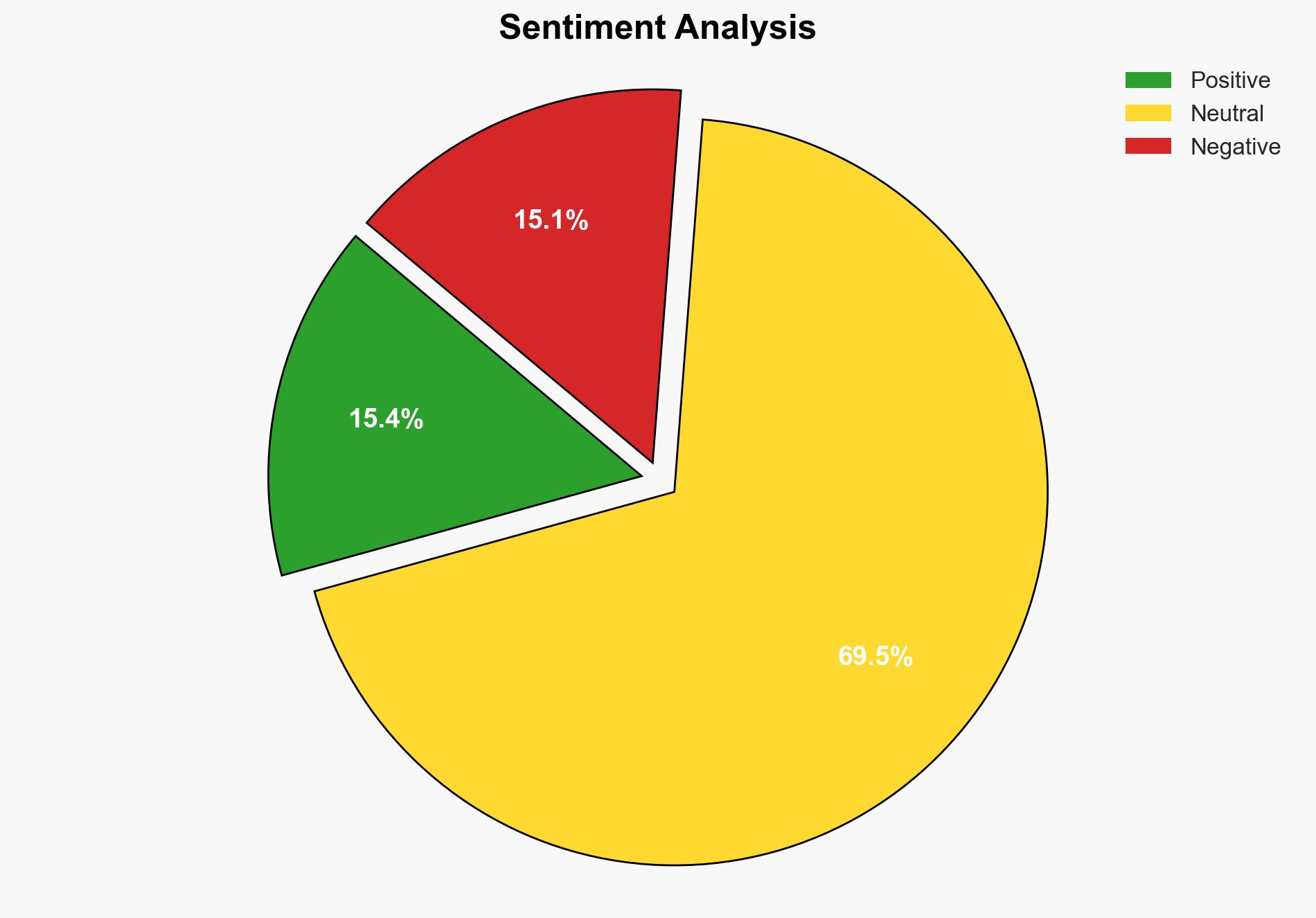
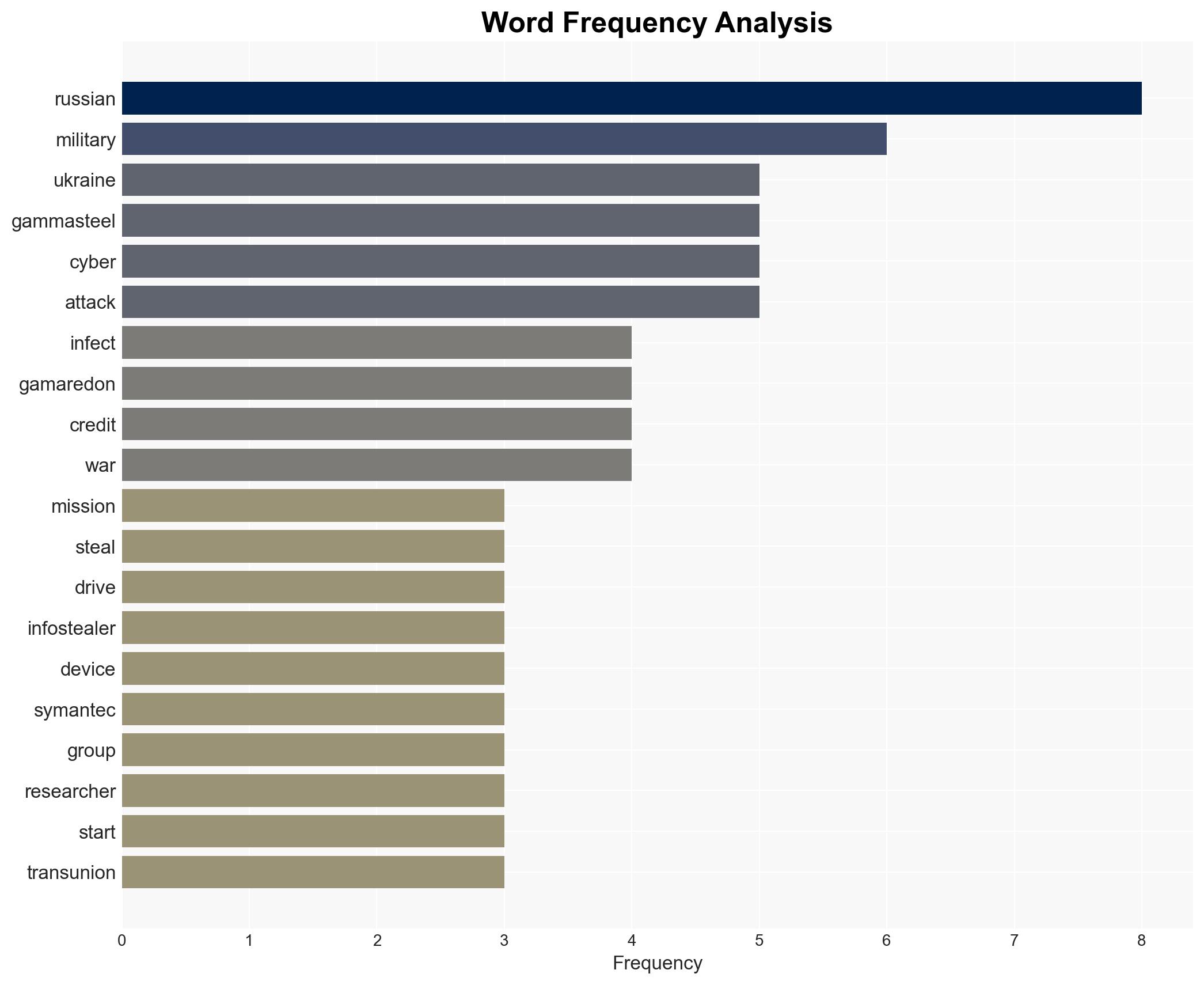
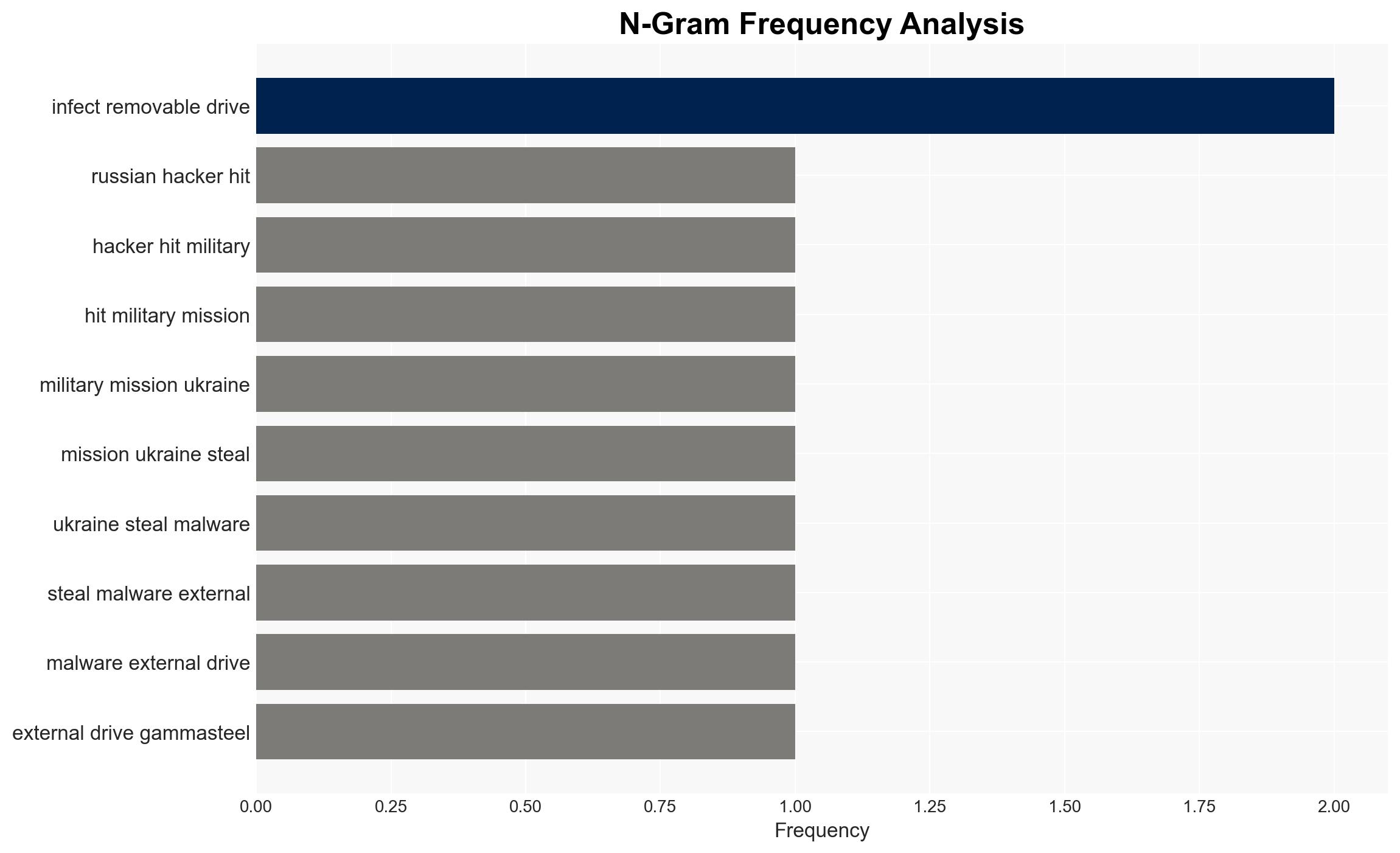
Russian hackers hit military mission in Ukraine with info-stealing malware on external drives – TechRadar
Published on: 2025-04-11
Intelligence Report: Russian hackers hit military mission in Ukraine with info-stealing malware on external drives – TechRadar
1. BLUF (Bottom Line Up Front)
Russian cyber group Gamaredon deployed the GammaSteel infostealer malware via infected removable drives targeting a military mission in Ukraine. The attack, identified by cybersecurity researchers, began in February 2025 and continued for several weeks. The malware is capable of exfiltrating sensitive documents and gathering system information. This incident is part of a broader cyber warfare campaign linked to ongoing geopolitical tensions between Russia and Ukraine. Immediate attention is required to enhance cybersecurity defenses and mitigate future risks.
2. Detailed Analysis
The following structured analytic techniques have been applied for this analysis:
General Analysis
The attack utilized a .LNK file on removable drives to initiate an infection chain, deploying GammaSteel malware. This malware targets various document formats and collects system data, including screenshots and antivirus information. Researchers noted a tactical shift in payload concealment, indicating evolving threat actor strategies. The attack aligns with Russia’s digital warfare tactics observed since the 2022 invasion of Ukraine, targeting critical infrastructure and military operations.
3. Implications and Strategic Risks
The attack poses significant risks to national security and regional stability. The exfiltration of sensitive military data could compromise operational security and strategic planning. The incident highlights vulnerabilities in cybersecurity defenses, emphasizing the need for enhanced protective measures. The ongoing cyber warfare underscores the evolving nature of conflict, where digital fronts are as critical as physical ones.
4. Recommendations and Outlook
Recommendations:
- Enhance cybersecurity protocols for military operations, focusing on removable media security and malware detection.
- Implement regular cybersecurity training for personnel to recognize and respond to cyber threats.
- Strengthen international cooperation on cybersecurity to share intelligence and develop joint defense strategies.
Outlook:
Best-case scenario: Enhanced cybersecurity measures prevent further breaches, and international collaboration reduces the effectiveness of state-sponsored cyber attacks.
Worst-case scenario: Continued cyber attacks lead to significant data breaches and operational disruptions, escalating geopolitical tensions.
Most likely scenario: Ongoing cyber threats persist, necessitating continuous adaptation and strengthening of cybersecurity defenses.
5. Key Individuals and Entities
The report mentions significant individuals and organizations but does not provide any roles or affiliations. Key entities include Gamaredon and Symantec, with the latter identifying the attack and providing analysis on the malware used.