This Tesla Attack Wants Your Data What You Need To Know – Forbes
Published on: 2025-04-20
Intelligence Report: This Tesla Attack Wants Your Data What You Need To Know – Forbes
1. BLUF (Bottom Line Up Front)
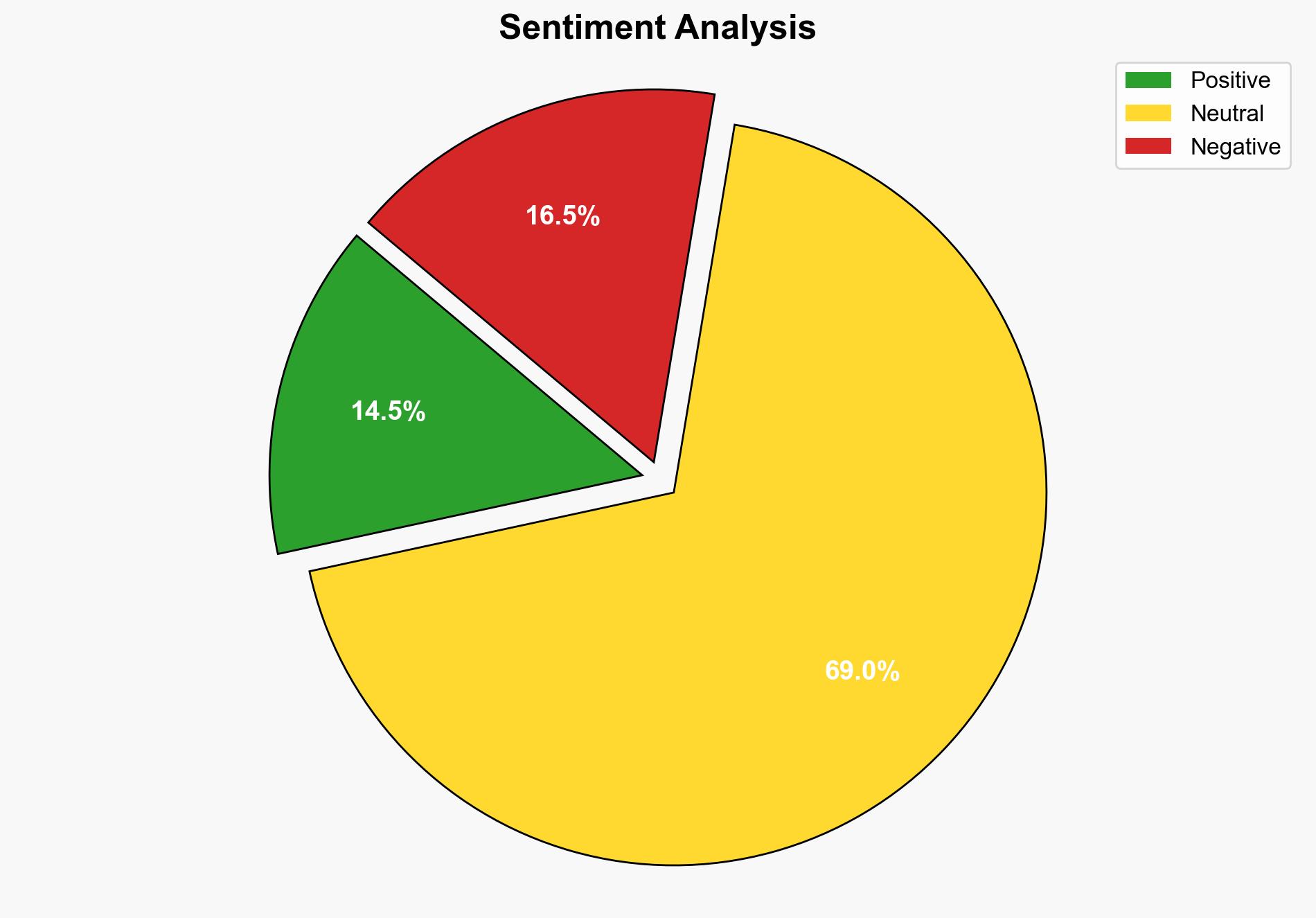
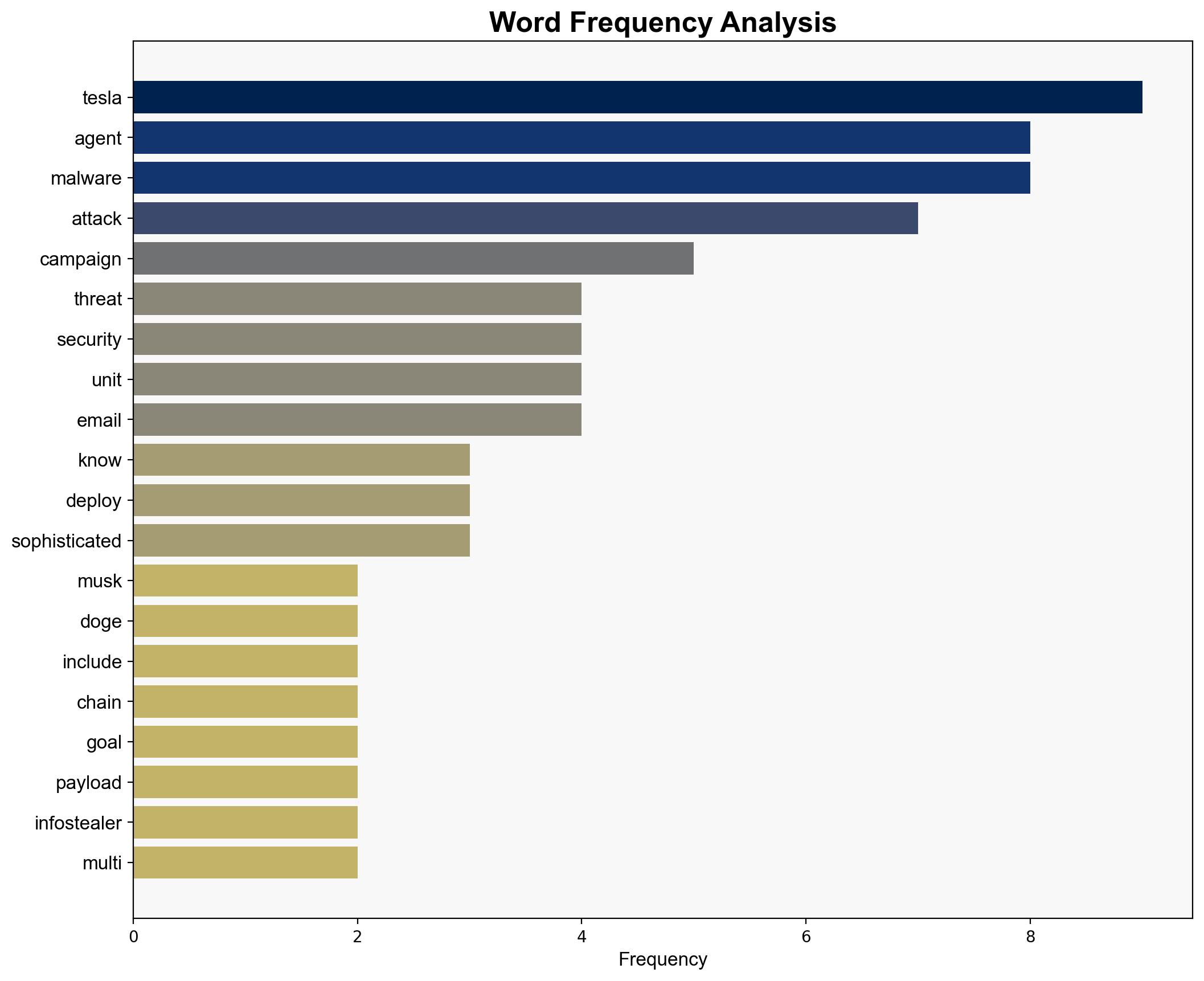
A sophisticated cyber threat campaign targeting Tesla has been identified, deploying Agent Tesla malware to steal sensitive data. The primary goal is data exfiltration using advanced techniques to evade detection. Immediate actions are required to enhance cybersecurity measures and awareness to mitigate potential impacts on data integrity and privacy.
2. Detailed Analysis
The following structured analytic techniques have been applied:
Scenario Analysis
The attack could lead to significant data breaches affecting Tesla’s operational integrity and customer trust. Potential scenarios include increased cyber operations targeting other high-profile technology firms, leading to broader implications for national cybersecurity.
Key Assumptions Check
It is assumed that the attack is driven by financial motives, given the malware’s focus on data theft. The assumption that traditional security measures are sufficient is challenged by the malware’s ability to bypass these defenses.
Indicators Development
Indicators of escalating threats include increased phishing attempts, the deployment of multi-stage malware, and the use of sophisticated evasion techniques. Monitoring these indicators can help in early detection and response.
3. Implications and Strategic Risks
The attack highlights vulnerabilities in cybersecurity frameworks, posing risks to data privacy and national security. Economic implications include potential financial losses and reputational damage to Tesla and similar entities. Politically, such attacks could strain international relations if linked to state-sponsored actors.
4. Recommendations and Outlook
- Enhance email security protocols and conduct regular phishing awareness training for employees.
- Implement multi-layered security systems and ensure regular updates to software and firmware to address known vulnerabilities.
- Adopt strong authentication and access control measures to protect sensitive data.
- Scenario-based projections suggest increased cyber threats; therefore, proactive threat intelligence and monitoring are essential.
5. Key Individuals and Entities
Elon Musk, Kriti Awasthi.