SAP Fixes Critical Vulnerability After Evidence of Exploitation – Infosecurity Magazine
Published on: 2025-04-25
Intelligence Report: SAP Fixes Critical Vulnerability After Evidence of Exploitation – Infosecurity Magazine
1. BLUF (Bottom Line Up Front)
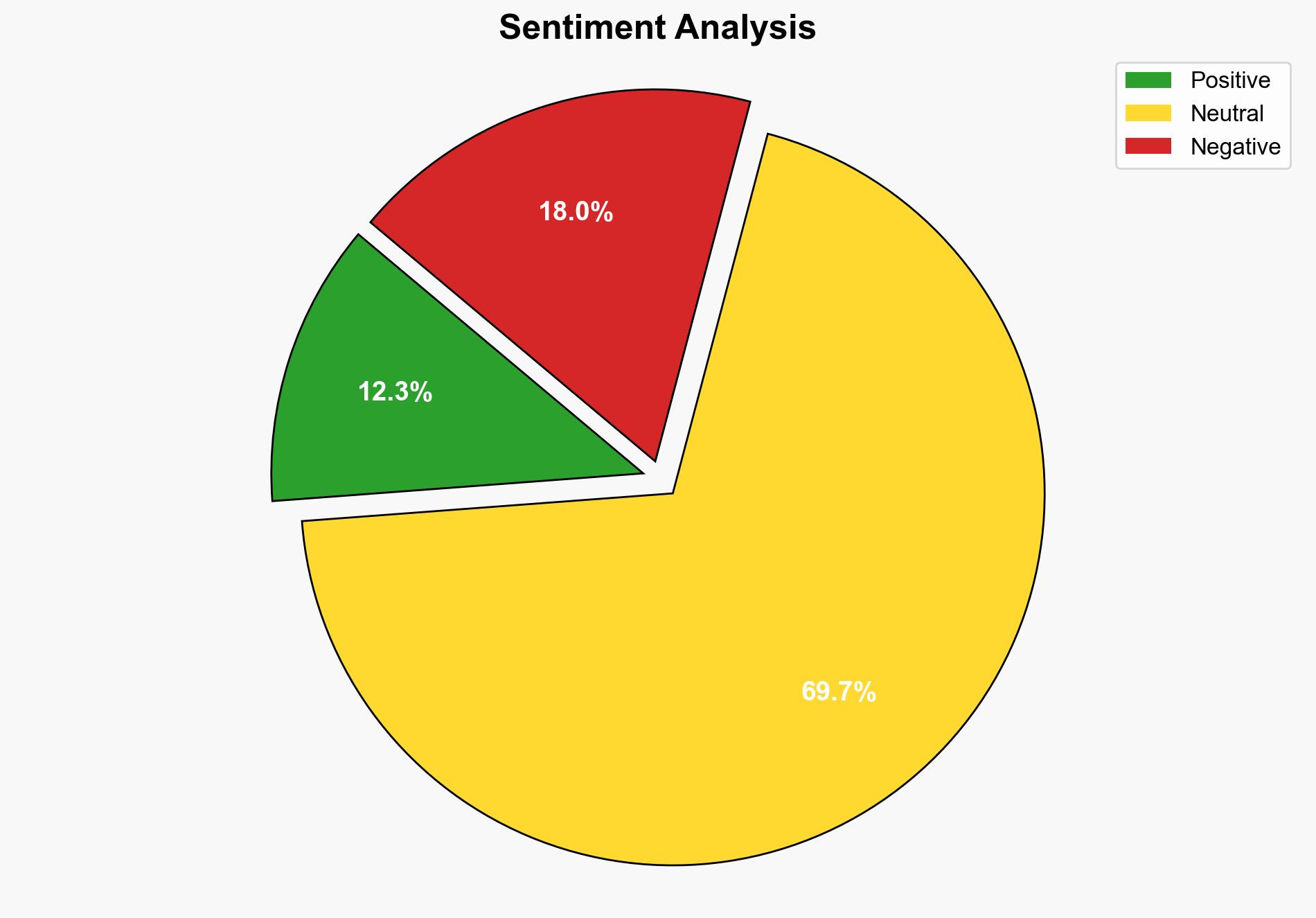
SAP has addressed a critical vulnerability in its NetWeaver Visual Composer, following evidence of exploitation in the wild. The vulnerability, tracked as CVE, allowed unauthorized file uploads, posing significant risks to system integrity and confidentiality. Immediate application of SAP’s emergency security update is crucial to mitigate potential threats.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Analysis of Competing Hypotheses (ACH)
The primary hypothesis is that the vulnerability was exploited by threat actors leveraging unauthorized file uploads to execute malicious code. Alternative explanations, such as internal misconfigurations or unrelated vulnerabilities, were tested and found less consistent with the evidence.
SWOT Analysis
Strengths: SAP’s rapid response and release of a security patch demonstrate robust incident management capabilities.
Weaknesses: Delayed disclosure and patching cycles may expose systems to zero-day exploits.
Opportunities: Enhancing real-time monitoring and threat intelligence sharing could improve proactive defenses.
Threats: Persistent exploitation attempts by sophisticated threat actors targeting unpatched systems.
Indicators Development
Key indicators include unauthorized file uploads, unexpected JSP webshell presence, and use of tools like Brute Ratel and Heavens Gate for execution evasion. Monitoring these signs can help detect ongoing or future exploitation attempts.
3. Implications and Strategic Risks
The exploitation of this vulnerability highlights the systemic risk posed by unpatched enterprise software. Government networks using SAP solutions may face increased exposure, potentially leading to unauthorized access and data breaches. The incident underscores the need for timely updates and robust cybersecurity measures.
4. Recommendations and Outlook
- Immediately apply SAP’s emergency security update to affected systems.
- Enhance monitoring for indicators of compromise, particularly unauthorized file uploads.
- Develop a comprehensive patch management strategy to reduce exposure to zero-day vulnerabilities.
- Scenario-based projections:
- Best case: Rapid patch deployment prevents further exploitation.
- Worst case: Delayed patching leads to widespread breaches.
- Most likely: Mixed patching speeds result in isolated incidents.
5. Key Individuals and Entities
ReliaQuest (investigative entity), SAP (software provider).
6. Thematic Tags
(‘national security threats, cybersecurity, counter-terrorism, regional focus’, ‘cybersecurity’, ‘counter-terrorism’, ‘regional focus’)