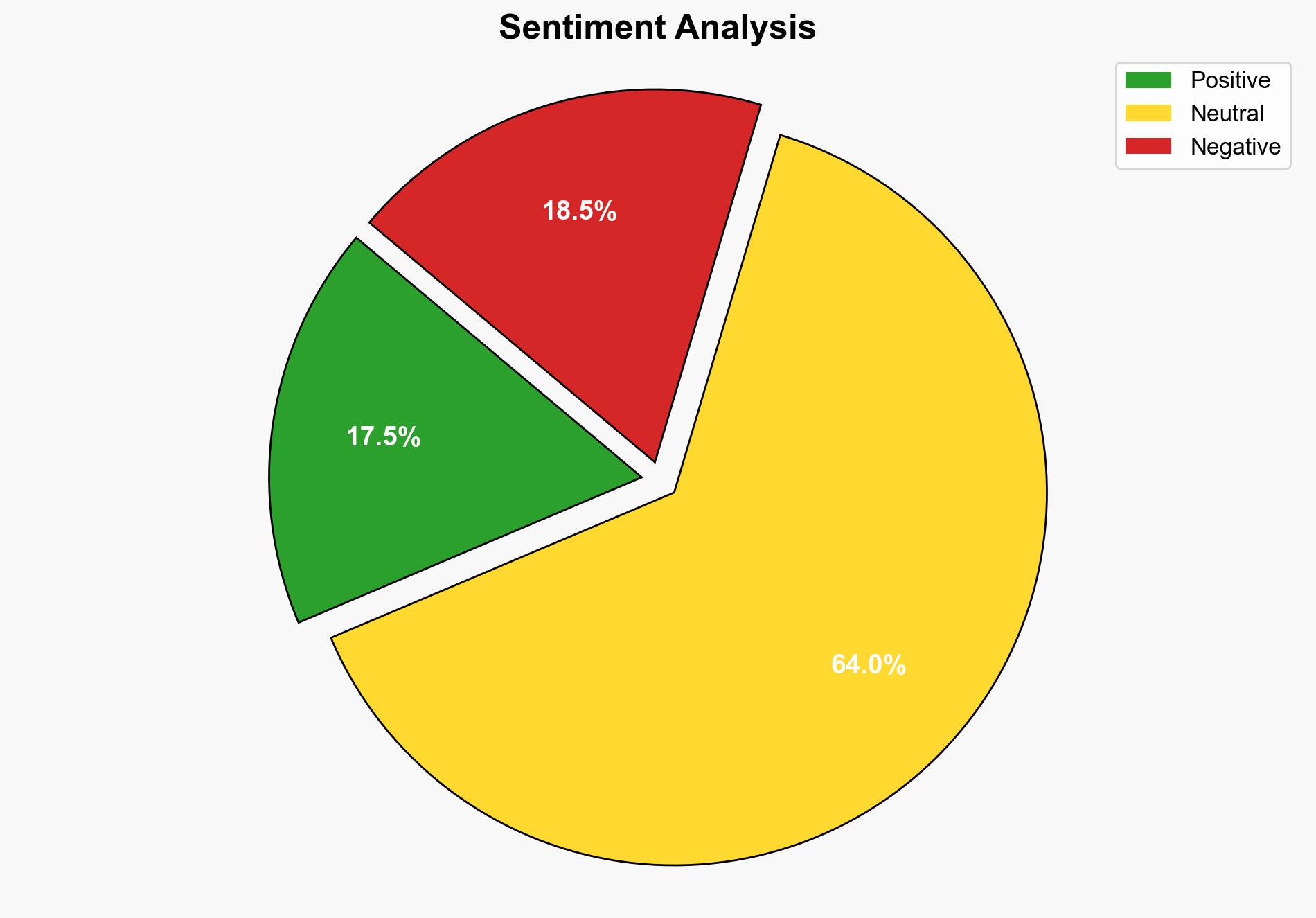
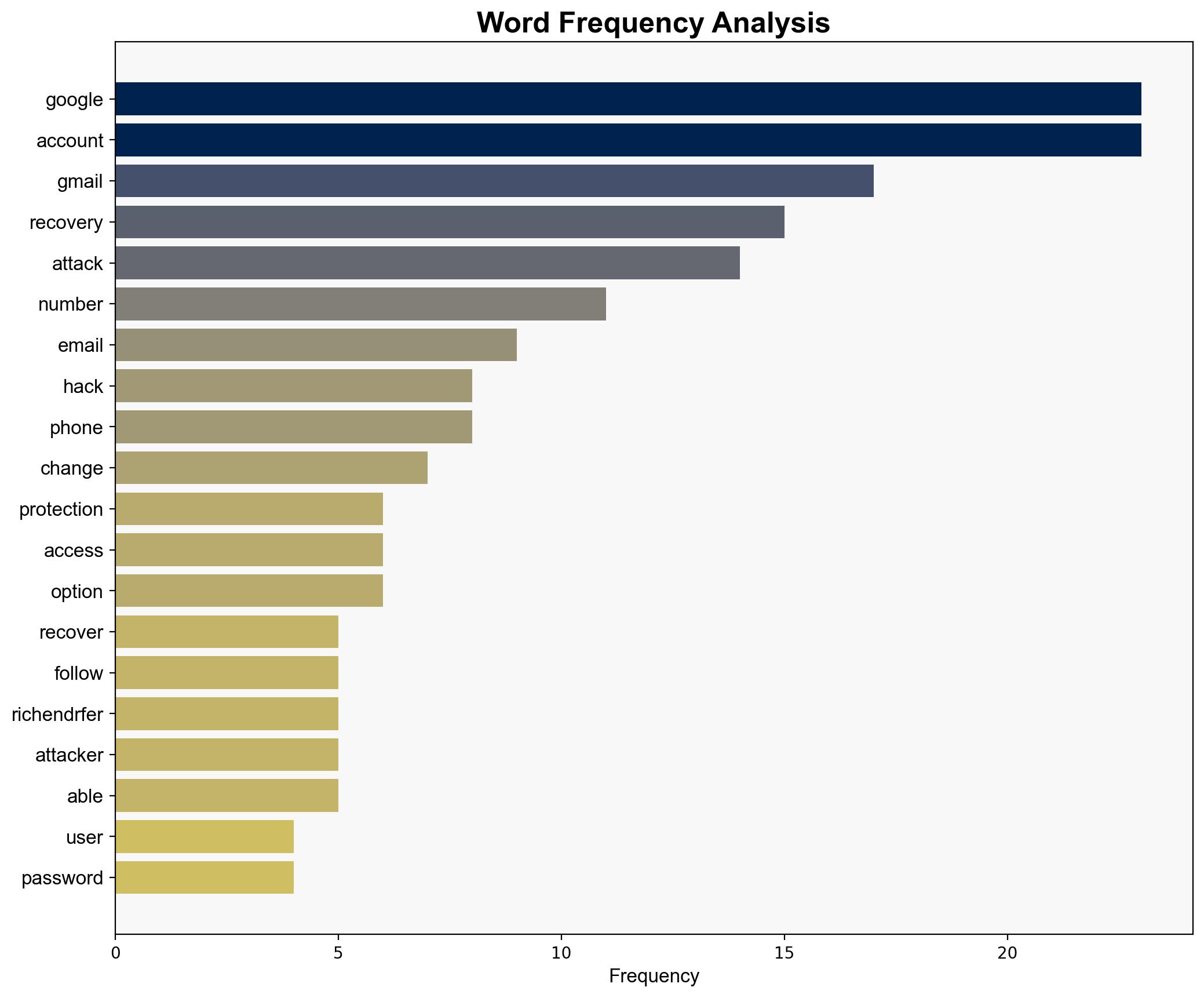
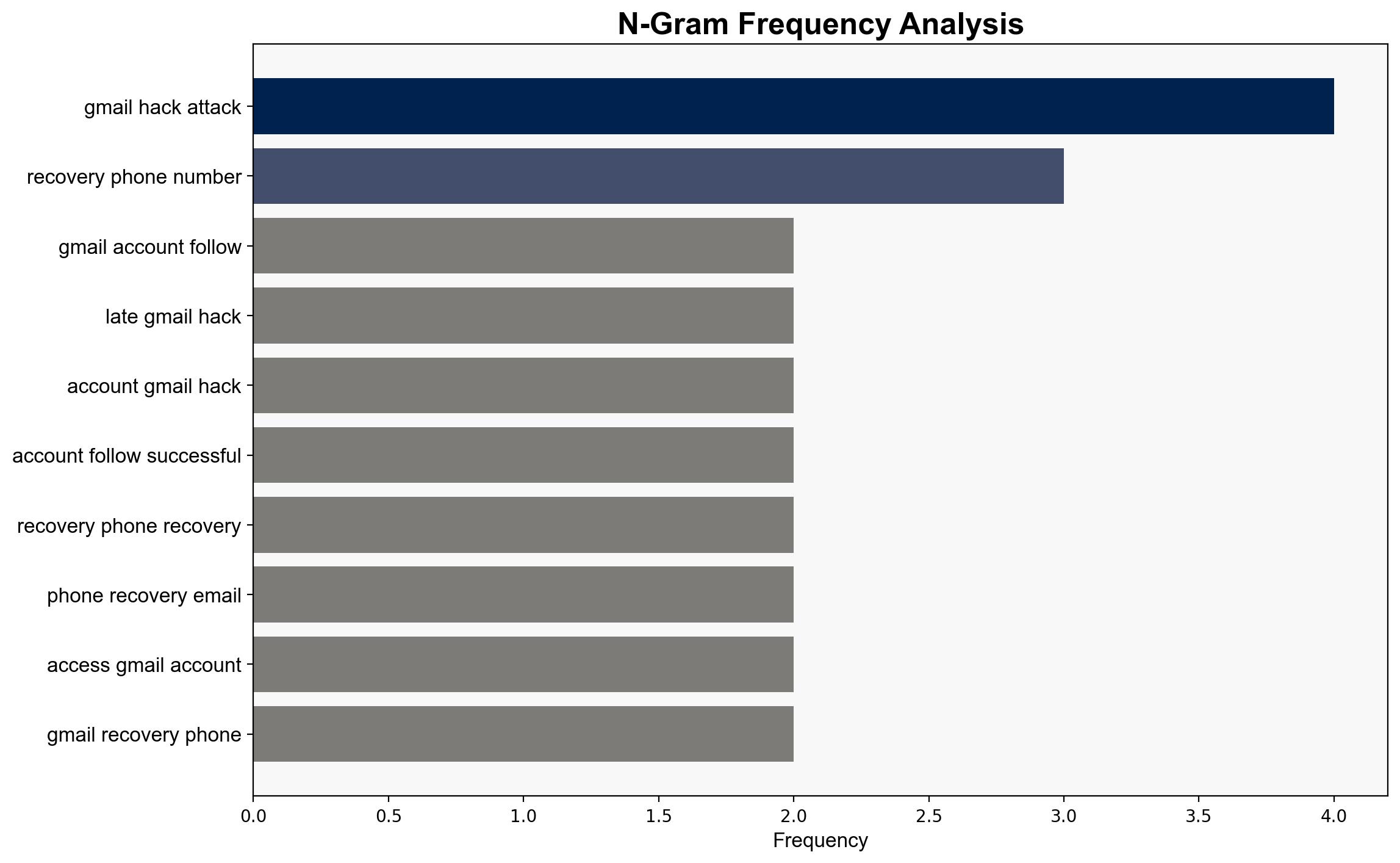
Gmail Hack Attack Google Says You Have 7 Days To Act – Forbes
Published on: 2025-04-21
Intelligence Report: Gmail Hack Attack Google Says You Have 7 Days To Act – Forbes
1. BLUF (Bottom Line Up Front)
A recent sophisticated phishing campaign has targeted Gmail users, exploiting OAuth applications and bypassing Google’s security measures. Users have a limited window of seven days to recover compromised accounts. Immediate action is required to prevent data breaches and unauthorized access. Enhanced security measures, including phishing-resistant authentication, are recommended.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Analysis of Competing Hypotheses (ACH)
The primary hypothesis is that the attack is a coordinated effort by advanced threat actors using AI-driven techniques to automate password hacking. Alternative hypotheses, such as isolated incidents or insider threats, are less supported by the evidence.
SWOT Analysis
Strengths: Google’s proactive security updates and user education initiatives.
Weaknesses: Current security measures can be bypassed by sophisticated phishing techniques.
Opportunities: Implementing advanced authentication methods like security keys or passkeys.
Threats: Increasing sophistication of phishing attacks and potential for widespread data breaches.
Indicators Development
Key indicators include unusual login attempts, changes in recovery information, and the presence of unauthorized OAuth applications. Monitoring these signs can help detect and mitigate ongoing or emerging threats.
3. Implications and Strategic Risks
The attack highlights systemic vulnerabilities in email security, with potential cascading effects on personal and organizational data integrity. The increasing use of AI in cyber-attacks poses a significant risk to global cybersecurity frameworks, necessitating enhanced cross-domain collaboration and threat intelligence sharing.
4. Recommendations and Outlook
- Implement multi-factor authentication and encourage users to update recovery information regularly.
- Conduct awareness campaigns on recognizing phishing attempts and securing personal information.
- Best Case: Users adopt enhanced security measures, reducing the impact of future attacks.
- Worst Case: Failure to act leads to widespread data breaches and loss of user trust.
- Most Likely: Incremental improvements in security posture with ongoing threat adaptation.
5. Key Individuals and Entities
Ross Richendrfer, Google spokesperson, has provided insights into the recovery process and security recommendations.
6. Thematic Tags
(‘national security threats, cybersecurity, counter-terrorism, regional focus’, ‘cybersecurity’, ‘counter-terrorism’, ‘regional focus’)