The Web Is Broken Botnet Part 2 – Wildeboer.net
Published on: 2025-04-19
Intelligence Report: The Web Is Broken Botnet Part 2 – Wildeboer.net
1. BLUF (Bottom Line Up Front)
The report highlights the emergence of a new class of botnets that exploit web crawlers and third-party SDKs to create extensive networks using unsuspecting users’ devices. This trend poses significant risks to web infrastructure and data security. Immediate action is recommended to address these vulnerabilities and mitigate the impact of such botnets.
2. Detailed Analysis
The following structured analytic techniques have been applied:
Analysis of Competing Hypotheses (ACH)
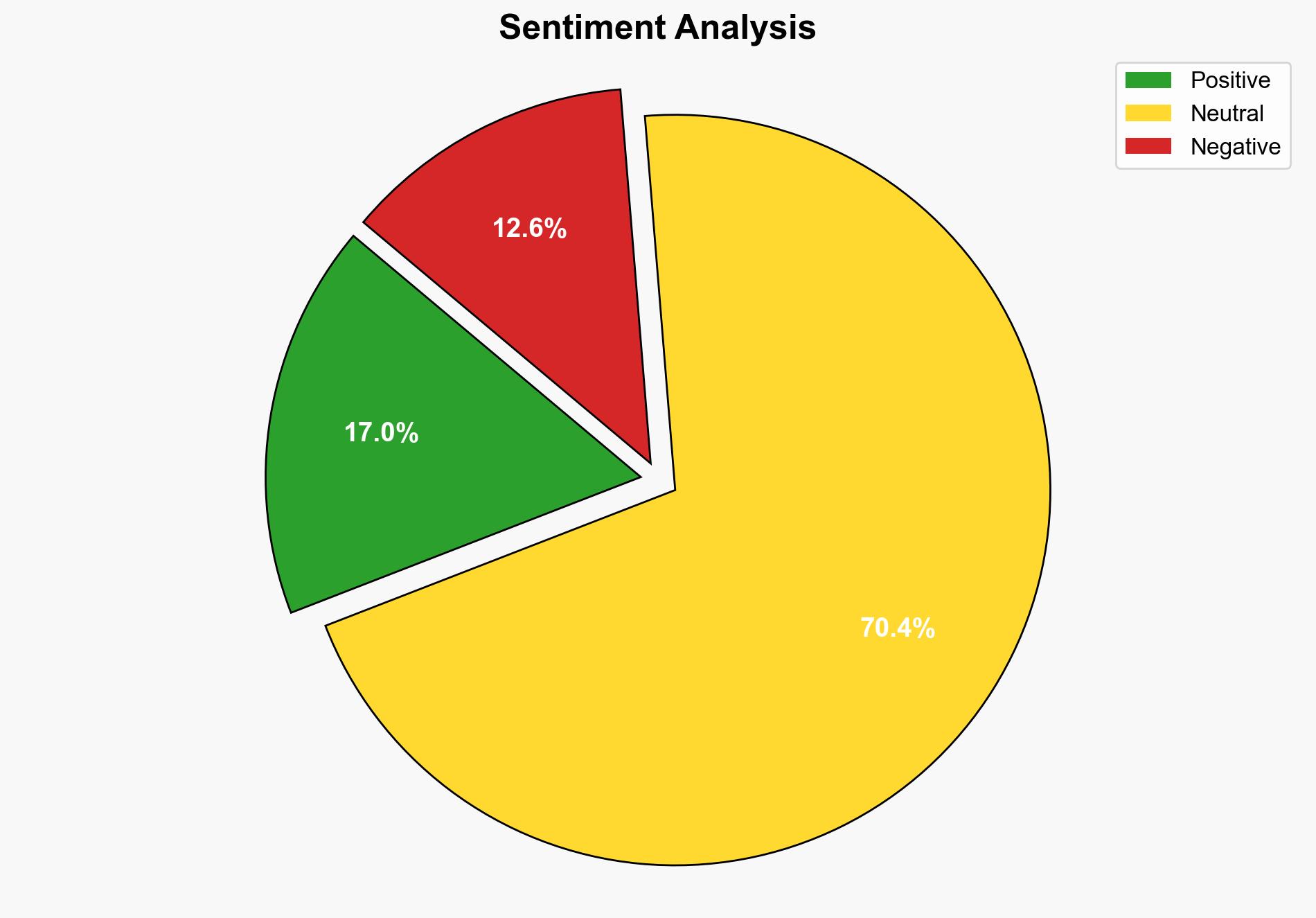
The primary hypothesis is that companies are leveraging AI-driven web crawlers and SDKs to create botnets for data collection and web scraping. Alternative hypotheses include the possibility of malicious actors exploiting these technologies for DDoS attacks or data theft.
SWOT Analysis
Strengths: Advanced AI capabilities enhance data collection efficiency.
Weaknesses: Increased vulnerability to DDoS attacks and unauthorized data access.
Opportunities: Development of more robust cybersecurity measures and protocols.
