North Korea Iran Russia-Backed Hackers Deploy ClickFix in New Attacks – HackRead
Published on: 2025-04-21
Intelligence Report: North Korea Iran Russia-Backed Hackers Deploy ClickFix in New Attacks – HackRead
1. BLUF (Bottom Line Up Front)
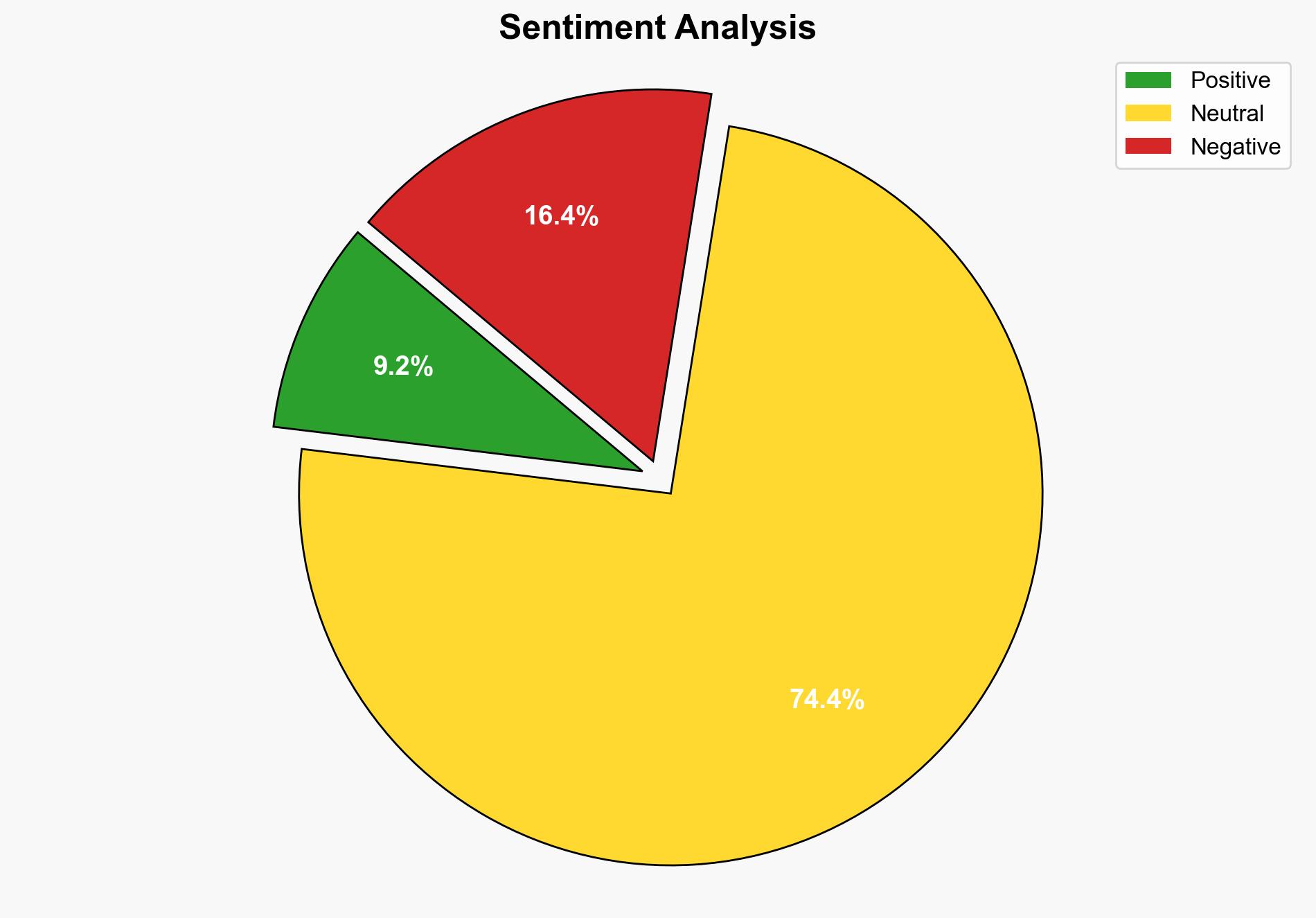
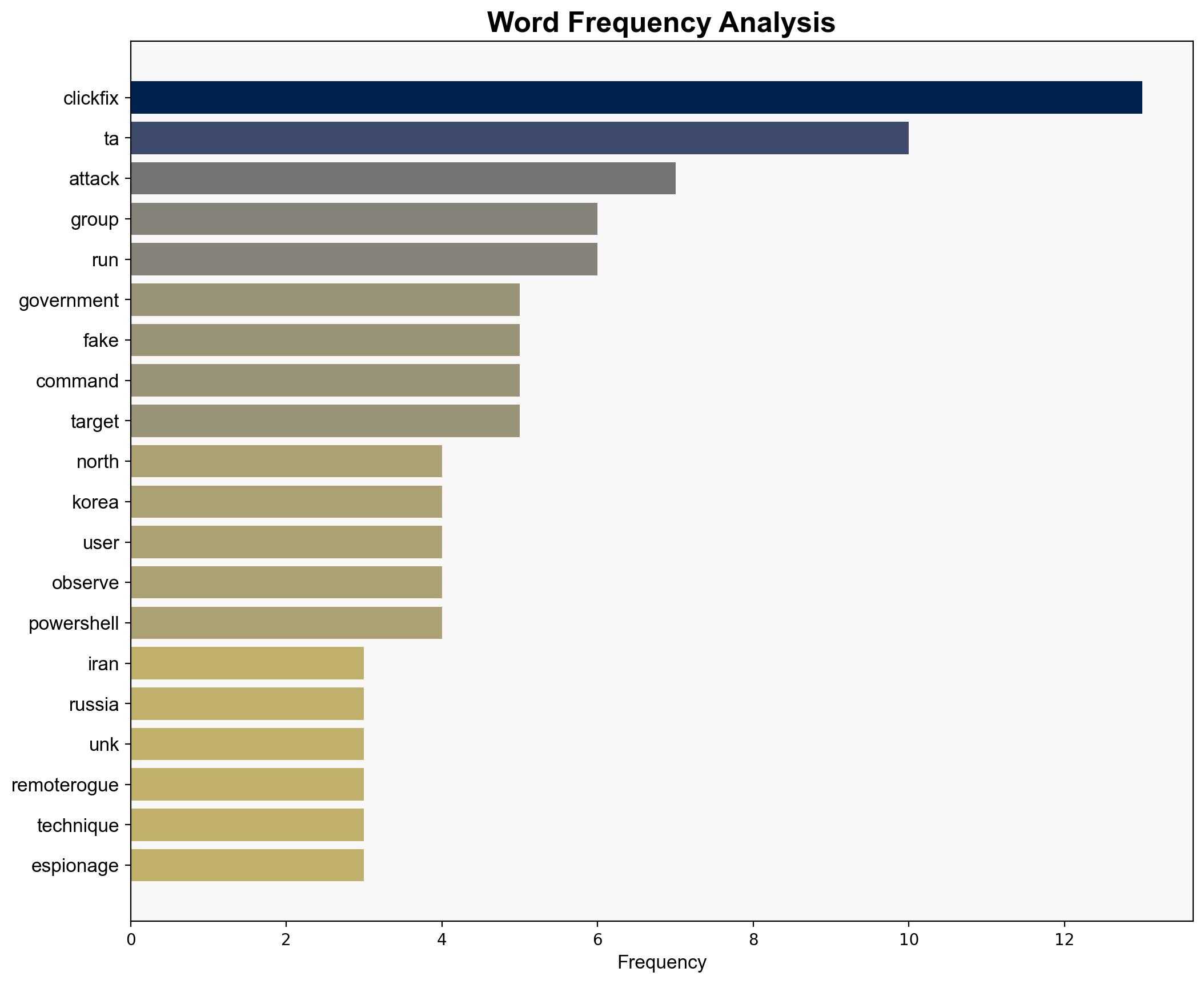
Recent intelligence indicates that state-backed hacking groups from North Korea, Iran, and Russia have intensified their cyber espionage activities using a technique known as ClickFix. This method exploits user trust through social engineering, leading to the execution of malicious commands on victim machines. The campaign targets sectors such as finance, government, and defense, with significant implications for national security. Immediate countermeasures are recommended to mitigate these threats.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Analysis of Competing Hypotheses (ACH)
The evidence suggests that the ClickFix technique is primarily used for espionage by state-sponsored actors. Alternative hypotheses, such as criminal syndicates using the technique for financial gain, are less supported by the current data.
SWOT Analysis
Strengths: Advanced social engineering tactics increase the success rate of attacks.
Weaknesses: Reliance on user interaction may limit the scope of successful breaches.
Opportunities: Increased awareness and training can reduce susceptibility.
Threats: Continued evolution of tactics could outpace current defense mechanisms.
Indicators Development
Key indicators include increased phishing campaigns, fake security alerts, and unusual command line activities. Monitoring these signs can provide early warnings of potential attacks.
3. Implications and Strategic Risks
The use of ClickFix by state actors poses significant risks to national security, particularly in sectors critical to political and economic stability. The potential for data theft and system compromise could lead to cascading effects, impacting international relations and economic confidence.
4. Recommendations and Outlook
- Enhance cybersecurity training focused on recognizing and responding to social engineering tactics.
- Implement advanced monitoring systems to detect and respond to phishing and command line anomalies.
- Scenario-based projections suggest that without intervention, the frequency and sophistication of attacks will increase, posing greater risks to national infrastructure.
5. Key Individuals and Entities
Notable groups involved include TA Kimsuky, Emerald Sleet, TA MuddyWater, Mango Sandstorm, and TA Sofacy. These entities have been linked to the deployment of ClickFix in recent campaigns.
6. Thematic Tags
(‘national security threats, cybersecurity, counter-terrorism, regional focus’, ‘cybersecurity’, ‘counter-terrorism’, ‘regional focus’)