Malicious NPM packages target PayPal users – Securityaffairs.com
Published on: 2025-04-14
Intelligence Report: Malicious NPM Packages Target PayPal Users – Securityaffairs.com
1. BLUF (Bottom Line Up Front)
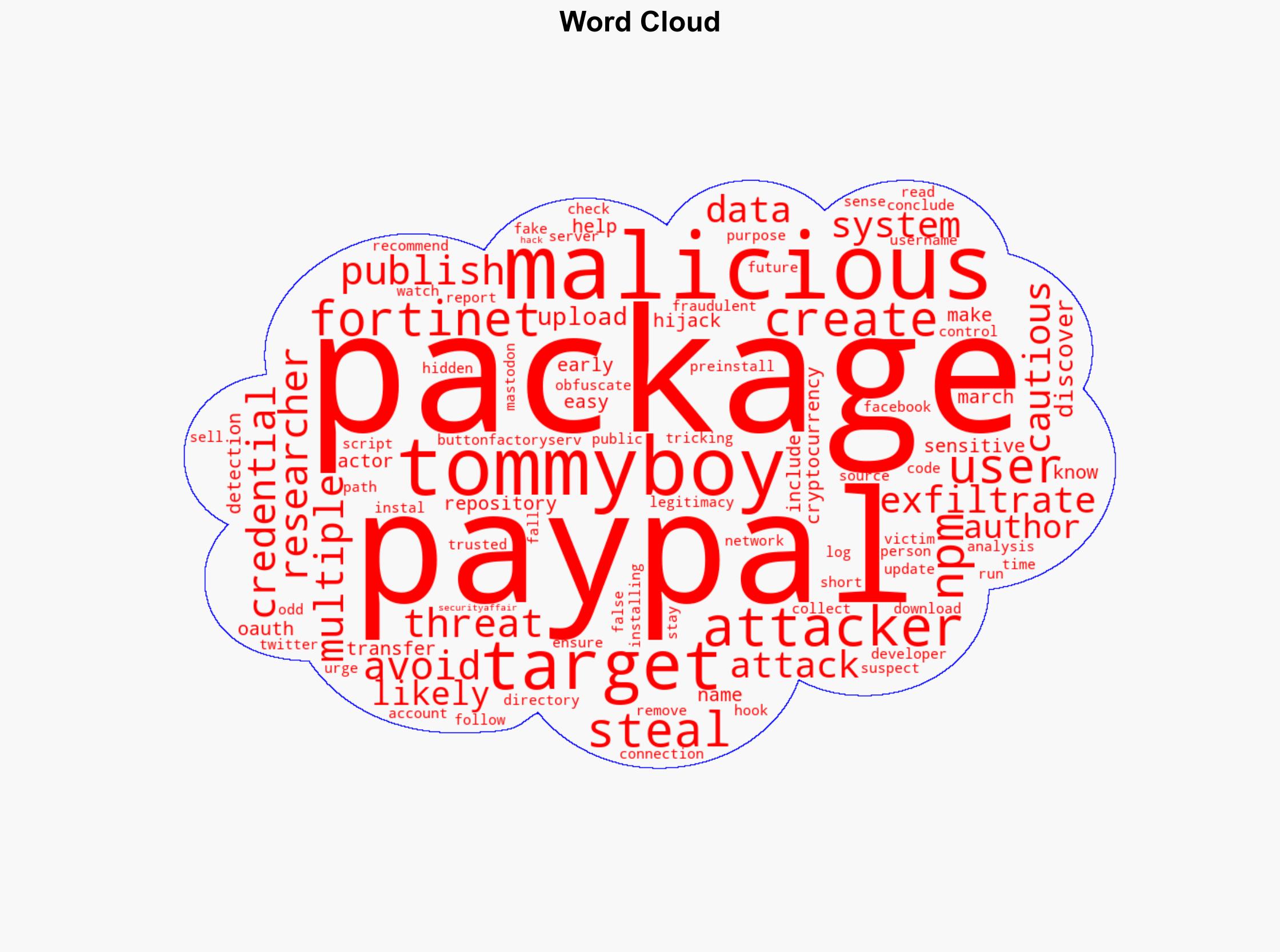
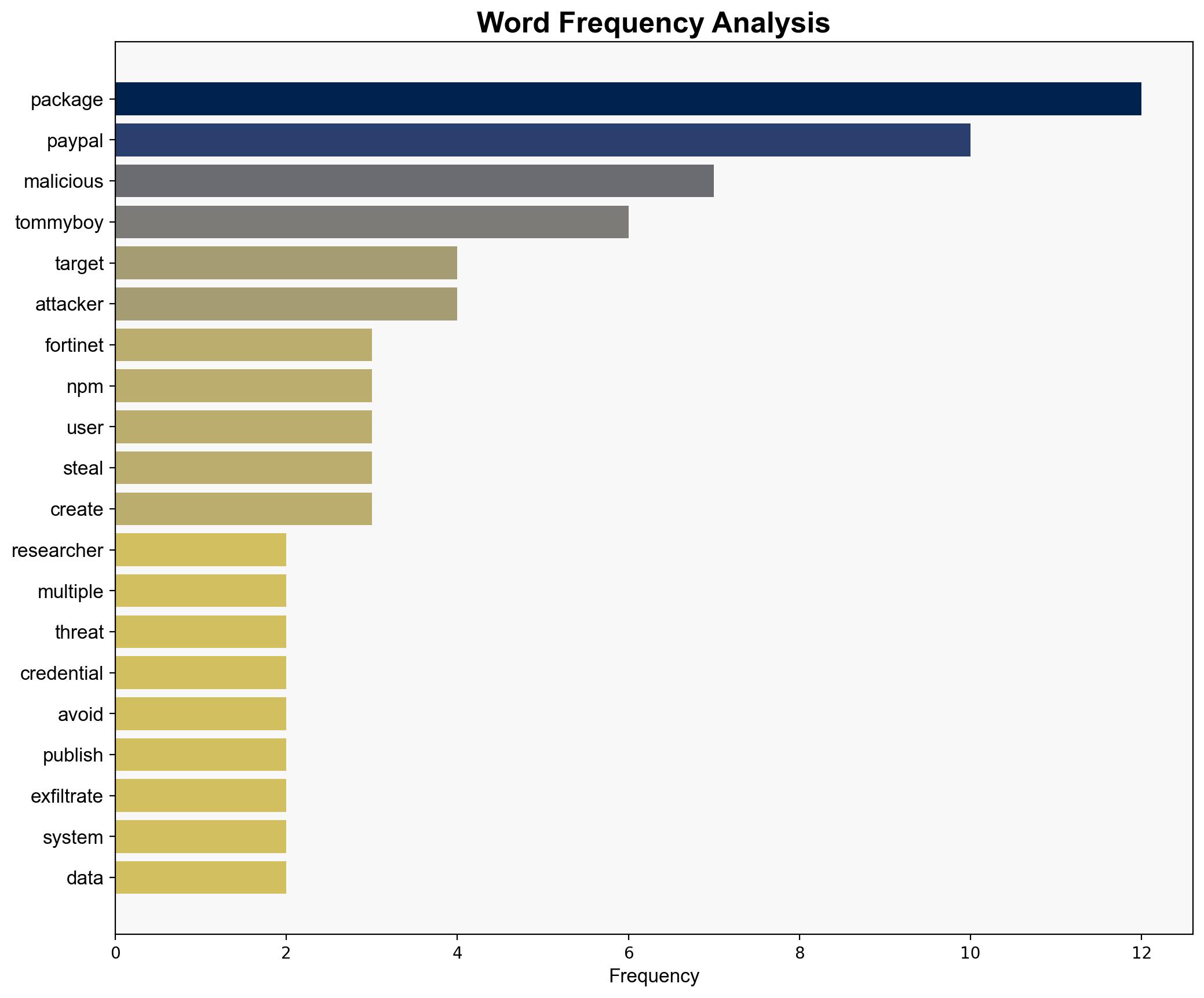
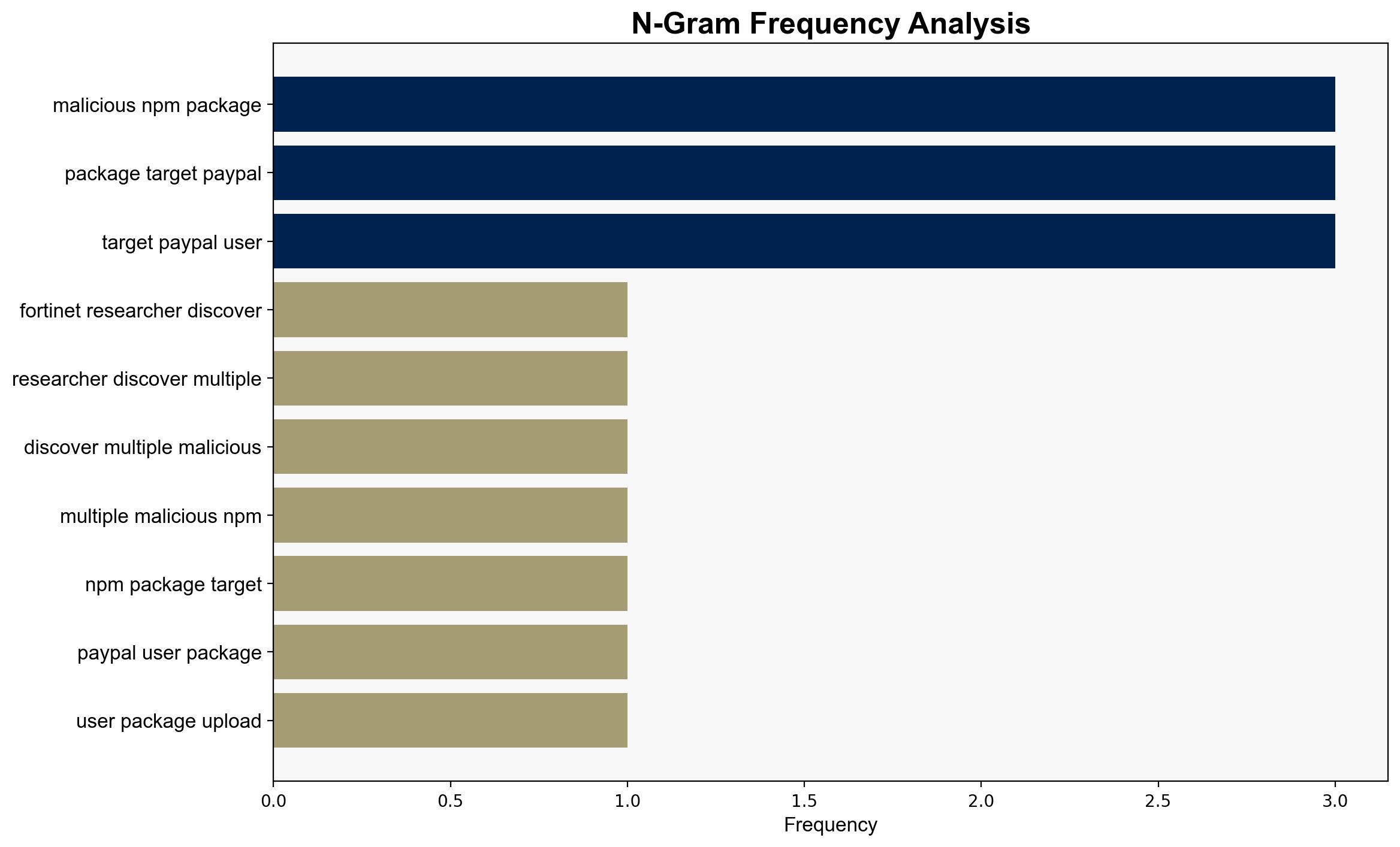
Fortinet researchers have identified multiple malicious NPM packages targeting PayPal users. These packages, uploaded by tommyboy_h1 and tommyboy_h2, are designed to steal PayPal credentials and hijack cryptocurrency transfers. The packages exploit PayPal-related names to avoid detection and create a false sense of legitimacy. Immediate actions include monitoring for fake packages, analyzing network logs for unusual activity, and ensuring package sources are trusted.
2. Detailed Analysis
The following structured analytic techniques have been applied for this analysis:
General Analysis
The malicious packages, such as oauth2-paypal and buttonfactoryserv-paypal, utilize preinstall hooks to execute hidden scripts that exfiltrate system data. This data includes usernames and directory paths, which can be used to compromise PayPal accounts or sold for fraudulent activities. The threat actor’s strategy of using PayPal-related names increases the risk of developers inadvertently installing these packages.
3. Implications and Strategic Risks
The proliferation of these malicious packages poses significant risks to individual users and organizations relying on PayPal for transactions. The potential compromise of PayPal credentials could lead to financial losses and undermine trust in digital payment platforms. Additionally, the hijacking of cryptocurrency transfers could have broader implications for the security and stability of digital financial systems.
4. Recommendations and Outlook
Recommendations:
- Implement stricter verification processes for NPM package uploads to prevent malicious actors from exploiting naming conventions.
- Encourage developers to verify the authenticity of packages before installation and regularly update security protocols.
- Enhance monitoring of network traffic for unusual patterns that may indicate data exfiltration.
Outlook:
Best-case scenario: Enhanced security measures and awareness campaigns reduce the prevalence of malicious packages, safeguarding PayPal users from credential theft.
Worst-case scenario: Failure to address the threat leads to widespread financial losses and erosion of trust in digital payment systems.
Most likely outcome: Incremental improvements in security practices mitigate some risks, but ongoing vigilance is required to address evolving threats.
5. Key Individuals and Entities
The report identifies tommyboy_h1 and tommyboy_h2 as the creators of the malicious packages. Their activities highlight the need for enhanced scrutiny of package repositories to prevent similar threats in the future.