How to check if someone is remotely accessing your computer – Thewindowsclub.com
Published on: 2025-04-20
Intelligence Report: How to check if someone is remotely accessing your computer – Thewindowsclub.com
1. BLUF (Bottom Line Up Front)
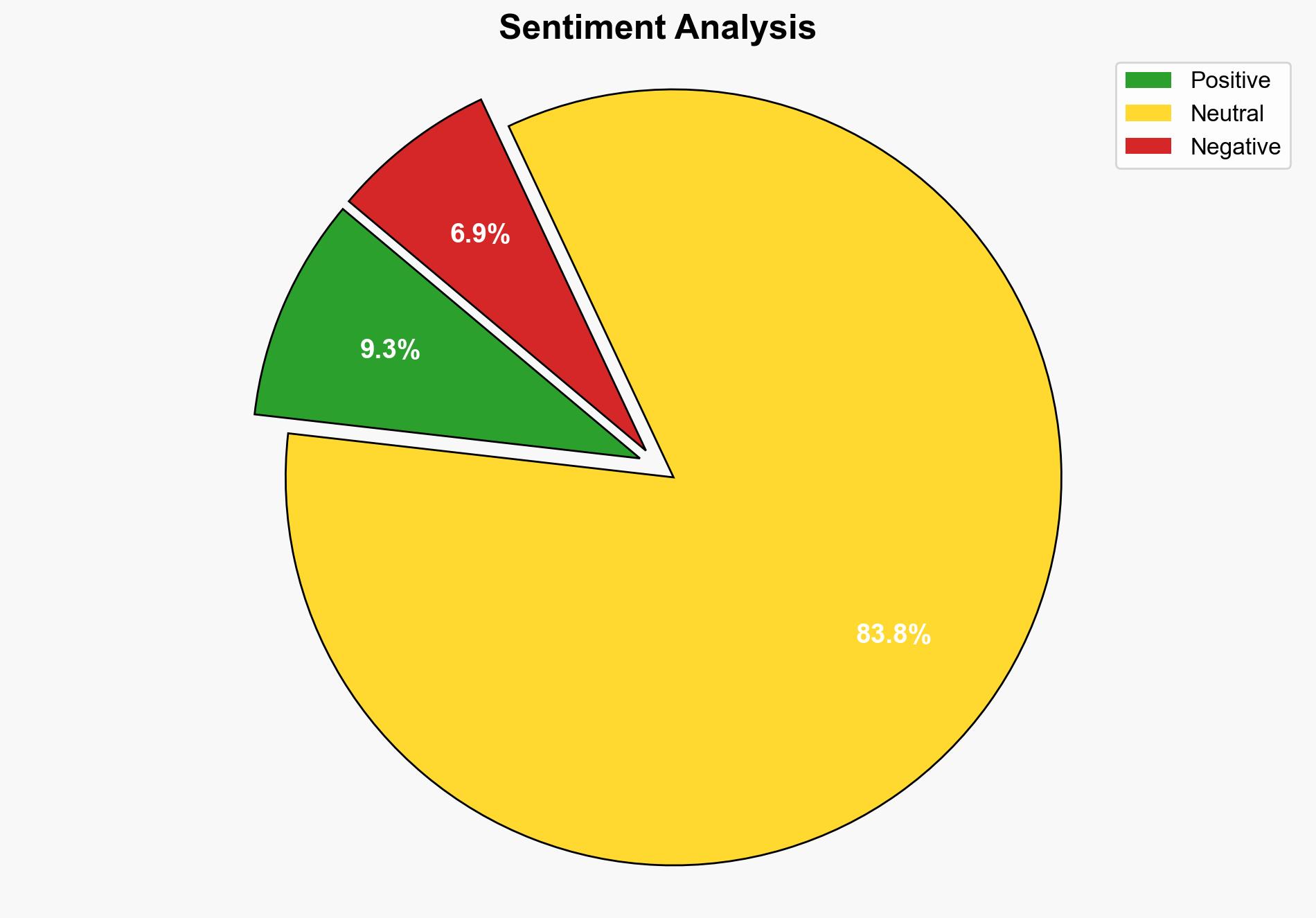
Unauthorized remote access to computers poses significant security risks, including data breaches and privacy violations. Key findings suggest that monitoring for unusual activities, such as unexpected program installations or automatic mouse movements, can help identify potential intrusions. Recommendations include disabling remote access features when not in use and employing robust network monitoring tools.
2. Detailed Analysis
The following structured analytic techniques have been applied:
Analysis of Competing Hypotheses (ACH)
Possible causes for unauthorized remote access include targeted cyber attacks, exploitation of software vulnerabilities, and user negligence in securing remote access settings. Motivations may range from data theft to espionage.
