Google Threat Intelligence Group GTIG tracked 75 actively exploited zero-day flaws in 2024 – Securityaffairs.com
Published on: 2025-04-29
Intelligence Report: Google Threat Intelligence Group GTIG tracked 75 actively exploited zero-day flaws in 2024 – Securityaffairs.com
1. BLUF (Bottom Line Up Front)
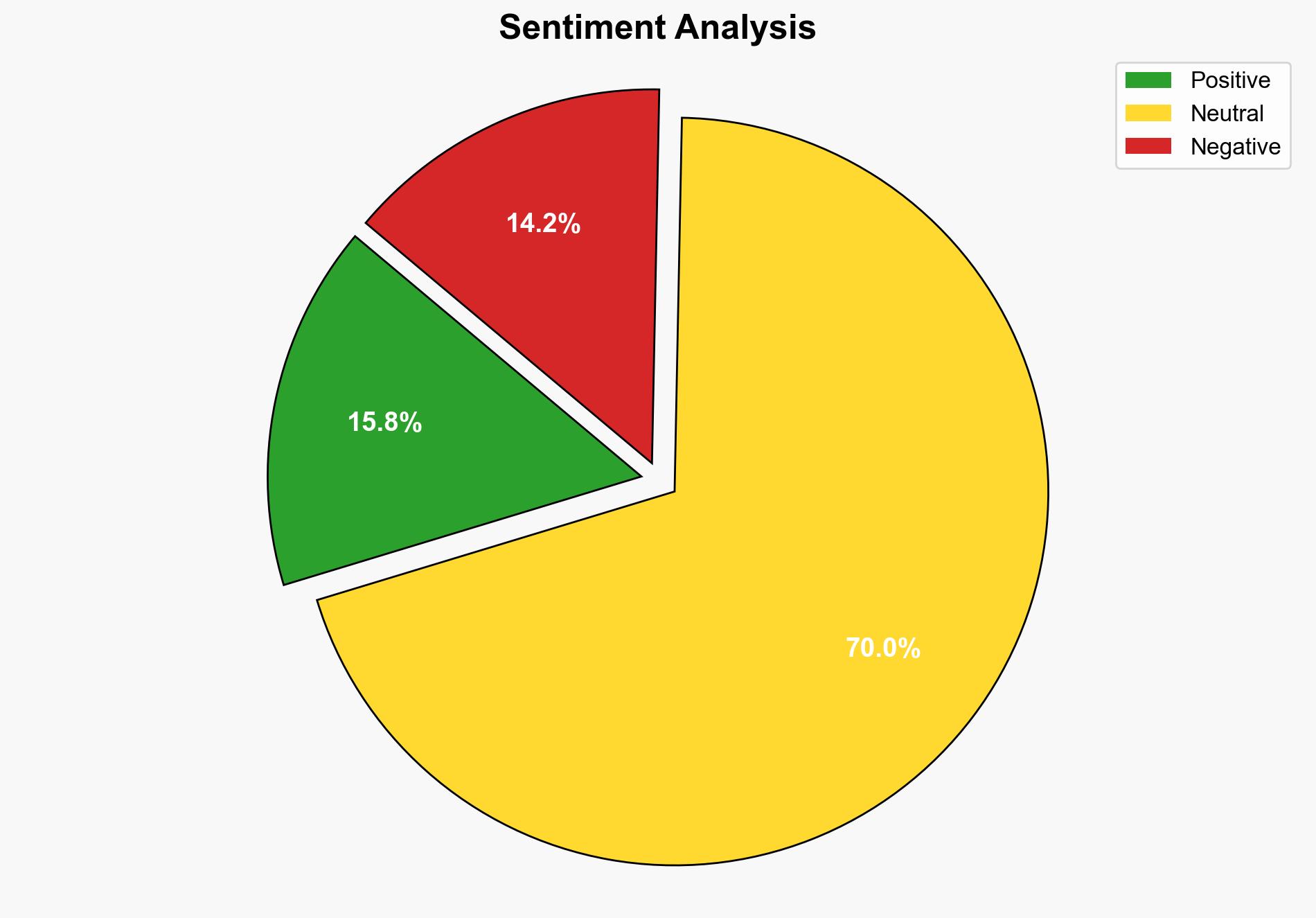
The Google Threat Intelligence Group (GTIG) has identified 75 zero-day vulnerabilities actively exploited in 2024, primarily targeting enterprise technologies. This trend underscores a significant rise in sophisticated cyber threats, with state-sponsored actors and commercial surveillance vendors playing prominent roles. Immediate action is recommended to enhance detection capabilities and patch management processes to mitigate these risks.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Scenario Analysis
Potential scenarios include increased cyber espionage activities by nation-states and commercial entities leveraging zero-day vulnerabilities to gain unauthorized access to sensitive enterprise systems. This could lead to significant data breaches and operational disruptions.
Key Assumptions Check
Assumptions that enterprise technologies are sufficiently protected against zero-day exploits are challenged. The persistent targeting of Microsoft Windows and other enterprise products suggests vulnerabilities in current defensive measures.
Indicators Development
Key indicators include spikes in zero-day exploit reports, increased patch releases by major software vendors, and heightened activity from known cyber espionage groups. Monitoring these indicators can provide early warning of escalating threats.
3. Implications and Strategic Risks
The exploitation of zero-day vulnerabilities poses significant risks to national security, economic stability, and corporate integrity. The reliance on enterprise technologies makes them attractive targets, potentially leading to widespread disruptions and loss of sensitive information. The involvement of state-sponsored actors increases the complexity and potential impact of these threats.
4. Recommendations and Outlook
- Enhance cybersecurity frameworks by prioritizing the identification and patching of zero-day vulnerabilities.
- Invest in advanced threat detection systems and employee training to recognize and respond to cyber threats effectively.
- Scenario-based projections suggest that without significant improvements in cybersecurity practices, the frequency and impact of zero-day exploits will continue to rise.
5. Key Individuals and Entities
The report does not specify individuals by name. However, it highlights the involvement of state-sponsored cyber espionage groups and commercial surveillance vendors.
6. Thematic Tags
(‘national security threats, cybersecurity, counter-terrorism, regional focus’, ‘cybersecurity’, ‘counter-terrorism’, ‘regional focus’)