An Employee Surveillance Company Leaked Over 21 Million Screenshots Online – Gizmodo.com
Published on: 2025-04-24
Intelligence Report: An Employee Surveillance Company Leaked Over 21 Million Screenshots Online – Gizmodo.com
1. BLUF (Bottom Line Up Front)
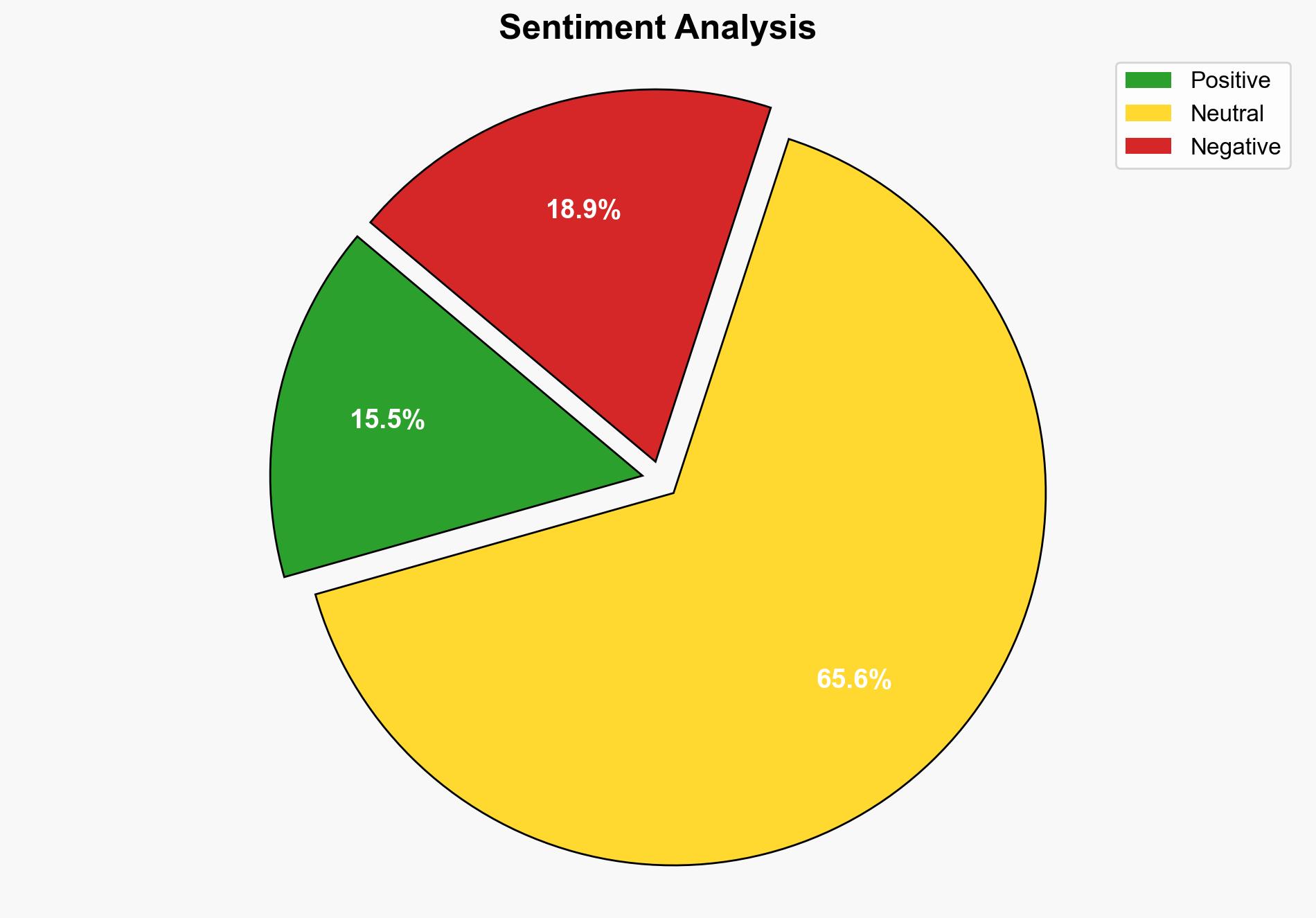
A significant data breach involving WorkComposer has exposed over 21 million screenshots of employee computer activity. This incident underscores the vulnerabilities inherent in employee surveillance technologies and poses substantial risks to personal privacy and corporate security. Immediate actions are recommended to secure data and reassess surveillance practices.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Analysis of Competing Hypotheses (ACH)
The breach could result from inadequate security protocols, insider threats, or external cyberattacks. Evidence suggests a lack of robust data protection measures as the most plausible explanation.
SWOT Analysis
Strengths: WorkComposer’s comprehensive monitoring capabilities.
Weaknesses: Insufficient data security measures.
Opportunities: Implementing enhanced cybersecurity protocols.
Threats: Potential legal and reputational repercussions.
Indicators Development
Monitor for signs of unauthorized access or data exfiltration, such as unusual network activity or phishing attempts targeting affected employees.
3. Implications and Strategic Risks
The breach highlights systemic vulnerabilities in digital surveillance tools, potentially leading to increased regulatory scrutiny and demands for stronger privacy protections. This incident could trigger a broader reassessment of surveillance practices across industries.
4. Recommendations and Outlook
- Secure all exposed data immediately and conduct a comprehensive security audit.
- Reevaluate and strengthen data protection protocols to prevent future breaches.
- Engage with stakeholders to address privacy concerns and rebuild trust.
- Scenario projections:
- Best Case: Rapid containment and improved security measures restore confidence.
- Worst Case: Prolonged data exposure leads to legal actions and reputational damage.
- Most Likely: Short-term reputational impact with gradual recovery following security enhancements.
5. Key Individuals and Entities
Jos Martinez
6. Thematic Tags
(‘cybersecurity’, ‘data breach’, ‘privacy’, ’employee surveillance’)