Explzh 971 – Neowin
Published on: 2025-04-20
Intelligence Report: Explzh 971 – Neowin
1. BLUF (Bottom Line Up Front)
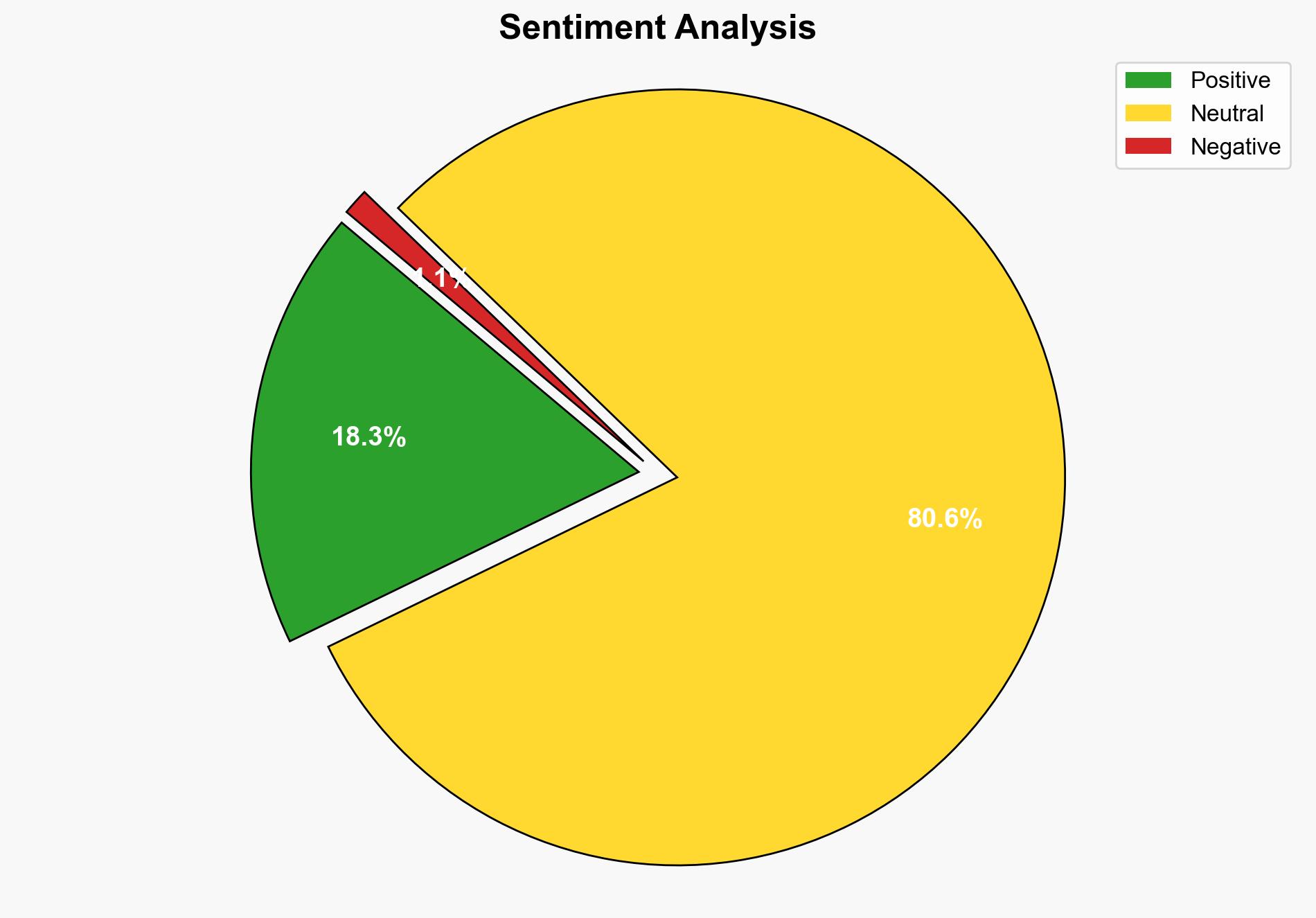
Explzh 971 is a comprehensive archive management tool with extensive format support and advanced features such as AES encryption and digital signatures. While it offers robust data protection and file management capabilities, potential vulnerabilities could arise from its integration with various file formats and digital signature processes. It is crucial to monitor for any security updates or patches to mitigate risks associated with these features.
2. Detailed Analysis
The following structured analytic techniques have been applied:
Analysis of Competing Hypotheses (ACH)
The integration of multiple archive formats and encryption methods could be targeted for exploitation. The motivations behind any potential breaches could include unauthorized data access, data manipulation, or disruption of service.
SWOT Analysis
Strengths: Wide range of supported formats, strong encryption options, and user-friendly interface.
Weaknesses: Potential vulnerabilities in handling multiple formats and digital signature processes.
Opportunities: Enhancements in security features could increase user trust and adoption.
Threats: Cyberattacks exploiting integration points or encryption weaknesses.
Indicators Development
Warning signs of emerging threats include unusual access patterns, failed signature verifications, and reports of data breaches involving archive files.
3. Implications and Strategic Risks
The use of Explzh in sensitive environments could pose risks if vulnerabilities are exploited. This could lead to unauthorized data access or integrity issues, impacting both security and economic interests. Monitoring updates and user feedback is essential to identify and address potential threats promptly.
4. Recommendations and Outlook
- Regularly update Explzh to the latest version to ensure all security patches are applied.
- Conduct periodic security audits focusing on encryption and digital signature processes.
- Develop contingency plans for potential data breaches involving archive files.
- Consider scenario-based simulations to prepare for possible exploitation of vulnerabilities.
5. Key Individuals and Entities
No specific individuals or entities are mentioned in the provided data. Monitoring the development team and associated cybersecurity experts could provide insights into future updates and security measures.