US CISA adds SonicWall SMA100 Appliance flaw to its Known Exploited Vulnerabilities catalog – Securityaffairs.com
Published on: 2025-04-17
Intelligence Report: US CISA adds SonicWall SMA100 Appliance flaw to its Known Exploited Vulnerabilities catalog – Securityaffairs.com
1. BLUF (Bottom Line Up Front)
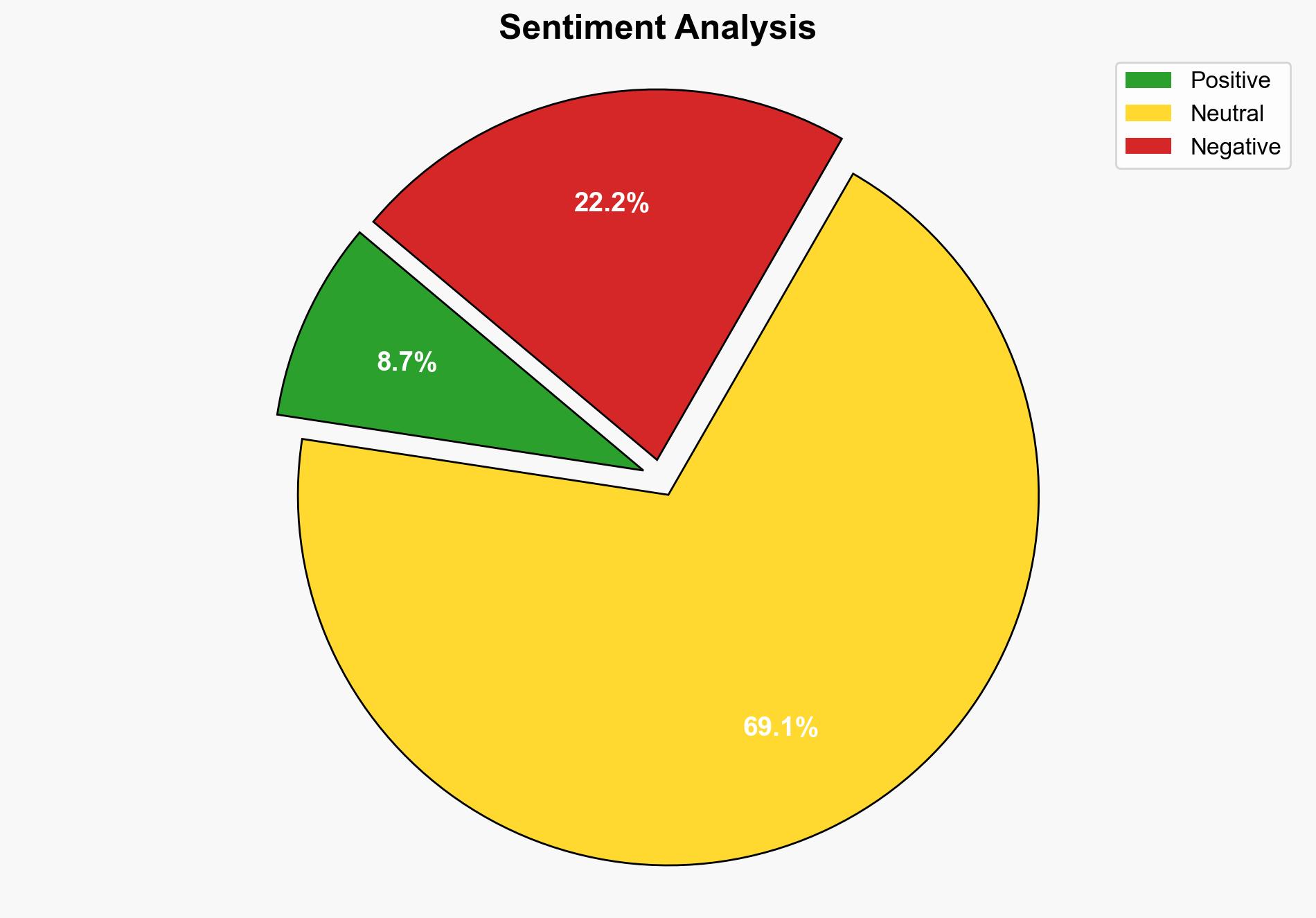
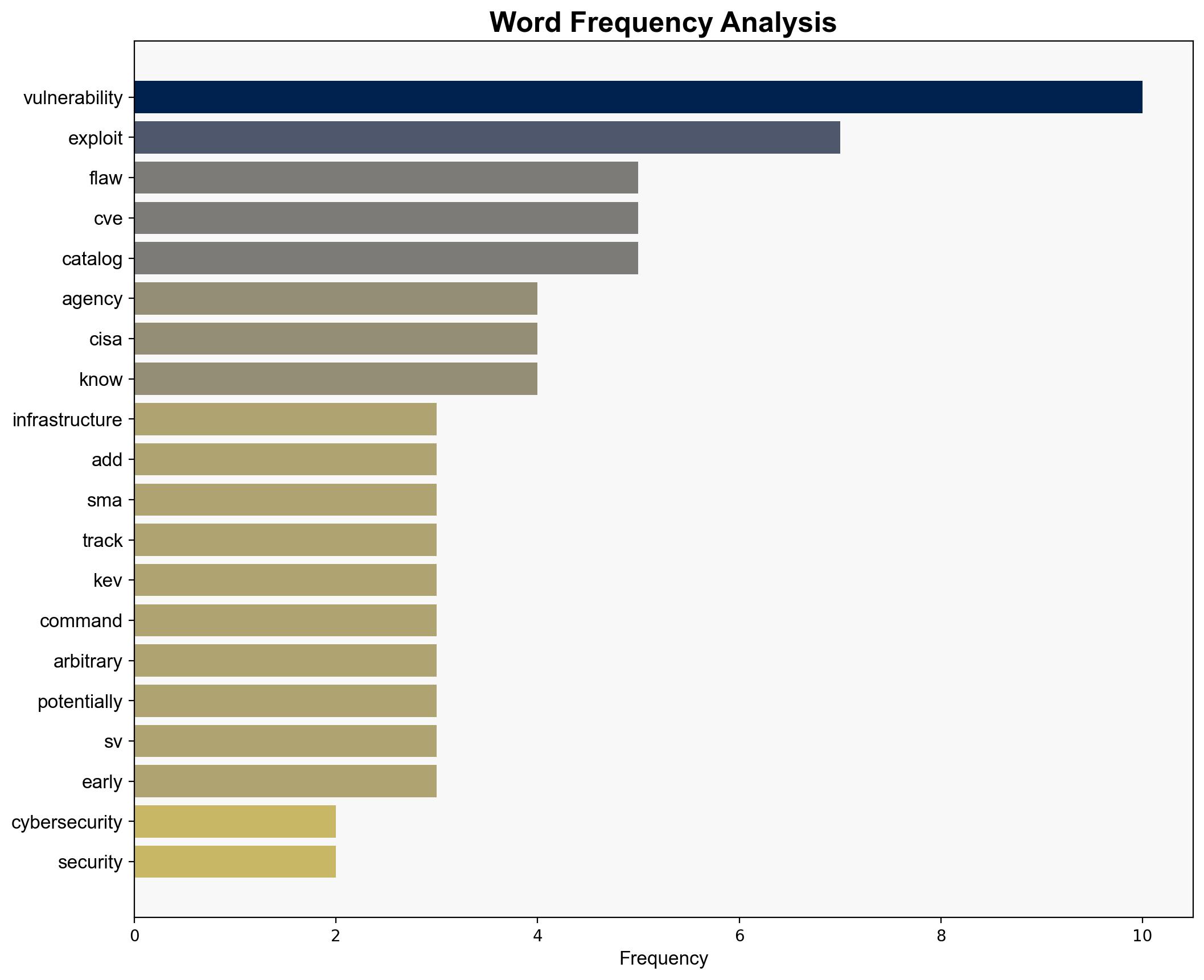
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has identified a critical vulnerability in the SonicWall SMA100 Appliance, tracked as CVE-2021-20035, and added it to the Known Exploited Vulnerabilities (KEV) catalog. This flaw allows remote authenticated attackers to execute arbitrary commands, posing a significant risk of code execution. Immediate mitigation is required, with federal agencies mandated to address this by May 7, 2025. Private organizations are also advised to review and address this vulnerability to protect their networks.
2. Detailed Analysis
The following structured analytic techniques have been applied:
Analysis of Competing Hypotheses (ACH)
The primary hypothesis is that the vulnerability is being actively exploited due to its inclusion in the KEV catalog. The motivation behind exploiting this flaw likely includes unauthorized access to sensitive data and disruption of services.
SWOT Analysis
Strengths: CISA’s proactive identification and cataloging of vulnerabilities enhance national cybersecurity posture.
Weaknesses: The widespread use of affected SonicWall appliances increases exposure.
Opportunities: Organizations can strengthen defenses by addressing this vulnerability promptly.
Threats: Continued exploitation could lead to significant data breaches and operational disruptions.
Indicators Development
Warning signs include unusual network activity, unauthorized access attempts, and exploitation of known vulnerabilities in similar systems.
3. Implications and Strategic Risks
The exploitation of this vulnerability could lead to severe security breaches, affecting both public and private sectors. The economic impact could be substantial, with potential disruptions to critical infrastructure. Politically, failure to address such vulnerabilities may undermine trust in cybersecurity frameworks.
4. Recommendations and Outlook
- Organizations should prioritize patching the identified SonicWall vulnerability and conduct regular security audits.
- Implement network segmentation and enhanced monitoring to detect and respond to suspicious activities.
- Scenario-based projections suggest that failure to address this flaw could lead to increased cyberattacks targeting similar vulnerabilities.
5. Key Individuals and Entities
The report does not specify individual names. Key entities include SonicWall, CISA, and affected federal and private organizations.