VeriSource data breach impacted 4M individuals – Securityaffairs.com
Published on: 2025-04-29
Intelligence Report: VeriSource Data Breach Impacted 4M Individuals – Securityaffairs.com
1. BLUF (Bottom Line Up Front)
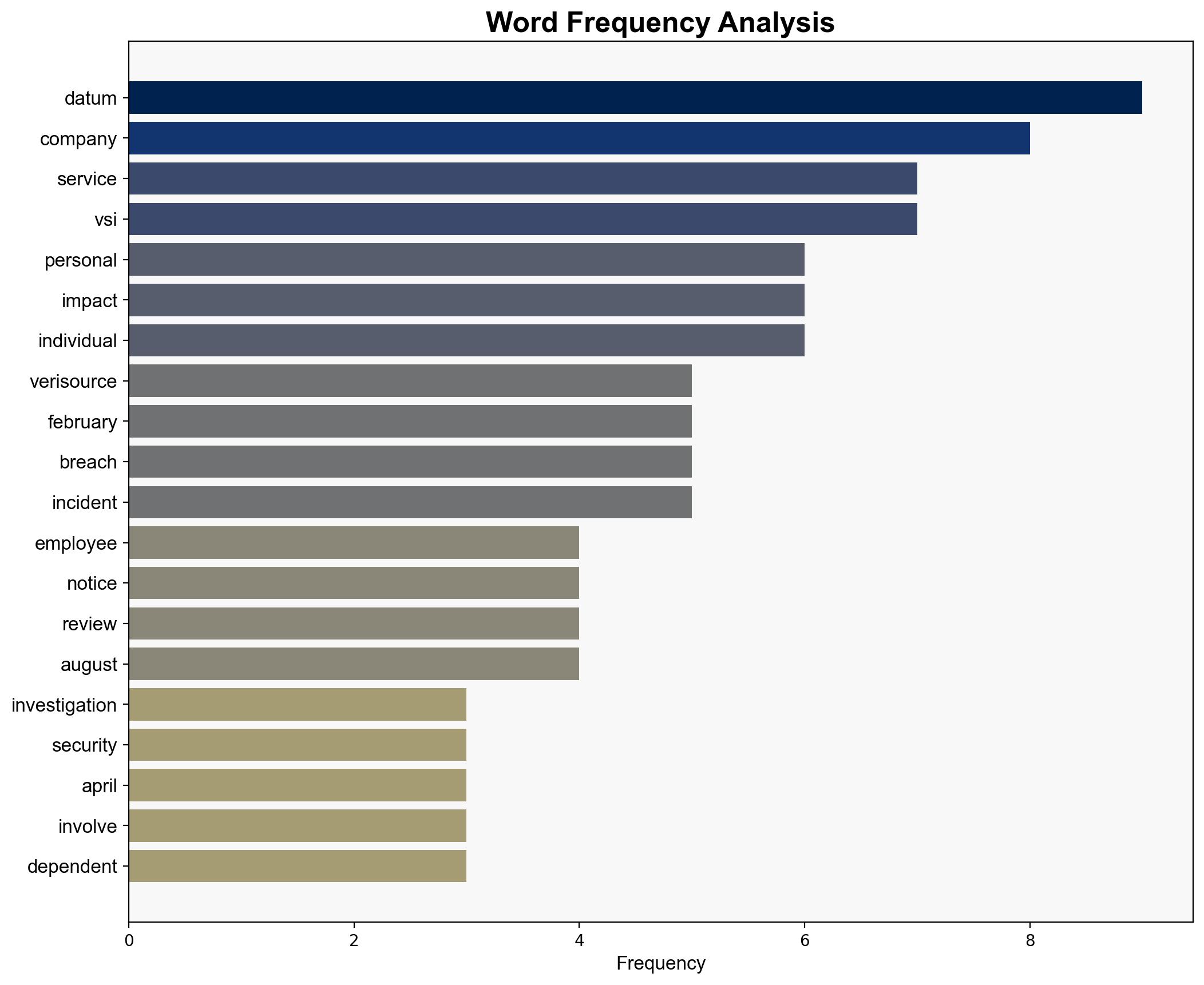
The data breach at VeriSource has compromised the personal information of approximately 4 million individuals, including employees and their dependents. The breach was discovered in February, with unauthorized access to sensitive data such as names, addresses, dates of birth, gender, and Social Security numbers. VeriSource has initiated a comprehensive response, including notifying affected individuals and offering identity protection services. The breach underscores the need for enhanced cybersecurity measures and proactive threat monitoring.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Analysis of Competing Hypotheses (ACH)
The breach could have resulted from various factors, including insider threats, external cyber-attacks, or system vulnerabilities. Current evidence suggests unauthorized external access, but further investigation is needed to rule out insider involvement.
SWOT Analysis
Strengths: Rapid response and notification efforts by VeriSource.
Weaknesses: Initial detection delay and potential gaps in network security.
Opportunities: Strengthening cybersecurity protocols and employee training.
Threats: Potential misuse of compromised data and reputational damage.
Indicators Development
Key indicators include unusual network activity, phishing attempts targeting employees, and unauthorized data access patterns. Monitoring these can help detect future threats.
3. Implications and Strategic Risks
The breach highlights vulnerabilities in data protection strategies, posing risks to personal privacy and organizational reputation. There is a potential for increased regulatory scrutiny and financial liabilities. Cross-domain risks include the possibility of data being used for identity theft or fraud.
4. Recommendations and Outlook
- Enhance cybersecurity infrastructure with advanced threat detection and response capabilities.
- Conduct regular security audits and employee training to mitigate insider threats.
- Implement a robust incident response plan to address future breaches swiftly.
- Scenario Projections:
- Best Case: Strengthened security measures prevent future breaches, and affected individuals face minimal impact.
- Worst Case: Data misuse leads to widespread identity theft and significant financial losses.
- Most Likely: Improved security posture mitigates further risks, but some individuals may experience data misuse.
5. Key Individuals and Entities
No specific individuals are named in the report. The focus is on VeriSource and its response to the breach.
6. Thematic Tags
(‘cybersecurity’, ‘data breach’, ‘identity protection’, ‘risk management’)