Protecting patient data starts with knowing where its stored – Help Net Security
Published on: 2025-06-06
Intelligence Report: Protecting patient data starts with knowing where its stored – Help Net Security
1. BLUF (Bottom Line Up Front)
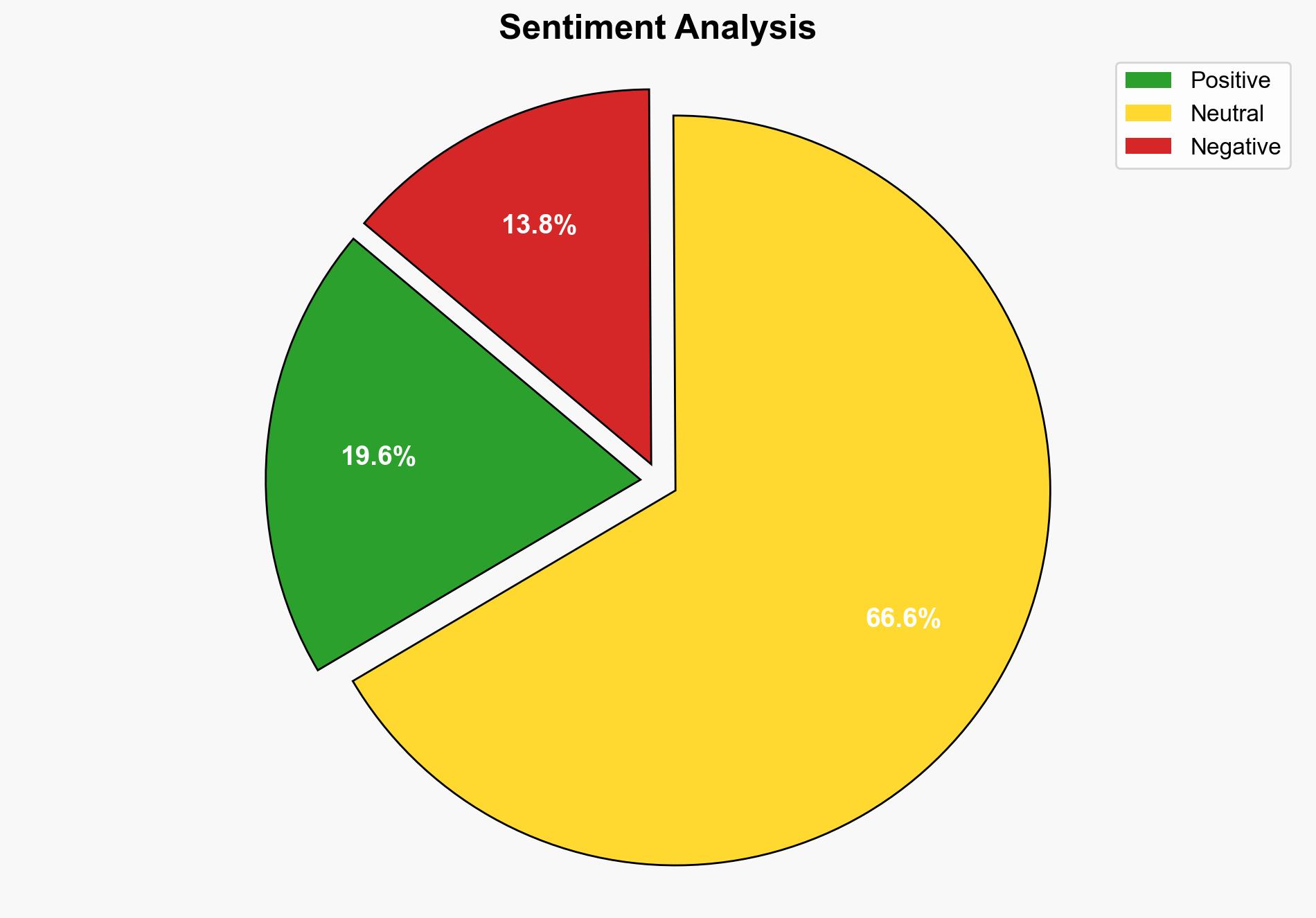
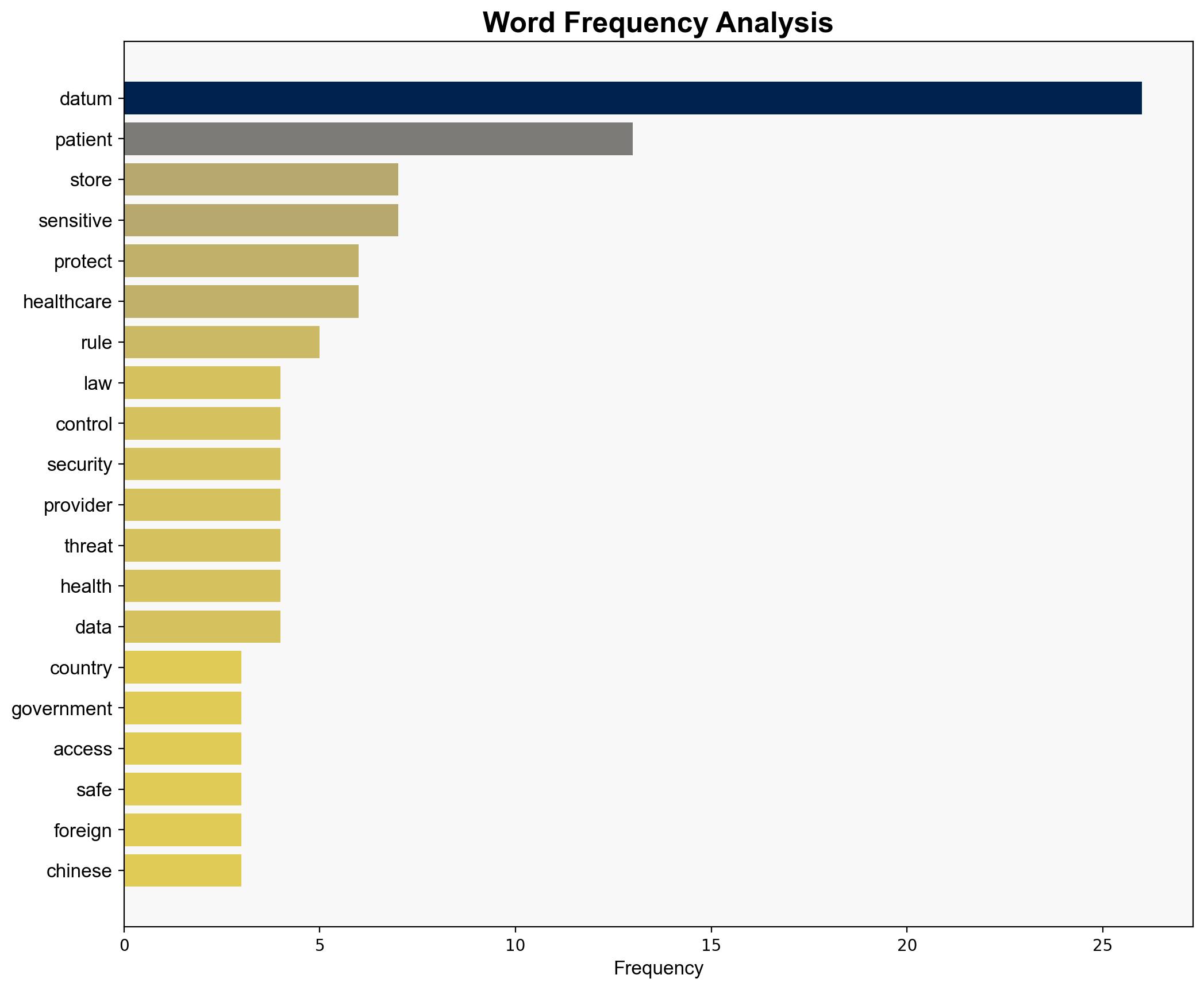
The report identifies significant vulnerabilities in the storage and processing of patient data, particularly concerning foreign infrastructure and legal compliance. Key recommendations include enhancing data residency policies, ensuring compliance with international and domestic regulations, and strengthening cybersecurity measures to protect sensitive health information.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Cognitive Bias Stress Test
Potential biases in assessing the risks of foreign data storage were challenged, ensuring a comprehensive evaluation of threats posed by entities with military or governmental affiliations.
Bayesian Scenario Modeling
Probabilistic forecasting was used to assess the likelihood of data breaches escalating into broader national security concerns, factoring in geopolitical tensions and regulatory changes.
Network Influence Mapping
Influence relationships between healthcare providers, data storage vendors, and foreign entities were mapped to assess the impact of these actors on data security.
3. Implications and Strategic Risks
The integration of foreign infrastructure in healthcare data storage poses significant risks, including potential unauthorized access to sensitive data by foreign adversaries. The evolving regulatory landscape, such as the new Department of Justice rules, further complicates compliance and increases the risk of legal penalties. These factors collectively threaten both national security and public trust in healthcare systems.
4. Recommendations and Outlook
- Enhance data residency policies to ensure patient data remains within domestic jurisdictions, reducing exposure to foreign legal systems.
- Conduct regular audits of third-party vendors to ensure compliance with data protection regulations like HIPAA and GDPR.
- Implement robust cybersecurity measures, including encryption and network segmentation, to safeguard data in transit and at rest.
- Scenario Projections:
- Best Case: Full compliance with regulations and enhanced cybersecurity measures lead to reduced data breach incidents.
- Worst Case: Persistent vulnerabilities result in significant data breaches, leading to national security threats and loss of public trust.
- Most Likely: Incremental improvements in data security and compliance mitigate some risks but do not eliminate them entirely.
5. Key Individuals and Entities
Aaron Weismann
6. Thematic Tags
national security threats, cybersecurity, data protection, healthcare compliance