Pete Hegseth faces overlapping new embarrassments amid Pentagon tumult – MSNBC
Published on: 2025-04-25
Intelligence Report: Pete Hegseth faces overlapping new embarrassments amid Pentagon tumult – MSNBC
1. BLUF (Bottom Line Up Front)
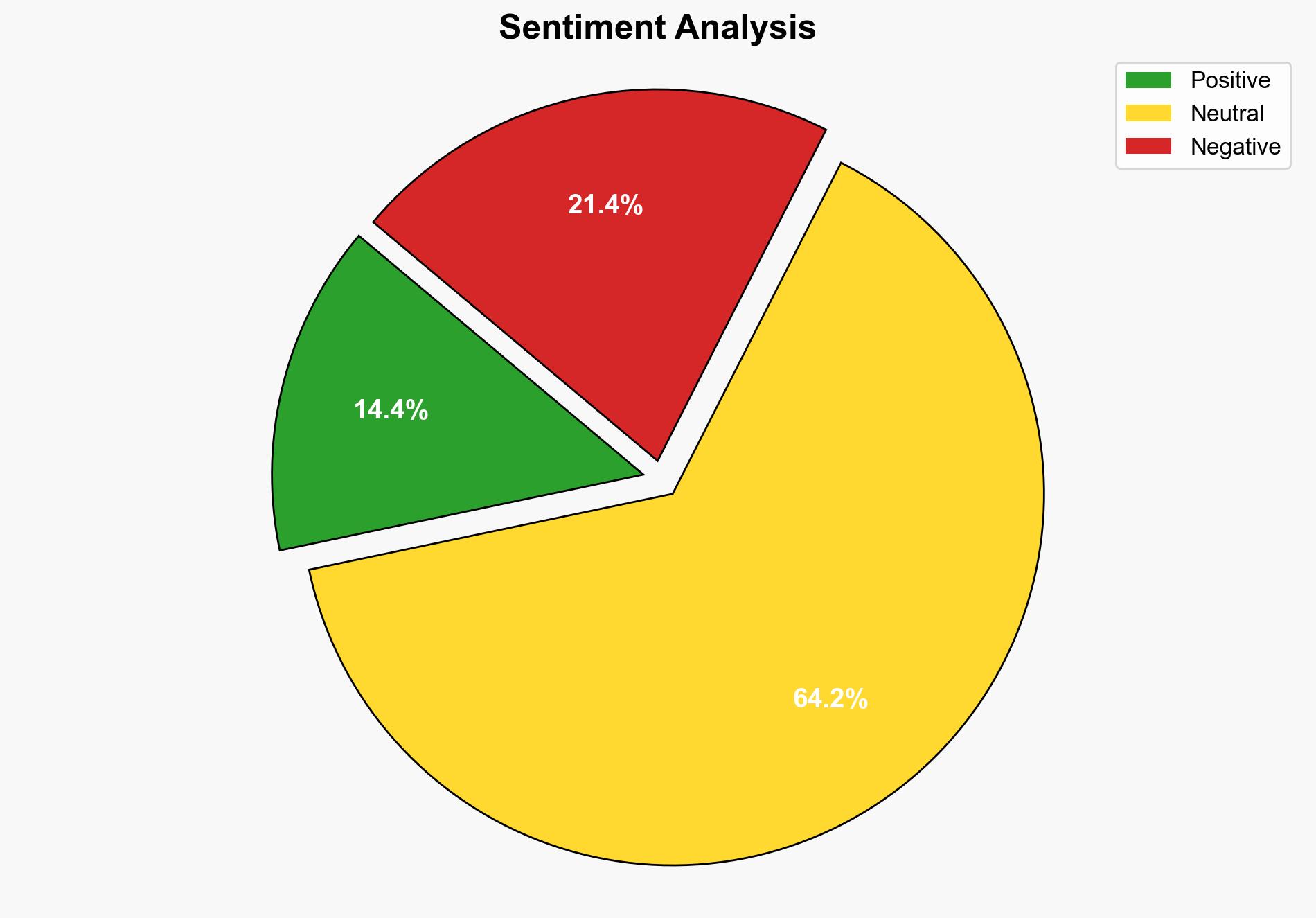
The report highlights significant security lapses and leadership challenges surrounding Pete Hegseth, exacerbating existing Pentagon instability. Key findings suggest vulnerabilities in cybersecurity protocols and potential exposure of sensitive information, necessitating immediate corrective actions to safeguard national security interests.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Analysis of Competing Hypotheses (ACH)
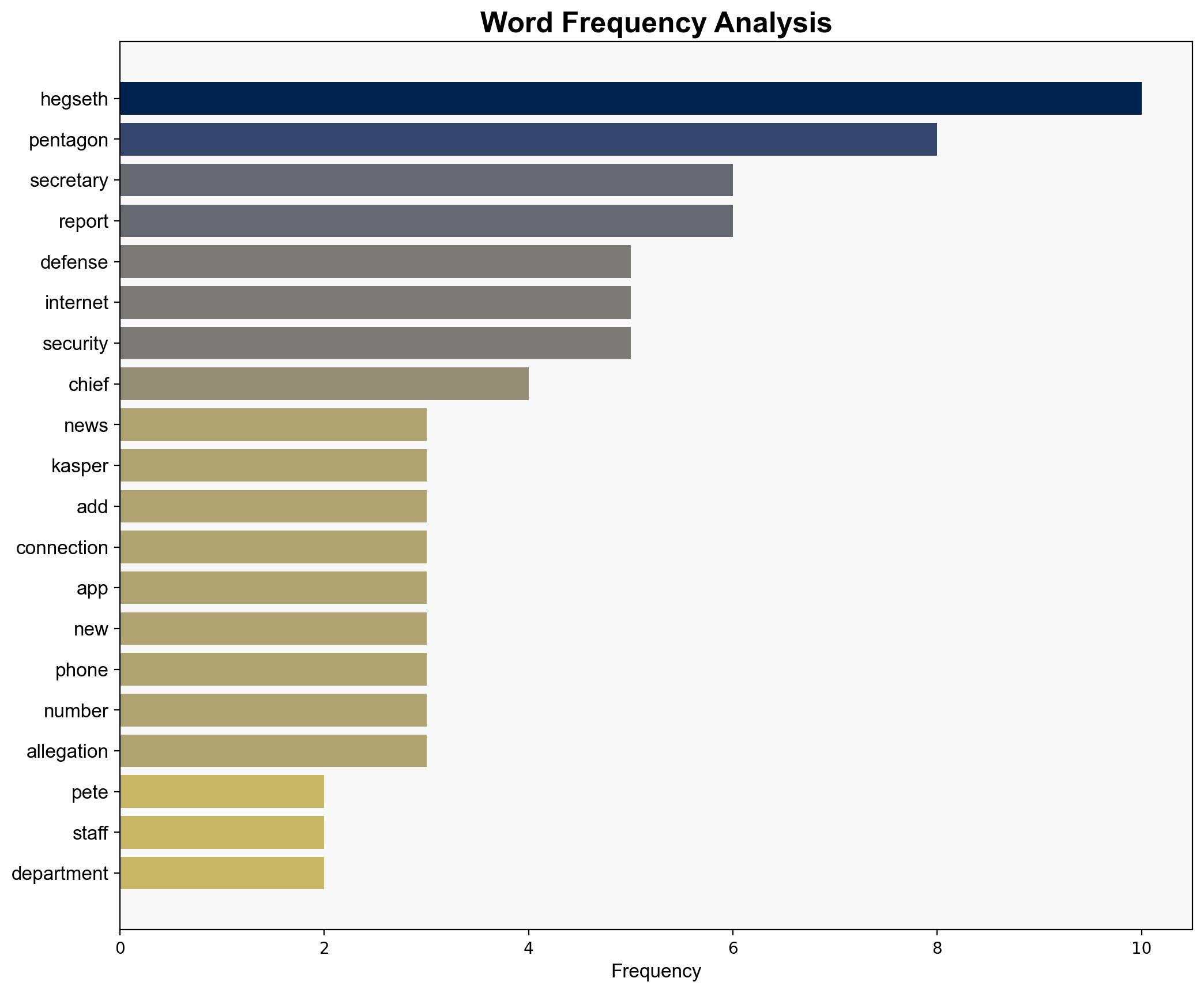
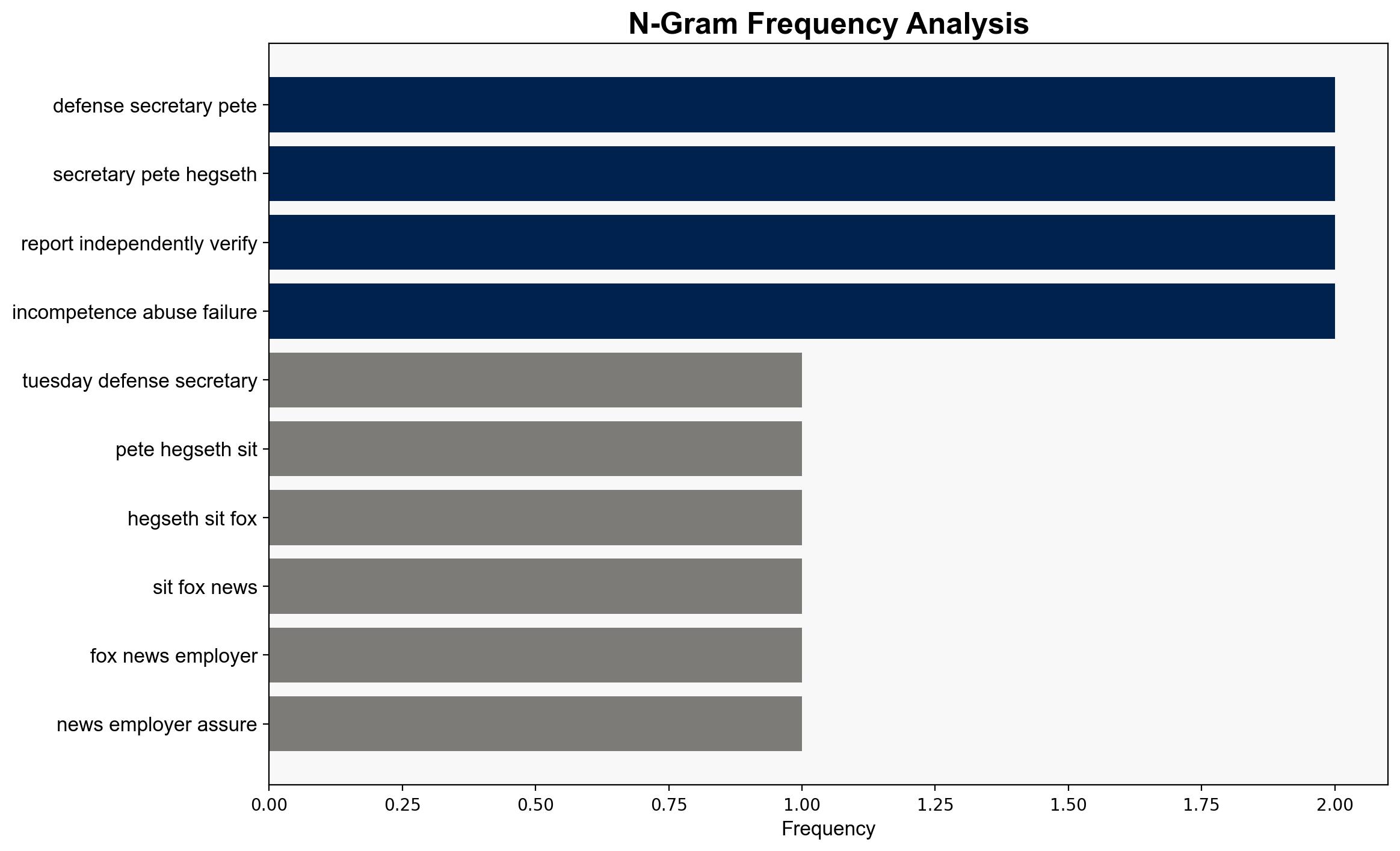
Multiple hypotheses were considered regarding the cyber incidents involving Pete Hegseth. The most plausible explanation points to inadequate cybersecurity measures and oversight, leading to potential data breaches and unauthorized access to sensitive information.
SWOT Analysis
Strengths include existing cybersecurity frameworks, while weaknesses are evident in their implementation. Opportunities lie in enhancing security protocols, and threats are posed by potential foreign adversary exploitation of these vulnerabilities.
Indicators Development
Key indicators of ongoing cyber threats include unusual network traffic patterns, unauthorized access attempts, and phishing campaigns targeting personnel. Monitoring these signs is crucial for early threat detection and response.
3. Implications and Strategic Risks
The current situation poses significant risks to national security, with potential for cascading effects across military and political domains. The exposure of sensitive information could lead to strategic disadvantages and undermine trust in leadership.
4. Recommendations and Outlook
- Immediate review and enhancement of cybersecurity protocols to prevent unauthorized access and data breaches.
- Conduct a comprehensive audit of communication channels and devices used by key personnel.
- Implement scenario-based training to prepare for potential cyber threats and breaches.
- Best case: Strengthened cybersecurity posture and restored confidence in leadership. Worst case: Continued breaches leading to significant national security threats. Most likely: Incremental improvements with ongoing challenges.
5. Key Individuals and Entities
Pete Hegseth, Joe Kasper, Mike Casey
6. Thematic Tags
(‘national security threats, cybersecurity, counter-terrorism, regional focus’, ‘cybersecurity’, ‘counter-terrorism’, ‘regional focus’)