SWOT Analysis
Strengths: Built-in security features in operating systems, such as Windows Defender and Firewall, provide a baseline defense.
Weaknesses: Default settings may leave systems vulnerable if not properly configured.
Opportunities: Increasing awareness and education on cybersecurity can enhance user defenses.
Threats: Advanced persistent threats and sophisticated hacking tools continue to evolve, challenging existing security measures.
Indicators Development
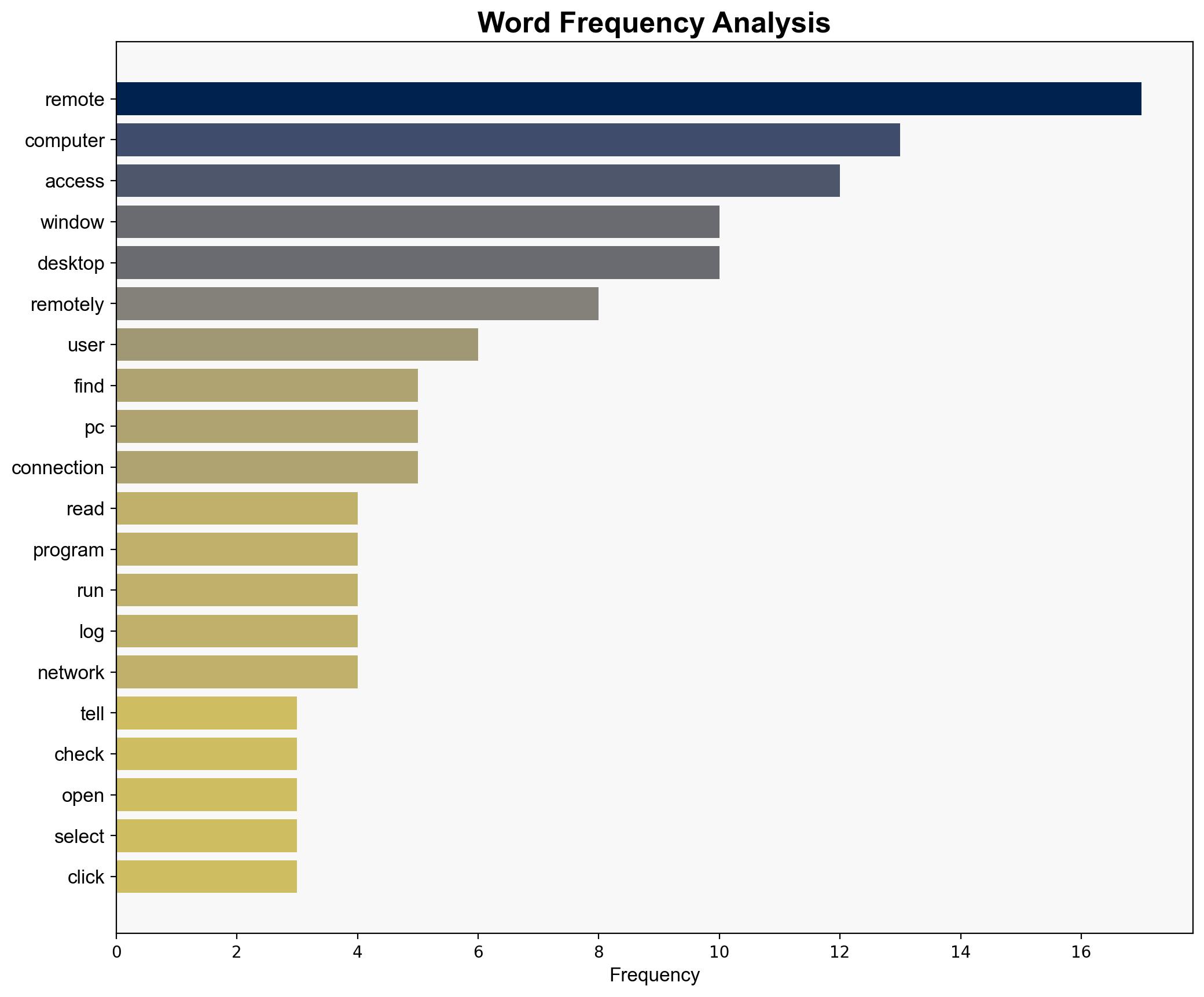
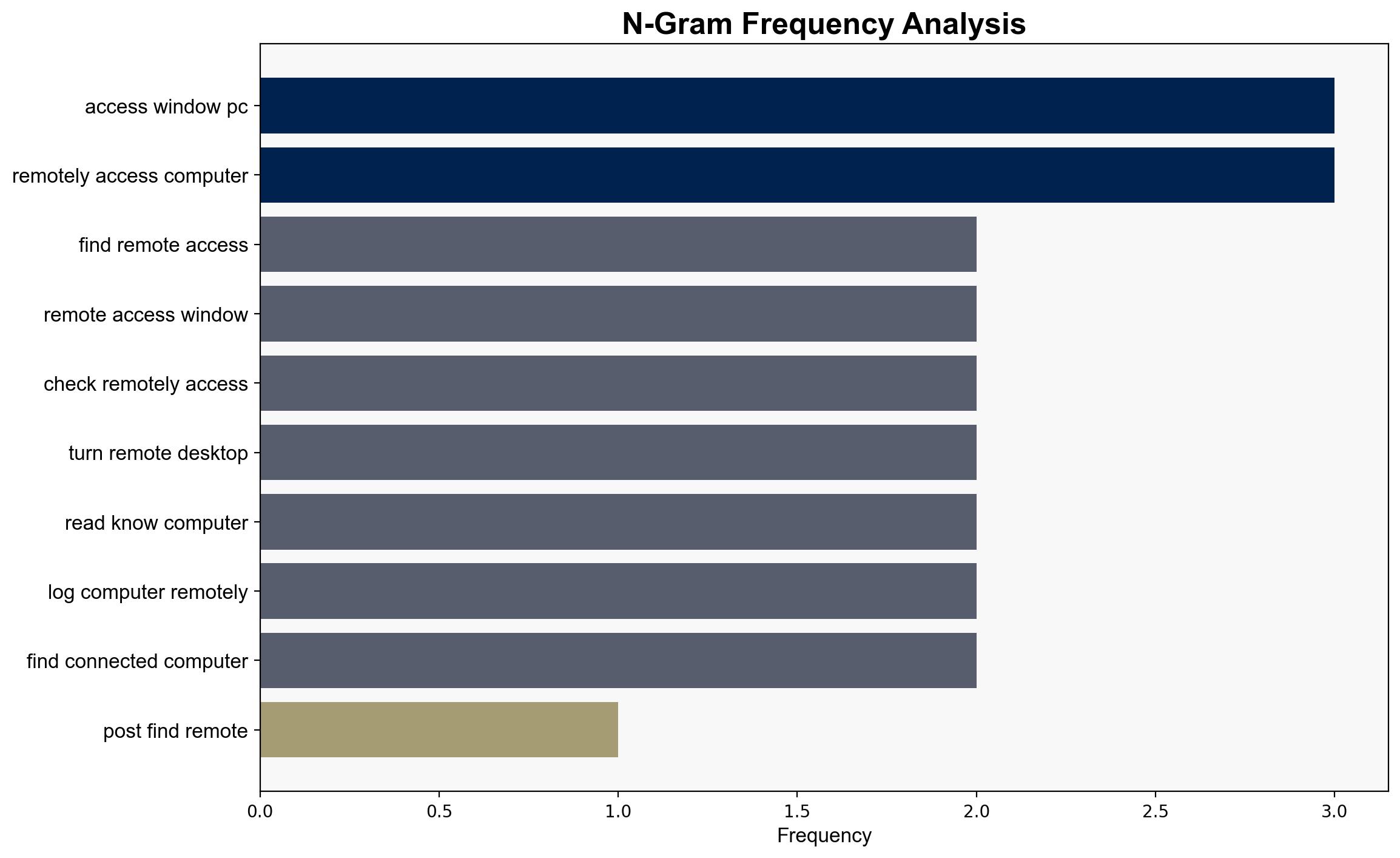
Warning signs of remote access include new user accounts, unexpected software installations, and unusual network traffic patterns. Monitoring event logs for remote logon attempts can provide early detection of unauthorized access.
3. Implications and Strategic Risks
The prevalence of remote access vulnerabilities poses risks to personal and organizational data security. Economically, data breaches can lead to significant financial losses and reputational damage. Politically, state-sponsored cyber activities may exploit these vulnerabilities for espionage.
4. Recommendations and Outlook
- Disable remote desktop features when not in use to reduce exposure to unauthorized access.
- Conduct regular security audits and update software to patch vulnerabilities.
- Implement network monitoring solutions to detect and respond to suspicious activities promptly.
- Scenario-based projection: If current trends continue, expect an increase in remote access attempts, necessitating stronger cybersecurity measures and user education.
5. Key Individuals and Entities
Not applicable for this report.