AI powering a dramatic surge in cyberthreats as automated scans hit 36000 per second – TechRadar
Published on: 2025-05-31
Intelligence Report: AI Powering a Dramatic Surge in Cyberthreats as Automated Scans Hit 36,000 per Second – TechRadar
1. BLUF (Bottom Line Up Front)
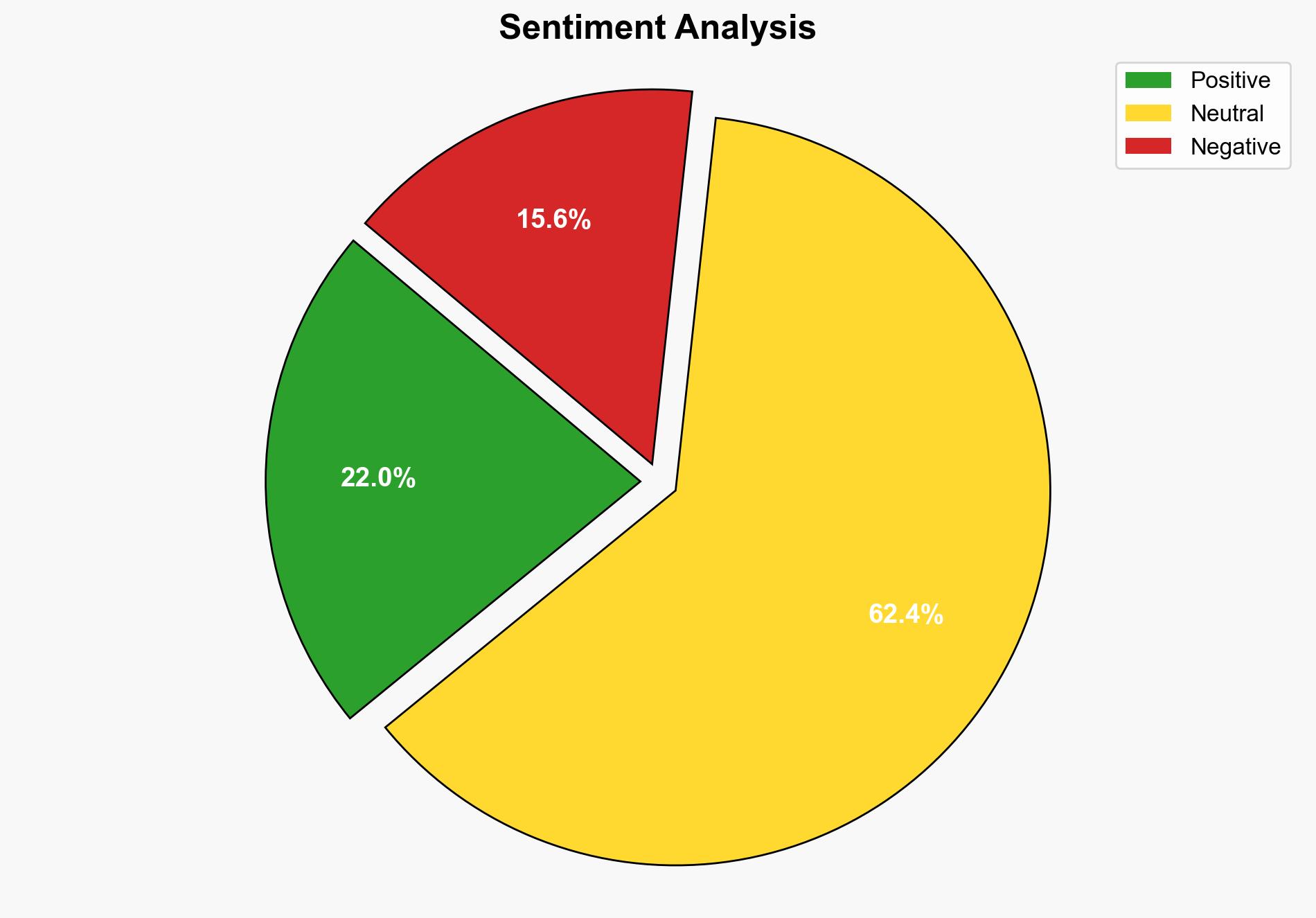
The integration of AI into cyber operations has led to a significant increase in automated cyberthreats, with scans reaching 36,000 per second. This surge is primarily driven by ransomware attacks and the exploitation of vulnerable digital assets. Immediate action is required to update cybersecurity strategies, incorporating AI-driven defenses and zero trust architectures to counteract these evolving threats.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Simulations indicate that threat actors are increasingly targeting remote desktop protocols, IoT systems, and session initiation protocols, exploiting these vulnerabilities early in the attack lifecycle.
Indicators Development
Monitoring has revealed a sharp increase in compromised credentials circulating on the dark web, necessitating enhanced detection of login anomalies and unauthorized access attempts.
Bayesian Scenario Modeling
Probabilistic models predict a continued rise in AI-fueled cyberattacks, with ransomware-as-a-service expanding and new threat groups emerging alongside established players like LockBit and Medusa.
3. Implications and Strategic Risks
The rapid escalation of AI-driven cyberthreats poses significant risks to national security and economic stability. The proliferation of compromised credentials can lead to targeted attacks on critical infrastructure and private sector entities. Failure to adapt to these evolving threats may result in widespread data breaches and financial losses.
4. Recommendations and Outlook
- Implement AI-enhanced security measures and transition to zero trust architectures to mitigate risks.
- Increase investment in continuous threat exposure management to identify and neutralize emerging threats.
- Best Case: Enhanced cybersecurity measures reduce the frequency and impact of cyberattacks.
- Worst Case: Failure to adapt results in significant data breaches and economic disruption.
- Most Likely: Continued adaptation and investment in AI-driven defenses will gradually stabilize the threat landscape.
5. Key Individuals and Entities
Derek Manky, Ellen
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus