Hertz So Bad Alarming Data Breach Exposes Customer Data To Hackers – Hot Hardware
Published on: 2025-04-16
Intelligence Report: Hertz So Bad Alarming Data Breach Exposes Customer Data To Hackers – Hot Hardware
1. BLUF (Bottom Line Up Front)
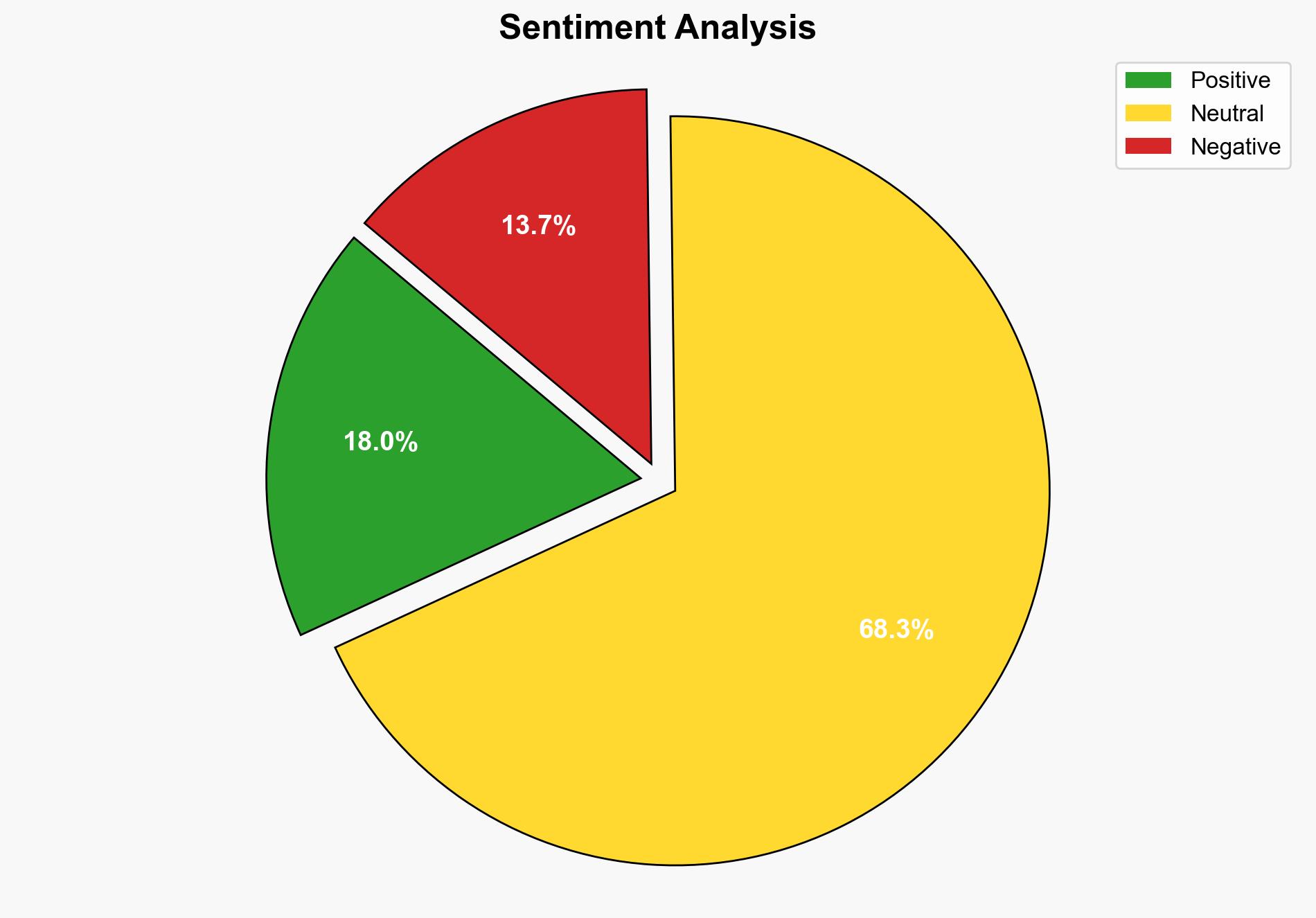
A significant data breach at Hertz, involving the Cleo file transfer platform, has exposed sensitive customer information to unauthorized third parties. The breach, linked to a zero-day attack, affects Hertz, Dollar, and Thrifty brands. Immediate actions are recommended for affected customers, including monitoring credit activity and utilizing identity protection services offered by Hertz.
2. Detailed Analysis
The following structured analytic techniques have been applied:
Analysis of Competing Hypotheses (ACH)
The breach likely resulted from a sophisticated zero-day attack on the Cleo platform. Motivations could include financial gain through data exploitation or resale on dark web markets. The involvement of the Clop ransomware gang suggests a coordinated effort to extract and potentially ransom sensitive information.
SWOT Analysis
Strengths: Hertz’s prompt response in engaging cybersecurity experts and offering identity protection services.
Weaknesses: Initial delay in breach detection and notification, indicating potential gaps in monitoring and response protocols.
Opportunities: Strengthening cybersecurity infrastructure and protocols to prevent future breaches.
Threats: Continued vulnerability to sophisticated cyber attacks and potential reputational damage impacting customer trust.
Indicators Development
Warning signs include increased phishing attempts targeting Hertz customers, unusual account activities, and reports of identity theft. Monitoring for these indicators can help in early detection of further malicious activities.
3. Implications and Strategic Risks
The breach underscores vulnerabilities in third-party platforms and the need for robust cybersecurity measures. Economically, potential costs include legal liabilities, regulatory fines, and loss of customer trust. Politically, the incident may prompt regulatory scrutiny and calls for stricter data protection laws.
4. Recommendations and Outlook
- Enhance cybersecurity protocols, including regular audits and penetration testing, to identify and mitigate vulnerabilities.
- Implement advanced threat detection systems and improve incident response times to reduce breach impact.
- Engage in public awareness campaigns to educate customers on protecting their personal information.
- Scenario-based projection: If cybersecurity measures are not strengthened, similar breaches could occur, leading to further financial and reputational damage.
5. Key Individuals and Entities
Hertz, Cleo, Clop ransomware gang, Kroll.