Microsoft and other security experts want a proper naming system for the worst hackers around – TechRadar
Published on: 2025-06-03
Intelligence Report: Microsoft and other security experts want a proper naming system for the worst hackers around – TechRadar
1. BLUF (Bottom Line Up Front)
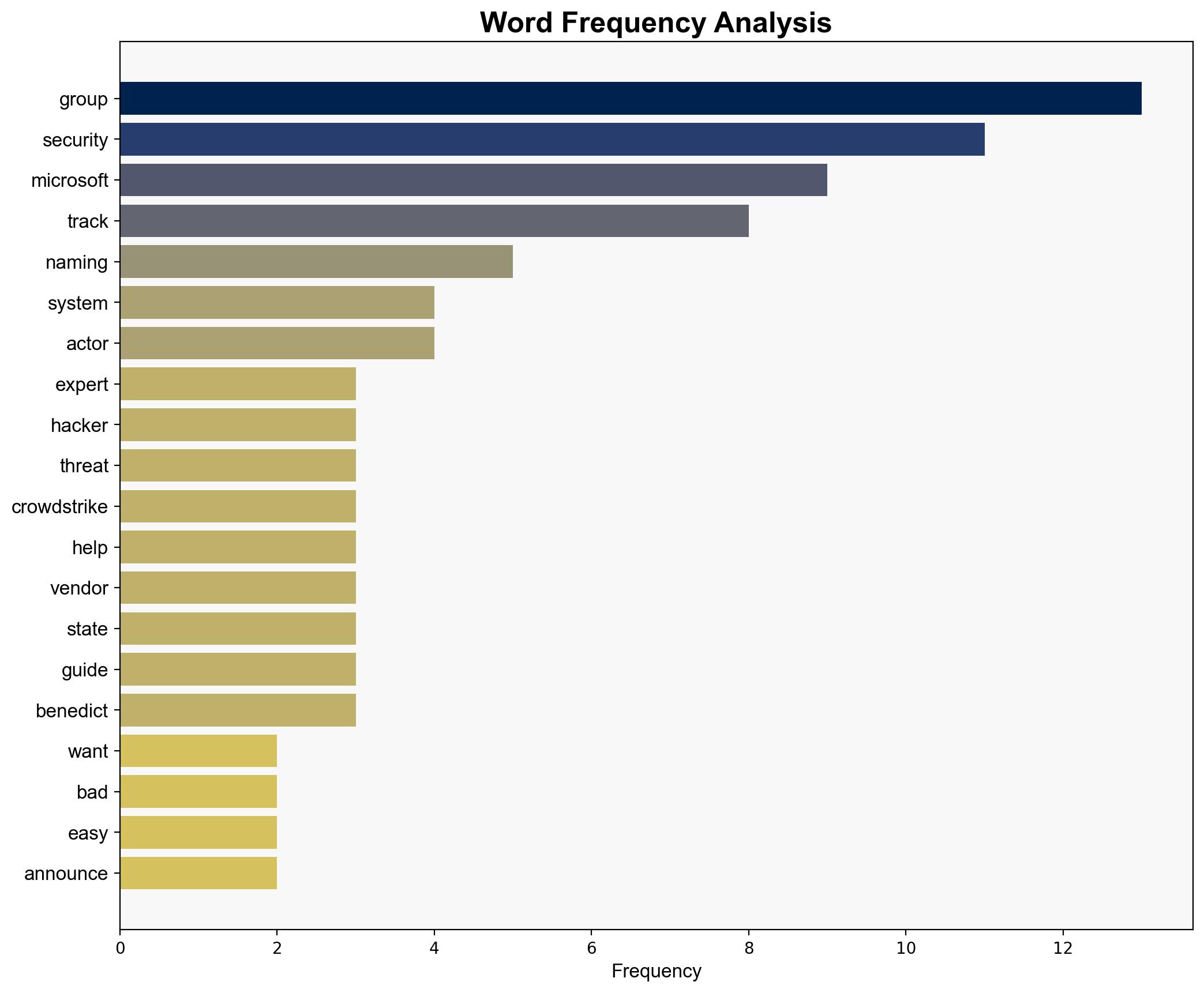
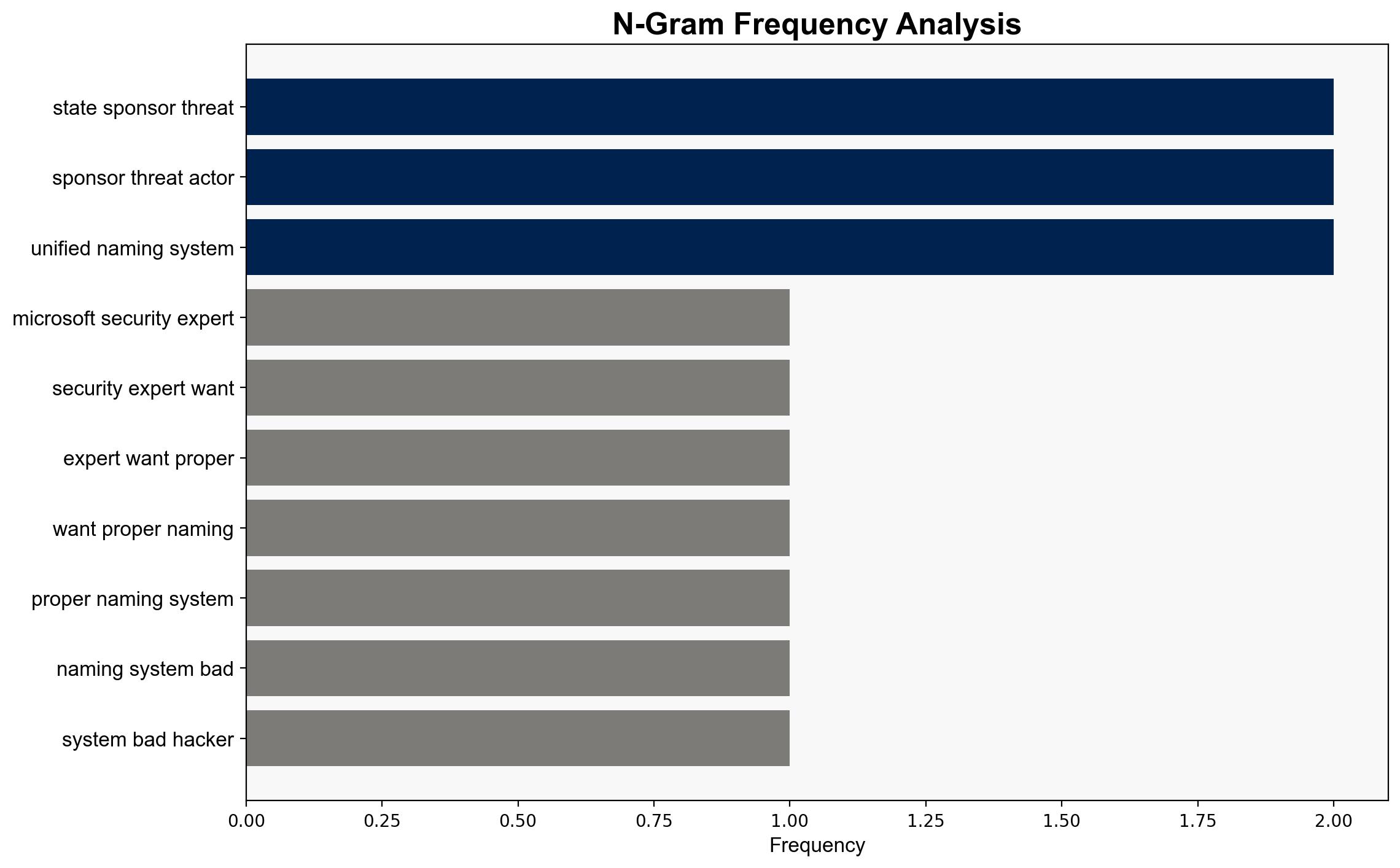
Microsoft, in collaboration with CrowdStrike and other security entities, is advocating for a unified naming system for cyber threat actors. This initiative aims to streamline the identification and response processes, enhancing the efficiency of cybersecurity measures. The proposed system will categorize threat actors based on geographic and motivational factors, using weather-themed nomenclature. This strategic move is expected to reduce confusion and improve the speed and accuracy of threat response.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
By simulating cyber adversary actions, potential vulnerabilities can be identified, allowing for the development of more robust defense strategies.
Indicators Development
Monitoring for anomalies in system behavior can lead to early detection of threats, enabling proactive responses.
Bayesian Scenario Modeling
This technique helps in predicting potential cyberattack pathways by quantifying uncertainties through probabilistic inference.
Network Influence Mapping
Mapping relationships and influences among actors aids in assessing the impact and reach of threat groups.
Narrative Pattern Analysis
Deconstructing ideological narratives allows for a deeper understanding of threat motivations and strategies.
3. Implications and Strategic Risks
The lack of a standardized naming system for threat actors currently complicates threat analysis and response efforts. The proposed unified system could mitigate these challenges, but there is a risk of initial resistance from entities accustomed to existing nomenclature. Additionally, the system must be adaptable to evolving threats and geopolitical changes to remain effective.
4. Recommendations and Outlook
- Encourage widespread adoption of the unified naming system across all cybersecurity stakeholders to ensure consistency.
- Develop training and awareness programs to facilitate the transition to the new system.
- Scenario-based projections: Best case – Rapid adoption leads to improved threat response times. Worst case – Resistance to change delays implementation, maintaining current inefficiencies. Most likely – Gradual adoption with initial challenges but eventual standardization.
5. Key Individuals and Entities
Microsoft, CrowdStrike, Google Mandiant, Palo Alto Networks
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus