The popular xrpljs Ripple cryptocurrency library was compromised in a supply chain attack – Securityaffairs.com
Published on: 2025-04-23
Intelligence Report: The popular xrpljs Ripple cryptocurrency library was compromised in a supply chain attack – Securityaffairs.com
1. BLUF (Bottom Line Up Front)
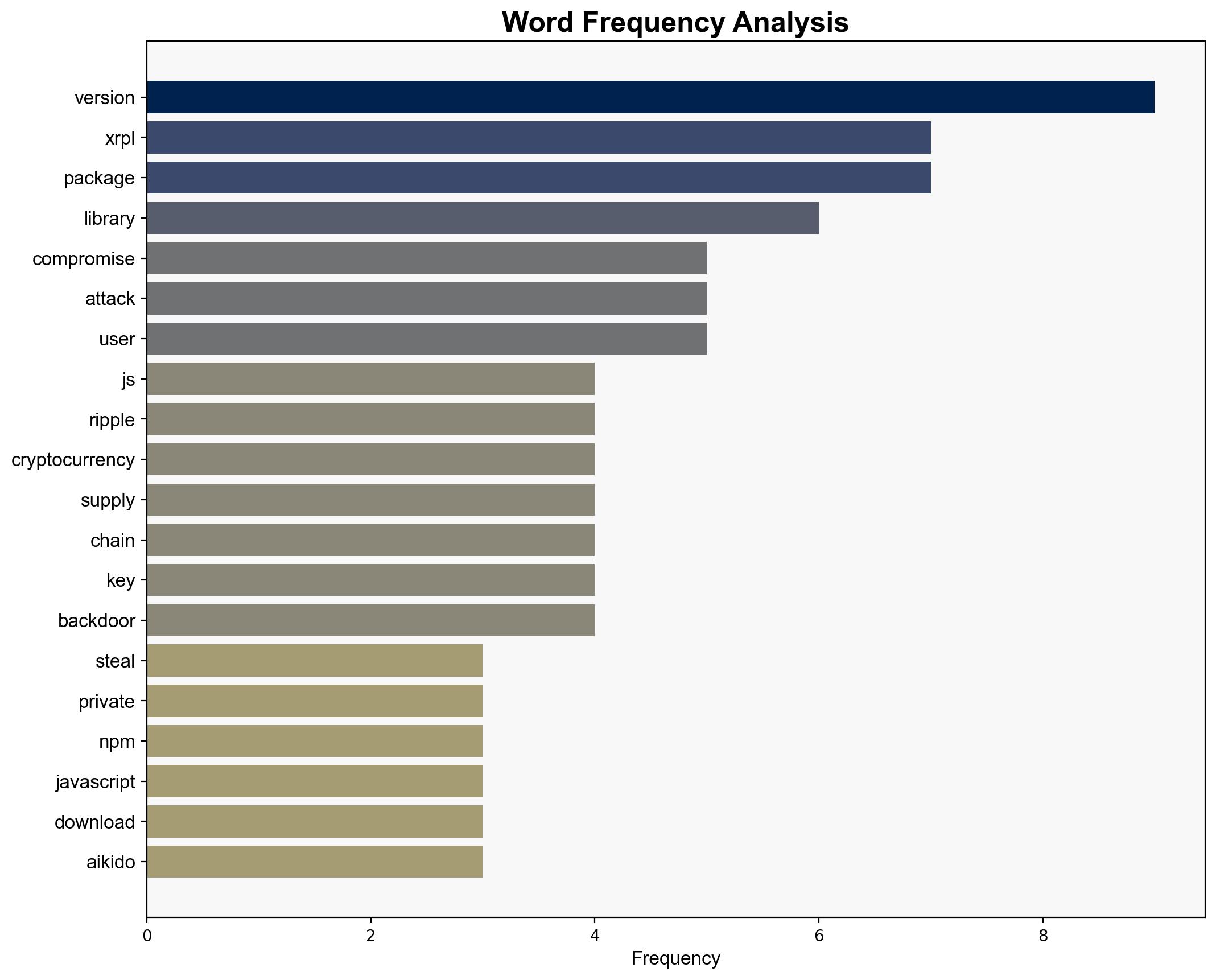
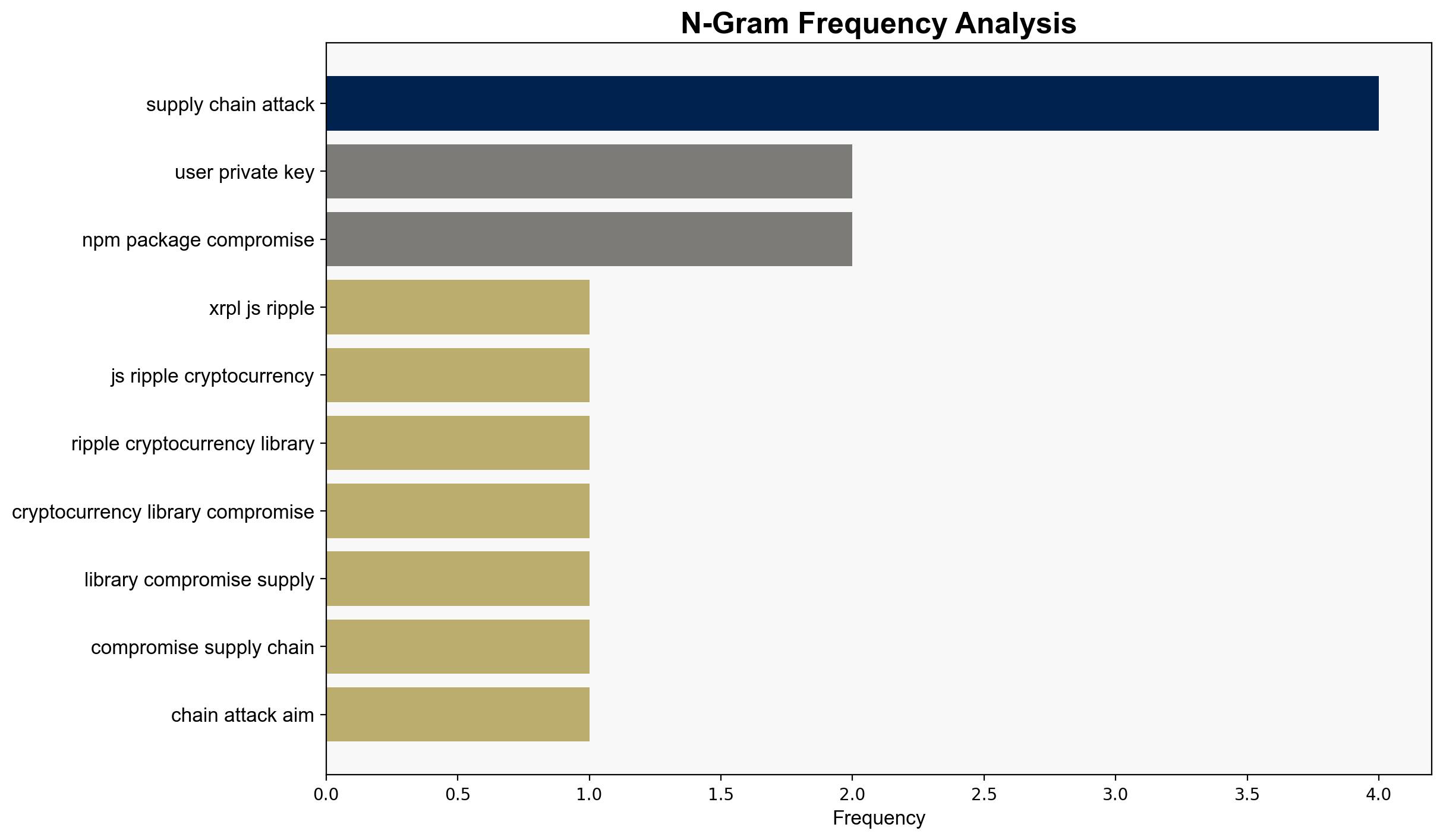
The xrpljs Ripple cryptocurrency library was compromised in a sophisticated supply chain attack, aiming to steal user private keys. The attack involved the insertion of malicious code into the official npm package, potentially affecting millions of users. Immediate updates to the latest secure version are recommended to mitigate risks.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Scenario Analysis
The compromise of the xrpljs library could lead to increased theft of cryptocurrency assets, undermining trust in digital financial systems. Future scenarios may include heightened scrutiny of open-source libraries and increased investment in supply chain security.
Key Assumptions Check
It is assumed that the attack was financially motivated, targeting user private keys for theft. This assumption is based on the nature of the malicious code and its intended function.
Indicators Development
Indicators of further compromise include unusual network traffic to suspicious domains, unauthorized access attempts to cryptocurrency wallets, and multiple version changes in open-source libraries without clear justification.
3. Implications and Strategic Risks
The attack highlights systemic vulnerabilities in software supply chains, particularly in open-source ecosystems. There is a risk of cascading effects, as compromised libraries can be integrated into numerous applications, potentially affecting broader financial and technological infrastructures.
4. Recommendations and Outlook
- Encourage immediate updates to the latest secure version of the xrpljs library to prevent further exploitation.
- Implement robust monitoring and alert systems for detecting unauthorized changes in software dependencies.
- Scenario-based projections: Best case – Rapid patching and user compliance mitigate risks; Worst case – Widespread exploitation leads to significant financial losses; Most likely – Gradual adoption of security measures reduces immediate threats.
5. Key Individuals and Entities
Mukulljangid is identified as a key individual associated with the release of the malware-laced version of the library.
6. Thematic Tags
(‘cybersecurity’, ‘supply chain security’, ‘cryptocurrency’, ‘open-source vulnerabilities’)