Threats: Proliferation of botnets could destabilize web services and compromise user data.
Indicators Development
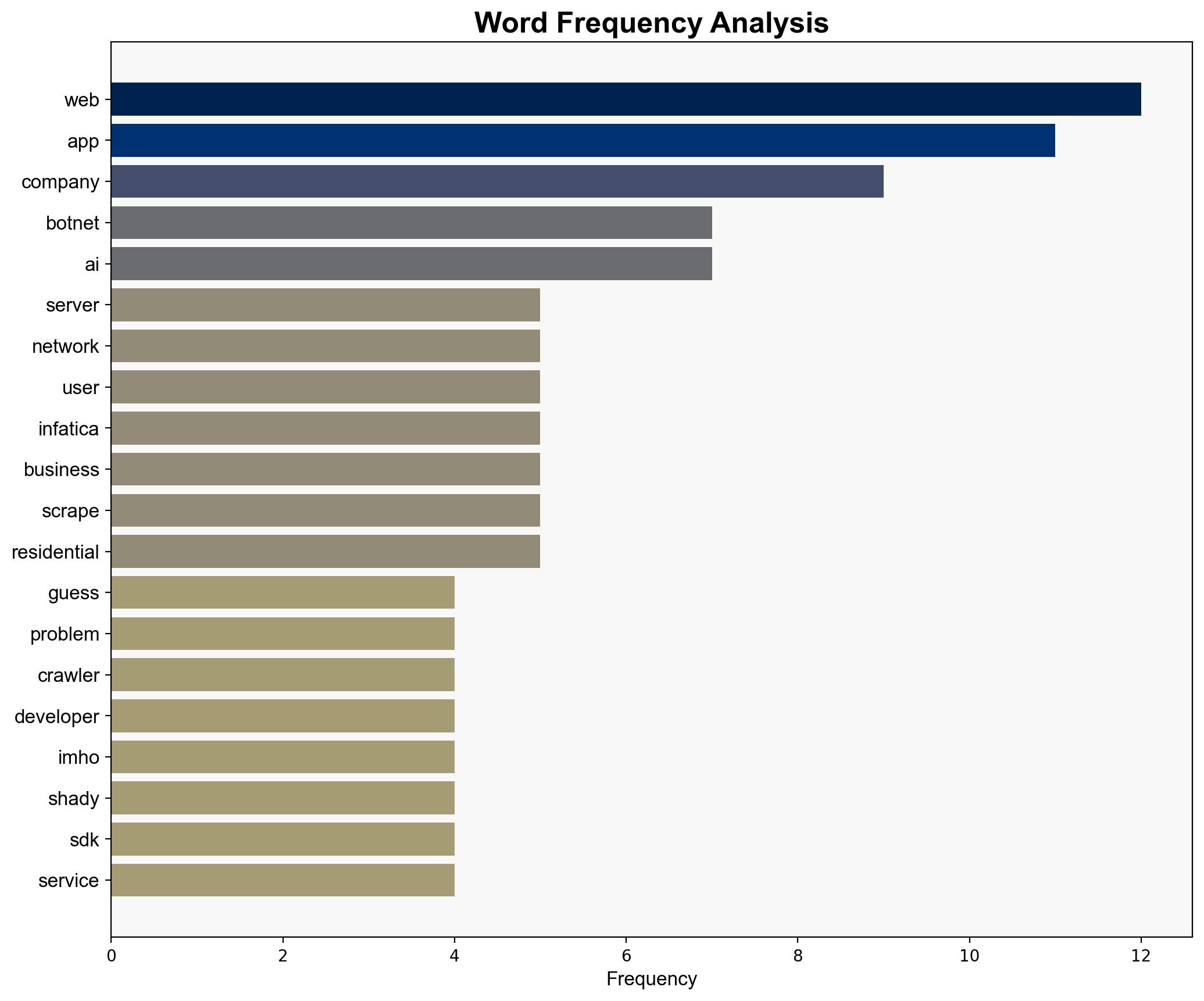
Indicators of emerging threats include a surge in unexplained network traffic, frequent server overloads, and the presence of unfamiliar SDKs in applications. Monitoring these signs can help in early detection and response to potential botnet activities.
3. Implications and Strategic Risks
The widespread use of AI-driven botnets presents a significant threat to cybersecurity, potentially leading to economic disruptions and loss of trust in digital services. The integration of malicious SDKs into legitimate applications exacerbates these risks, making detection and prevention more challenging.
4. Recommendations and Outlook
- Enhance monitoring of network traffic to identify and block suspicious activities promptly.
- Develop and enforce stricter regulations on the use of third-party SDKs in applications.
- Invest in research and development of advanced cybersecurity solutions to counter AI-driven threats.
- Scenario-based projection: If current trends continue, expect an increase in botnet-related disruptions, necessitating coordinated international cybersecurity efforts.
5. Key Individuals and Entities
Mentioned entities include Infatica, Trend Micro, and major tech companies such as Apple, Microsoft, and Google. These entities are pivotal in either contributing to or combating the botnet phenomenon.