CISA Releases Guidance on Credential Risks Associated with Potential Legacy Oracle Cloud Compromise – Cisa.gov
Published on: 2025-04-16
Intelligence Report: CISA Releases Guidance on Credential Risks Associated with Potential Legacy Oracle Cloud Compromise – Cisa.gov
1. BLUF (Bottom Line Up Front)
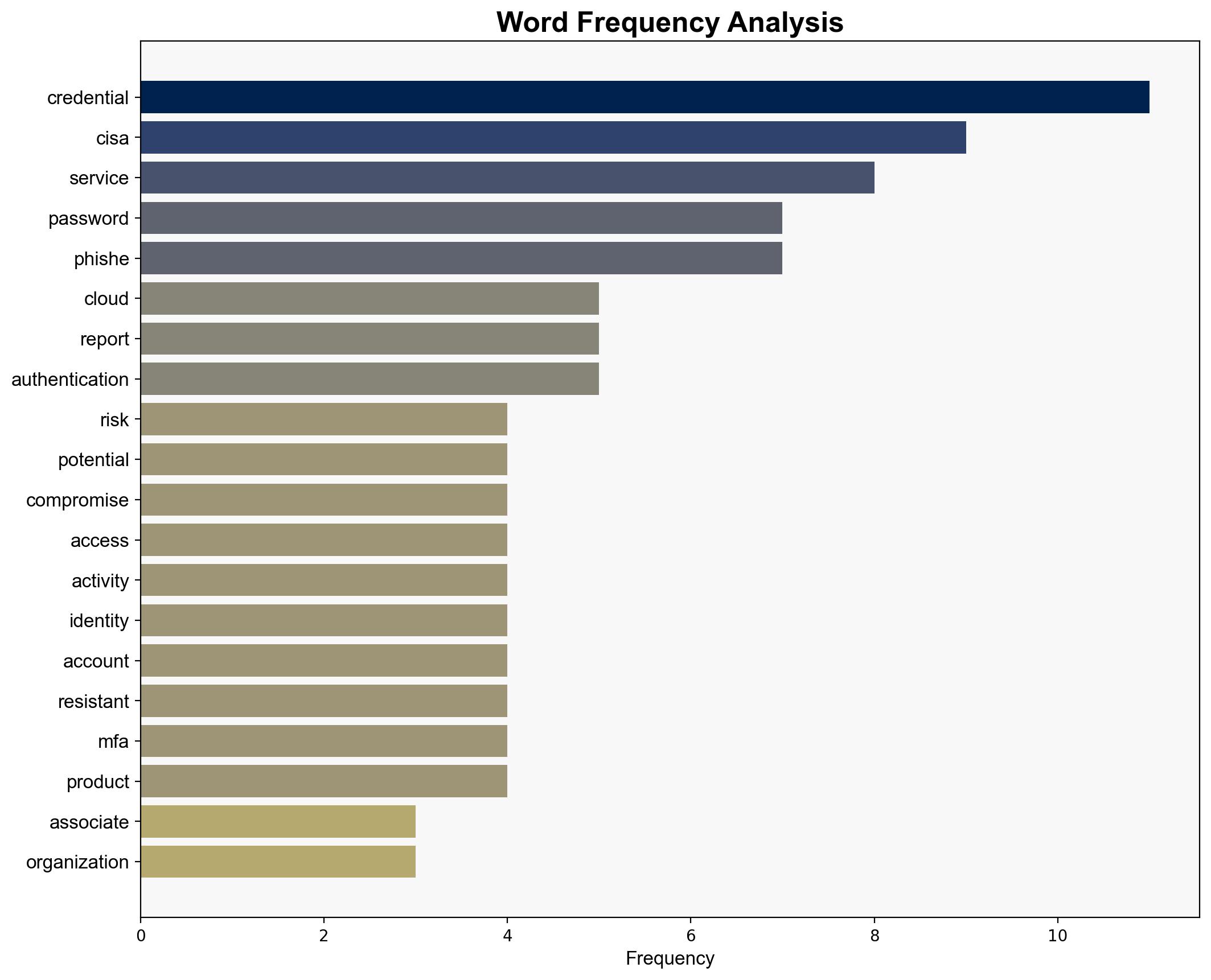
The Cybersecurity and Infrastructure Security Agency (CISA) has issued guidance on potential credential risks linked to a reported compromise in a legacy Oracle cloud environment. The primary concern is unauthorized access to credential material, which poses significant risks to organizations and individuals. CISA recommends immediate actions including password resets, code reviews for embedded credentials, and the implementation of phishing-resistant multi-factor authentication (MFA).
2. Detailed Analysis
The following structured analytic techniques have been applied:
Analysis of Competing Hypotheses (ACH)
Potential causes for the security breach include unauthorized access due to outdated security protocols in legacy systems and credential reuse across multiple platforms. Motivations may range from financial gain through credential resale to strategic data acquisition for further cyber operations.
SWOT Analysis
Strengths: CISA’s proactive guidance and established protocols for credential management.
Weaknesses: Legacy systems with embedded credentials are vulnerable to exploitation.
Opportunities: Strengthening cloud security practices and adopting centralized secret management.
Threats: Continued exploitation of compromised credentials leading to broader network intrusions.
Indicators Development
Warning signs include unusual authentication attempts, especially involving privileged accounts, and the presence of hardcoded credentials in scripts and applications.
3. Implications and Strategic Risks
The compromise of credential material can lead to significant security breaches, affecting both public and private sectors. This could result in economic losses, reputational damage, and increased geopolitical tensions if state-sponsored actors are involved. The incident underscores the need for robust cybersecurity measures and the risks associated with legacy systems.
4. Recommendations and Outlook
- Organizations should conduct immediate password resets and review all systems for embedded credentials, replacing them with secure methods.
- Implement phishing-resistant MFA across all user and administrator accounts to enhance security.
- Regularly monitor authentication logs for anomalies and conduct security audits to identify vulnerabilities.
- Scenario-based projections suggest that without immediate action, the risk of further breaches and data exploitation will increase, potentially affecting critical infrastructure and national security.
5. Key Individuals and Entities
The report does not specify individual names but focuses on organizations and entities involved in cybersecurity and cloud services.