Qualcomm finally patches Adreno GPU zero-day flaws used in Android attacks – TechRadar
Published on: 2025-06-03
Intelligence Report: Qualcomm finally patches Adreno GPU zero-day flaws used in Android attacks – TechRadar
1. BLUF (Bottom Line Up Front)
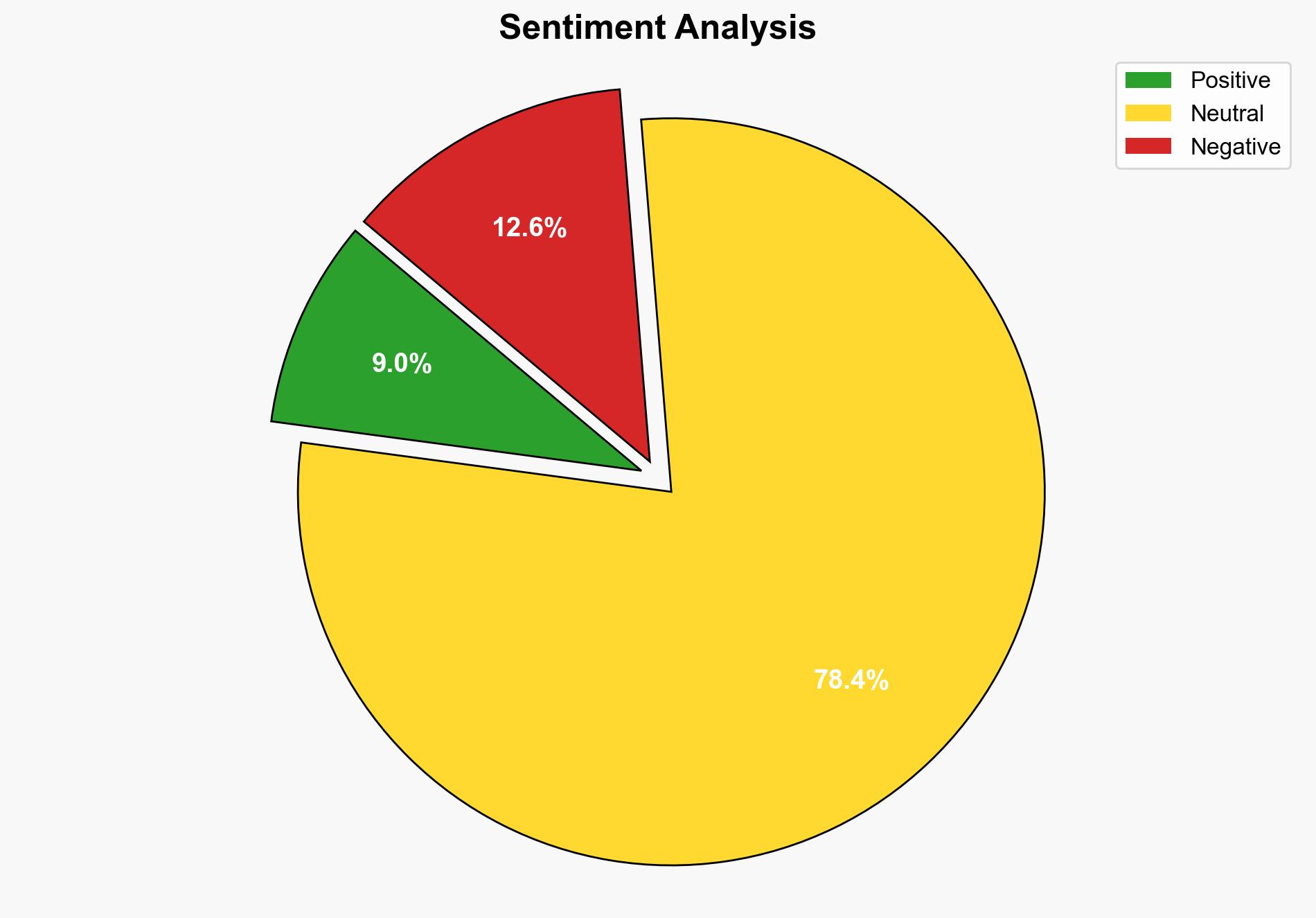
Qualcomm has addressed critical zero-day vulnerabilities in the Adreno GPU drivers, which were actively exploited in Android devices. These vulnerabilities posed significant security risks, allowing unauthorized access and potential memory corruption. Immediate deployment of the patches by OEMs is crucial to mitigate ongoing threats. Key recommendations include prioritizing patch application across affected devices and enhancing monitoring for similar vulnerabilities.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Simulated potential actions by cyber adversaries exploiting the Adreno GPU vulnerabilities, highlighting the need for robust defensive measures.
Indicators Development
Identified behavioral and technical anomalies that could signal exploitation attempts, aiding in early detection and response strategies.
Bayesian Scenario Modeling
Utilized probabilistic models to predict potential attack vectors and assess the likelihood of future exploitation attempts.
3. Implications and Strategic Risks
The exploitation of these vulnerabilities underscores the persistent threat posed by cyber adversaries targeting mobile devices. The widespread use of Qualcomm chipsets amplifies the risk, potentially affecting millions of users globally. Failure to promptly apply patches could lead to increased incidents of data breaches and unauthorized access, impacting both individual and organizational security.
4. Recommendations and Outlook
- Ensure immediate application of Qualcomm’s patches across all affected devices to neutralize current threats.
- Enhance monitoring systems to detect and respond to similar vulnerabilities in the future.
- Best Case: Swift patch deployment prevents further exploitation, maintaining device integrity.
- Worst Case: Delayed patching leads to widespread exploitation, resulting in significant data breaches.
- Most Likely: Gradual patch adoption mitigates most threats, though isolated incidents may persist.
5. Key Individuals and Entities
Sead, a seasoned journalist based in Sarajevo, Bosnia and Herzegovina, contributed to the reporting of this issue.
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus